2024-2-23 00:35:43 Author: research.nccgroup.com(查看原文) 阅读量:12 收藏
Author: Zaid Baksh
In the ever-evolving landscape of cyber threats, ransomware remains a persistent menace, with groups like Lorenz actively exploiting vulnerabilities in small to medium businesses globally. Since early 2021, Lorenz has been employing double-extortion tactics, exfiltrating sensitive data before encrypting systems and threatening to sell or release it publicly unless a ransom is paid by a specified date.
Recent investigations by NCC Group’s Digital Forensics and Incident Response (DFIR) Team in APAC have uncovered significant deviations in Lorenz’s Tactics, Techniques, and Procedures (TTPs), shedding light on the group’s evolving strategies.
Key TTP changes:
- New encryption extension – .sz41
- Random strings for file and schedule task names
- Binaries to create local admin accounts for persistence
- Scheduled tasks to conduct enumeration
- New encryption method – DLL – RSA using current time epoch as seed (predictable)
Changing Encryption Extensions
One notable shift observed in Lorenz’s recent activities is a change in their encryption extension. Previously, the group used the extensions ‘Lorenz.sz40’ or ‘.sz40’; however, during the recent compromise, a new extension, ‘.sz41,’ was identified. While seemingly minor, these extensions often serve as the group’s signature, making this change noteworthy. A change in the encryption extension can also indicate a change in the encryption methods being used.
File and Task Naming Conventions
During the investigation, the threat actor preferred the use of randomly generated strings, such as ‘[A-Z]{0-9},’ for file names and scheduled tasks. This includes the ransom note, now named ‘HELP__[A-Za-z]{0-9}__HELP.html,’ in contrast to the previously reported ‘HELP_SECURITY_EVENT.html.’ This demonstrates the group’s adaptability and attempts to subvert known Indicators of Compromise.

Malicious File: Wininiw.exe
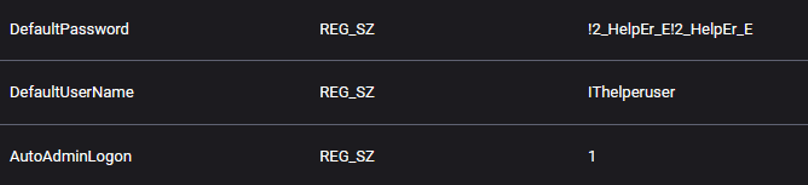
A key discovery during the investigation was the presence of ‘Wininiw.exe’ in the ‘C:\Windows\*’ directory on compromised systems. The threat actor utilized this executable to modify the local Windows Registry, creating a new user with a specified password, and adding it to the Administrator group. Although the threat actor already had Administrator privileges, the creation of a new user may serve as a backup persistence mechanism.

Scheduled Tasks
To conduct enumeration, the threat actor utilized Scheduled Tasks to execute command prompt to run built-in commands. These commands matched previously reported TTPs, and primarily consisted of searching the device for cleartext passwords and dumping the result to C:\Windows\Temp. It is likely the threat actor used Scheduled Tasks to automate enumeration and to ensure their commands were being executed with SYSTEM privileges.

Encryption
We observed the threat actor employing a DLL titled ‘[A-Z]{0-9}.sz41,’ positioned within the ‘C:\Windows\*‘ directory. This DLL was responsible for both the encryption process and the creation of the ransom note. Notably, the encryption technique deviated from previously documented methods.
In this instance, the threat actor employed the current epoch time as a seed for a random number generator, which was subsequently used to generate a passphrase and then derive the encryption key. It is worth noting that this approach introduces a level of predictability to the encryption key if the period during which the encryption occurred is known. The DLL also contained a significant amount of redundant code, which does not execute, indicating this DLL has been iterated upon and possibly customized depending on the victim’s environment.
As ransomware gangs continue to evolve their tactics, organisations must remain vigilant and adapt their cybersecurity strategies accordingly. The recent investigation by NCC Group underscores the importance of continuous monitoring and analysis to stay ahead of ransomware threats. By understanding the evolution of Lorenz’s recent activities, organisations and cyber defenders can be better prepared to identify ransomware precursors and mitigate the risk associated with ransomware groups.
Indicators of Compromise
| IoC | Type |
| “cmd.exe” /Q /C (copy \\<Domain>\NETLOGON\report.txt c:\Windows\WinIniw.exe dir dir start /b c:\Windows\WinIniw.exe dir) | Command |
| cmd.exe /c bcdedit /set {default} safeboot network | Command |
| “cmd.exe” /Q /C dir shutdown /r /t 600 dir | Command |
| “cmd.exe” /Q /C del c:\Windows\Wininiw.exe | Command |
| “cmd.exe” /C dir D:\ /s/b |findstr pass > C:\Windows\Temp\[A-Za-z].tmp 2> 1 | Command |
| “cmd.exe” /C dir D:\ /s/b |grep pass > C:\Windows\Temp\[A-Za-z].tmp 2> 1 | Command |
| “cmd.exe” /C dir C:\Windows\ /s/b |findstr .sz4 > C:\Windows\Temp\[A-Za-z].tmp 2> 1 | Command |
| cmd.exe /c schtasks /Create /F /RU Users /SC WEEKLY /MO 1 /ST 10:30 /D MON /TN “GoogleChromeUpdates” /TR | Command – Scheduled Task within .sz41 DLL |
| Wininiw.exe | Malicious Executable |
| [A-Z]{0-9}.sz41 | Malicious Executable |
| .sz41 | Encryption extension |
| HELP__[A-Za-z]{0-9}__HELP.html | Ransom note |
| IThelperuser | Username |
| !2_HelpEr_E!2_HelpEr_E | Password |
| 165.232.165.215 49.12.121.47 168.100.9.216 174.138.25.242 143.198.207.6 134.209.96.37 | FZSFTP – IP Addresses Port: 443 (HTTPS) |
| 167.99.6.112 | FZSFTP – IP Address Port: 22 (SSH) |
| GoogleChromeUpdates | Scheduled Task Name within .sz41 DLL |
| \[A-Za-z] | Scheduled Task Name |
| lorenzmlwpzgxq736jzseuterytjueszsvznuibanxomlpkyxk6ksoyd[.]onion | Lorenz Darkweb Website |
If you think your organisation may have been compromised reading any of the above indicators, please contact our 24/7 Cyber Incident Response Team immediately to conduct an assessment.
Here are some related articles you may find interesting
Puckungfu 2: Another NETGEAR WAN Command Injection
A story on finding a zero day attacking the NETGEAR WAN interface after a last minute patch for Pwn2Own 2022, involving a command injection, predicting random numbers, boot timing and voltage supply variations.
Public Report: Aleo snarkOS Implementation and Consensus Mechanism Review
In November 2023, Aleo engaged NCC Group’s Cryptography Services team to perform a review of the consensus mechanism implemented by snarkOS: “a decentralized operating system for zero-knowledge applications [that] forms the backbone of Aleo network, which verifies transactions and stores the encrypted state applications in a publicly verifiable manner.” The…
Analyzing AI Application Threat Models
Abstract The following analysis explores the paradigm and security implications of machine learning integration into application architectures, with emphasis on Large Language Models (LLMs). Machine learning models occupy the positions of assets, controls, and threat actors within the threat model of these platforms, and this paper aims to analyze new…
View articles by category
如有侵权请联系:admin#unsafe.sh