Key point
- On January 2023, a new Android banking trojan appeared on multiple hacking forums under the name of Nexus. However, Cleafy’s Threat Intelligence & Response Team traced the first Nexus infections way before the public announcement in June 2022.
- Nexus is promoted via a Malware-as-a-Service (MaaS) subscription a particular type of cybercrime in which malware creators or distributors provide their services to other criminals or individuals on a rental or subscription basis. Developers offer their services on underground forums or through private channels (e.g., Telegram), and their clients pay a fee to use the malware.
- Nexus appears to be in its early stages of development (BETA). Multiple campaigns active worldwide confirm that multiple TAs are already using this thread to conduct fraudulent campaigns.
- Nexus provides all the main features to perform ATO attacks (Account Takeover) against banking portals and cryptocurrency services, such as credentials stealing and SMS interception. It also provides a built-in list of injections against 450 financial applications.
- Despite Nexus being promoted as a brand-new malware, it contains some relations with the SOVA banking trojan, suggesting that developers adopted and reused old developments.
Introduction
At the beginning of January 2023, a new Android banking botnet named Nexus was promoted by a user on multiple underground hacking forums. The following image represents the original thread promoted by the author:

Following the discussion, the authors claim that the source code of Nexus has been entirely written from scratch, but it is still in its early development days. Despite this, the authors behind Nexus announced that it was already available for rent at a steep price of $3000 per month through a MaaS subscription. MaaS stands for Malware-as-a-Service, and it is a model used in the cybercrime world to offer their malware for rent or sale to other TAs who lack the technical expertise to develop their malware.
This model is prevalent in Android banking trojans, where malware authors use MaaS platforms to distribute their malware to a broader audience. The MaaS model allows criminals to monetize their malware more efficiently by providing a ready-made infrastructure to their customers, who can then use the malware to attack their targets.
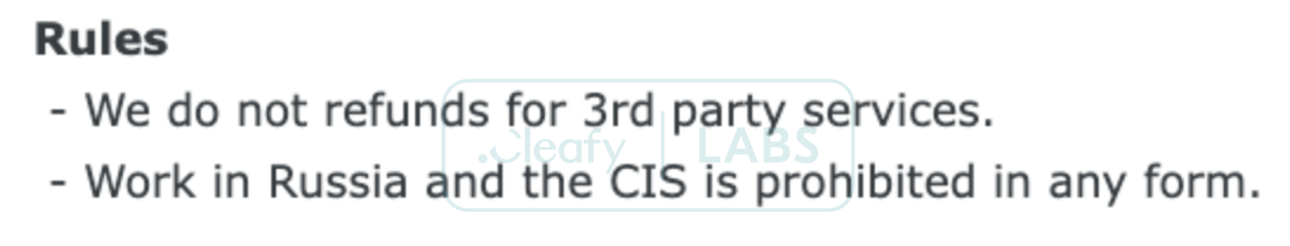
It is common for MaaS providers to impose restrictions on the geographies where their customers can conduct attacks using rented or purchased malware. The Nexus authors, for example, have a "code of conduct" rule prohibiting using their malware in Russia and CIS countries.

Previous activities and linking with SOVA
Despite the official launch of the Nexus MaaS program on 27th January 2023, our internal telemetries identified previous related activities behind this botnet, as shown in the following Figure:

On August 2022, during the analysis of those samples, technical indicators suggested some code similarity between Nexus samples and SOVA, an Android banking trojan emerged in mid-2021. At that time, it was considered a new variant of SOVA, as described in our previous blog article.
Despite the new MaaS program launched under the name Nexus, the authors may have reused some parts of SOVA internals, to write new features (and rewrite some of the existing ones).
Recently, the SOVA author, who operates under the alias “sovenok”, started sharing some insights on Nexus and its relationship with SOVA, calling out an affiliate who previously rented SOVA for stealing the entire source code of the project.

This event could explain why parts of the SOVA source code have been passing through multiple banking trojans. In fact, sovenok identified another Android botnet that operates under the name of POISON, which he considers to be highly linked to Nexus:

Focusing on technical indicators, the following Figure shows the overlap found between the commands on SOVA and Nexus. As a result, it appears that most of the SOVA commands (marked in green) were also reused on Nexus:

Another similarity between Nexus and SOVA is how geographic location is checked. Analyzing the bootstrap of the infection, it was possible to discover that Nexus implements a function called preloadCheck() to identify if the victim is actually in a country “allowed” to be attacked. If the check succeeds, it starts the infection chain. Otherwise, the application simply terminates the activity.

Currently, countries that are ignored are: AZ (Azerbaijan), AM (Armenia), BY (Belarus), KZ (Kazakhstan), KG (Kyrgyzstan), MD (Moldova), RU (Russian Federation), TJ (Tajikistan), UZ (Uzbekistan), UA (Ukraine), ID (Indonesia).

Moreover, another routine is deployed to discern if the victim is eligible to become part of the botnet. In this case, the attackers try to verify if the official Sberbank (Russia's biggest bank) application is installed.

Lastly, there are many APIs similarities used by both SOVA and Nexus to communicate with the C2 server, as confirmed by sovenok.

Technical Analysis: Main features and Commands
Nexus contains all the main features to perform Account Takeover attacks (ATO) against banking apps from all over the world and cryptocurrency services. In particular, it can:
- Perform Overlay attacks and keylogging activities to steal users' credentials.

- Steal SMS messages to obtain the two-factor authentication codes.
- Through the abuse of the Accessibility Services, Nexus can steal some information from crypto wallets (such as seeds and balance), the 2FA codes of Google Authenticator app, and the cookies from specific websites.
Comparing the list of commands of two Nexus samples (one from August 2022 and one from March 2023), it is possible to note the addition of some new commands, such as the ability to remove received SMS and the feature to activate or stop the 2FA stealer module.
The following evidence, in addition to some claims by the Nexus author concerning the possibility of adding a VNC module, underlines the desire to further improve the malware with new features.

Update Capacity
Nexus is also equipped with a mechanism for autonomous updating. A dedicated function asynchronously checks against its C2 server for updates when the malware is running. More specifically, it performs a check towards a dedicated endpoint asking for the last version; the query look like the following line:
http(s)://C2_domain/lastversion?access=XXXXX&key=XXXXXXXX
If the value sent back from the C2 does not correspond to the one installed on the device, the malware starts the update process. Otherwise, it ignores the value and continues with all its routine activities. The update begins concatenating the URL related to the C2 and a key that will be used as an authorization token.

At the time of writing, the version available is related to the build 7.20.

Analysts could use the “key” value to keep track of different custom versions of Nexus, it was possible to identify a slightly modified version of the malware for each key. This suggests that more actors are renting customized samples that aim to hit specific targets and countries.

Ransomware module?
According to the information retrieved from various samples, Nexus is equipped with encryption capabilities. However, this module seems to be under development due to the presence of debugging strings and the lack of usage references (especially within the C2 command list).
However, we can’t exclude that this function is a “typo” associated with the cut-and-paste activities that seem to involve many parts of the code.

It is reasonable to ask why this encryption paradigm has been implemented. An explanation could be found in an attempt of making it harder for the user to realize what happened. A similar approach, even more destructive, has been used by Brata, where TAs adopted the strategy of factory resetting the device right after an unauthorized wire transfer attempt to reduce the evidence.
According to our experience, it’s also hard to think about a ransomware modus operandi on mobile devices since most information stored is synced with cloud services and easily recoverable. In fact, as confirmed by sanovek it started to design a ransomware capability in SOVA, but it was pointless for a banking trojan on mobile devices.

Noisy Logs
Another interesting characteristic of Nexus that strengthens the hypothesis of its development stage is the number of logging messages spread throughout the code. Those messages are intended to track all actions performed, and some of them are paired with a debugging string that contains the message “plz report this accident”.

Logging messages are not limited to local devices. In fact, it was possible to discover that most of the messages are also intended to be sent over the C2 communication channel. The message should follow this syntax: [ botId : Log Message]. However, at the time of writing, due to the lack of references to the variable botID related to the logging class, this capability still seems to be in the development phase.
C2 web panel
Once Nexus is installed on a victim's device, it connects to its C2 server. This server is used by TAs to remotely control the malware, issue commands, and receive stolen data.
Nexus provides a C2 web panel, which is an essential tool for cyber criminals who are using malware or a botnet to carry out attacks. It provides a centralized interface for managing the malware and the data it collects, making it easier for attackers to carry out their malicious activities.
Typically Nexus C2 web panels expose the login page on the Internet through port 80 or 5000 as follows:

The string “Jojo no Kimyou na Bouken: Eyes of Heaven” references an action video game based on the “Jo Jo's Bizarre Adventure” manga series by Hirohiko Araki, a Japanese manga artist.
Once logged in, the panel offers the following features:
- Dashboard: displays the status of the botnet, including the number of infected devices, data collected, and any recent activity.
- Bots: a detailed list of the infected devices, locations, and other metrics.
- Data Collection: tools for collecting and analyzing data from infected devices. This includes login credentials, cookies, credit card details, and other sensitive information.
- Injects: a comprehensive list of 450 banking application login pages for grabbing valid credentials.
- Builder: interface for creating customized versions of Nexus, allowing TAs to customize various aspects, such as the command-and-control server (C&C) address, the icon and name of the app, and more.


As the alleged author claimed on multiple hacking forums, the complete list of injections has 450 different targets, which are searchable through the panel. They also offer the possibility to create custom injections.

Pivoting C2 fingerprints through Internet search engines, such as Shodan, could provide excellent information, and in this case, it confirms that the growing trend began in the very first of 2023 when Nexus was officially promoted on multiple hacking forums:

Conclusion
Nexus is an emerging malware that allegedly has taken more than a few “ideas” from SOVA (a threat that hit the international landscape in the last year). According to the similarities observed in the code, and the insights retrieved from underground forums, it is possible to confirm that Nexus represents a new malware, guided by an entirely new group, which was capable of retrieving parts of SOVA source code after they were stolen by an Android botnet operator called POISON.
By analyzing the latest retrieved samples, we can say that Nexus is still in an early stage of development, still including snippets of code that seem to belong to its ancestor.
As always, the main question here is: Does it represent a threat to Android users?
At the time of writing, the absence of a VNC module limits its action range and its capabilities; however, according to the infection rate retrieved from multiple C2 panels, Nexus is a real threat that is capable of infecting hundreds of devices around the world. Because of that, we cannot exclude that it will be ready to take the stage in the next few months.
Appendix 1: IOCs
| IoC | Description |
|---|---|
| d4c6871dbd078685cb138a499113d280 | MD5 of Nexus |
| 193.42.32.]87 | C2 |
| 193.42.32.]84 | C2 |
Meet the authors
Francesco Iubatti - Mobile Malware Analyst & Threat Intelligence Analyst.
Federico Valentini - Head of Threat Intelligence and Incident Response.
Alessandro Strino - Malware Analyst.
如有侵权请联系:admin#unsafe.sh