
2024-2-20 05:39:10 Author: www.offensiveosint.io(查看原文) 阅读量:28 收藏
CEO, VP of Engineering and PR specialist (spoiler - this is the same person) approved the release of a new feature for the community, free of charge, to offer a preview of geo-tracking individuals across various social media platforms
From now on, you can search by username, directly in OSS, and get coordinates and other important information back. All results are displayed on the map what makes it super easy to determine last activities of the person.
Register on
Open Source Surveillance
Real time intelligence gathering tool
 Links Other projects & Social Offensive OSINT
www.offensiveosint.io Kamerka.io
kamerka.io Twitter
@the_wojciech Github
woj-ciech Discord
Offensive OSINT channel
Links Other projects & Social Offensive OSINT
www.offensiveosint.io Kamerka.io
kamerka.io Twitter
@the_wojciech Github
woj-ciech Discord
Offensive OSINT channel

In addition, couple weeks ago feature to generate PDF report was released
Reporting in #OSINT investigations is crucial, and Open Source Surveillance makes it easy! 🕵️♂️ Export PDF reports with detailed insights on user activity, location & more. Check it out at https://t.co/sXiTUvAmZt #CyberSecurity #privacy #infosec pic.twitter.com/QNvJLitu7i
— Offensive OSINT (@the_wojciech) January 30, 2024
There are already plenty of tools to check whether account exists based on the username, but not many to gather additional details, and I didn't find any that also collects geolocation data from the profile, that's why I've decided to publish this feature. However though, it's part of even bigger project, that I released last month, to cross reference Location-->Activity-->Person
Offensive OSINT s05e03 - Open Source Surveillance - People API
I’m super excited to announce newest update which allow to easily uncover the person behind the photo or activity in your research area. REGISTER Open Source SurveillanceReal time intelligence gathering toolLinks Other projects & Social Offensive OSINT www.offensiveosint.io Kamerka.io kamerka.io Twitter @the_wojciech Github woj-ciech Discord Offensive
 Wojciech
Wojciech

This article describes how to find user geolocated activity on a couple of popular social media platform with help of Open Source Surveillance.

Gallinago is the codename for this project, and the logo features a depiction of the bird species Gallinago Gallinago anthropomorphized as a human and holding a gun. One month free to someone who figures out the meaning behind the logo. Send answers to #general on Offensive OSINT Discord.
When you access the website, new button on sidebar "Search username" appears.
The rule is simple, you must provide ID or Username to the search field and choose the platform, which we will go through each one to introduce how to get maximum out of the process.
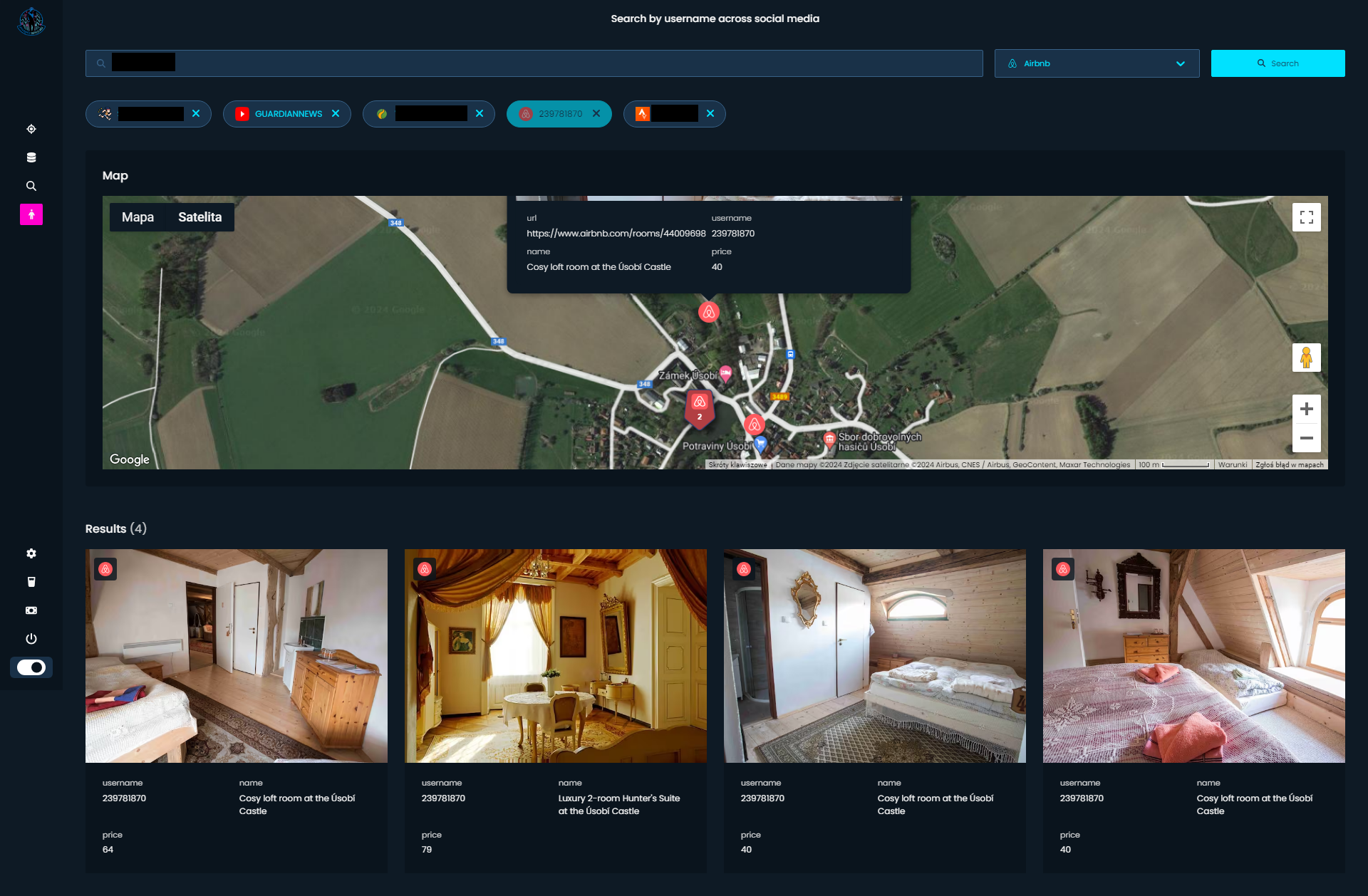
Airbnb
Unfortunately, after some changes, it's not possible to obtain information about trips for specific user. What we can get though, are listings, if user is a Host.
https://www.airbnb.com/users/show/57382448
When you provide user ID (digits in the GET request) module will collect 50 latest listings, i.e. apartments this person rent or is responsible for renting
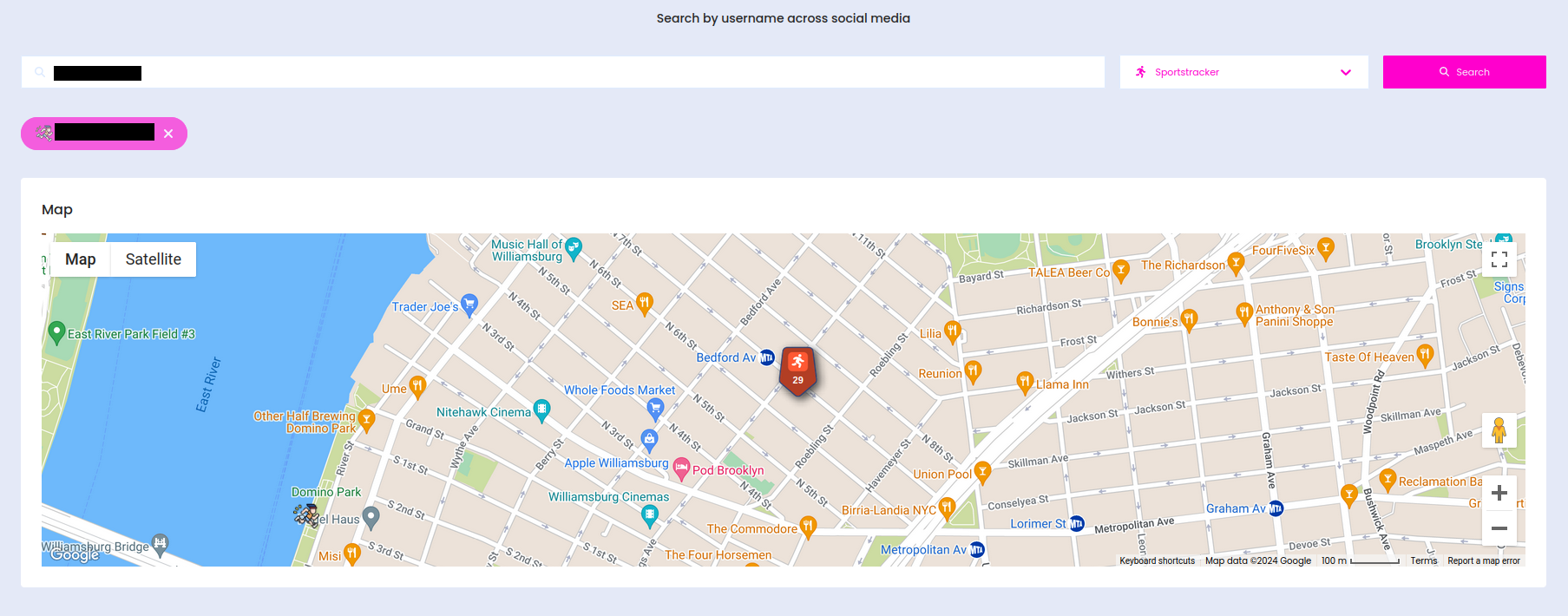
Sportstracker
As name suggest, Sportstracker is yet another fitness activity tracking website. You can get data like timestamp, full name, distance, speed and of course latitude and longitude of activity.
You need to pass username from the Sportstracker user profile, to get latest 100 results.
Sports Tracker - the original sports app with maps and GPS tracker for running, cycling, fitness, workout and training.
Sports Tracker turns your mobile into a social sports computer


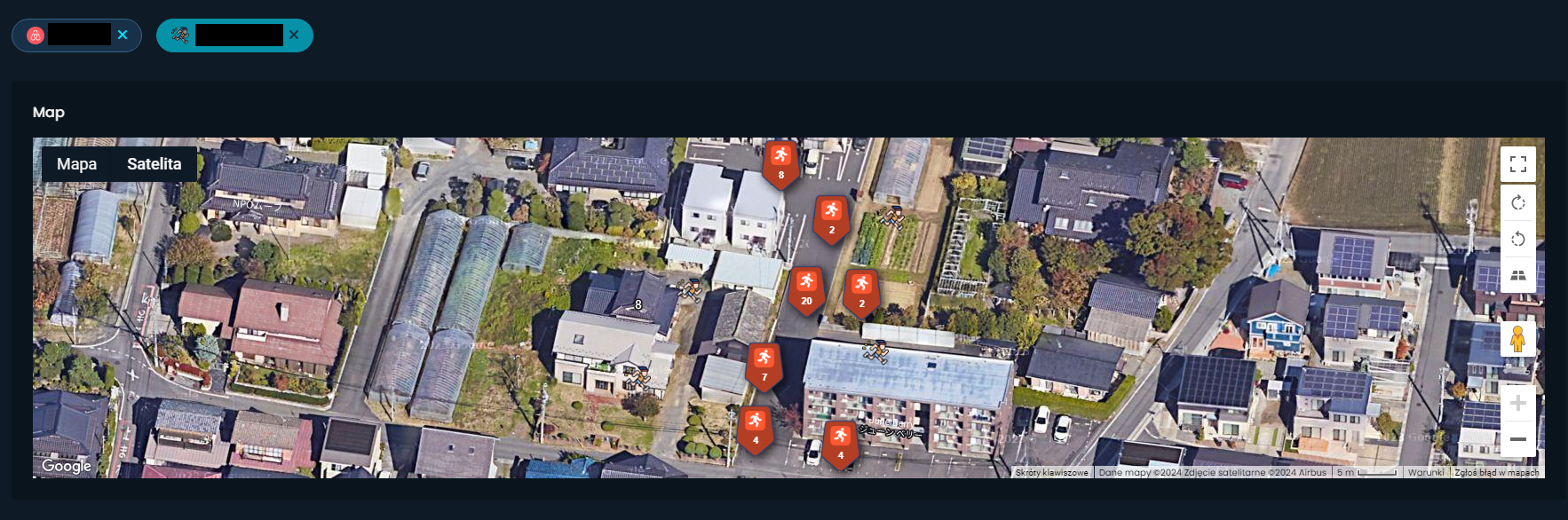
Building where person starts his running
This is the only application that allows to display activity of the user on map. For the rest of the websites, it's not possible directly on website or it's a paid feature.
Strava
Strava has changed, same as Airbnb, and it's not easy to gather any data from the user profile. However, if you pass User ID, Open Source Surveillance will gather activities, including group ones, from last 3 months.
Adam Plows | Strava Runner Profile
Adam Plows is a runner from United Kingdom. Join Strava to track your activities, analyze your performance, and follow friends. Strava members can plan routes, participate in motivating challenges, and join clubs. Get started by signing up for free.
 Strava
Strava

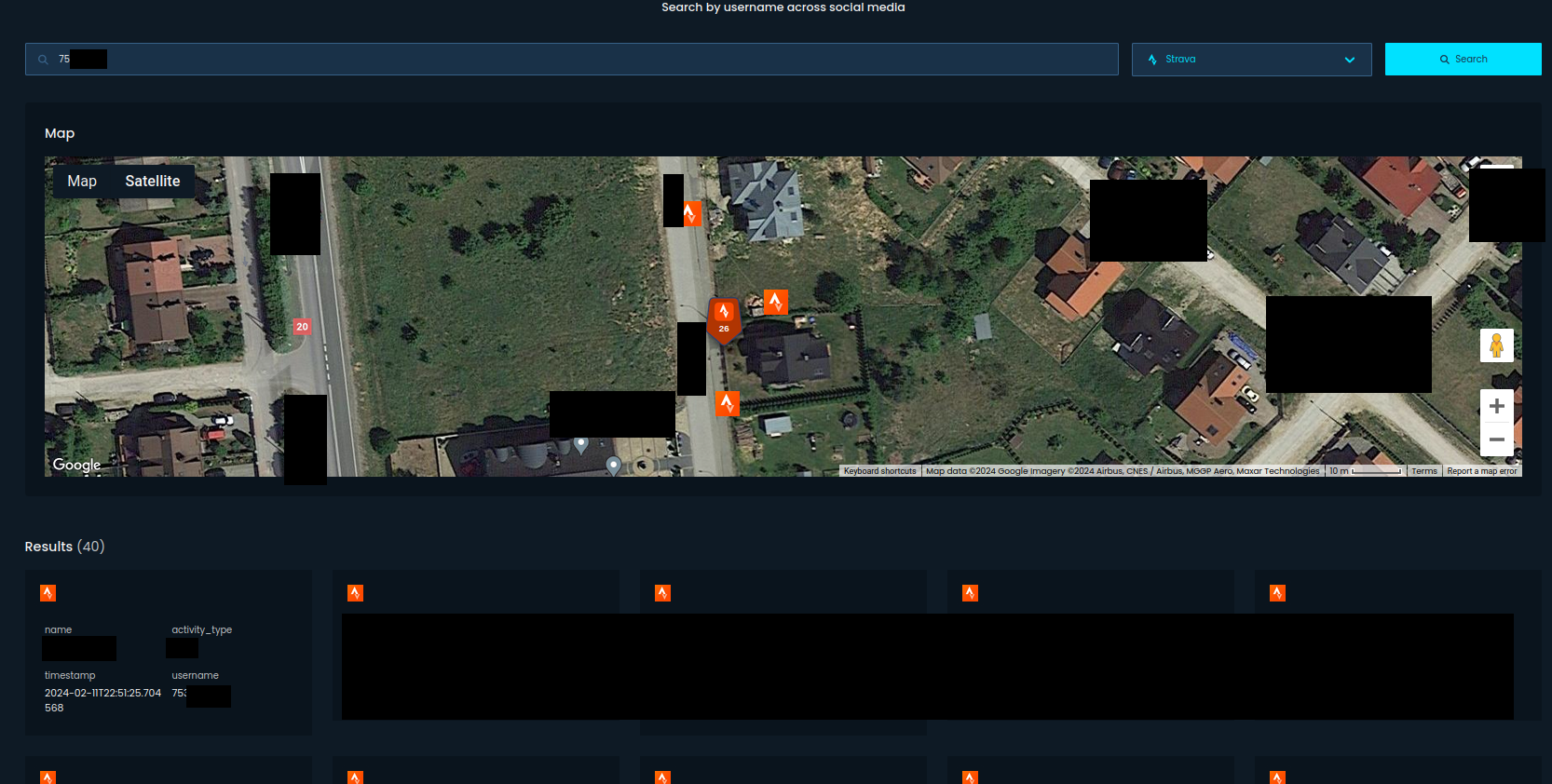
Another example
Wikiloc
This is popular fitness tracking application, where users can share their runs, walks and other trips. From OSINT perspective, it's trove of information; like any other modules honestly. For this module you need to pass user ID, like below.
App returns latest 25 activities.
Below screenshot presents activity in one of the United States Air Force Base and couple months later in another military base in South Korea.
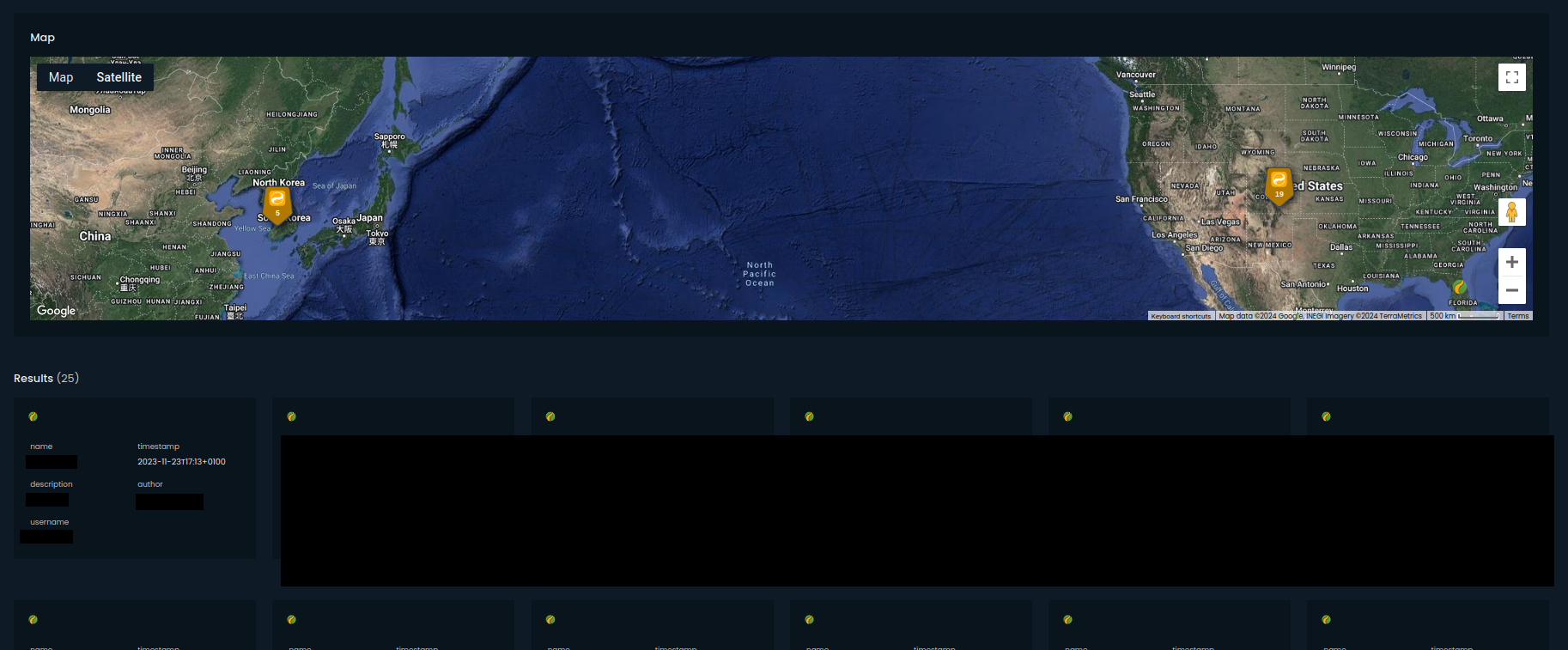
From one Air Force Base to another
Youtube
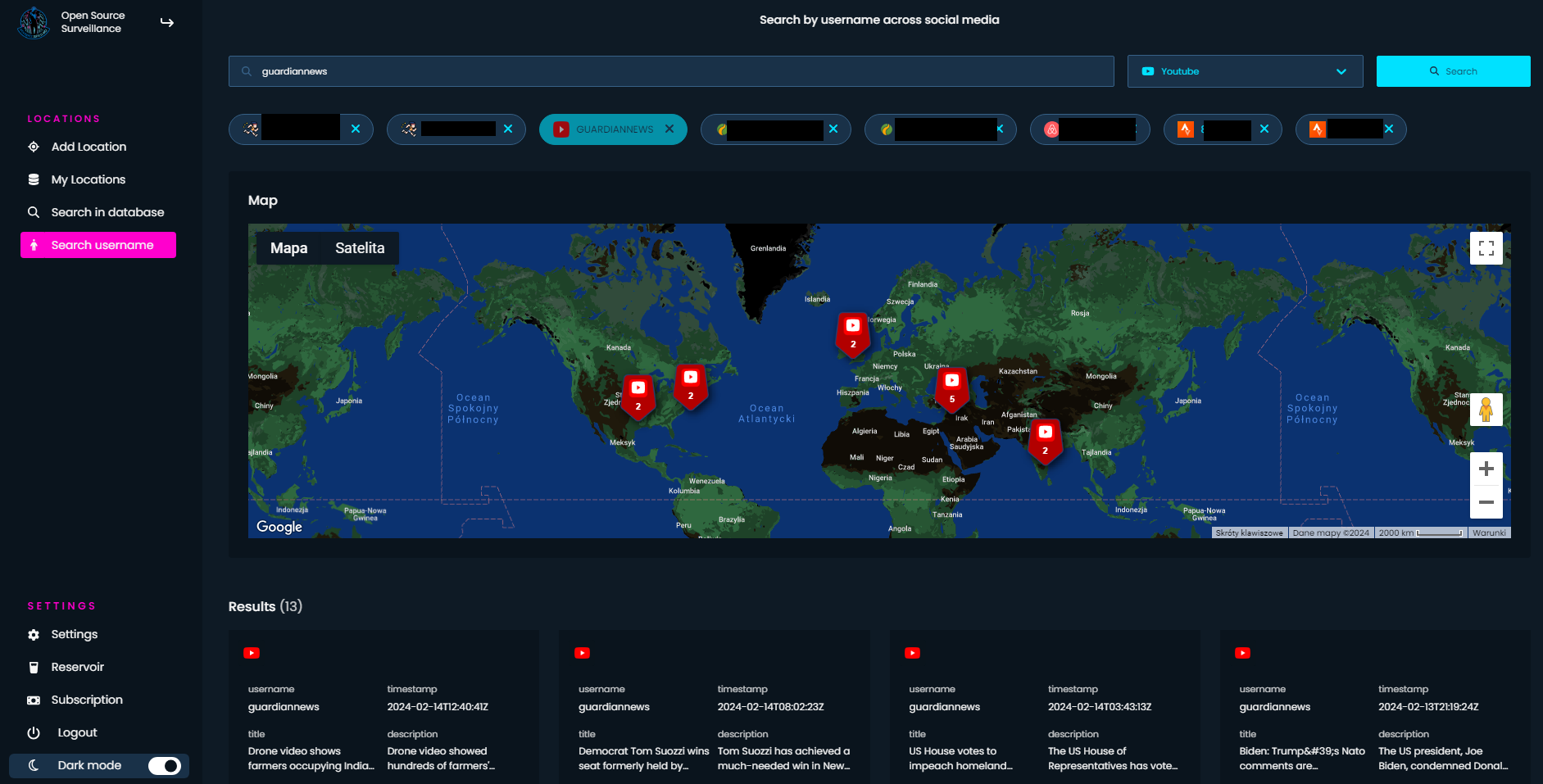
Everyone knows Youtube, it's the most popular video streaming service, where users can upload geotagged videos. This is the only module, from above mentioned, where location cannot be exact, or at least exact to the city.
https://www.youtube.com/@TraxNYCDiamondJewelry
OSS searches 25 latest videos and gather only ones with geolocation.
Gallinago has been implemented to Open Source Surveillance for a reason and it's another step for OSINT researchers, from variety of professions, to monitor & track users, activity and location based on social media and other open sources.
So let's focus on the workflow and how to utilize new features into your investigation.
As mentioned at the beginning, one of the goals of OSS is to research Location and look for Activity, and now it's possible to cross check it against Person.
Let's take a look on example. You investigate specific case and look for activity in particular timeframe on specific territory and found Sportstracker run (right side of the image, trail is drawn).
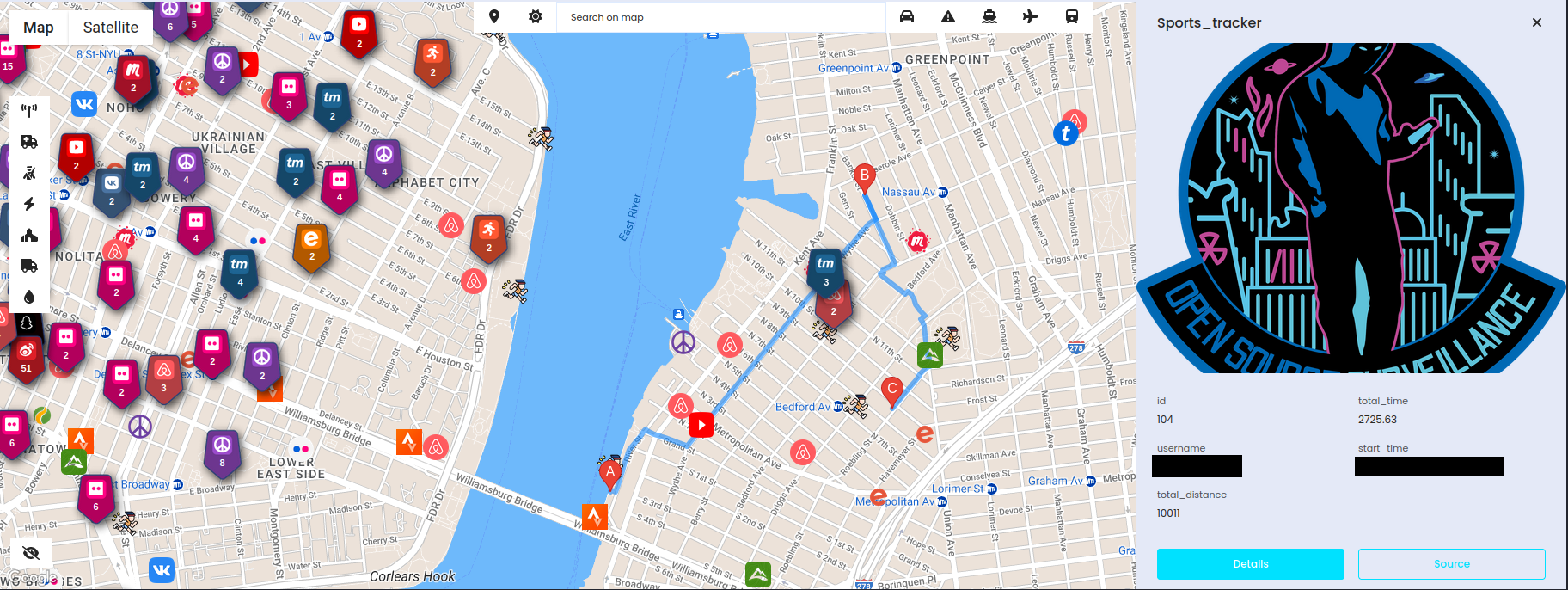
Returned response contains username, so we don't need to even go to website to grab one but directly to search username in the tool.
Results show original run (on the left, near Domino Park) and 29 other in same location, which is most probably place where Person lives.
I've been always fascinated about critical infrastructure from physical as well as cyber side - offensive as well as defensive approach, you can read about the identification of employees of particular facility in my previous article
TL;DR Based on the information gathered from government websites, facility and exposed industrial control devices it's quite simple to find workers and details about them, including email address.
Every piece of information allows for more successive phishing attack, and OSS can help to identify and search for routine of people from variety of professions. One of my favourite example, also previously mentioned, is look for military bases and activity in them.
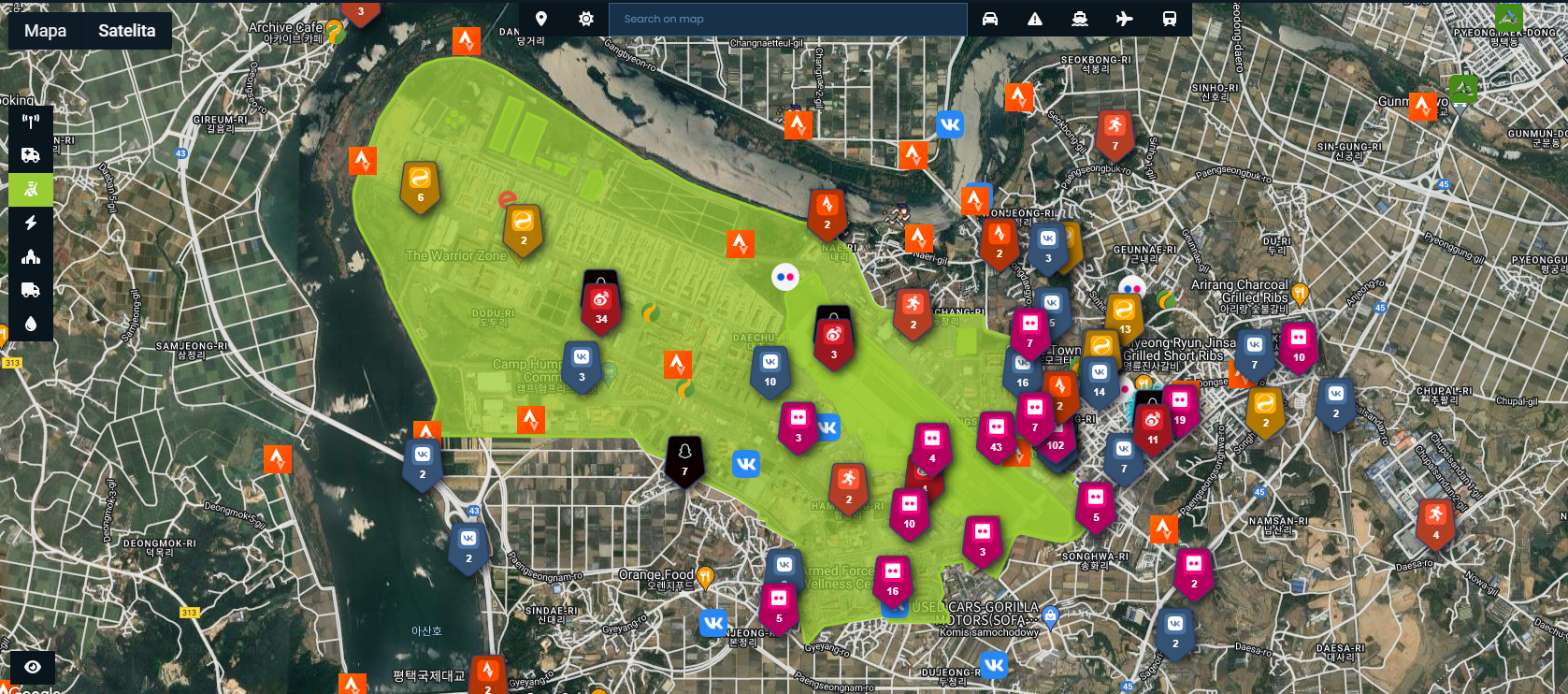
Above you can see results from quick scan of Camp Humphreys in South Korea. There are couple Wikiloc findings, so we can scan one user and get other locations.
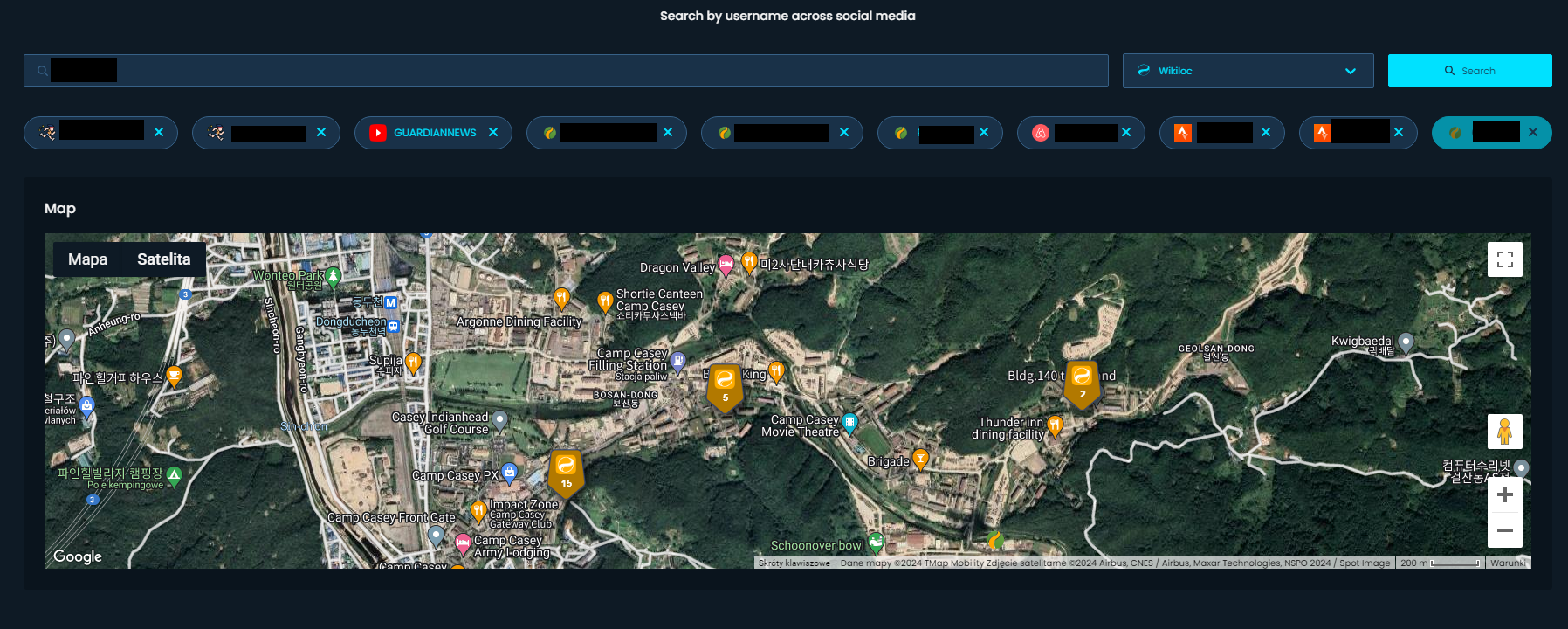
Results were as expected, it's clearly visible, he visited Camp Casey during his trip to South Korea. And now we can scan Camp Casey and get more findings to cross check again and again.
You can try it on
Open Source Surveillance
Real time intelligence gathering tool
 Links Other projects & Social Offensive OSINT
www.offensiveosint.io Kamerka.io
kamerka.io Twitter
@the_wojciech Github
woj-ciech Discord
Offensive OSINT channel
Links Other projects & Social Offensive OSINT
www.offensiveosint.io Kamerka.io
kamerka.io Twitter
@the_wojciech Github
woj-ciech Discord
Offensive OSINT channel

Summary
Open Source Surveillance is not only real-time intelligence gathering product, but also supports HUMINT investigations in different forms. New modules will be implemented soon to make it completely out of the box geo investigation tool, so you won't need to jump from source to source to get relevant data for your research. Stay tuned for more updates.
如有侵权请联系:admin#unsafe.sh