
2024-3-1 22:0:0 Author: www.tenable.com(查看原文) 阅读量:12 收藏
Check out what’s new in NIST’s makeover of its Cybersecurity Framework. Plus, the latest guidance on cyberattack groups APT29 and ALPHV Blackcat. Also, how to assess the cybersecurity capabilities of a generative AI LLM. And the most prevalent malware in Q4. And much more!
Dive into six things that are top of mind for the week ending March 1.
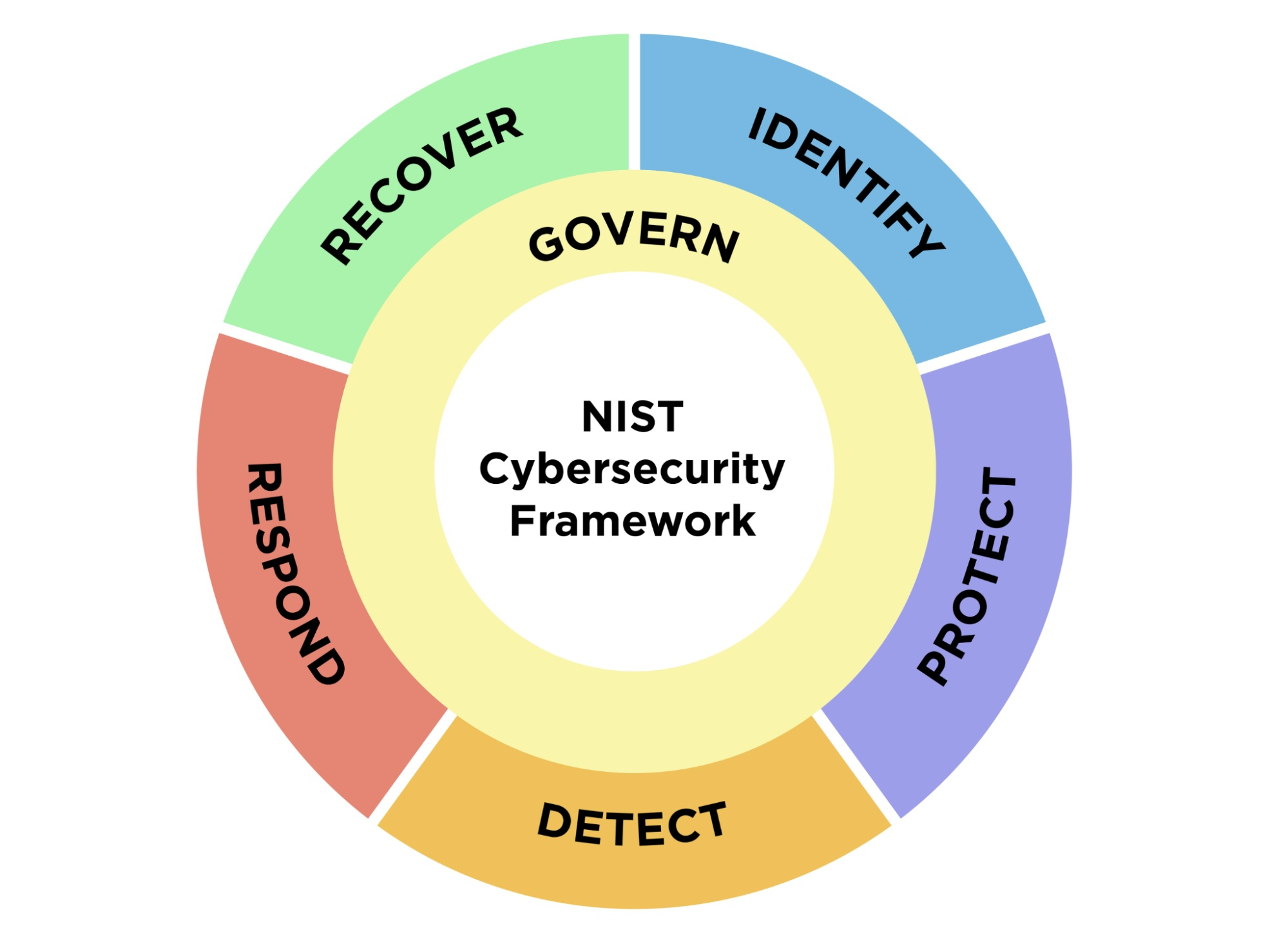
1 - NIST’s Cybersecurity Framework 2.0 places stronger emphasis on governance, features broader scope
The much awaited revamping of the National Institute of Standards and Technology’s (NIST) Cybersecurity Framework (CSF) is finally here.
After a years-long revision process, NIST this week rolled out version 2.0 of the CSF, which is broadly used by organizations to assess, manage and reduce their cybersecurity risks. It’s the first major update to the CSF since version 1.0 came out in 2014.
Key changes from CSF 1.1, released in 2018, include an expanded scope beyond critical infrastructure; stronger emphasis on governance; and more guidance, tools and resources to facilitate its implementation.
Regarding its scope, CSF 2.0 has been crafted to have broad relevance and usefulness for all organizations globally – regardless of size, type, industry sector and cybersecurity sophistication. Initially, the CSF specifically focused on helping critical infrastructure organizations.
“CSF 2.0, which builds on previous versions, is not just about one document. It is about a suite of resources that can be customized and used individually or in combination over time as an organization’s cybersecurity needs change and its capabilities evolve,” NIST Director Laurie E. Locascio said in a statement about CSF 2.0.
Meanwhile, CSF 2.0’s new “Govern” function addresses areas such as risk management strategy; organizational context; supply chain risk; and policies, processes and procedures.
“The CSF’s governance component emphasizes that cybersecurity is a major source of enterprise risk that senior leaders should consider alongside others such as finance and reputation,” reads NIST’s statement.
CSF 2.0’s five other functions are:
- Identify, focused on assessing an organization’s cyber risk
- Protect, about adopting measures to prevent and reduce cyber risk
- Detect, centered on discovering and analyzing cyberattacks and breaches
- Respond, devoted to taking action after a cyber incident
- Recover, focused on the restoration of impacted assets and operations
To make it easier for a wide variety of organizations to adopt CSF 2.0, NIST has created quick-start guides tailored for specific audiences; case studies about successful implementations; and a searchable catalog of references.
To get more details, check out commentary and analysis about CSF 2.0 from CSO Magazine, The Register, SC Magazine and Help Net Security, as well as the videos below.
The Cybersecurity Framework at 10...and Beyond (The Aspen Institute)
NIST Cybersecurity Framework 2.0 - What Changed? (Optic Cyber)
2 - Study: How to evaluate a GenAI LLM’s cyber capabilities
From the moment OpenAI’s ChatGPT became a global sensation, cybersecurity pros have explored whether and how generative AI tools based on large language models (LLMs) can be used for cyber defense.
All along, a core question has been: How do you test and evaluate an LLM’s cybersecurity capabilities and risks? Well, researchers from OpenAI and Carnegie Mellon University (CMU) tackled this question and just published a study outlining specific assessment criteria.
In their paper “Considerations for Evaluating Large Language Models for Cybersecurity Tasks,” the authors state that current assessment methods fall short, because they focus on evaluating LLMs’ factual knowledge by, for example, having them take a cybersecurity certification exam.

“Fundamentally, we argue that practical, real-world evaluations are necessary to understand the cyber capabilities of LLMs; fact-based examinations are insufficient,” they wrote.
The paper covers the following areas:
- The nature of cybersecurity tasks and the pros and cons in using LLMs to perform them
- The way LLMs capture and apply cybersecurity knowledge
- How specific cybersecurity tasks can be supported by LLMs
- Recommendations to help cybersecurity pros evaluate LLMs’ cyber capabilities
Some of the recommendations include:
- Define the real-world task that the evaluation should capture by considering, for example, how humans do it and listing the steps involved
- Represent tasks in a way that captures their real-world nuance and complexity by, for example, defining their scope appropriately
- Design and perform rigorous assessments by, for example, modifying and varying input queries by changing words, altering phrases and introducing misspellings
“Understanding how an LLM performs on real cybersecurity tasks will provide policy and decision makers with a clearer sense of capabilities and the risks of using these technologies in such a sensitive context,” the authors wrote.
To get more details, check out:
- The blog “OpenAI Collaboration Yields 14 Recommendations for Evaluating LLMs for Cybersecurity”
- The research paper “Considerations for Evaluating Large Language Models for Cybersecurity Tasks”
For more information about the use of generative AI LLMs for cybersecurity:
- “6 ways generative AI chatbots and LLMs can enhance cybersecurity” (CSO)
- “How generative AI will enhance cybersecurity in a zero-trust world” (VentureBeat)
- “AI Is About To Take Cybersecurity By Storm: Here's What You Can Expect” (Tenable)
- “Generative AI making big impact on security pros, to no one’s surprise” (CSO)
- “Using generative AI to strengthen cybersecurity” (KPMG)
VIDEO
Practical Applications for Generative AI in Cybersecurity (OWASP)
3 - CISA, NCSC issue cloud security advisory on Russia-backed APT29
Cloud security teams, listen up: APT29, the notorious cybercrime group sponsored by the Russian Foreign Intelligence Service (SVR), is shifting its attention to cloud computing environments.
So said cyber agencies from Australia, Canada, New Zealand, the U.K. and the U.S. this week in the joint advisory “SVR Cyber Actors Adapt Tactics for Initial Cloud Access.” The advisory details tactics, techniques and procedures (TTPs) observed over the past 12 months, along with detection and mitigation recommendations.
“As organizations continue to modernize their systems and move to cloud-based infrastructure, the SVR has adapted to these changes in the operating environment,” reads the 8-page document.
APT29, also known as the Dukes, CozyBear and Nobelium/Midnight Blizzard, was responsible for the SolarWinds supply chain attack and other high-profile hacks against targets including Microsoft and Hewlett-Packard Enterprise.
These are some of the TTPs used by APT29:
- Using brute forcing and password spraying to access service accounts, which are used to run and manage applications and services
- Compromising dormant accounts that haven’t been deactivated although they belong to users who no longer work at the targeted organization
- Using valid, unexpired tokens to access accounts
Recommended mitigations include:
- Use multi-factor authentication and require strong, unique passwords
- Have a process in place for identifying and disabling accounts from users who are no longer with the organization
- Apply the principle of least privilege to service accounts, so that their scope of access to resources is limited
- Keep user sessions as short as is practical, so that attackers have less of a chance of using stolen session tokens
To get more details about APT29:
- APT29 (MITRE)
- “Russian hackers breached Microsoft, HPE corporate mailboxes” (Help Net Security)
- “CISA: Russian hackers target TeamCity servers since September” (BleepingComputer)
- “Hackers backed by Russian government reportedly breached US government agencies” (The Verge)
- “Russia’s APT29 intensifies espionage operations” (SC Magazine)
4 - A Tenable poll on identity security challenges and strategies
During our recent webinar “Securing Identities Across Your Entire Attack Surface,” we polled attendees about various aspects of their identity security strategy. Check out what they said about their biggest challenges, their approach and more.
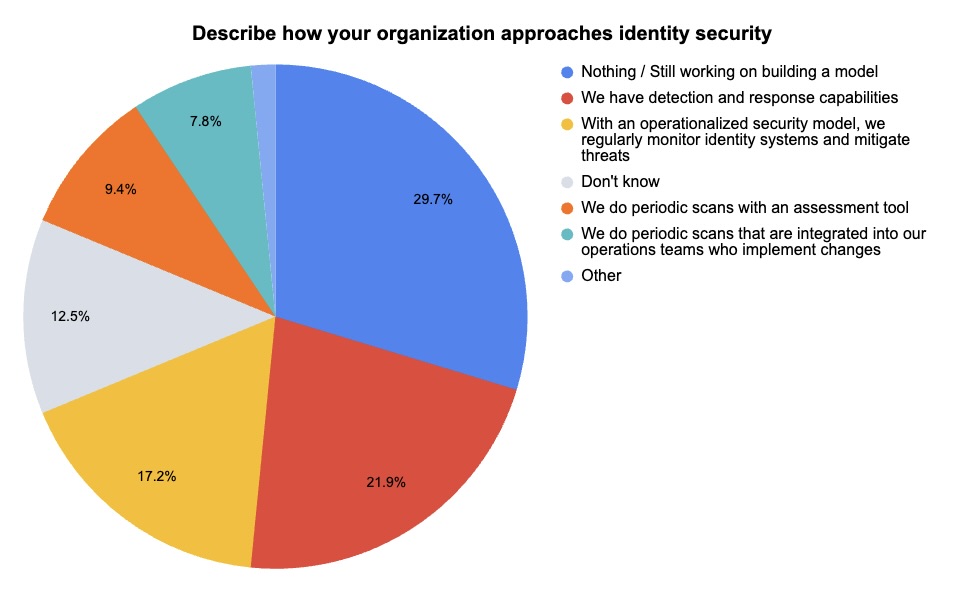
(64 respondents polled by Tenable, February 2024)
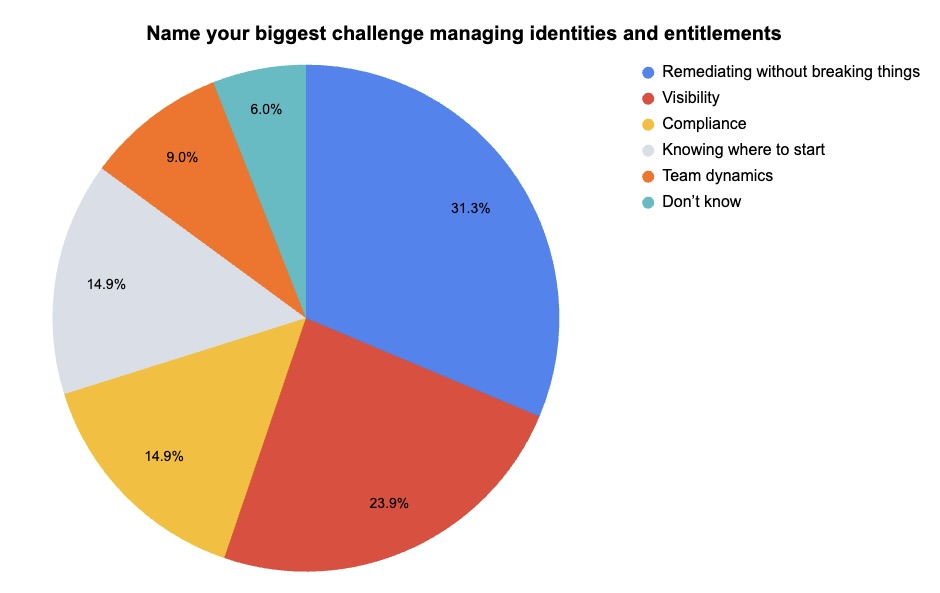
(67 respondents polled by Tenable, February 2024)
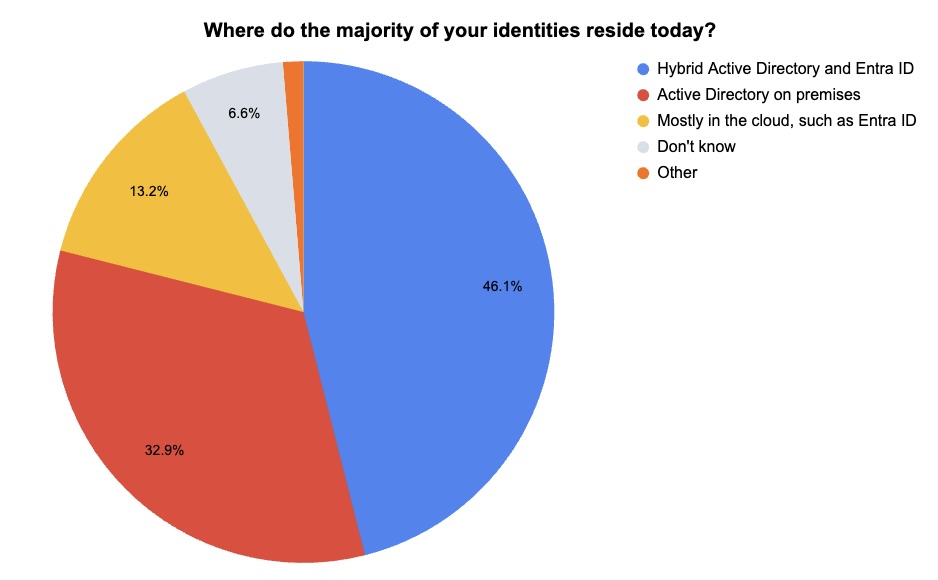
(76 respondents polled by Tenable, February 2024)
Want to learn about the nuances of identity risk management across multi-cloud and on-prem environments? Watch the on-demand webinar “Securing Identities Across Your Entire Attack Surface.”
5 - U.S. updates guidance on ALPHV Blackcat, warns healthcare orgs
The U.S. government is alerting healthcare companies in particular about the threat from the ALPHV Blackcat ransomware-as-a-service (RaaS) group, which this week claimed responsibility for an attack against Change Healthcare.
In an updated joint advisory, CISA, the FBI and the Department of Health and Human Services (HHS) released new indicators of compromise (IOCs), as well as tactics, techniques, and procedures (TTPs) associated with ALPHV Blackcat. The advisory also includes recommendations for mitigation and incident response.
About two months ago, the FBI announced it had disrupted ALPHV Blackcat’s operations, but the ransomware gang has regrouped and has been causing mayhem recently.
To gain initial access, cybercriminals associated with ALPHV Blackcat employ advanced social engineering techniques and publicly-available information about a company.
“Actors pose as company IT and/or helpdesk staff and use phone calls or SMS messages to obtain credentials from employees to access the target network,” the advisory reads.
Mitigation advice includes:
- Maintain a regularly updated inventory of IT assets and data to identify authorized and unauthorized devices and software
- Prioritize remediating known exploited vulnerabilities
- Secure remote access tools by implementing application controls, such as allowlisting remote access programs
- Adopt phishing-resistant multi-factor authentication
- Train staff on social engineering attacks, such as how to identify suspicious emails
To get more details, read the updated advisory “#StopRansomware: ALPHV Blackcat.”
For more information about ALPHV Blackcat:
- “Russian Ransomware Gang ALPHV/BlackCat Resurfaces with 300GB of Stolen US Military Documents” (CPO Magazine)
- “FBI hits ALPHV/Blackcat ransomware gang” (Tenable)
- “Prudential Financial, loanDepot attacks admitted by ALPHV/BlackCat” (SC Magazine)
- “US Government Warns Healthcare is Biggest Target for BlackCat Affiliates” (Infosecurity Magazine)
- “Feds post $15 million bounty for info on ALPHV/Blackcat ransomware crew” (The Register)
6 - SocGholish tops list of Q4 malware incidents
SocGholish, a malware variant used in fake browser attacks, accounted for most malware incidents in the fourth quarter.
In these attacks, users are tricked into installing what they think is a legitimate browser update that in reality is malware that infects their computers.
SocGholish accounted for 60% of all malware incidents observed by the Center for Internet Security (CIS), which this week released its “Top 10 Malware Q4 2023” list.
It’s been a meteoric rise for SocGholish, which first cracked the CIS list in the third quarter, with a 31% share of malware incidents.
Fake browser update attacks also propelled the RogueRaticate malware variant into the CIS list for the first time in the third quarter. It again ranked in the top 10 in the fourth quarter.
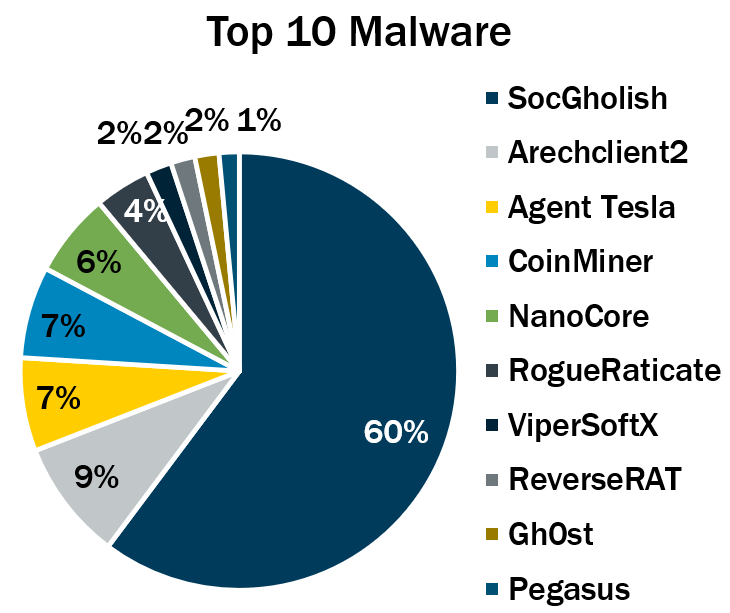
(Source: Center for Internet Security, February 2024)
Here’s the full list, in descending order:
- SocGholish, a downloader distributed through malicious websites that tricks users into downloading it by offering fake software updates
- Arechclient2, also known as SectopRAT, is a .NET remote access trojan (RAT) whose capabilities include multiple stealth functions
- Agent Tesla, a RAT that captures credentials, keystrokes and screenshots
- CoinMiner, a cryptocurrency miner that spreads using Windows Management Instrumentation (WMI)
- NanoCore, a RAT that spreads via malspam as a malicious Excel spreadsheet
- RogueRaticate, a downloader distributed through malicious or compromised websites using fake browser updates.
- ViperSoftX, a multi-stage crypto stealer that's spread within torrents and file sharing sites
- ReverseRAT, a RAT that lets hackers breach a compromised system and that’s often used to steal information and to spy on victims
- Gh0st, a RAT designed to control infected endpoint devices
- Pegasus, spyware that steals data from iOS and Android devices
To get more information, check out the CIS blog report, which offers details, context and indicators of compromise for each malware strain.
For details on fake browser update attacks:
- “The Fake Browser Update Scam Gets a Makeover” (Krebs on Security)
- “Atomic Stealer malware strikes macOS via fake browser updates” (Bleeping Computer)
- “Hackers Use Fake Browser Updates for AMOS Malware Attacks Targeting Mac Users” (MSSP Alert)
- “New ‘Big Head’ ransomware displays fake Windows update alert” (Bleeping Computer)
- “Hackers have been spreading malware via fake Chrome updates” (TechRadar)
VIDEOS
Fake Chrome Update Malware (The PC Security Channel)
Apple Mac OS users falling for fake browser update that installs malware (Windows, Computers and Technology)

Juan Perez
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
如有侵权请联系:admin#unsafe.sh