2024-2-21 20:0:0 Author: checkmarx.com(查看原文) 阅读量:12 收藏
-
 By
Yohai West
By
Yohai West
- February 21, 2024
Just as a homeowner might grapple with trying to find the source of a water leak, the challenge of identifying and plugging a leak in code, especially one involving 'secrets' like login credentials, SSH Keys, API Keys, and AWS tokens can be just as frustrating for developers and cybersecurity professionals.
There has been a recent uptick in leaks, most notably Mercedes-Benz and Football Australia, who found themselves as victims in incidents that highlight the need for robust data protection strategies.
The Mercedes-Benz Source Code Exposure
Mercedes-Benz faced a significant breach when an employee inadvertently published a private authentication token on a public GitHub repository, granting unfettered access to the company's source code. This error was discovered by RedHunt Labs during a routine scan in January, revealing that the exposed token provided complete access to Mercedes's GitHub Enterprise Server. This access level meant that anyone with the token could download private repositories containing sensitive data, including intellectual property, cloud access keys for Microsoft Azure and Amazon Web Services (AWS), database connection strings, and other critical internal information.
The Incident at Football Australia
Cybernews researchers reported a significant data leak at Football Australia, where personal information of Australian soccer players (including passports and contracts), as well as customer purchase details, were exposed online. The security breach lasted for at least 681 days and could potentially impact many local customers, with over 100 buckets of data exposed. The exposed data poses a severe threat, with potential for identity theft and fraud.
This cybersecurity incident, attributed to human error, resulted from a leak of secrets from plain-text Amazon Web Services (AWS) keys. This allowed public access to 127 digital storage containers containing sensitive data.
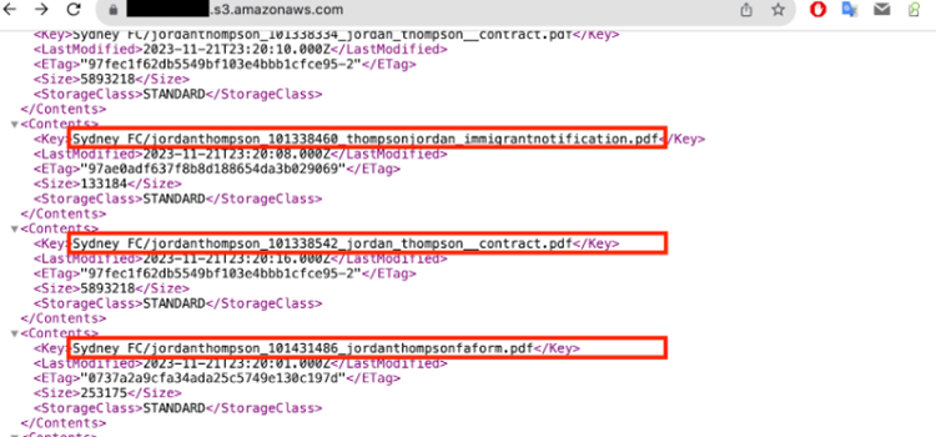
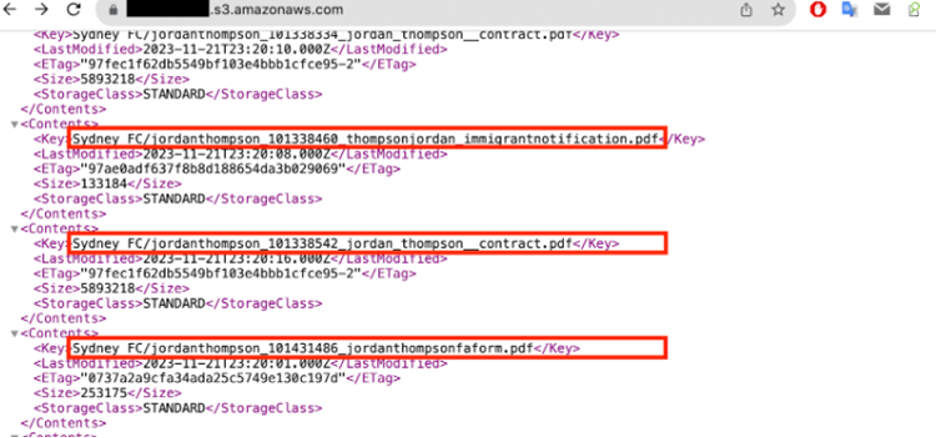
Sample of the exposed data. Image by Cybernews.
Lessons Learned
These incidents serve as potent reminders of the vulnerabilities inherent in digital infrastructures across all sectors. They highlight the need for:
- Enhanced Secret Management: Employing tools and practices that ensure the secure handling of keys and tokens is non-negotiable.
- Regular Security Audits: Proactively scanning for vulnerabilities and exposures can prevent potential breaches.
- Education and Awareness: Human error being a common factor in both cases, underscores the importance of continuous education on best practices for all personnel involved in handling sensitive information.
- Incident Response Planning: Both organizations acted swiftly upon discovery, a testament to the importance of having an effective incident response strategy in place.
The cybersecurity incidents faced by Football Australia and Mercedes-Benz illuminate the critical need for heightened security measures and vigilant management of digital assets. Let these stories be a rallying cry for a unified approach to protecting our digital world—from the pitch to the pavement.
Maintaining the Sanctity of Secrets
To avert the leakage of secrets, consider implementing these strategies:
- Environment Variables for Secrets: Store secrets in environment variables rather than embedding them directly in code to facilitate easier management and prevent their accidental inclusion in version control.
- .gitignore for Sensitive Files: Utilize a .gitignore file to exclude files containing secrets from Git tracking. This ensures that these details do not inadvertently enter version control systems. If using environment variables for secrets, ensure their associated files are also ignored.
- Secrets Management Tools: Employ secrets management tools for the secure handling and storage of system or application secrets. This guarantees encryption and access solely to authorized individuals.
- Encryption of Secrets: Encrypt secrets prior to their storage in code repositories to add a security layer, making it challenging for attackers to obtain sensitive information.
- Two-Factor Authentication (2FA): Activate 2FA for access to code repositories, enhancing security and complicating unauthorized repository access efforts.
These practices can significantly mitigate the risk of inadvertently exposing sensitive information across various platforms, including code repositories, content management systems, emails, and other digital assets not contained within a repository.
Preventing secrets from leaking on external tools with Secrets Detection by Checkmarx
Secrets Detection integrates and expands deeper scanning capabilities of Too many secrets 2MS, a command line tool written in Go language and built over gitleaks, directly into Checkmarx One. 2MS is one of the most popular open-source tools for secret detection, with over 2 million downloads. Secrets Detection in Checkmarx One finds secrets such as login credentials, API keys, SSH keys and more hidden in code, content systems, chat applications and more.
- Supported tools include Confluence, Discord, filesystem, git, paligo, Slack, Git Hooks, GitHub Actions
- Scan history to ensure secrets are not leaked in any previous versions
- Detect secrets that are specific to your company with secret customization
Learn more about reducing the risk of leaked secrets across the supply chain
![]()
Yohai West
As a Senior Product Marketing Manager with over 15 years of experience in enterprise software, I am currently leading product marketing for Checkmarx SSCS (Software Supply Chain Security), and SCA products. My expertise lies in fortifying applications crucial to enterprises' digital transformation and business growth. My journey in the tech world has been marked by significant contributions to the fields of physical security information management, digital intelligence, and software development life cycle (SDLC)/DevOps. As a passionate speaker and content creator, I have had the privilege of producing and hosting podcasts, delivering keynote speeches, and leading numerous thought leadership webinars. These platforms have not only allowed me to share my knowledge but also to stay at the forefront of industry trends and challenges. My focus is to bridge the gap between advanced technology and robust security, making application security an enabler of business growth rather than a hurdle.
![]()
Yohai West
As a Senior Product Marketing Manager with over 15 years of experience in enterprise software, I am currently leading product marketing for Checkmarx SSCS (Software Supply Chain Security), and SCA products. My expertise lies in fortifying applications crucial to enterprises' digital transformation and business growth. My journey in the tech world has been marked by significant contributions to the fields of physical security information management, digital intelligence, and software development life cycle (SDLC)/DevOps. As a passionate speaker and content creator, I have had the privilege of producing and hosting podcasts, delivering keynote speeches, and leading numerous thought leadership webinars. These platforms have not only allowed me to share my knowledge but also to stay at the forefront of industry trends and challenges. My focus is to bridge the gap between advanced technology and robust security, making application security an enabler of business growth rather than a hurdle.
Never miss an update. Subscribe today!
By submitting my information to Checkmarx, I hereby consent to the terms and conditions found in the Checkmarx Privacy Policy and to
the
processing of my personal data as described therein. By clicking submit below, you consent to allow Checkmarx
to store and process the personal
information submitted above to provide you the content requested.
More Resources to Consider
如有侵权请联系:admin#unsafe.sh