Regular readers of my blogs know that I love browser extensions. Extensions can make using your browser more convenient, fun, and secure. Unfortunately, extensions can also break websites in bizarre ways, dramatically slow your browser performance, leak your personal data, or compromise your device.
The designers of the Chromium extension system created a platform with a huge amount of power and an attack surface dramatically smaller than its predecessors (COM and NPAPI). That smaller attack surface meant that it was much harder for a rogue extension to harm your device, and it was much easier to tell how much access a given extension would get to your pages and data inside your browser. Unfortunately, many common tasks (particular scenarios like blocking ads) require that extensions be granted a very high level of permission.
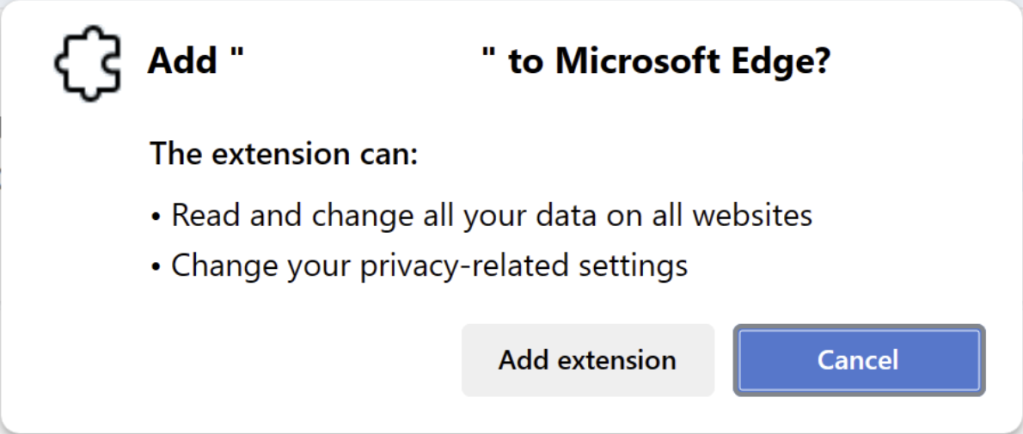
As a consequence, users quickly get accustomed to approving permission requests like this one:
…which grants the extension the ability to: read your email, send email to your entire address book from you, delete files from your cloud storage, put malicious files into your cloud storage and share them to your friends, use your credit card number to order a thousand beanie babies for delivery to your boss, publish your usernames and passwords as a thread on Twitter, dial your mom and ex-girlfriend at 2am, update your LinkedIn profile to reflect a career as a circus clown, and publish embarrassing pictures on your Facebook wall. And more.
Providing this level of access to your browser is more risky than having your password stolen, because many web systems use 2FA and other techniques to prevent abuse of your password, but these techniques are ineffective against a sock-puppet browser.
But… but… but I want what this extension offers and I trust those guys! Heck, I’ve even reviewed their code using the very cool Chrome extension source viewer!
Well, that’s good, but it’s important to understand the full threat environment. Even if the version of the extension you’ve got today is safe, there’s no guarantee that it will remain safe in the future. Popular extensions (particularly free extensions) are a common target of supply chain attacks. The extension author might get sloppy and accidentally update to a new library with a security bug or trojan code. Or their Google account gets hacked and the bad guy takes over the extension. Or perhaps they accept one of the enticing offers that they’re frequently emailed, offering them a few hundred or thousand dollars to “take over” their extension. Your browser installs a new version of their extension without any notice, and your previously-secure browser has turned from a “User Agent” into an “Attacker Agent.”
It’s scary.
Over the last few years, the Chrome team has tried to reduce the potential for abuse in the new “Manifest V3” system, but pundits and others have popularized elaborate conspiracy theories that this was just a way for Google to crack down on adblockers for their own business interests. (This is an especially silly claim, since Google ads are trivially blockable in the new system)
So, what’s a human to do? Use as few extensions as you can, and prefer your browser’s built-in capabilities as much as you can. Periodically review the extensions in your browser (and your dad’s!) by visiting about:extensions and remove any you don’t recognize or need.
If you work in IT Security, it’s important that you understand the security risk of extensions is almost as great as traditional malware. Develop a policy that helps protect your enterprise from malicious extensions by blocking certain permissions, and if feasible, blocking all extensions except a curated allow-list. Chrome and Edge offer a powerful set of Group Policies to control what extensions are permitted and how those extensions may interact with your domains.
If you’re especially on-the-ball, you can create your own company-internal “Web Store” and allow users to only install extensions that your IT Security team has reviewed and vetted. This approach helps prevent the supply-chain attack because your Internal Web Store will control the update cadence, and you can only allow updates after they’ve been reviewed by experts. If you want to learn more, Google has published a pretty thorough PDF describing Enterprise Management of browser extensions.
Stay safe out there!
-Eric
Impatient optimist. Dad. Author/speaker. Created Fiddler & SlickRun. PM @ Microsoft 2001-2012, and 2018-, working on Office, IE, and Edge. Now a GPM for Microsoft Defender. My words are my own, I do not speak for any other entity. View more posts