2024-2-22 09:0:12 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:34 收藏

Executive Summary
Feb. 13, 2024, ConnectWise was notified of two vulnerabilities impacting their remote desktop software application ScreenConnect. These vulnerabilities were first reported through their vulnerability disclosure channel in the ConnectWise Trust Center.
Feb. 19, 2024, ConnectWise publicly disclosed the vulnerabilities in a security bulletin.
As of Feb. 21, 2024, Unit 42 observed 18,188 unique IP addresses hosting ScreenConnect globally.
The newly disclosed vulnerabilities have now been assigned the following CVEs:
| CVE Number | Description | CVSS Severity |
| CVE-2024-1708 | ScreenConnect 23.9.7 and prior are affected by a path-traversal vulnerability, which may allow an attacker the ability to execute remote code or directly impact confidential data or critical systems. | 8.4 High |
| CVE-2024-1709 | ConnectWise ScreenConnect 23.9.7 and prior are affected by an authentication bypass using an alternate path or channel vulnerability, which may allow an attacker direct access to confidential information or critical systems. | 10.0 Critical |
The authentication bypass vulnerability (CVE-2024-1709) is considered to be trivially exploitable, and proof-of-concept exploits are already available.
We assess with high confidence that this vulnerability will be actively targeted by various types of threat actors, including cybercriminals and nation-state actors, given the severity and scope of the vulnerability and the nature of the impacted product.
Table of Contents
Current Scope of the Attack
Mitigation Actions
Conclusion
Cloud-Delivered Security Services for the Next-Generation Firewall
Cortex XDR and XSIAM
Indicators of Compromise
Current Scope of the Attack
ConnectWise has confirmed that it has “received updates of compromised accounts that our incident response team have been able to investigate and confirm.”
As of Feb. 21, 2024, Unit 42 observed 18,188 unique IP addresses hosting ScreenConnect globally.
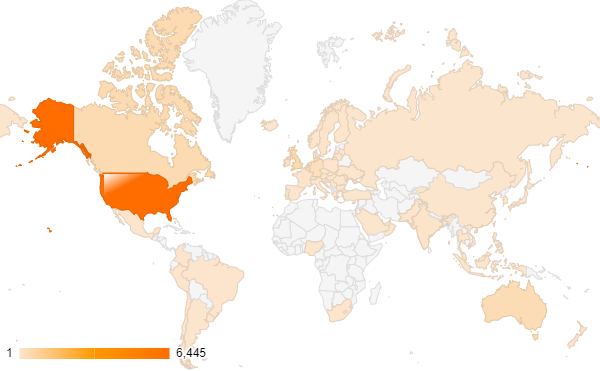
Earlier scans showed that nearly three-quarters of these hosts were in the U.S. The top ten countries accounted for over 95% of global exposure. Our observations are summarized in Figure 1 and Table 1.
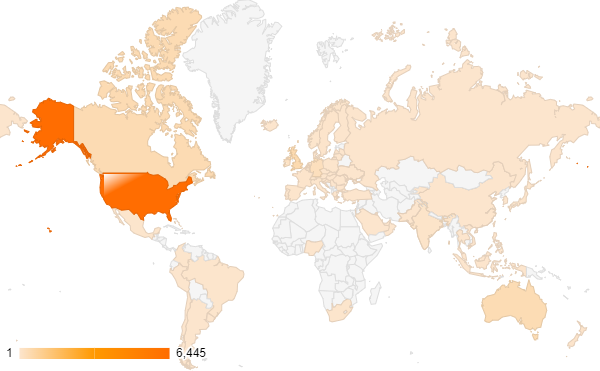
| Top Ten Countries with ConnectWise ScreenConnect Exposure | |
| Country Name | Unique IP Addresses |
| United States | 6,445 |
| United Kingdom | 466 |
| Canada | 407 |
| Australia | 401 |
| Germany | 259 |
| Ireland | 143 |
| Netherlands | 71 |
| India | 57 |
| Singapore | 40 |
| Sweden | 38 |
Table 1. Top ten countries with ConnectWise ScreenConnect exposure.
Mitigation Actions
The ConnectWise bulletin indicates that ScreenConnect servers hosted in screenconnect[.]com cloud or hostedrmm[.]com have been updated to remediate the issue and no end user action is required. For those with self-hosted or on-premise deployments, the guidance is to patch as soon as possible.
Conclusion
Unit 42 will continue to monitor the situation and will update this post as more information becomes available.
Palo Alto Networks customers can leverage a variety of product protections and updates to identify and defend against this threat.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Cloud-Delivered Security Services for the Next-Generation Firewall
Advanced URL Filtering categorizes exploit and scanning attempts as Scanning Activity.
Cortex XDR and XSIAM
Cortex XDR and XSIAM help protect against post-exploitation activities using the multi-layer protection approach.
Cortex Xpanse
Cortex Xpanse has added Attack Surface Rules for both generic ConnectWise ScreenConnect as well as known insecure versions of identified ConnectWise ScreenConnect instances. These rules are also available to XSIAM customers who have purchased the ASM module.
Additionally, Cortex Xpanse has published a new Threat Response Center event for this pair of vulnerabilities.
Indicators of Compromise
ConnectWise has identified the following IoCs, which were recently used by threat actors:
- 155.133.5[.]15
- 155.133.5[.]14
- 118.69.65[.]60
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh