
2024-3-6 19:3:39 Author: pixmsecurity.com(查看原文) 阅读量:12 收藏
Overview
Multi-Factor Authentication (MFA) phishing campaigns targeting teachers, staff, and executive administrators in large school districts throughout the United States have continued to be on the rise since December 2023. The attacks use dadsec and phishingkit Phishing-as-a-Service (PhaaS) platforms, which include a number of stealthy features, with the purpose of compromising key administrator email accounts and ultimately delivering ransomware.
Introduction
This report focuses on ongoing phishing activity beginning in November 2023 that is linked to two prominent threat groups: Tycoon and Storm-1575. Prior reports identified these groups waging aggressive phishing campaigns across diverse sectors like financial services, manufacturing, local government and energy. Many attacks our research found involved stealthy tactics like MFA phishing, targeted key HR and finance personnel, and were hosted on Russian infrastructure. These Tycoon and Storm-1575 attacks were distinguished by their use of Adversary-in-the-Middle (AiTM) tools, allowing them (had they gone unthwarted) to capture MFA codes and session cookies.
Research found that targeted officials would receive classic phishing emails prompting them via a link to update their passwords for security purposes. They would then be directed to a Cloudflare Captcha, followed by a spoofed Microsoft password page embedded in a background with their distinct logo. Had the attacks gone unthwarted, the attacker would forward the passwords to the actual legitimate login pages upon stealing user passwords. From there, victims were directed to pages requesting the actual two-factor authentication codes, which were then forwarded to the actual servers, thus completely bypassing MFA protections. Common users targeted across districts include the Chief of Human Capital and multiple finance and payroll administrator accounts that send regular communications to staff members.
Some of the attacks would attempt to alter Windows registry keys with the possibility of infecting the target Windows machines with malicious scripts. The attacks concealed their tracks with a number of stealth tactics, such as hiding behind Cloudflare infrastructure and quickly spinning up new domains with domain generation algorithms.
Most security practitioners believe MFA is a silver bullet for protecting users from credential harvesting phishing attacks. While equipping corporate users with MFA remains a key step in securing an organization’s environment, the increased use and lowered cost of AiTM infrastructure highlight the need for additional measures like proactive AI-powered detection in the browser.
Context: Storm-1575, Tycoon, and Phishing-as-a-Service (PhaaS)
Both the Tycoon and the Storm-1575 groups orchestrate robust and dangerous PhaaS platforms to target victims across diverse sectors of business and government. PhaaS is a malicious model where cybercriminals or threat actors offer ready-made phishing tools and services. Storm-1575 and Tycoon make use of dadsec and phishingkit PhaaS services, respectively. Some research indicates that the two platforms are linked. While any threat actor with sufficient intent and funds can purchase dadsec and phishingkit tools, the specific tactics, techniques and procedures our research identified closely match the cluster of activity associated with Storm-1575 and Tycoon.
Tycoon
The Tycoon Phishing Group is a notorious cybercrime organization that targets a wide range of victims. Their website (below) boasts “the best 2fa bypass phishing platform”. They have an active Telegram that offers professional grade customer service and tiered product packaging akin to a typical B2B SaaS business.
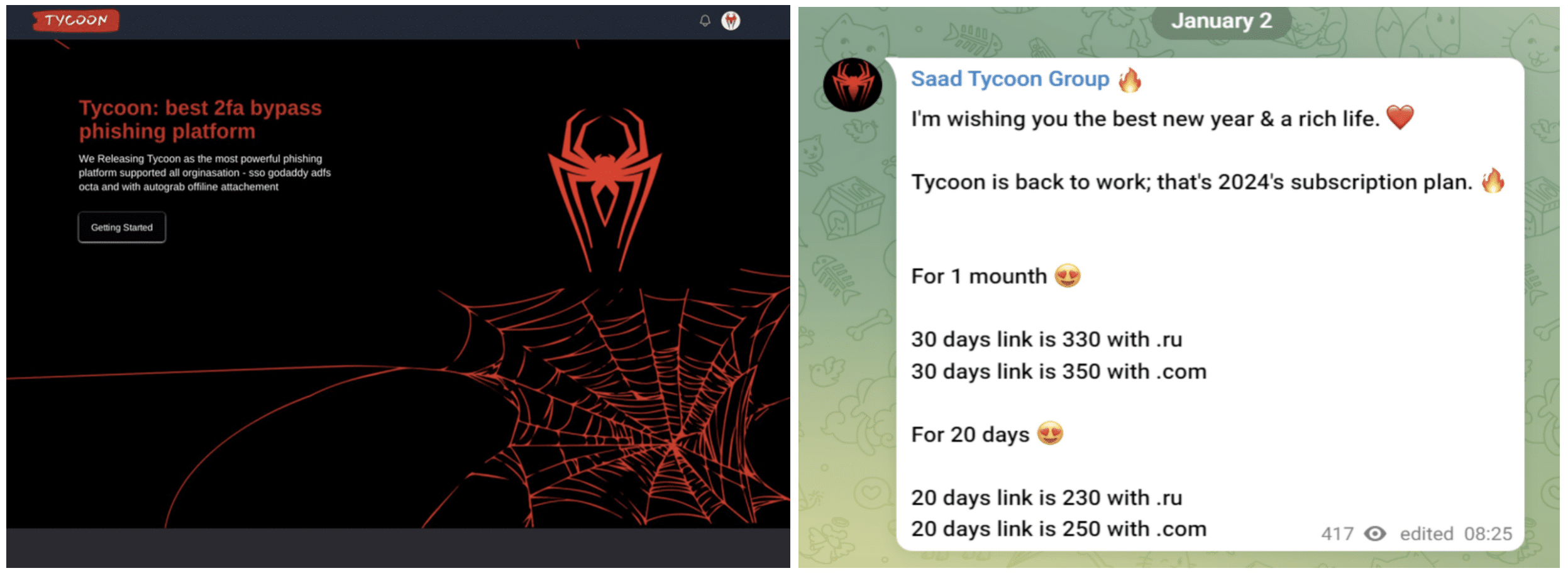
The group has created a PhaaS platform called phishingkit that allows the use of different types of branded templates. They are known for highly targeted delivery mechanisms to infiltrate small to medium sized companies. Recent reports of the group involved targeting investment firms using 2FA phishing links delivered through QR codes in XLS and PDF attachments.
Storm-1575
Storm-1575 provides a PhaaS platform named dadsec (recently rebranded as “Phoenix Panel”). Their platform offers AiTM capabilities. This means the attackers are proxying all the requests between the victim and a legitimate site (for example, Microsoft). A successful attack results in a complete take over of the victim’s account, even if MFA is enabled. The group recently deleted their store websites, Telegram channels and YouTube videos, but they are still very active.
Microsoft has issued a warning against Storm-1575 in their monthly news.
Tactics, Techniques and Procedures
Analysis of Tycoon and Storm-1575 phishing attacks targeting district officials revealed a common attack pattern. Here are the key elements:
Social Engineering. Typical across most phishing attacks, Tycoon and Storm-1575 attacks rely heavily on social engineering techniques, spoofing their emails to appear to come from legitimate sources and using fear-inducing language to create a sense of urgency.
Adversary-in-the-Middle (AiTM). The attacks targeting k12 officials were distinguished by the use of AiTM phishing. Unlike traditional credential harvesting attacks, these attacks complete the authentication process by proxying stolen credentials into their legitimate server. This enables the attacker to further steal MFA tokens and altogether bypass MFA safeguards. The below diagram illustrates this for a 2FA Microsoft phishing attack.
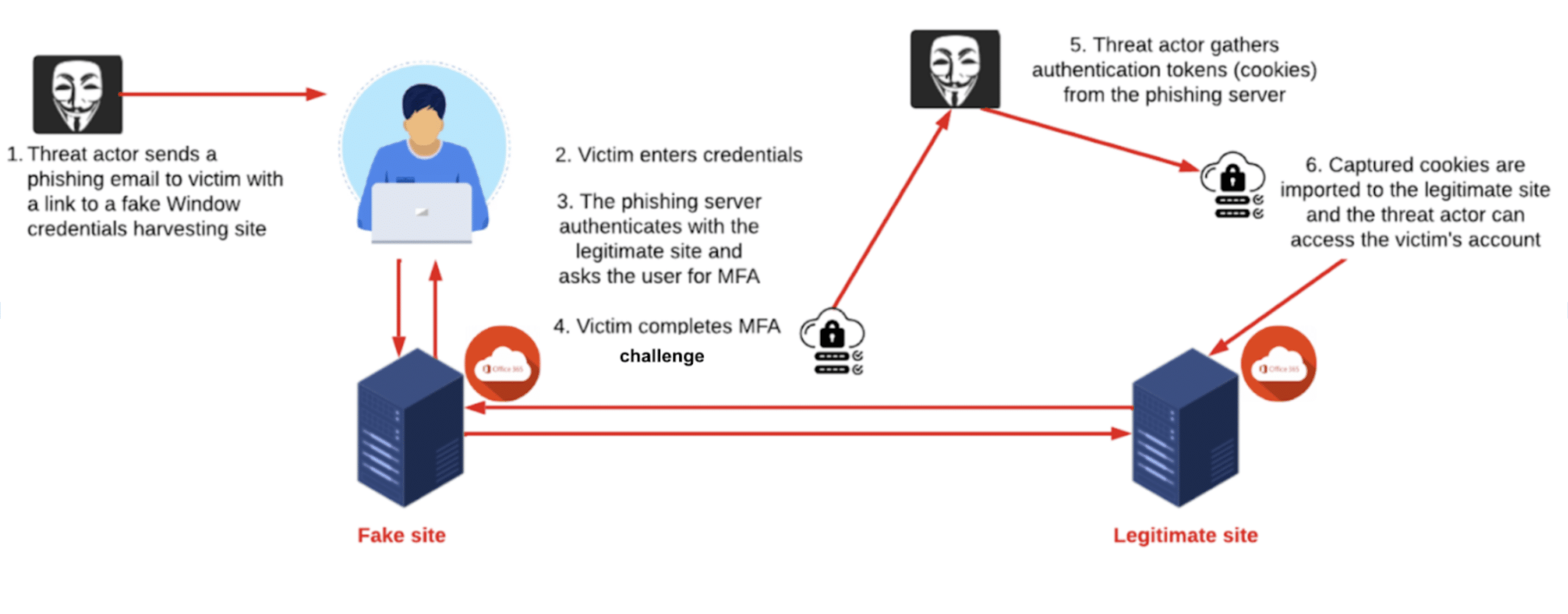
The phishing attacks also steal session cookies, which allow attackers to maintain unauthorized access without requiring re-authentication.
Customized Login Experiences. The attacks targeting school districts incorporated not only official email addresses but also cloned district logos in the background (illustrated below with a fictitious school district).

Indeed, the dadsec and phisingkit PhaaS services allow operators to point at legitimate sites and produce custom login experiences to match their target’s typical workflow (illustrated below). Such automation further frees operators to invest efforts in crafting more targeted phishing attacks.
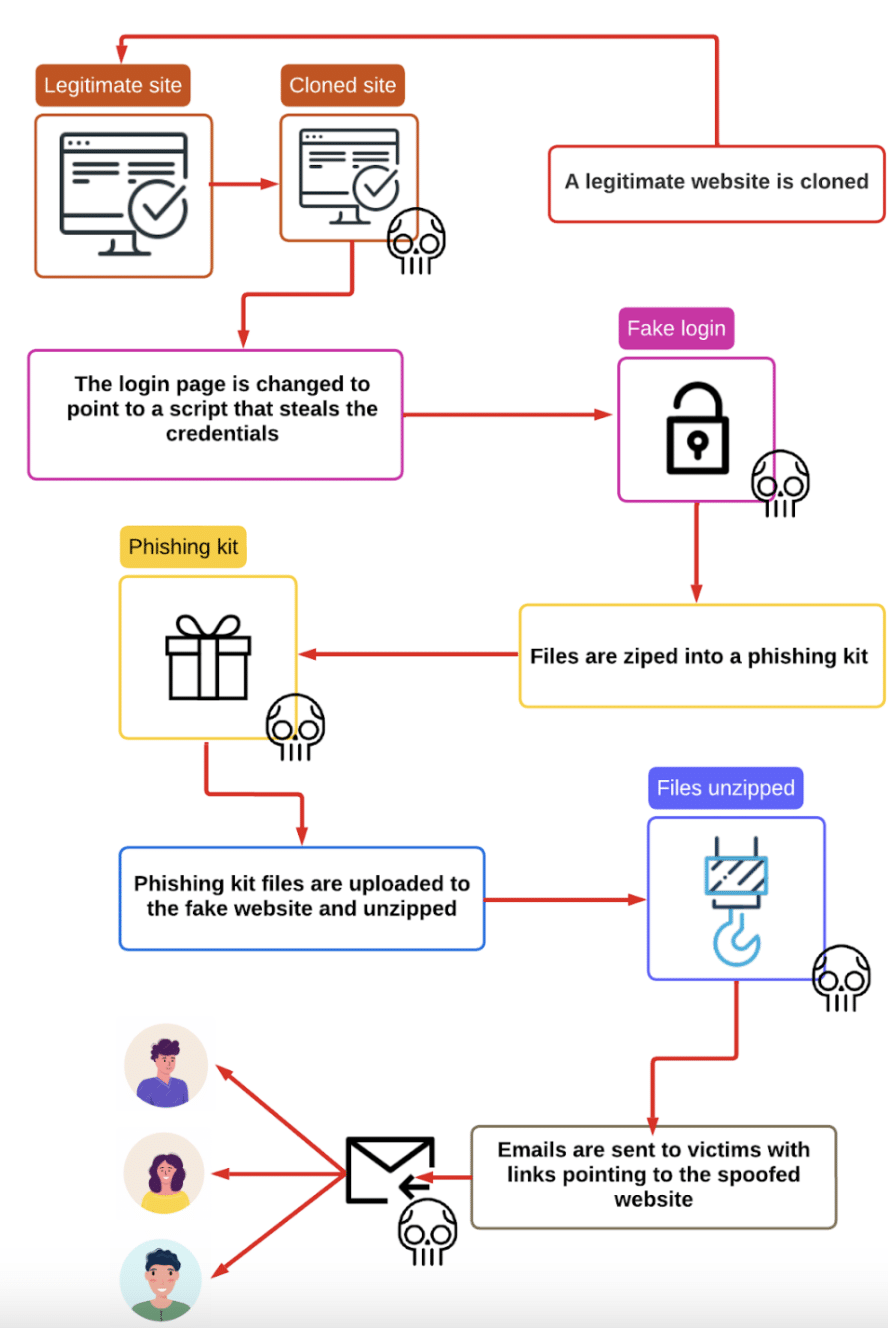
Robust and large scale infrastructure. These attacks involved a robust infrastructure, including Command & Control (C&C) servers, domain generation algorithms (DGA), legitimate hosting services (CloudFlare) and SSL certificates (provided by ‘Google Trusted Services’). This allows operators to spin up quickly and control large numbers of phishing websites, while hiding behind legitimate host and certificate providers to avoid detection. Here is a sample of the domains that were identified.
https://o97egqznd6rat2s[.]oyderxxkfs[.]ru/
https://8fcqoxugstc9smg[.]tpulsiwlor[.]ru/
https://gysew[.]itquw[.]ru/
https://a87hurvpg3y5qd0[.]jpsbvhcqnh[.]ru
https://fijdylxtwnm4k15[.]qpxr43vtgm[.]ru
https://fqpp[.]nb6o[.]com
Many of the phishing attacks include a CloudFlare CAPTCHA as part of the login experience.
Adding CAPTCHAs to the attack flow postpones the phishing payload delivery, allowing malicious pages to evade security content analysis. CAPTCHAs can further add a sense of legitimacy from the end user perspective.
Potential of Malicious Trojan Activity. Several of the attacks revealed the possibility for malicious trojan activity. Investigations into the phishing attacks showed the ability to modify Windows registry keys for the VBS (Visual Basic script) file format and the injection of a malicious file ‘script.vbs’. This can be used to run arbitrary scripts to achieve malware installation, ransomware, data exfiltration etc.
Takeaways and Recommendations
- The proliferation of MFA PhaaS tools make it mere routine for adversaries to bypass MFA controls and customize highly targeted phishing attacks.
- The scale of infrastructure and use of legitimate hosting services make these attacks difficult to detect.
- While email security, Multifactor Authentication and awareness training have been traditional table stakes to protect organizations from phishing attacks, the modern attack environment leaves organizations vulnerable without additional protections.
- Identify high priority staff who have sensitive access or have regular communication patterns across the organization (eg. payroll, invoicing, or HR). Invest in extra and, if needed, tailored awareness efforts for this group. This can pay huge dividends even in the context of sophisticated attacks so that sensitive accounts are not compromised.
- Arm users with caution against links and websites even if they prompt them for MFA tokens and CAPTCHAs.
- Implement additional proactive AI-driven protections at the browser layer and email layer to protect users from stealthy phishing tactics like AiTM.
Conclusion
The recent Tycoon and Storm-1575 spear phishing activity targeting US school district officers highlights the proliferation of sophisticated cyber threats. PIXM’s AI browser extension using computer vision technology quickly detected and prevented these attacks, showcasing the need for advanced cybersecurity measures. The incidents particularly underscore the vulnerability of MFA to sophisticated AiTM techniques that are becoming increasingly commoditized.
Questions or Feedback
PIXM Threat Research Team
[email protected]
如有侵权请联系:admin#unsafe.sh