2024-2-2 03:13:3 Author: securityboulevard.com(查看原文) 阅读量:8 收藏
In the ever-evolving landscape of cybersecurity, the choice of cryptographic algorithms and certificates plays a pivotal role in ensuring the confidentiality and integrity of sensitive information.
While traditional methods such as the RSA public-key cryptosystem have been the cornerstone of secure communication and data transmission for decades, Elliptic Curve Cryptography (ECC) is emerging as an alternative option for organizations that want to enhance their security posture. With Imperva, you have two options for certificates: Bring your own certificates or have Imperva manage it for you.
Let’s explore why ECC, 2K RSA Certificates, and Imperva-managed certifications are options to consider when building your security environment.
What are RSA Cryptography and SSL Cryptography?
RSA encryption, developed in 1977, is an asymmetric encryption technique that uses two varying but linked encryption keys. Full decryption of an RSA ciphertext is considered infeasible, assuming no efficient algorithm exists for integer factorization.
SSL Cryptography uses public-key cryptography to secure communication between servers and clients, commonly seen in the form of HTTPS in web browsers.
The landscape of SSL has evolved. Organizations now commonly use TLS protocol instead of SSL due to vulnerabilities. Asymmetric encryption, a fundamental aspect of SSL, involves using two keys for encryption and decryption. RSA has been the go-to algorithm for asymmetric encryption, with key sizes of 1024- or 2048-bits. While RSA is proven, ECC is emerging as a more efficient alternative.
Elliptic Curve Cryptography (ECC): Efficiency and Enhanced Security
ECC introduces a shift in cryptographic algorithms. Based on elliptic curves over finite fields, ECC provides the same level of security as RSA but with significantly shorter key lengths. The efficiency of ECC allows for faster computation times, reduced computational power requirements, and decreased bandwidth usage. This makes ECC an ideal choice for resource-constrained devices like IoT devices and mobile phones.
The comparison between ECC and RSA key sizes demonstrates the advantage of ECC in providing the same cryptographic strength with much smaller key sizes (seen in the chart below). ECC’s ability to offer robust security with reduced computational requirements is particularly valuable in today’s diverse and interconnected digital landscape.
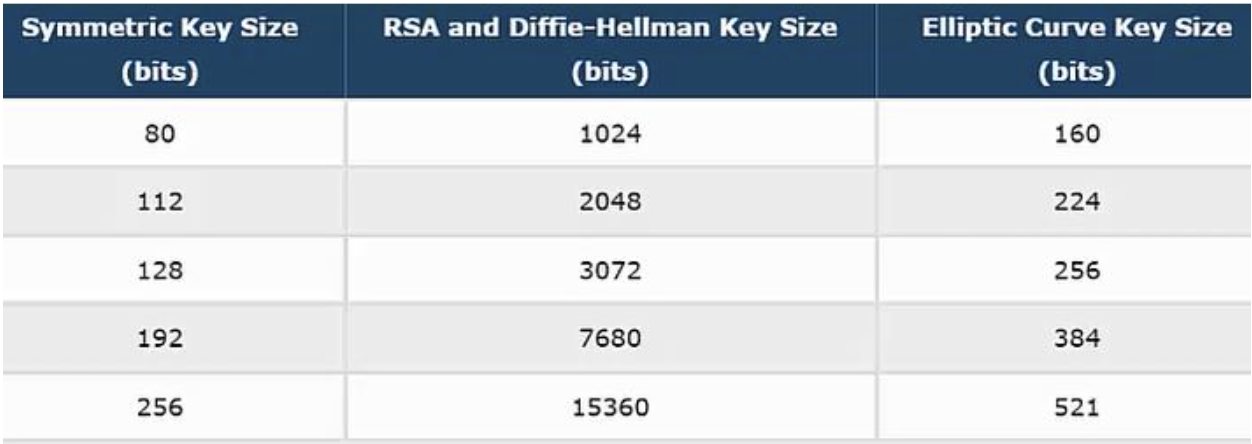
NIST recommended key sizes
2K RSA Certificates: Striking the Right Balance
As websites transitioned from SSL to TLS, certificates became pivotal for establishing secure connections. The industry standard for SSL/TLS certificates is the 2K RSA Certificate, referring to a 2048-bit key size. This key size balances security and performance, ensuring robust encryption without compromising user experience.
Imperva-managed Certification: Elevating Security with Trusted Certificates
Imperva offers 2K Certificates managed by our team of experts. We offer full certificate lifecycle management from creation to revoke, renewal, and reissue. Imperva-managed 2K Certificates are a great way to reduce total cost of ownership (TCO) while using services from a trusted partner.
Advantages for Customers
- Enhanced Security: ECC, 2K RSA Certificates, and Imperva-managed 2K Certificates collectively provide high-level security, protecting customer data from unauthorized access and cyber threats.
- Improved Performance: The efficiency of ECC and the optimal key size of 2K certificates contribute to faster computation times and better overall performance, ensuring a seamless user experience.
- Compatibility: 2K certificates are widely supported by browsers and devices, ensuring compatibility across various platforms. This compatibility is crucial for a seamless and secure online experience for customers.
- Trusted Certificates: Leveraging the Imperva reputation as a trusted cybersecurity provider, customers can have confidence in the authenticity and reliability of the 2K certificates they use.
The combination of advanced cryptographic algorithms, efficient key sizes, and the trust associated with a cybersecurity leader like Imperva makes managed certificates a compelling option for customers aiming to enhance their security posture. By embracing these technologies, customers can navigate the digital realm with confidence, knowing that their data is protected by robust and efficient encryption measures.
To learn more about how Imperva can help your organization, contact us.
The post Improving Cybersecurity: Different Certifications Explained appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Luke Richardson. Read the original post at: https://www.imperva.com/blog/improving-cybersecurity-different-certifications-explained/
如有侵权请联系:admin#unsafe.sh
