Introduction
With the never-ending amount of data we generate, process, and share within and between companies, and the value this information can hold – such as personal data, top secret documents, or even information related to national security – it is natural that one of the main interests in cybersecurity is data security. Let it be data discovery, classification, access control, encryption or Data Loss Prevention (DLP), it is often unclear in which direction to go or which product to use to start tackling the long journey of data security.
In this article, I will focus on Microsoft Purview and its data security capabilities, starting with an overview of the best practices. For those who do not know it yet, Microsoft Purview is a comprehensive set of solutions that aims to help companies in governing, protecting and managing data. Microsoft Purview was born from the merging of Azure Purview and Microsoft 365 compliance solutions.
To demonstrate the credibility of Microsoft when it comes to data security, it is important to know that Microsoft was recognized as a leader in The Forrester Wave: Data Security Platforms, Q1 2023 and Microsoft Purview product integrates well with the rest of the Microsoft solutions, such as Entra ID and Microsoft 365. You can find the official statement from Microsoft here: Microsoft a Leader in the 2023 Forrester Wave™ for Data Security Platforms | Microsoft Security Blog
Theory and practice
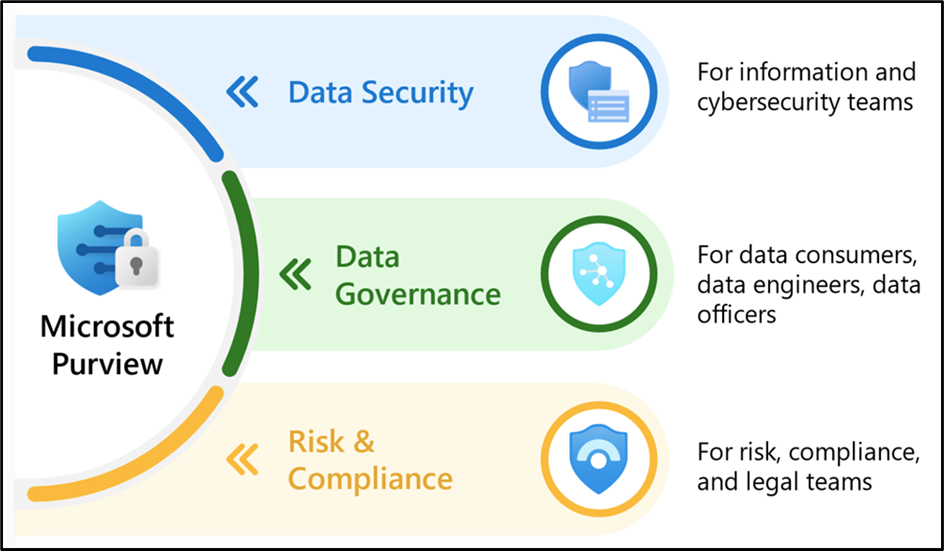
As we all know now that theory will only take you this far, it is important to map the theoretical concept of information protection and practical solutions. It is commonly accepted that the four pillars that serve as a roadmap in information protection can be summarized as follows:
- Know your data: You want to know what data is being used and generated, and how it is used and generated.
- Protect your data: Following the what and how, you must create and maintain the first line of defense for your information by enforcing security and access controls.
- Prevent data loss: Intentional or accidental data leaks can and will happen sooner or later. Defining and enforcing the use cases to mitigate will represent the last line of defense for your data.
- Govern your data: On top of the three other pillars, it is important to put in place governance processes to identify the gaps that remain uncovered by your current solutions. Additionally, a good governance helps you with achieving compliance with the regulations applicable to your company. However, I will not extend myself further on this in this blog post as the focus is data security.
The good news is that Microsoft Purview does cover these four pillars, by providing the tools and solutions shown in the following picture:

Note that the above is not an exhaustive list of all Microsoft Purview tools, but rather an example of the mapping between the theory and some aspects of Microsoft Purview.
It must be noted that to use Microsoft Purview to the fullest extent possible, we strongly advise using the Entra ID Premium P2 license and providing users with Microsoft 365 Enterprise E5 licenses is mandatory.
Triangle of Paranoia
Now I would like to introduce you to the concept of the triangle of paranoia. In data protection, we want to know and control everything, everywhere, all at once. How to do so? Well, let’s have a look at the diagram below:

On the top sits the Data Classification, where the goal is to discover and classify information. There are multiple ways to proceed with Data Classification. For example, it can be done manually using sensitivity labels (i.e., tags that the users apply to their documents and emails), or automatically by identifying the content of documents based on information types or regular expressions. It is crucial to understand the importance of knowing what data and how it is used across the company. Knowledge is power, and it is especially true when it comes to data protection.
On the left corner of the triangle, we have the Data Loss Prevention (DLP) policies. Each of these policies can contain multiple rules whose goal is to restrict or audit data transfers that are deemed forbidden. The DLP rules can be triggered upon identification of a sensitivity label, or when risky activities – such as copying files to an untrusted network drive – are identified and remediation actions can be taken in the Microsoft 365 suite or directly on the device (i.e., Endpoint DLP). The reason why one policy can contain multiple rules is to have different actions based on slightly different conditions within the same scope of the policy. For example, a single event consisting of an accidental leak of a document will only trigger a restriction and a medium severity alert. While the same kind of event but repeated hundreds of times might be an indicator of intentional and malicious leak of information, therefore additional actions can be triggered, the severity of the alerts will be higher, and notification would be sent to administrators via emails. And the two rules will be inside the same policy that aims to protect sensitive documents from being sent externally via emails.
On the right side of the triangle, the Insider Risk Management (IRM) aims to identify and reduce the risk caused by malicious insiders, by gathering and correlating indicators and applying policies to raise the risk level of a user. The policies can raise the risk level of a user by either focusing on the extraction attempts pattern (e.g., mass download followed by renames and zip, then sent via email) or when the user triggers a DLP policy. The IRM dashboard then shows insights on activities and their risk rating.
The above three pieces work in an interconnected manner, one complementing the other. If you already started implementing data security measures with Microsoft Purview, you might have started by classifying data and then applying DLP right after. While this is indeed a common way to approach data security, you are only focusing on the accidental data leaks but omitting insider risks.

When Insider Risk Management is not in place, users with malicious intent could eventually leak or steal data without being detected. Although DLP policies might be able to block some leak attempts, the malicious users will continue to try and find holes, and there is a high chance that they succeed. This kind of scenario – intentional data leak – can be identified by gathering indicators and creating policies in IRM.
What it is important to remember with the concept of such triangle, is to control all sides, not just one or two of them. Developing the Data Classification, the Insider Risk Management, and the Data Loss Prevention all together will allow you to reach a state of mutual enrichment which is primordial to get the most out of data security with Purview.

Purview permissions
As Purview allows its administrators to access sensitive – and sometimes private – information, the permissions model must follow the least-privilege principle to avoid over-permissive set of permissions. While the Security Administrator role in Entra ID allows you to configure and maintain most of Microsoft Purview aspects, it is over-permissive as it also allows you to read the audit log, for example. Therefore, instead of relying on the built-in Entra ID roles, we recommend that you use the Microsoft Purview permissions as they provide more fine-grained functionality. To access the Microsoft Purview permissions, sign in to the Compliance portal (compliance.microsoft.com) with a Global administrator role, navigate to permissions, and select “Roles” under Microsoft Purview solutions.
The Global administrator role is the most privileged role in Entra ID Role-Based Access Control (RBAC).
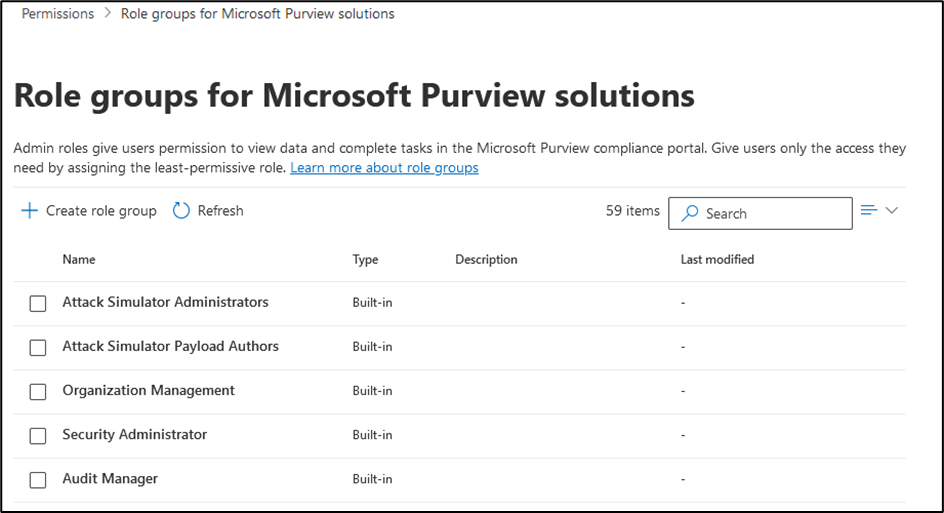
From this dashboard, it is possible to assign built-in groups of permissions that are only applicable to Microsoft Purview. Additionally, you can create your own group of permissions that fits your business and security requirements.
More information about the Purview permissions can be found in the Microsoft documentation.
Our recommended approach
Now that we know about the required licenses, the triangle of paranoia, and the permission model, our Purview implementation needs a direction. There are many approaches to implementing data security with Microsoft Purview, and the one I will describe to you contains everything you need to start in the right direction.

Phase 1 – Prerequisites
This preparation phase includes everything we need to prepare before starting to work on the solution. The Microsoft Enterprise E5 licenses is non-negotiable and while we understand that the cost can be a blocker, it is important to know the true value of the highest licensing model. If you or your company remain undecided, keep in mind that identity protection, advanced mail protection, premium audit, cloud access security broker, privileged identity management, advanced endpoint detection and response, compliance manager (such as NIST CSF or NIS2 assessments) … etc., are only a few of the products you allow your organization to rely on when adopting the Enterprise E5 licenses. And if you were already relying on other vendors for the same features that are part of the E5, upgrading your licenses could even help you save money.
As soon as licenses are adopted, the permission model must be designed. Ask yourself the following questions:
- Who needs access to Purview?
- What will they do in Purview?
- Are there built-in Purview roles correctly scoped to my needs?
- Do we need to create customized set of permissions?
The goal of this exercise is to start identifying the different actors that will use Purview. In any case, a global administrator is required to get started.
Phase 2 – Data Classification
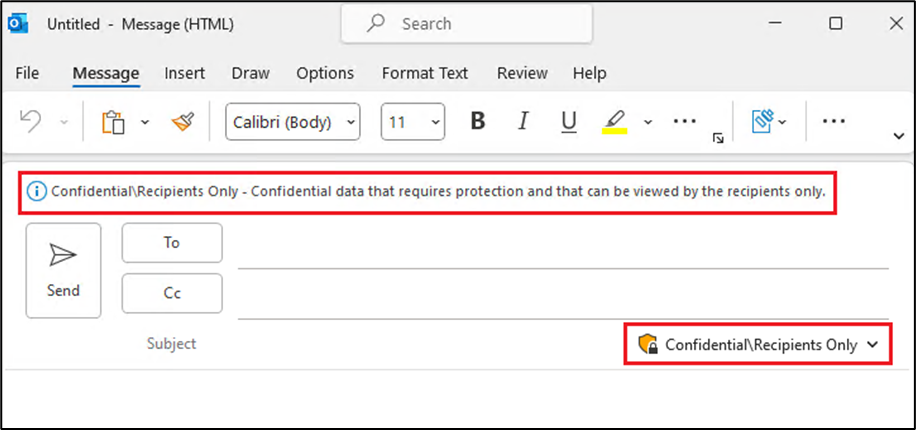
If you remember your theory well, you already know that you should now focus on the very first pillar of data security: Know your data. And this is exactly what we want you to do by starting the implementation and deployment of sensitivity labels. Those labels are metadata added to your information (files, emails, meetings, sites, …). In addition to classify your data for later purpose (i.e., Data Loss Prevention), Sensitivity Labels can also apply content marking to your documents as depicted below:
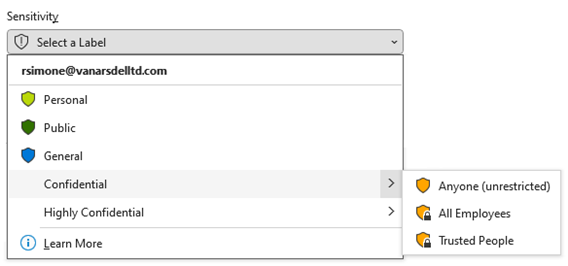

And they can also apply encryption to ensure only explicitly authorized users can access the content as shown below:
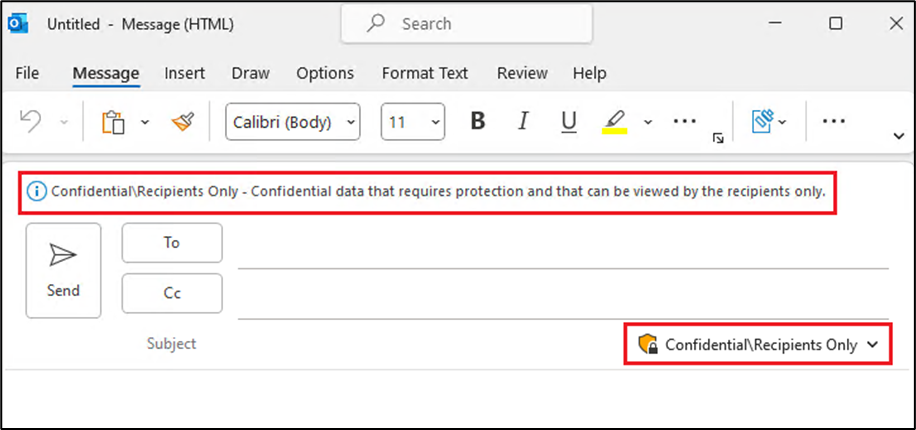
Here are our recommendations for this phase:
- Depending on the company, the different sensitivity levels of information might have already been defined. In that scenario, it is easy to adapt them to the sensitivity labels of Microsoft Purview. If this isn’t the case, then it is important to start thinking about it in general, not just Microsoft Purview but rather for all assets owned by your company.
- The user adoption takes time and effort as the users must label their documents and emails correctly. Do not underestimate this step: correctly classifying information is one third of the paranoia triangle. Although it is possible to automate some part of the classification, training users to use the different sensitivity labels correctly is primordial in the first place.
- Proceeding with baby steps is considerably recommended with all tools in Microsoft Purview, especially with sensitivity labels as they should never be deleted. So, our advice is to think twice before creating a label, don’t be too specific in the beginning as you can always work with additional sensitivity labels or sublabels in the future.
You identified some kind of information that should be treated differently while thinking about the sensitivity labels (e.g., your own company tax number that is always added to your signatures)? Great! You successfully identified a Sensitive Information Type (SIT) exception. Keep note of them as they will come in handy as you progress toward maturity in Microsoft Purview.
Phase 3 – Insider Risk Management
Now that the data classification started as the sensitivity labels are defined and being tested, what do you do? As you want to follow the triangle of paranoia principle, you need to involve Insider Risk Management, and it’s the right moment to start looking into it. First and foremost, inform any relevant team about the upcoming action which is the gathering of anonymized indicators. To do so, ensure that the anonymization of usernames is enabled in the Insider Risk Management settings, and all indicators are selected.

Figure 12: Insider Risk Management – Indicators settings
Note that when selecting some indicators, the consent to process company information from other Microsoft sources such as Entra ID is granted to Microsoft Purview. So, make sure that work council or union is involved in the discussion, if there is one in your company. You might wonder why we recommend proceeding with this step. The answer is short: there is no impact on the end-users’ productivity, and the earlier you gather indicators the sooner you will be able to work with IRM to identify insider risks.
Phase 4 – Data Loss Prevention and enrichment
Let’s assume that the sensitivity labels are now correctly used and applied to all documents and emails, and IRM is gathering indicators. This is now the moment to enable the final piece of the triangle, this is time to design Data Loss Prevention policies. This is where creativity is welcomed, as it is the only limit to what can be done with DLP. Here’s a basic example of an early design of a DLP policy:
- Identifying a use-case: The users from department A should not send documents containing tax numbers (but not your own company tax number! Remember the Sensitive Information Type exception from earlier?) or document with the “Secret” sensitivity label.
- Set the scope: This is applicable to SharePoint Online, OneDrive, Exchange Online.
- Define the action: Block only people outside your organization from receiving emails or accessing shared documents in OneDrive, SharePoint, and Teams.
- Include additional action: Inform the user with tips about sharing sensitive information and raise an alert when the volume of matched activities reaches a threshold.
While DLP policies can be highly customized, we advise you to start with the basics by focusing on external sharing of documents via SharePoint Online, OneDrive, Teams, and Exchange Online. Please note that every DLP policy must be set in test mode first to gather information and fine-tune the policy if needed. As always, we want you to protect your information while avoiding impact on productivity.
If you remember the triangle of paranoia, we went through all pieces. From the data classification, to the Data Loss Prevention, and enabling Insider Risk Management on the way. You have now entered the enrichment part of the last phase, which is a never-ending loop of continuously raising the maturity level of your Microsoft Purview solution. From now on, you will improve on all pieces of the triangle to get the most of Microsoft Purview. Here is a concrete example of how each side enriches its neighbors:
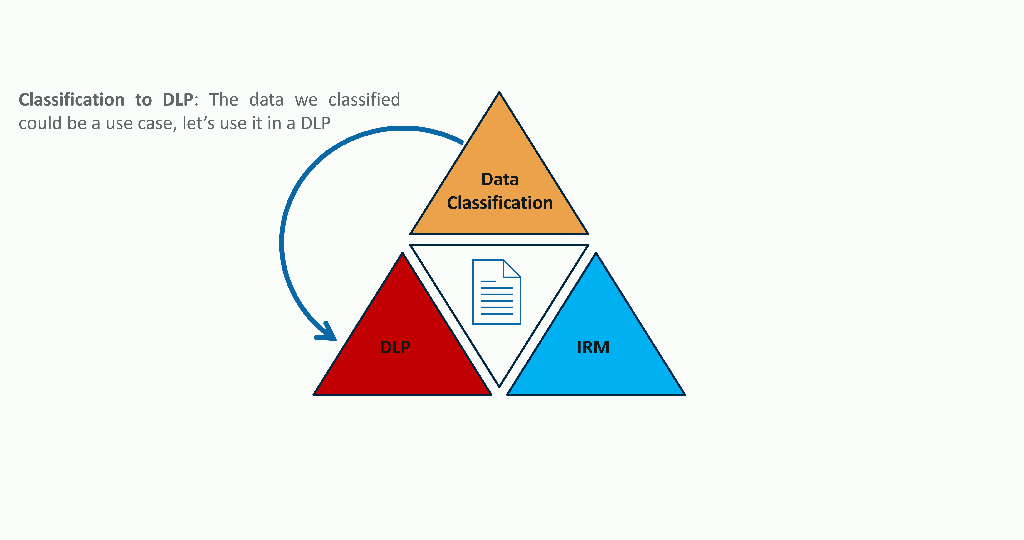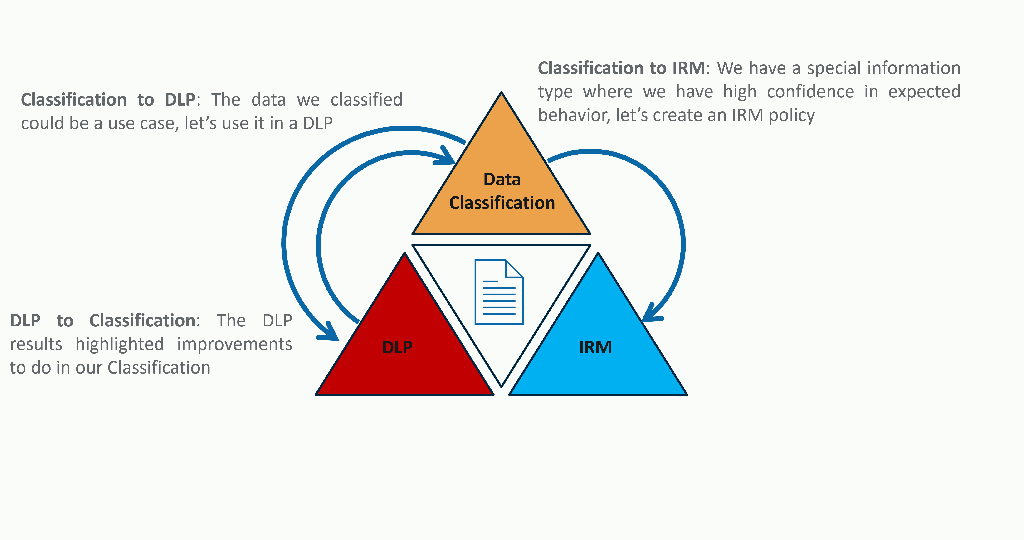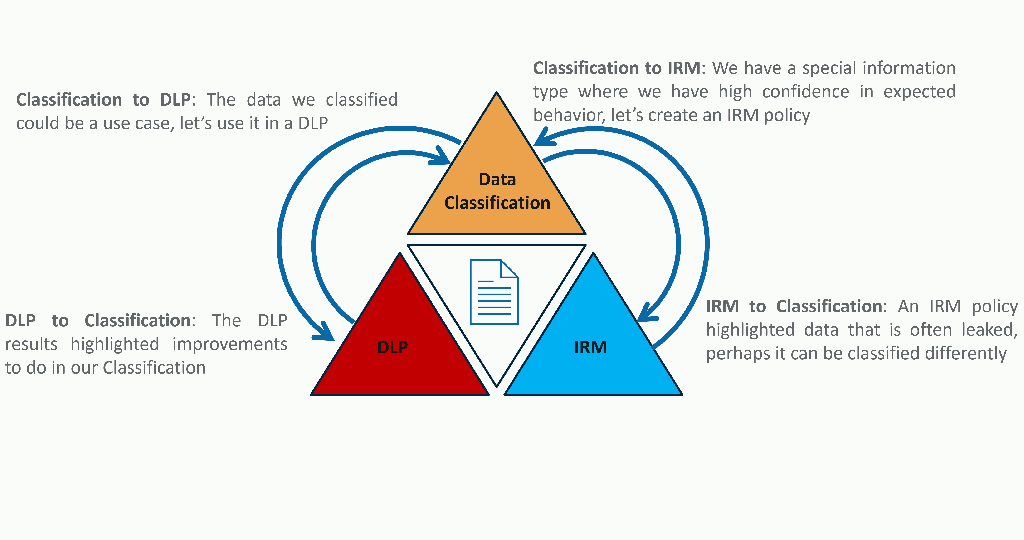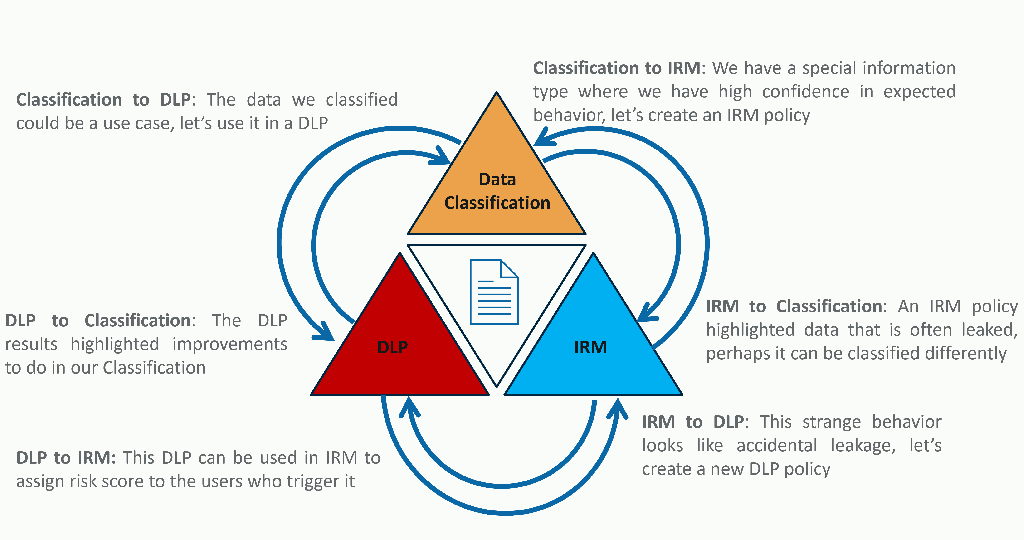
Conclusion
While data security represents a massive effort to be effective due to the tremendous amount of information your company is generating every second, Microsoft Purview is there to provide you with all the necessary tools to tackle this considerable challenge and we are here to guide you during this journey. If you were to remember the main takeaways of this post, think about this:
- Triangle of paranoia: Microsoft Purview provides three amazing tools – Data Classification, Data Loss Prevention, and Insider Risk Management – so use them all together and rely on the mutual enrichment provided by the connections between them to leverage the most of this data security capability.
- Baby steps: The features in Microsoft Purview require a lot of critical thinking and testing. Don’t overwhelm yourself and your teams with a gargantuan initial implementation of the three features. It’s better to accomplish something small with solid foundations than being stuck in a complex design that is not going anywhere.
- Never-ending story: Data security is a dynamic topic. It must be seen as a never-ending race against information leaks where you can only proactively identify use-cases and detect insider risks to stay ahead. Therefore, you must continuously review and assess the state of implementation of Microsoft Purview and include new content. This can be more data classification and refining exceptions, new data loss prevention policies and rules, insider risk management policies, or ideally, all of them at once.
If you feel like we could help you get started with this powerful tool, don’t hesitate to visit our website www.nviso.eu or connect with us on LinkedIn!
Resources
Should you have any questions or remarks, please feel free to connect me with the details at the end of the article.
While the topic tackled in this article reflects professional experience and expertise, the Microsoft resources I used below will also help you in understanding Microsoft Purview:
- Microsoft Purview introduction:
https://learn.microsoft.com/en-us/purview/purview - Microsoft Purview roles and roles groups:
https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/scc-permissions - Microsoft Purview Data Classification overview:
https://learn.microsoft.com/en-us/purview/data-classification-overview - Microsoft Purview Insider Risk Management overview:
https://learn.microsoft.com/en-us/purview/insider-risk-management - Microsoft Purview Data Loss Prevention overview:
https://learn.microsoft.com/en-us/purview/dlp-learn-about-dlp - Microsoft Purview Email encryption:
https://learn.microsoft.com/en-us/purview/email-encryption - Azure Rights Management explained:
https://learn.microsoft.com/en-us/azure/information-protection/how-does-it-work - Learn more about sensitivity labels:
https://learn.microsoft.com/en-us/purview/sensitivity-labels - Restrict access to content by using sensitivity labels to apply encryption:
https://learn.microsoft.com/en-us/purview/encryption-sensitivity-labels
About the author

Mathéo Boute
Mathéo is a Senior Cybersecurity Consultant and member of the Cloud Security Team. His area of expertise revolves around Azure and Microsoft 365 with a focus on Microsoft Purview, Entra ID, Intune, and Defender, where he has an extensive experience of assessing, designing and implementing multiple security solutions in various industries.
Mathéo confirmed his skills by passing all the security-related Microsoft certification, including the Microsoft Certified Cybersecurity Architect.
如有侵权请联系:admin#unsafe.sh