When we discuss the challenge of managing the enterprise attack surface, it is important to understand that it is not a homogenous entity. Rather, it comprises a multitude of disparate elements, each presenting its unique risk profile and demanding tailored security measures. Among these components, one of the most prevalent yet often overlooked is the identity attack surface.
From external-facing systems to cloud infrastructure, on-premises networks, and even third-party supply chains, the attack surface encompasses diverse landscapes vulnerable to exploitation. However, amidst this complexity, the identity attack surface stands out as a particularly notorious vector for cyber threats.
In this context, effective management of the identity attack surface emerges as a linchpin in any robust exposure management strategy. By diligently addressing vulnerabilities inherent in identity systems, organizations can fortify their defenses, thwart potential cyber assaults, and safeguard their invaluable assets. Join us as we delve into the intricacies of identity security and explore its pivotal role in contemporary cybersecurity landscapes.
The identity attack surface encompasses the various identities and access points within an organization’s ecosystem that are susceptible to potential breaches. These identities can include employees, contractors, partners, and even customers who have access privileges to critical systems and data.
The identity attack surface is also made up of:
- Authentication Mechanisms: Methods used to verify the identity of users accessing systems or resources, such as passwords, multi-factor authentication (MFA), biometrics, or single sign-on (SSO), which may be vulnerable to brute-force attacks, phishing, or bypass techniques.
- Access Controls: Policies, rules, and mechanisms governing the permissions and privileges granted to users for accessing specific resources or performing certain actions, which may be misconfigured, outdated, or insufficiently enforced, leading to unauthorized access or privilege escalation.
- Privileged Accounts: Specialized accounts with elevated permissions or administrative privileges, such as system administrators or service accounts, which may be targeted for exploitation to gain unrestricted access to critical systems, data, or infrastructure components.
- Identity Federation: Mechanisms for establishing trust relationships and sharing identity information across different systems or organizations, such as federated identity providers or identity federation protocols, which may introduce security risks if not properly configured or managed.
- Identity Repositories: Databases or directories containing information about user identities, attributes, and entitlements, such as LDAP directories or cloud-based identity repositories, which may be targeted for unauthorized access, data exfiltration, or manipulation.
Risks Within the Identity Attack Surface
Organizations that fail to effectively manage their identity attack surface expose themselves to a myriad of risks, each capable of inflicting substantial damage to their operations, reputation, and bottom line. Among the most prevalent and concerning of these risks are account takeover, lateral movement, and ransomware spread.
1. Account Takeover
Account takeover occurs when threat actors gain unauthorized access to user accounts by exploiting weak passwords, stolen credentials, or social engineering techniques. Once commandeered, these accounts become a gateway for malicious actors to masquerade as legitimate users, granting them unrestricted access to sensitive information, financial assets, and critical systems. The repercussions of account takeover can be severe, ranging from data breaches and financial losses to reputational harm and regulatory penalties.
2. Lateral Movement
Once inside an organization’s network, threat actors can move laterally, seeking to gain access to additional systems and data. By exploiting vulnerabilities in identity and access controls, attackers can traverse through interconnected systems, accessing confidential data, intellectual property, and mission-critical assets. The consequences of lateral movement can be far-reaching, including widespread data exfiltration, disruption of operations, and prolonged breaches that remain undetected for extended periods.
3. Ransomware Spread
Ransomware attacks pose a significant and growing threat to organizations worldwide, with devastating consequences for victims. In many cases, threat actors exploit vulnerabilities in identity and access management systems as a foothold to initiate ransomware attacks. From there, they demand hefty ransom payments in exchange for decryption keys, threatening to permanently encrypt or publish sensitive data if demands are not met. The widespread disruption caused by ransomware attacks make them highly lucrative and impactful form of cybercrime.
Introducing Identity Detection and Response
To mitigate the risks associated with the identity attack surface, security teams have continued to invest in identity and access management (IAM) solutions as a key pillar of their cybersecurity programs. Recognizing the limitations of traditional methods such as multi-factor authentication (MFA) and privileged access management (PAM), security leaders are turning to modern solutions such as Identity Detection and Response (ITDR).
Identity Detection and Response (ITDR) as defined by Gartner is “a discipline that includes tools and best practices that protect identity infrastructure itself from attacks.” Unlike conventional measures, ITDR goes beyond authentication and access controls, focusing on proactively identifying, monitoring and mitigating threats associated with unauthorized access, misuse, or compromise of digital identities.
At its core, IDTR involves continuous monitoring of user behaviors, access patterns, and authentication activities to detect anomalies, suspicious activities, or potential indicators of compromise (IOCs) that may signify a security incident.
The Noetic Approach
The Noetic platform maps security data from different security and IAM tooling, enabling users to find control gaps and weaknesses in the identity attack surface. These could include over-privileged users with missing credentials, or high-risk vulnerabilities within the identity IT infrastructure which could allow attackers to compromise user identities.
All elements of the identity attack surface can be presented to the relevant IAM team via simple dashboards, or proactive alerting through integrations with Slack, Teams, or email.
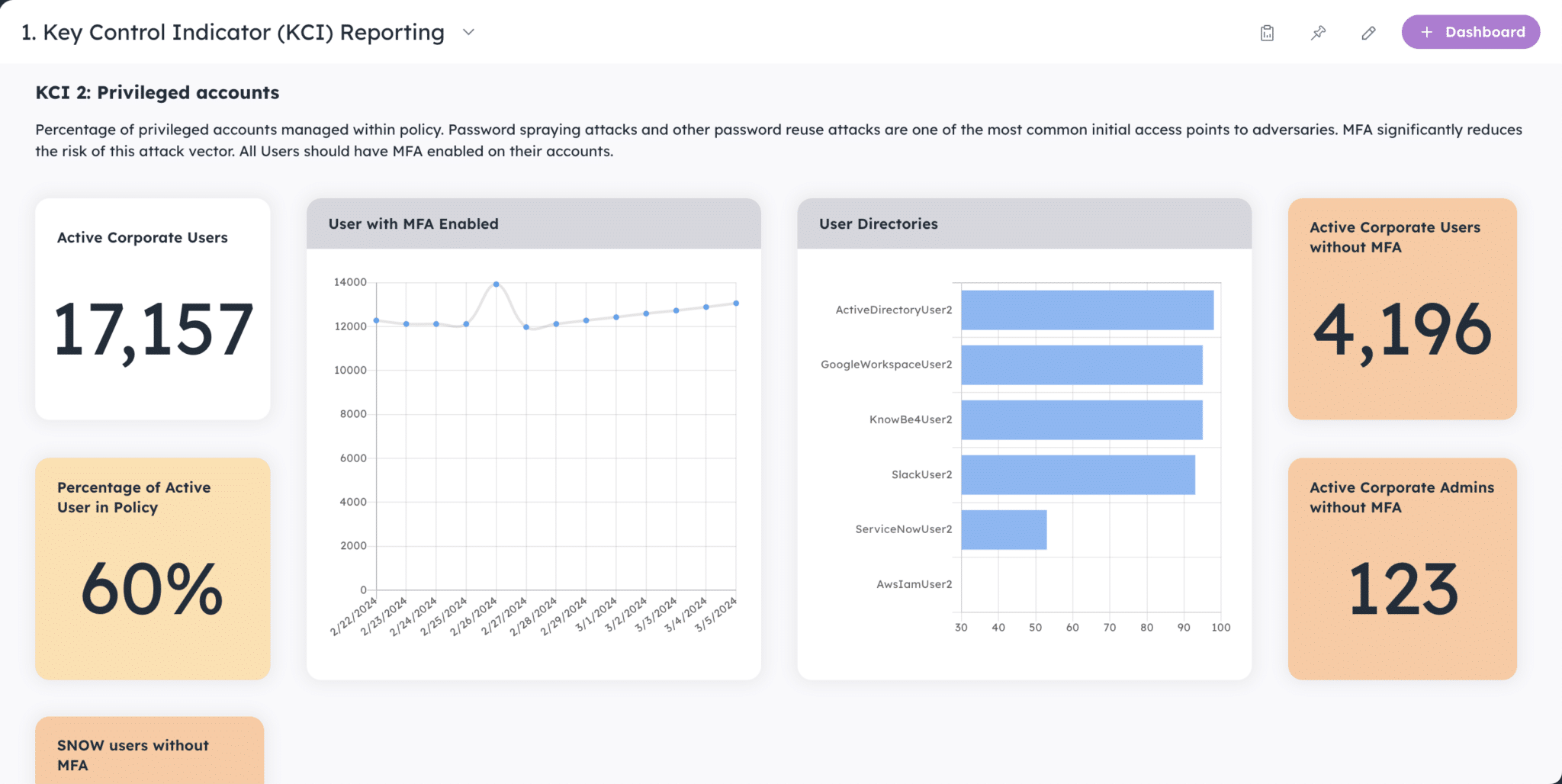
Managing the identity attack surface is a crucial aspect of a comprehensive exposure management program. Organizations must adopt innovative identity security solutions to effectively protect their identity assets from attack. Through integrating their IAM stack with cloud security, networking, vulnerability management and threat detection and response technologies to give them a complete view of their cyber assets and potential exposure, they are better able to measure risk and ensure that user identities can be protected.
By prioritizing the management of the identity attack surface, organizations bolster their cybersecurity posture, mitigating potential risks, and safeguarding critical assets from malicious exploitation. Thus, proactive management of the identity attack surface emerges as a vital strategy in maintaining resilience against evolving cyber threats.
*** This is a Security Bloggers Network syndicated blog from Noetic: Cyber Asset Attack Surface & Controls Management authored by Alexandra Aguiar. Read the original post at: https://noeticcyber.com/understanding-the-identity-attack-surface/
