Background and key points
- TeaBot is an Android banking trojan emerged at the beginning of 2021 designed for stealing victim’s credentials and SMS messages
- TeaBot RAT capabilities are achieved via the device screen’s live streaming (requested on-demand) plus the abuse of Accessibility Services for remote interaction and key-logging. This enables Threat Actors (TAs) to perform ATO (Account Takeover) directly from the compromised phone, also known as “On-device fraud”.
- Initially TeaBot has been distributed through smishing campaigns using a predefined list of lures, such as TeaTV, VLC Media Player, DHL and UPS and others.
- Recent samples show how TAs are evolving their side-loading techniques, including the distribution of applications on the official Google Play Store, also known as “dropper applications”.
- In the last months, we detected a major increase of targets which now count more than 400 applications, including banks, crypto exchanges/wallets and digital insurance, and new countries such as Russia, Hong Kong, and the US (Figure 1).
The following article is a major update of the previous TeaBot: a new Android malware emerged in Italy, targets banks in Europe published in May, 2021 in our blog “Cleafy Labs”.

How TeaBot is evolving its distribution
One of the most interesting aspects of the TeaBot’s distribution are the latest techniques implemented on its campaigns. During 2021, TeaBot appeared to be at its early stages of development and it was mainly distributed through smishing campaigns using a predefined list of lures, such as TeaTV, VLC Media Player, DHL and UPS and others.
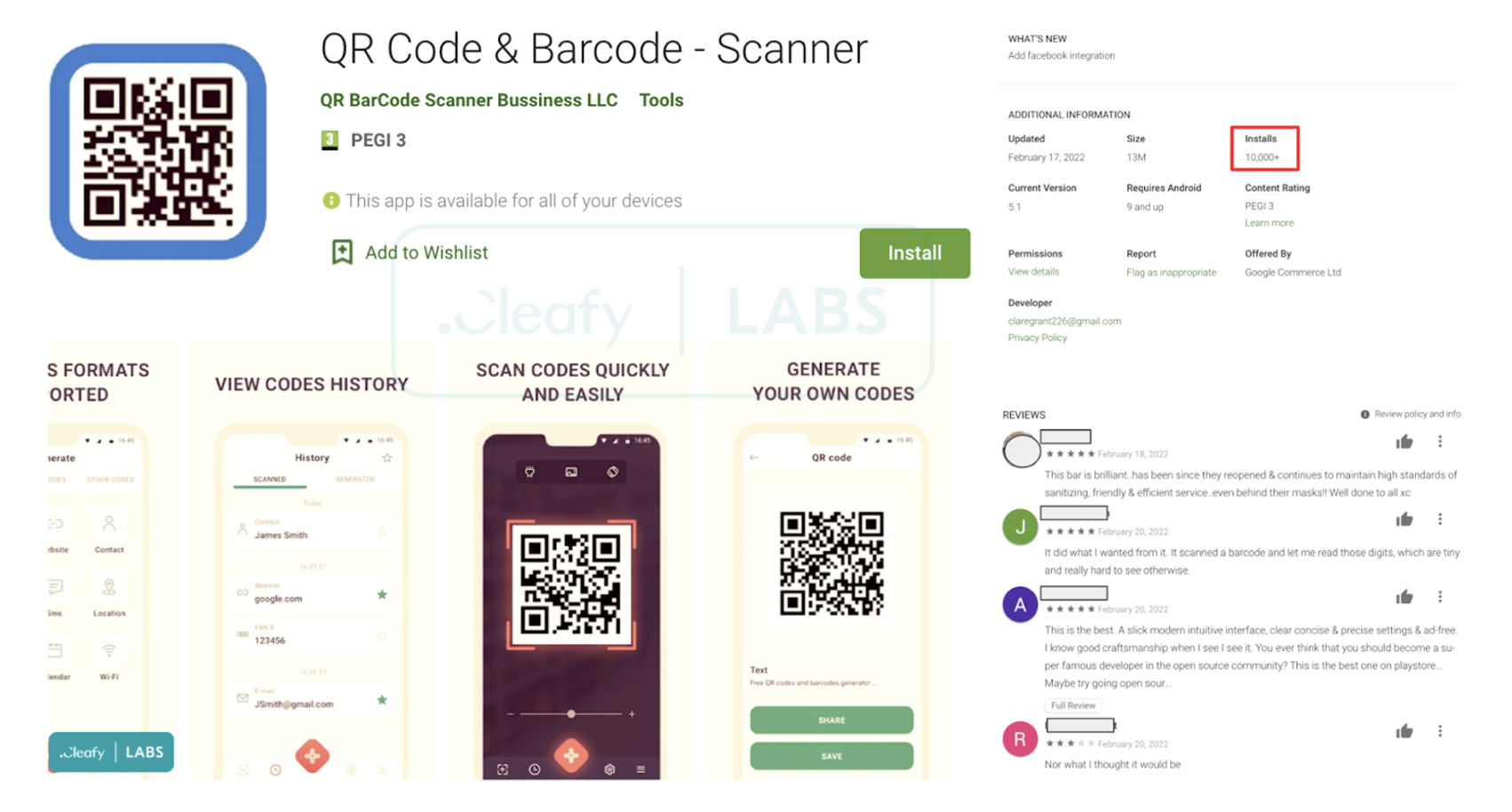
On February 21, 2022, the Cleafy Threat Intelligence and Incident Response (TIR) team was able to discover an application published on the official Google Play Store, which was acting as a dropper application delivering TeaBot with a fake update procedure. The dropper lies behind a common QR Code & Barcode Scanner and, at the time of writing, it has been downloaded +10.000 times. All the reviews display the app as legitimate and well-functioning.

However, once downloaded, the dropper will request immediately an update through a popup message. Unlike legitimate apps that perform the updates through the official Google Play Store, the dropper application will request to download and install a second application, as displayed in Figure 3. This application has been detected to be TeaBot.

TeaBot, posing as “QR Code Scanner: Add-On”, is downloaded from two specific GitHub repositories created by the user feleanicusor. It has been verified that those repositories contained multiple TeaBot samples starting from Feb 17, 2022:

The following graph will give you an overview of the actual infection chain developed by TAs and how they are improving their sideloading technique for distributing TeaBot, starting from a dropper application spreaded via the official Google Play Store and abusing Github service for hosting the actual malicious payload:

Once the users accept to download and execute the fake “update”, TeaBot will start its installation process by requesting the Accessibility Services permissions in order to obtain the privileges needed:
- View and control screen: used for retrieving sensitive information such as login credentials, SMS, 2FA codes from the device’s screen.
- View and perform actions: used for accepting different kinds of permissions, immediately after the installation phase, and for performing malicious actions on the infected device.

New targets, new evasion techniques
One of the biggest difference, compared to the samples discovered during the May 2021 [1], is the increase of targeted applications which now include home banking applications, insurances applications, crypto wallets and crypto exchanges. In less than a year, the number of applications targeted by TeaBot have grown more than 500%, going from 60 targets to over 400.

During the last months, TeaBot has also started supporting new languages, such as Russian, Slovak and Mandarin Chinese, useful for displaying custom messages during the installation phases.

Moreover, it has been observed that TAs have been working on the sophistication of evasion techniques, such as string obfuscation, used both for preventing a smooth static analysis, and for further lowering the detection rate by anti-malware solutions available on the market. An example of the new evasion techniques introduced in recent TeaBot samples is given in Figure 9.

It is also clear how the deobfuscation routine works: each class has been paired with a short array that is filled with pseudo-random codes. It is then manipulated by a function that uses those codes to perform an XOR operation on its input and then returns the actual string.
Since the dropper application distributed on the official Google Play Store requests only a few permissions and the malicious app is downloaded at a later time, it is able to get confused among legitimate applications and it is almost undetectable by common AV solutions.

[1] https://www.cleafy.com/cleafy-labs/teabot
Appendix 1: IOCs
| IoC | Description |
|---|---|
| QR Code & Barcode - Scanner | App Name (TeaBot dropper) |
| https://play.google[.]com/store/apps/details?id=com.scanner.buratoscanner | Link Google Play Store (TeaBot dropper) |
| 104046f5cf2fb5560acf541d4f9f6381 | MD5 (TeaBot dropper) |
| QR Code Scanner: Add-On | App Name (TeaBot) |
| com.nnawozvvi.pamwhbawm | Package Name (TeaBot) |
| bf2ddaf430243461a8eab4aa1ed1e80d | MD5 (TeaBot) |
| https://github[.]com/leroynathanielxnlw | GitHub repository (proxy) |
| https://github[.]com/feleanicusor | GitHub repository (hosting multiple TeaBot samples) |
| 185[.]215[.]113[.]31 | C2 Server |
如有侵权请联系:admin#unsafe.sh