● 背景 ●
诱饵特点
钓鱼诱饵文件名:
2024年1月最新发布-财会人员薪资补贴调整新政策所需材料.exe 2024年最新高级会计工资补助处理手册11.exe 人社部发〔2024〕关于个税调整及社保缴纳比例公布(电脑版).exe 2024关于企业单位调整增值税税率有关政策.exe 财会人员薪资补贴调所需材料.exe 企业税收-优惠政策操作指南.exe 2024年“国家补助”会计福利优惠新政策.exe 2024财会人员薪资补贴通告(密码:321).exe 2024年关于企业员工《社保医保缴纳新规定》最新发布(试行方案).exe 关于24年度企业所得税年度纳税申报有关最新事项【电脑版】.exe】
技术分析
钓鱼样本常见的执行路径是使用MSI文件打包,白加黑启动恶意DLL,将恶意代码注入系统白进程,内存解密shellcode加载,读取并解密非PE文件,从云平台分发payload数据。此外,最近几天发现新型的通过VB实现的木马有所增多,这些VB钓鱼诱饵压缩包文件名称为:
2024年度1月税务稽查局企业随机抽查结果名单公示.zip 2024年新政财会人员薪资补贴调整新政策.zip
文件名 | sha256 |
2024-01-31-N01_U9.exe | c721dcff63c93b673b8cad558a6bac480fdda8f2afe6b11a7d934d6504eea45f |
2024-01-31-N02_U9.exe | ada2ed28ffd92ec3e5a841f33c80e2018d18bfa81f094f4a5d4cc68241702fdd |
2024-02-01-N02_U9.exe | eee35379c2bf0720ba14d44dec51a35c9eb001c19470700d290c2f4a5519ebd4 |
2024-02-02-N02_U9.exe | e99e5d56aba0995e48764b99133e0c1360cde4b22e37cb0390f4e862e8359954 |
2024-02-19-N01_VM_U9.exe | e3d5cd729a76f69c0edb9d16935815a111eb9bd3411caa700b41cbd381018f3a |
2024-02-19-N01_U9_0C.exe | 58f273475f44d4e96b1fe6c3c4303cc5cfaf799a3b21eccf33679d7e8adab71a |
2024-02-19-N01_U9_0B.exe | 7f7ead24ee11357c3b4d94ecdb22db2d5f33dfcf2f9f49efa333429eb620e129 |
2024-02-20-N04_U2.exe | 2c1bc3cf19f05f20ffd95a344a926d7bbe34b9b8d48da525de7a0285f7925c5f |
2024-02-20-N04_U1.exe | 47208f431eaff6c48fa7a0fbe8ba2f51f9e30fbb655b8fe20e96ad1b63ce72bc |
2024-02-20-N03_U1.exe | 7fffa1abe4bc59d4618807143664da1cedb11a2f2e6ca84f5aeb2959b68218e9 |
2024-02-21-N02_U3.exe | 135cc65d046edb27ffe7e809975606131878a19f59123d02ee08738b2b8e4096 |
2024-02-21-N01_U1.exe | 05ff4a08d5169d22841cdf760f53fa8f827b74f871415a926c155e1cba76a21c |
2024-02-21-E01_U1.exe | 9e607c1c32a9d92c27d02fb870a8f78ff9c861ac88c0cb1ce827596a9743c4f2 |
2024-02-21-E01_U3.exe | ec7dc2acd873d9590b99a7d362121f6b8be43bad4e696a3bc062b93dfa27ef18 |
2024-02-21-E01_U2.exe | f106f3f1f2a9bf72d3d0db1c49042f37a72d1a12d2e8386b87808eeaa95a0aa0 |
2024-02-21-E02_U1.exe | 0e50316932582ea06bfe20846ea1fcd70ed2c124078acba90234afff2f7b6ee2 |
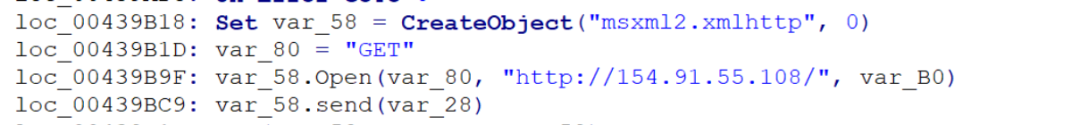
通过反编译后,可以看到请求 154.91.55.108 判断出口IP,判断是否为云机器
查看显卡等硬件信息判断虚拟机环境
通过cmd命令自删除
解密加载shellcode
内存dump出来的shellcode 代码
shellcode连接远程地址38.55.215[.]168
连接端口为7000或者8000
IOC
| a94695b6755b23929c8c3756645b4080179716667f798fadd05f589d59a3aecc |
| d04403c13ae1ae812cff08218c41300d5bcd3cd2b532f107e96cfa75867c38ca |
| fc16df8e342cdd75e408518c460183d2e98307289dbd84ee8fe7cbee5bd82464 |
| abd99bdded3e503e17a1d98e09c9c62501a3a0f0b31b0aa5d30af4ae534a6e85 |
| 8ba965111dc36f29c8729ef8da0cfb15bc7eb8e8074cf9b4594e9142794ccf8d |
| 8a094182f21820ffdb6d7d9d20d6c088f6802ac70f6919f525a99dcbc03793e2 |
| 1ab34bbfe21efd614890012a0b86e189c0b01f3df3215de8f3490c5e4befd494 |
| 62a7c6f6fff5bc6c6686fead338cdf53530be15ae629783a827e517393b56698 |
| 780cfd3e767257881d5f65b5ee7c47f55f7b5f10af61425f14a9dd1c7d6238b0 |
| cb63fe1e934e63e4a78fc3c7a0a9a4c713d757515d4a010412873c6276f3aa4c |
| d04403c13ae1ae812cff08218c41300d5bcd3cd2b532f107e96cfa75867c38ca |
| 7828365c5f984a0c302837b87c7e2d74d732427e62eb5c5d6070748528d4eb42 |
| 99b74d2ae41994fb0c9edd60cbe5f6f8e97ff689c3d3a0c7ff15a1a32f2c88e8 |
| https[:]//ced-oss.oss-cn-shanghai.aliyuncs[.]com/2.dat |
| https[:]//ced-oss.oss-cn-shanghai.aliyuncs[.]com/d.jpg |
| http[:]//oqlap5.2xsi.cn[:]8099/sdfsd23/act[.]rar |
| http[:]//89u1ej.uyg4[.]cn:8099/ts/exehook11.dll |
| 38.55.215[.]168 |
| 122.10.13[.]144 |
| 123.176.98[.]122 |
| 107.151.245[.]85 |
| 122.10.11[.]251 |
| 122.10.10[.]135 |
| 206.238.220[.]75 |
腾讯电脑管家此前已发布的相关分析报告:
产品体验
如有侵权请联系:admin#unsafe.sh