2024-2-23 00:8:53 Author: www.malwarebytes.com(查看原文) 阅读量:13 收藏
One of the most alarming trends our ThreatDown Intelligence team has noticed lately is the increased exploitation of legitimate Remote Monitoring and Management (RMM) tools by ransomware gangs in their attacks.
RMM software, such as AnyDesk, Atera, and Splashtop, are essential for IT administrators to remotely access and manage devices within their networks. Unfortunately, ransomware gangs can also exploit these tools to penetrate company networks and exfiltrate data, effectively allowing them to “live off the land”.
In this post, we will delve into how ransomware gangs use RMM tools, identify the most exploited RMM tools, and discuss how to detect and prevent suspicious RMM tool activity using Application Block and Endpoint Detection and Response (EDR).
How ransomware gangs utilize RMM tools
Ransomware gangs exploit Remote Monitoring and Management (RMM) tools through one of three main strategies:
- Gaining initial access via preexisting RMM tools: As RMM tools typically require credentials for system access, attackers can exploit weak or default RMM credentials and vulnerabilities to gain unauthorized access to a network.
- Installing RMM tools post-infection: Once inside a network, ransomware attackers can install their own RMM tools to maintain access and control, setting the stage for a ransomware attack. For example, the ThreatDown Intelligence team noted a case where ransomware attackers exploited an unpatched VMWare Horizon server to install Atera.
- Hybrid approach: Attackers can use a slew of different social engineering scams, such as technical support scams or malvertising, to trick employees into installing RMM tools onto their own machines, enabling both initial access and a mechanism for ransomware deployment. The Barclays banking scam we wrote about in February 2024 is an example of this approach.
Top RMM tools exploited by ransomware gangs
The following RMM tools are commonly used by both ransomware gangs to oversee and control IT infrastructure remotely.
- Splashtop: A remote access and support solution tailored for businesses, MSPs, and educational institutions. Exploited by the ransomware gangs CACTUS, BianLian, ALPHV, Lockbit.
- Atera: An integrated RMM tool for MSPs that offers remote access, monitoring, and management. Exploited by Royal, BianLian, ALPHV.
- TeamViewer: A software for remote access and support. Exploited by BianLian.
- ConnectWise: A suite that includes solutions for remote support, management, and monitoring. Exploited by Medusa.
- LogMeIn: Provides secure remote access to computers from any location for IT management and support. Exploited by Royal.
- SuperOps: An MSP platform that combines RMM, PSA, and other IT management features. Exploited by CACTUS.

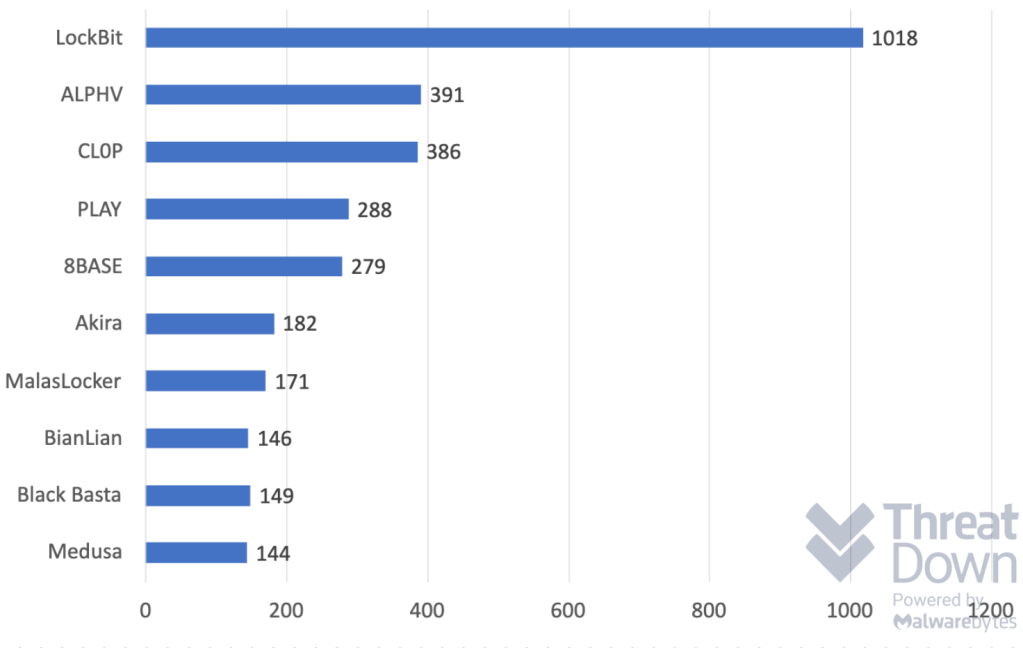
Nearly all of the ten ransomware gangs have included one of the above RMM tools in their attacks.
Preventing RMM ransomware attacks with Application Block and EDR
To prevent ransomware gangs from misusing RMM tools, businesses can adopt two strategies: blocking unnecessary RMM tools using application blocking software and utilizing EDR to detect suspicious RMM tool activity.
For instance, by employing applications like ThreatDown’s Application Block, businesses can prevent the use of non-essential RMM applications.
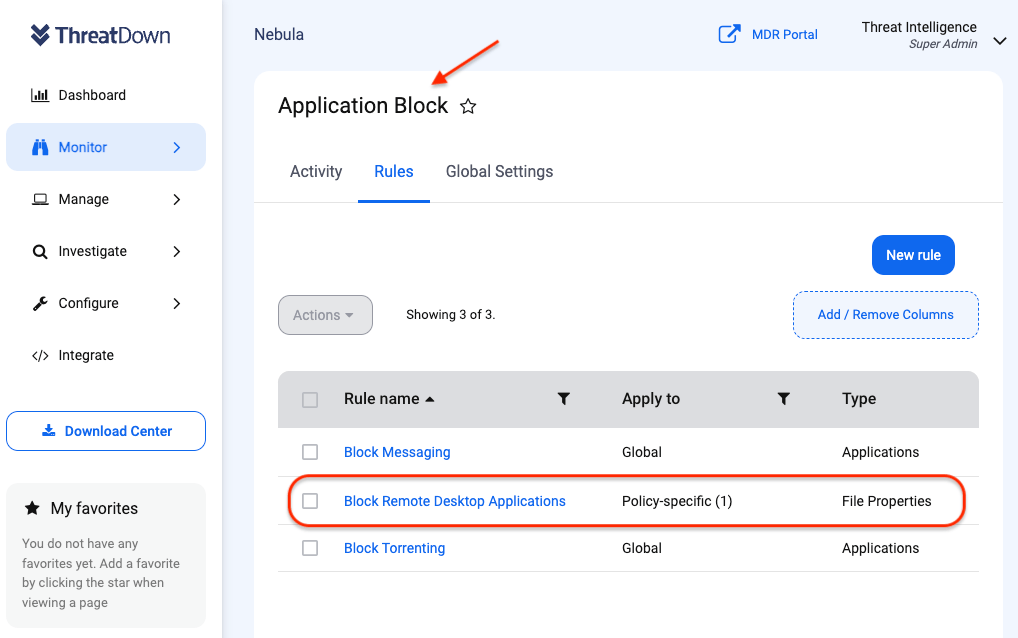
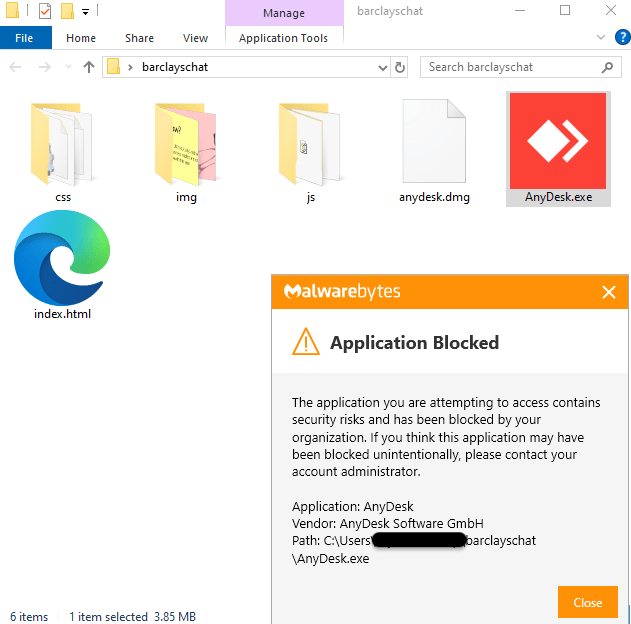
For necessary tools, such as AnyDesk, the EDR/MDR layers within ThreatDown Bundles can offer an additional layer of protection in case of an infection.
Consider a real example where ransomware attackers used AnyDesk to establish a Command and Control (C&C) server. In one case, a threat actor infiltrated a customers environment by exploiting an unpatched server with open ports exposed to the internet. AnyDesk was installed by the threat actor afterward, as indicated in the EDR alert below. Such activity is typical of what our Threat Intel teams observe just before the widespread encryption carried out in ransomware attacks.
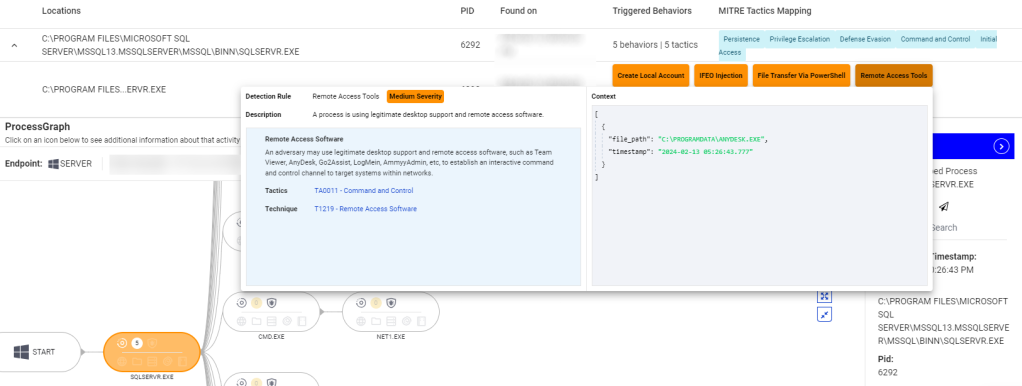
EDR detecting malicious RMM tool usage, with relevant MITRE techniques
After investigating the alert, however, a customer can quickly isolate the affected endpoint to prevent encryption. Alternatively, the ThreatDown MDR service can identify the alert and offer guidance on remediation.
Stop ransomware RMM attacks today
Much like other Living Off the Land tools designed to facilitate IT administration, RMM tools are now double-edged swords.
Whether using RMM tools for initial access, post-infection ransomware deployment, or a combination of the two, ransomware attackers are upping the sophistication of their attacks. However, with ThreatDown, organizations can effectively curtail the abuse of RMM tools through technologies like Application Block and EDR.
Discover the difference with ThreatDown Bundles and elevate your organization’s defense against cyber threats. Get in touch for a free trial and experience the benefits of a simplified, yet robust, security framework.
如有侵权请联系:admin#unsafe.sh