Sasha Gohman, VP of research at Cymulate, co-authored this article.
The FBI and the U.S. Cybersecurity and Infrastructure Security Agency (CISA) have warned of new Androxgh0st malware that scans for and extracts application secrets, such as credentials and API keys from Laravel .env files. The end goal is to steal credentials from popular cloud applications such as Office 365, AWS, Twilio, SendGrid and others that use the vulnerable Apache web server.
When faced with emergent threats like Androxgh0st, it’s important to take action with three questions in mind:
- What is the behavior of this attack?
- Can my controls mitigate a potential attack?
- Am I vulnerable?
The Androxgh0st Behavior
Attackers deploy Androxgh0st malware by exploiting initial vulnerabilities to search for exposed credentials in Laravel .env files and scanning web servers running Apache HTTP Server versions 2.4.49 or 2.4.50 that are vulnerable to CVE-2021-41773, a path traversal vulnerability from 2021 that allows for remote code execution. CISA has previously warned about this CVE among the list of vulnerabilities that China-backed threat actors tend to exploit the most in their campaigns.
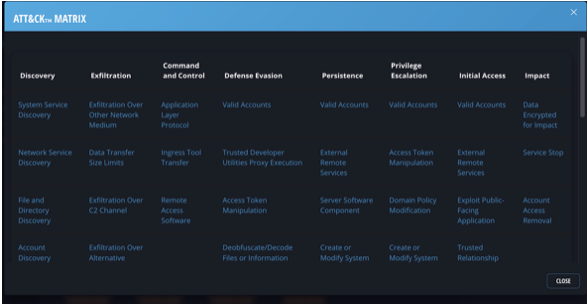
When mapped to MITRE ATT&CK, this campaign is known to apply more than 20 techniques across eight tactics from discovery to impact.
Researchers have identified more than 20 indicators of compromise (IoC) associated with this threat, including, but not limited to URLs:
- http://download·asyncfox·xyz/download/xmrig·x86_64
- http://raw·githubusercontent·com/0x5a455553/MARIJUANA/master/MARIJUANA·php
- http://tangible-drink·surge·sh/configx·txt
- https://pastebin·com/raw/zw0gAmpC
- http://45·95·147·236/tmp·x86_64
- http://main·dsn·ovh/dns/pwer
See the full list of IoCs at the end of this blog.
Threat Validation
When faced with notable emergent threats and CISA advisories, it’s critical that security teams test their controls for their ability to block or detect a related attack. Within hours of the CISA advisory, trustworthy exposure management and security validation platforms would have been updated with a threat assessment that includes all available IoCs for Androxgh0st malware and this related campaign.
Exposure Discovery and Vulnerability
To answer the question of “Am I vulnerable?” security teams must identify the vulnerabilities and misconfigurations in their applications and systems. An added protection that organizations can use to protect against similar threats is attack surface management, which scans internet-facing assets for vulnerabilities such as CVE-2021-41773 and identify exposed configuration files, such as Laravel .env files, often targeted by threat actors to deploy Androxgh0st malware.
Preparation is Key
As threats continue to emerge, organizations who rely on reactive security methods will not endure. Without a strong exposure management and security validation partner, risk will ultimately go unnoticed, leaving businesses vulnerable to the next great threat.
Androxgh0st IoCs
Note: The period character ‘.’ in the hash names has been replaced with a ‘·’ out of an abundance of security caution.
0df1_browsing7ad20bf796ed549c240856ac2bf9ceb19f21a8cae2dbd7d99369ecd317efXxX1Php·php
MD5: 95f745a5db131b1ca34e44848fd52edb
SHA1: 5fae94432540ade68eabce94140c9a5be153b3c8
SHA256: 0df17ad20bf796ed549c240856ac2bf9ceb19f21a8cae2dbd7d99369ecd317ef
23fc51fde90d98daee2_browsing7499a7ff94065f7ed4ac09c22867ebd9199e025dee066XxX2So·so
MD5: 62a06bea8c6e276b5e532944cfc863e5
SHA1: 09bd9b17a64b20ba66582dbc3ce08169697177a8
SHA256: 23fc51fde90d98daee27499a7ff94065f7ed4ac09c22867ebd9199e025dee066
59e90be_browsing75e51c86b4b9b69dcede2cf815da5a79f7e05cac27c95ec35294151f4XxX3Html·html
MD5: 1fb78440dc44b0900b27260a16d9771e
SHA1: 452ec481734a78597b928e29c834d0e43fb2c7e2
SHA256: 59e90be75e51c86b4b9b69dcede2cf815da5a79f7e05cac27c95ec35294151f4
6b5846f32d8009e6b54_browsing743d6f817f0c3519be6f370a0917bf455d3d114820bbcXxX4So·so
MD5: 9039ae16e5aaa63d9ffe88dfaf0f5108
SHA1: 59ce7486745b08d1adba49f2413133c441194986
SHA256: 6b5846f32d8009e6b54743d6f817f0c3519be6f370a0917bf455d3d114820bbc
bb_browsing7070cbede294963328119d1145546c2e26709c5cea1d876d234b991682c0b7XxX5Elf·elf
MD5: c1070aca9fcff4a32934e6c8aee4ea48
SHA1: 7d1beb03c32db43f5edd4c28f3c905954e40dbd6
SHA256: bb7070cbede294963328119d1145546c2e26709c5cea1d876d234b991682c0b7
ca45a14d0e88e4aa408a6ac2ee3012bf9994b16b_browsing74e3c66b588c7eabaaec4d72XxX6Php·php
MD5: fe53c38f61588efd90af97185e315612
SHA1: 79d3143a47dc02768ff5fda8dbcf464c5cdf115b
SHA256: ca45a14d0e88e4aa408a6ac2ee3012bf9994b16b74e3c66b588c7eabaaec4d72
de1114a09cbab5ae9c1011ddd11_browsing719f15087cc29c8303da2e71d861b0594a1baXxX8Txt·txt
MD5: 3fae93618edffe4331d18d8b8e6df693
SHA1: 06641b9b3b5088c48c7660ad3bf160bc87a929fd
SHA256: de1114a09cbab5ae9c1011ddd11719f15087cc29c8303da2e71d861b0594a1ba
0df1_edr7ad20bf796ed549c240856ac2bf9ceb19f21a8cae2dbd7d99369ecd317efXxX1Php·php
MD5: 95f745a5db131b1ca34e44848fd52edb
SHA1: 5fae94432540ade68eabce94140c9a5be153b3c8
SHA256: 0df17ad20bf796ed549c240856ac2bf9ceb19f21a8cae2dbd7d99369ecd317ef
23fc51fde90d98daee2_edr7499a7ff94065f7ed4ac09c22867ebd9199e025dee066XxX2So·so
MD5: 62a06bea8c6e276b5e532944cfc863e5
SHA1: 09bd9b17a64b20ba66582dbc3ce08169697177a8
SHA256: 23fc51fde90d98daee27499a7ff94065f7ed4ac09c22867ebd9199e025dee066
59e90be_edr75e51c86b4b9b69dcede2cf815da5a79f7e05cac27c95ec35294151f4XxX3Html·html
MD5: 1fb78440dc44b0900b27260a16d9771e
SHA1: 452ec481734a78597b928e29c834d0e43fb2c7e2
SHA256: 59e90be75e51c86b4b9b69dcede2cf815da5a79f7e05cac27c95ec35294151f4
6b5846f32d8009e6b54_edr743d6f817f0c3519be6f370a0917bf455d3d114820bbcXxX4So·so
MD5: 9039ae16e5aaa63d9ffe88dfaf0f5108
SHA1: 59ce7486745b08d1adba49f2413133c441194986
SHA256: 6b5846f32d8009e6b54743d6f817f0c3519be6f370a0917bf455d3d114820bbc
bb_edr7070cbede294963328119d1145546c2e26709c5cea1d876d234b991682c0b7XxX5Elf·elf
MD5: c1070aca9fcff4a32934e6c8aee4ea48
SHA1: 7d1beb03c32db43f5edd4c28f3c905954e40dbd6
SHA256: bb7070cbede294963328119d1145546c2e26709c5cea1d876d234b991682c0b7
ca45a14d0e88e4aa408a6ac2ee3012bf9994b16b_edr74e3c66b588c7eabaaec4d72XxX6Php·php
MD5: fe53c38f61588efd90af97185e315612
SHA1: 79d3143a47dc02768ff5fda8dbcf464c5cdf115b
SHA256: ca45a14d0e88e4aa408a6ac2ee3012bf9994b16b74e3c66b588c7eabaaec4d72
de1114a09cbab5ae9c1011ddd11_edr719f15087cc29c8303da2e71d861b0594a1baXxX8Txt·txt
MD5: 3fae93618edffe4331d18d8b8e6df693
SHA1: 06641b9b3b5088c48c7660ad3bf160bc87a929fd
SHA256: de1114a09cbab5ae9c1011ddd11719f15087cc29c8303da2e71d861b0594a1ba
0df1_mail7ad20bf796ed549c240856ac2bf9ceb19f21a8cae2dbd7d99369ecd317efXxX1Php·php
MD5: 95f745a5db131b1ca34e44848fd52edb
SHA1: 5fae94432540ade68eabce94140c9a5be153b3c8
SHA256: 0df17ad20bf796ed549c240856ac2bf9ceb19f21a8cae2dbd7d99369ecd317ef
59e90be_mail75e51c86b4b9b69dcede2cf815da5a79f7e05cac27c95ec35294151f4XxX3Html·html
MD5: 1fb78440dc44b0900b27260a16d9771e
SHA1: 452ec481734a78597b928e29c834d0e43fb2c7e2
SHA256: 59e90be75e51c86b4b9b69dcede2cf815da5a79f7e05cac27c95ec35294151f4
ca45a14d0e88e4aa408a6ac2ee3012bf9994b16b_mail74e3c66b588c7eabaaec4d72XxX6Php·php
MD5: fe53c38f61588efd90af97185e315612
SHA1: 79d3143a47dc02768ff5fda8dbcf464c5cdf115b
SHA256: ca45a14d0e88e4aa408a6ac2ee3012bf9994b16b74e3c66b588c7eabaaec4d72
http://download·asyncfox·xyz/download/xmrig·x86_64
http://raw·githubusercontent·com/0x5a455553/MARIJUANA/master/MARIJUANA·php
http://tangible-drink·surge·sh/configx·txt
https://pastebin·com/raw/zw0gAmpC
http://45·95·147·236/tmp·x86_64
http://main·dsn·ovh/dns/pwer
如有侵权请联系:admin#unsafe.sh
