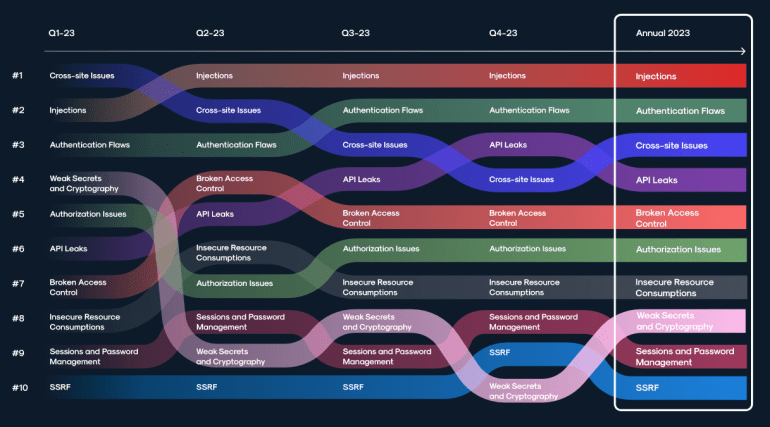
In our Annual API ThreatStats report, we highlighted the increasing threat of API Leaks. An API Leak is the disclosure of sensitive API information, such as a token, credential, or private schema. These leaks can occur directly via the API itself, but also via third party tools used to manage source code, such as Github or Postman. API Leaks came in at number 4 in our dynamic top 10 list of API Security issues. Almost more interesting is that the ranking of API leaks steadily increased throughout 2023, indicating that it’s an increasingly problematic issue for organizations.

On February 1st, we saw the breaking story that Cloudflare had been compromised by attackers using a stolen authentication token from the Okta breach. While not exactly a leak, the incident is still relevant to how organizations can protect themselves from compromised tokens like these.
Wallarm provides the ability to block the use of specific authentication tokens in traffic. Wallarm users can create Virtual Patch rules that block based on a regular expression in a specific header or request point. In other words, if you know the token or tokens that are compromised, and the authentication mechanism for those tokens, you can create a rule to block their use before they even get to your application. Here’s an example of what a rule might look like:

Additionally, the API Leak Detection capability can proactively find leaked tokens for which you can seamlessly create a virtual patch.
To find out more about what’s possible in Wallarm rules, check out the documentation.
The post Blocking Compromised Tokens with Wallarm appeared first on Wallarm.
*** This is a Security Bloggers Network syndicated blog from Wallarm authored by Jaweed Metz. Read the original post at: https://lab.wallarm.com/blocking-compromised-tokens-with-wallarm/