2024-2-14 00:38:28 Author: www.malwarebytes.com(查看原文) 阅读量:17 收藏
Remote Monitoring & Management (RMM) software, including popular tools like AnyDesk, Atera, and Splashtop, are invaluable for IT administrators today, streamlining tasks and ensuring network integrity from afar. However, these same tools have caught the eye of cybercriminals, who exploit them to infiltrate company networks and pilfer sensitive data.
The modus operandi of these threat actors involves deceiving employees through sophisticated scams and deceptive online advertisements. Unsuspecting employees, misled by these tactics, may inadvertently invite these criminals into their systems. By convincing employees to download and run these seemingly benign RMM applications under the guise of fixing non-existent issues, these fraudsters gain unfettered access to the company’s network.
In this post, we explore a particular phishing scam targeting corporate users via the AnyDesk remote software and how ThreatDown can prevent the misuse of such programs by cybercriminals.
Phishing site hosts remote software
We believe victims are first targeted and then contacted via phishing emails or text messages (smishing) based on their position in the company.
Attackers could trick them by sending them to a typical phishing page or making them download malware, all of which are good options. However, they are instead playing the long game where they can interact with their victims.
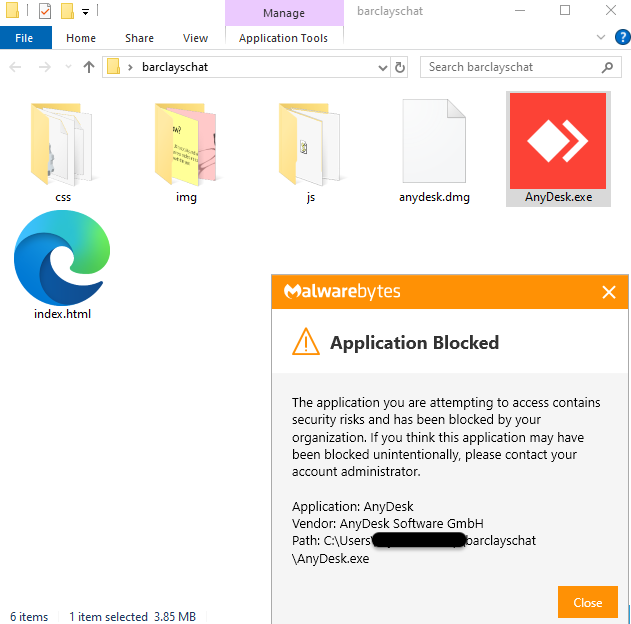
Users are directed to newly registered websites that mimic their financial institution. In order to get support, they need to download remote desktop software disguised as a ‘live chat application’.
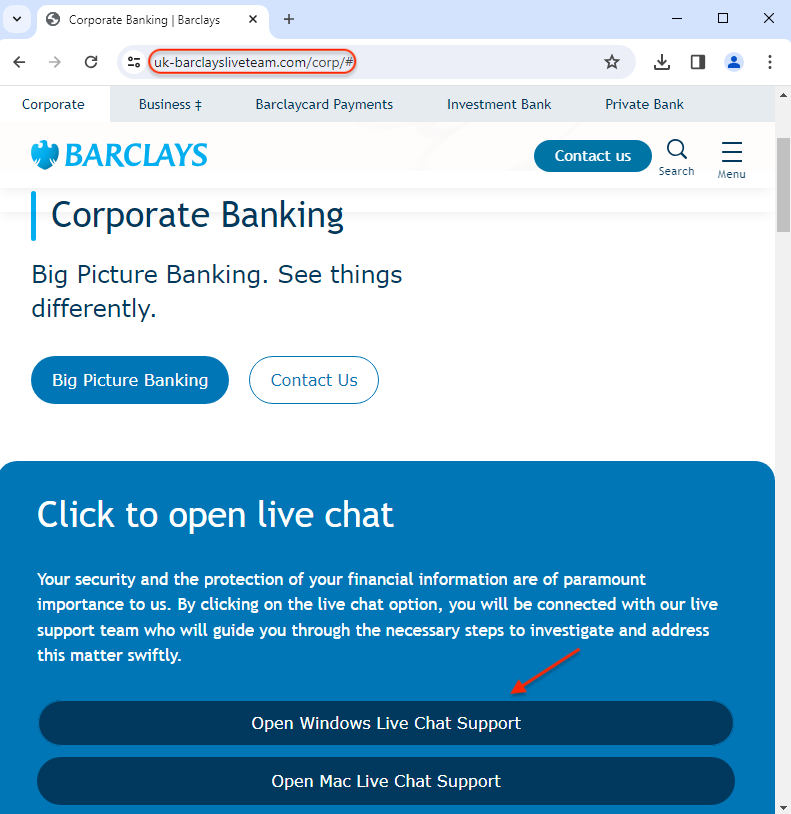
uk-barclaysliveteam[.]com/corp/AnyDesk.exe
uk-barclaysliveteam[.]com/corp/anydesk.dmg
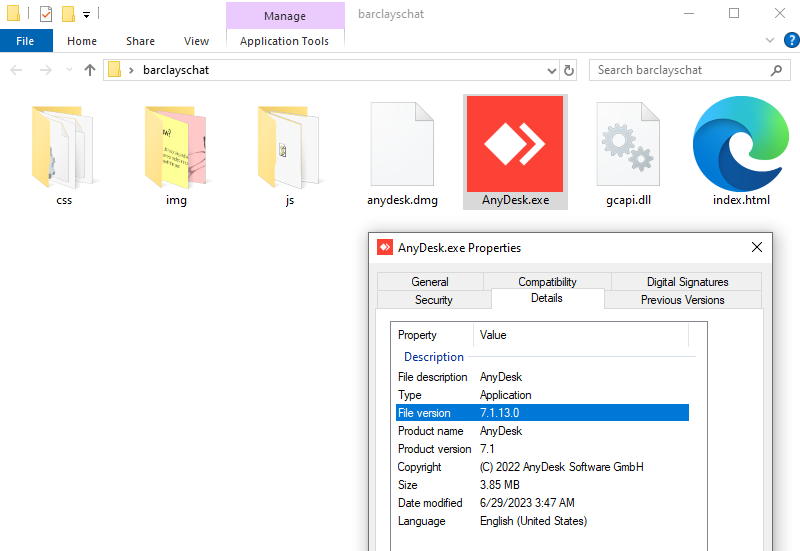
It’s interesting to note that the downloaded software is not malware. For example, in this instance they are using a legitimate (although outdated) AnyDesk executable which would not be detected as malicious by security products.
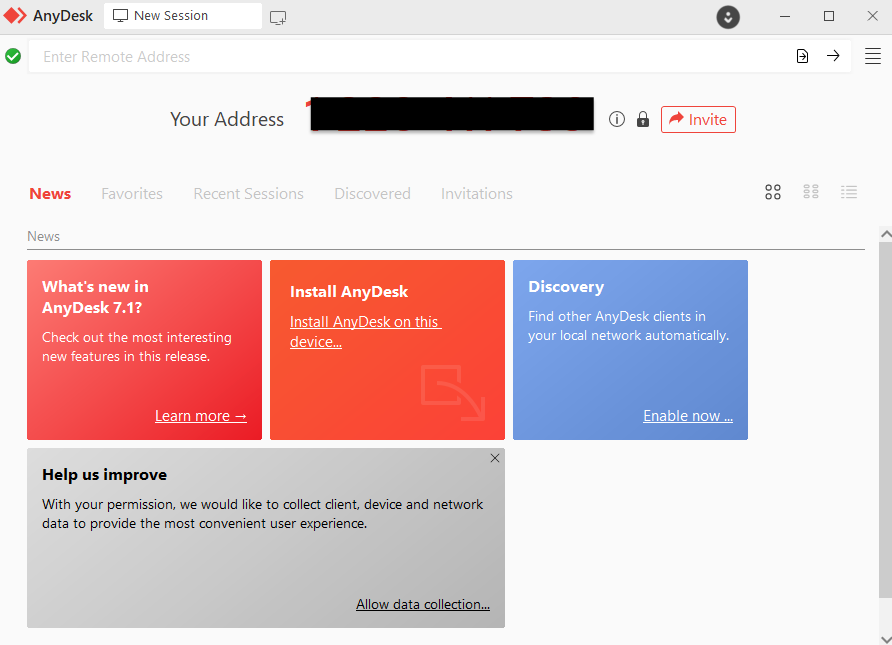
Running the program will show a code that you can give to the person trying to assist you. This can allow an attacker to gain control of the machine and perform actions that look like they came directly from the user.
This is one reason why certain banking sites try to can detect if a customer is currently running a remote program, before allowing them to login. However, not all banks have this feature and there are certain cases where threat actors can evade such detection.
There are a number of RMM tools on the market which scammers and criminals will leverage. Ironically, the more popular and simple ones also tend to be the most abused.
AnyDesk recently got in the news for a security breach that allowed the attackers to compromise their production systems. The vendor has since revoked its code signing certificates and is urging customers to update their software.
RMM vendors are aware of the illicit use of their software and regularly remind users about common safety tips. AnyDesk also partnered with fraud fighters such as ScammerPayback to shut down call centers.
Free with every ThreatDown Bundle, Application Block can easily protect organizations against the rising trend of legitimate RMM tools being exploited. Organizations can block RMM tools via Application Block by:
- Navigating to the ‘Monitor’ section within their Nebula console.
- Selecting ‘Application Block’
- Enabling the ‘Block RMM’ toggle switch provided by ThreatDown or customizing the list to fit their specific needs.
Saving the configuration to immediately block these RMM tools network-wide.
Adopt a robust defense stance by blocking all unnecessary applications, and for those you must use, the EDR/MDR layers of our ThreatDown Bundles will provide an additional safety net in the event of an infection.
Try ThreatDown bundles today
For IT teams plagued by the triad of complex deployment, scattered tooling, and excessive alert noise, ThreatDown bundles emerge as a superior solution that caters to the needs of today’s security teams.
Discover the difference with ThreatDown Bundles and elevate your organization’s defense against cyber threats. Get in touch for a free trial and experience the benefits of a simplified, yet robust, security framework.
如有侵权请联系:admin#unsafe.sh