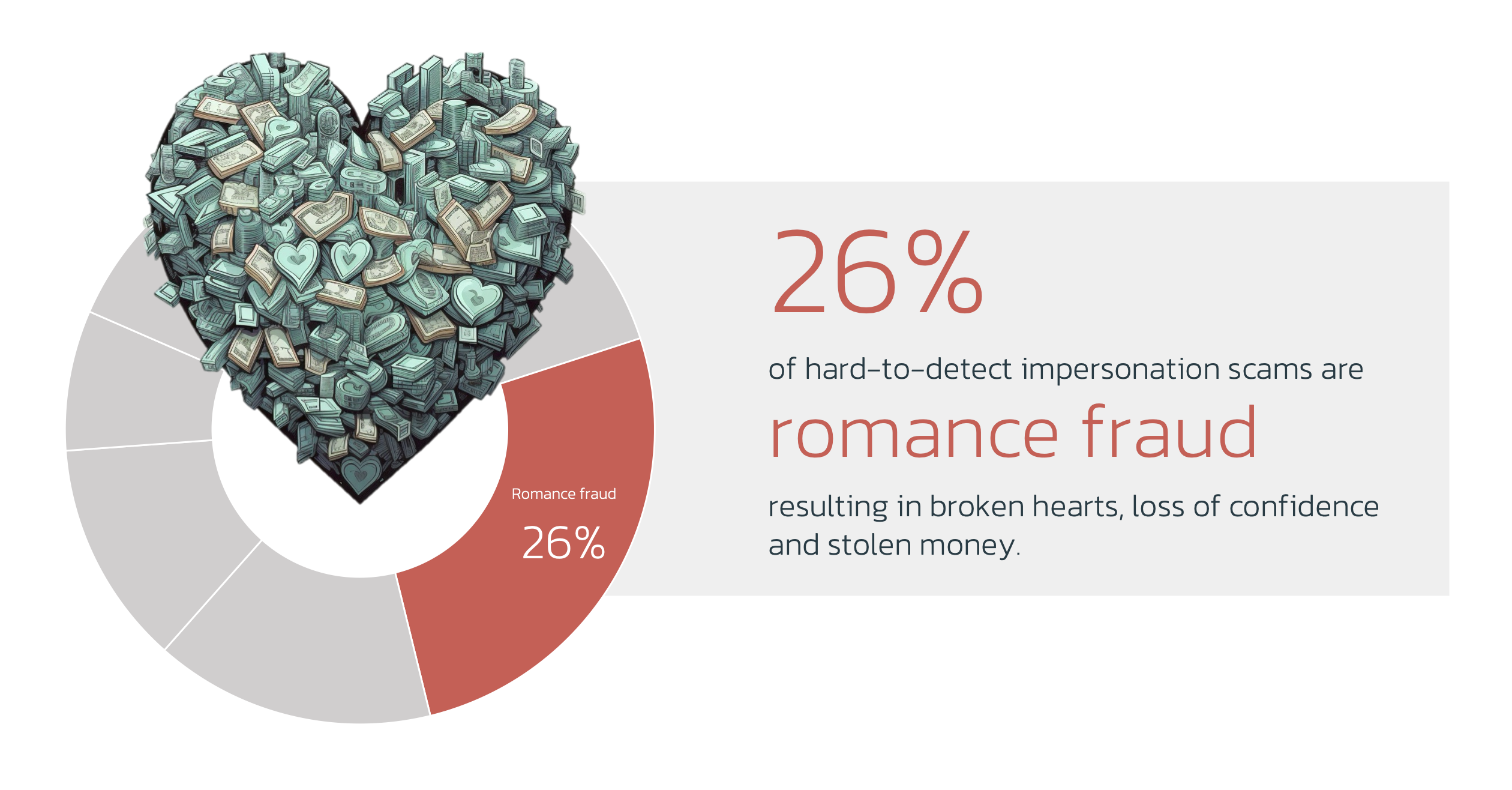
From Malware campaigns to scams, we’ll analyse TTPs, Fraud Kill Chain mappings, and detection gaps. Romance scams require the scammer to invest quite some time with the victim. A typical interaction has these steps: Our research shows over a quarter of scams are performed in this way. With the right tools, anti-fraud teams should be able to pick up the tell-tale signs of these attacks. The Fraud Kill-chain is a useful tool to identify detection opportunities and gaps. It allows anti-fraud teams to map capabilities to attacks and helps control various frauds and scams. The difficulty with scam detection is the lack of “technical” TTPs. “Receiving flowers” isn’t something you can detect in on-line session data. There’s a clear gap in the “account access” stage. Since most of the manipulation is done by social engineering rather than technical manipulation, detecting anomalous behavior is key. We can see a plethora of TTPs identifying various stages of attacks before, during, and after. This means there is a lot of opportunity for detection, but it requires sensors and processes in digital channels. In many scam attempts, device use and the transaction will seem completely benign. To detect behavioral aspects, it’s key to have customer journey visibility: all interactions happening between login and transactions. Web and app adoption is increasing rapidly. This is why a detection stack should include customer journey visibility on any online channel: web, mobile, and app. Manipulation of behavior requires a different perspective. Behavioral Biometrics is the best technology available. It’s key to have multiple models: As scammers are raking in billions, anti-fraud teams are to perform the following checks: ThreatFabric helps banks and financials globally perform these analyses. If you’re interested in a detection readiness workshop, use the link below for a free consultation.This blog is part of a series, where we will offer the tools to check your fraud detection capabilities for readiness on the most prolific fraud and scam types.
This second episode is about one of the most impactful scams for victims: Romance Scams The Problem
About the Fraud Kill Chain
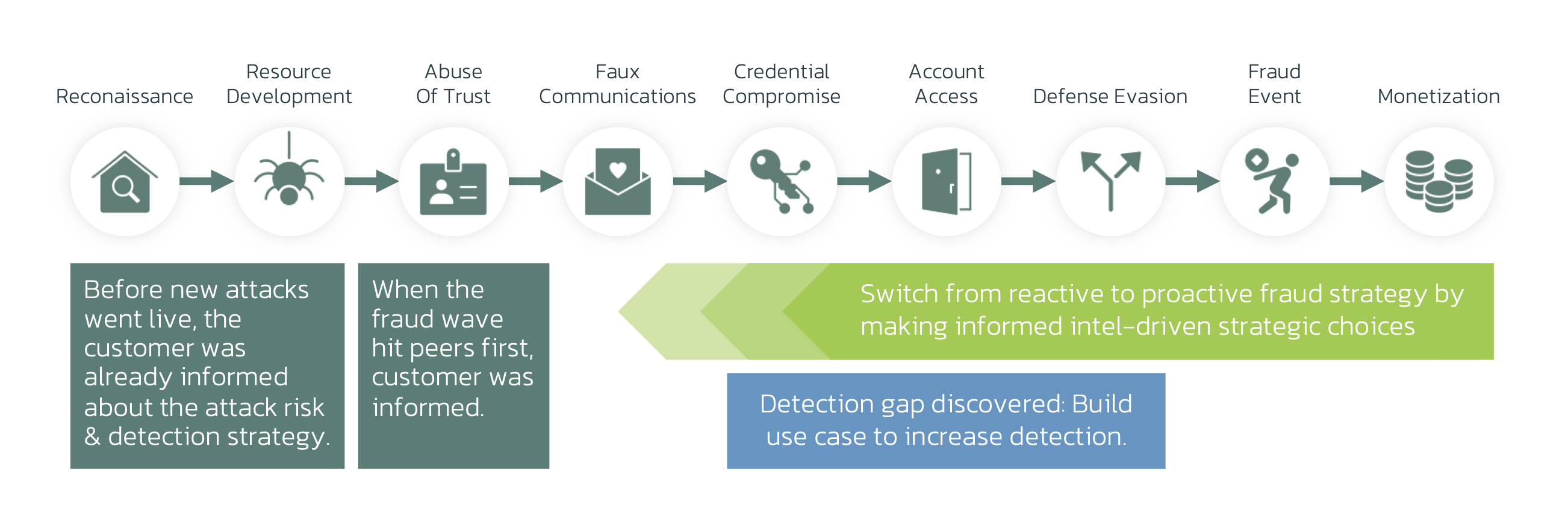
Romance Fraud vs Fraud Kill Chain

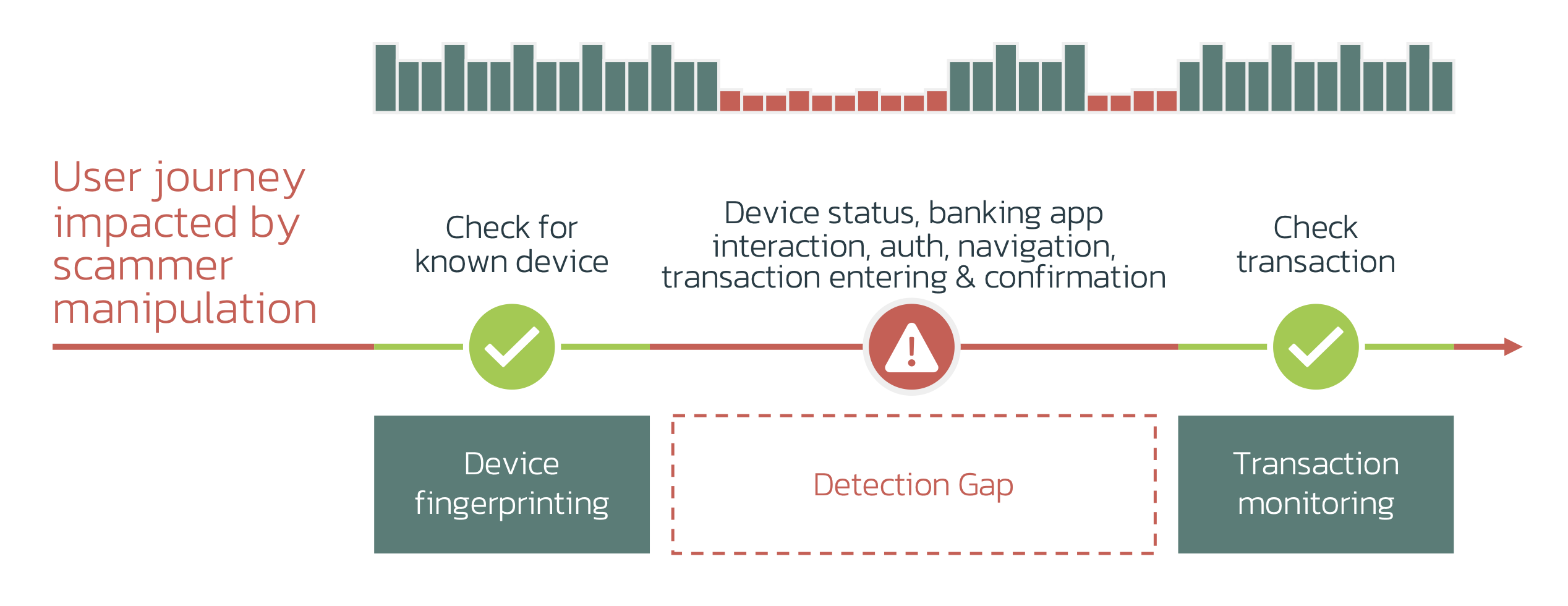
Detection Gaps & Opportunities Gap 1: Customer Journey Visibility
Gap 2: Web, Mobile & App Visibility
Gap 3: Behavioral Biometrics
Conclusion & Takeaways
Detection Readiness Workshop
如有侵权请联系:admin#unsafe.sh