
2024-3-8 04:33:3 Author: securityboulevard.com(查看原文) 阅读量:9 收藏
SOAR solutions create a centralized queue of all incidents going on in a security team’s environment. Endpoint, SIEM, email, behavior, and network alerts are all collected inside of a holistic SOAR solution. As such, SOAR analytics are a unique way to understand your overall security environment and what threats you’re facing on a day-to-day basis.
D3 Labs analyzed 75,331 incidents in order to determine the 10 most common MITRE ATT&CK techniques. This dataset was derived from a subset of our customers who are based in North America and Europe.
In this report, you’ll see the findings of our study, as well as automated incident response playbooks you can deploy to ensure you have an effective answer to these threats.
About D3 Labs
D3 Labs represents the research and development backbone of D3 Security, consisting of a dedicated team of cybersecurity analysts, automation engineers, network architects, and threat researchers. This skilled group is tasked with simulating attacks, utilizing the same security tools employed by D3’s clients, to identify and bridge detection and response gaps within those tools. In addition to testing and refining cybersecurity measures, D3 Labs is instrumental in developing and maintaining an extensive library of industry-best integrations, thereby minimizing the complexity and number of steps clients need to incorporate into their playbooks, even for the most sophisticated and unique workflows.
What Are MITRE ATT&CK Tactics and Techniques?
MITRE ATT&CK is a globally accessible knowledgebase of adversary tactics and techniques based on real-world observations. In MITRE ATT&CK, tactics represent the “why” of an adversary’s actions—their objectives or goals during an attack. These include objectives like initial access, defense evasion, and execution. Each tactic includes many techniques, which represent the “how”—the specific methods adversaries use to achieve their tactical objectives, such as exploiting a software vulnerability, phishing, or keylogging.
Read: What Are MITRE ATT&CK and MITRE D3FEND?
Key Findings
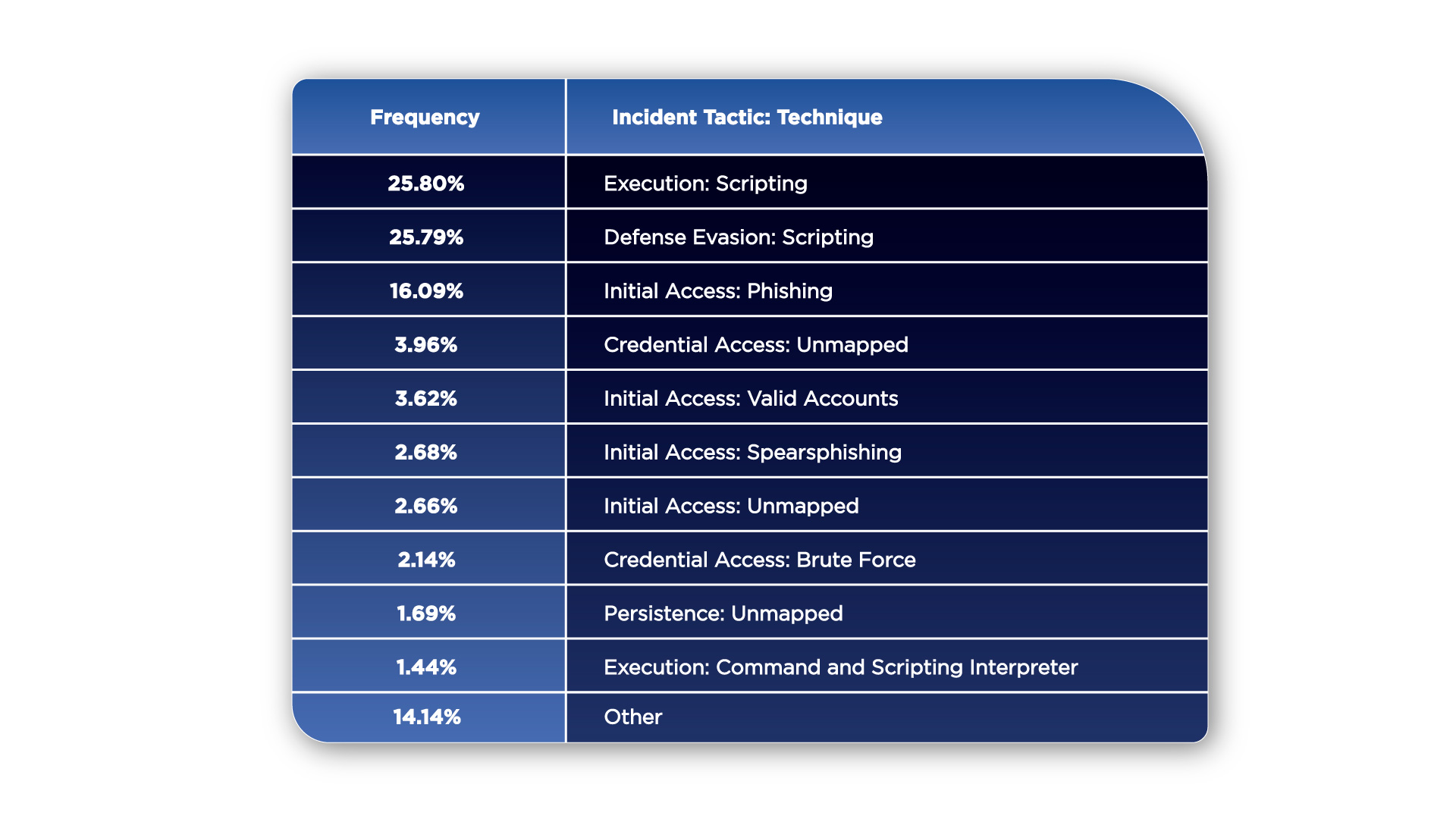
The most common tactics in our dataset are Execution and Defense Evasion, both predominantly through the technique of Scripting, combining to account for more than 50% of incidents. Phishing remains a significant initial access vector, followed by other notable techniques involving valid account exploitation, spear-phishing, and brute force attacks. The presence of unmapped techniques that fall under the tactics of Credential Access and Persistence indicate that some incidents used methods not fully captured by existing categorizations.
Detection, Monitoring, and Response in Smart SOAR
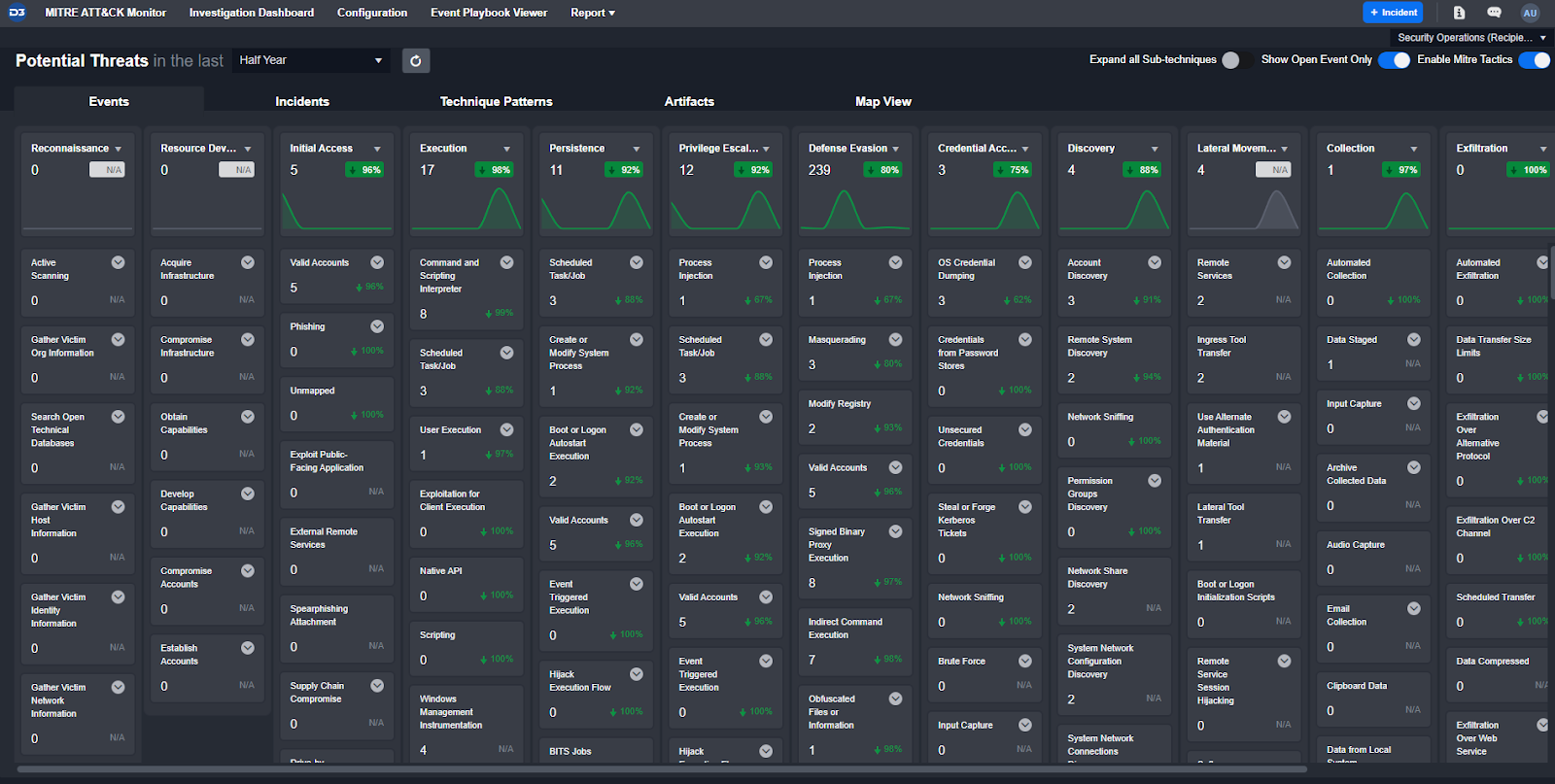
D3’s Smart SOAR detects MITRE tactics and techniques in three different places: on ingestion, at the event level, and at the incident level. All MITRE detections are collected and displayed in the MITRE ATT&CK Monitor dashboard, which gives security professionals an at-a-glance view of their threat landscape. Users can create custom detection logic directly in the platform to ensure all data is relevant and up to date.
When an event or incident is tagged with a specific MITRE tactic or technique, the corresponding playbook can be attached to it, ensuring teams are following the right protocol for each unique threat. Here you can see an incident that has been categorized as a Credential Access: Brute Force threat, with the corresponding response playbook attached.
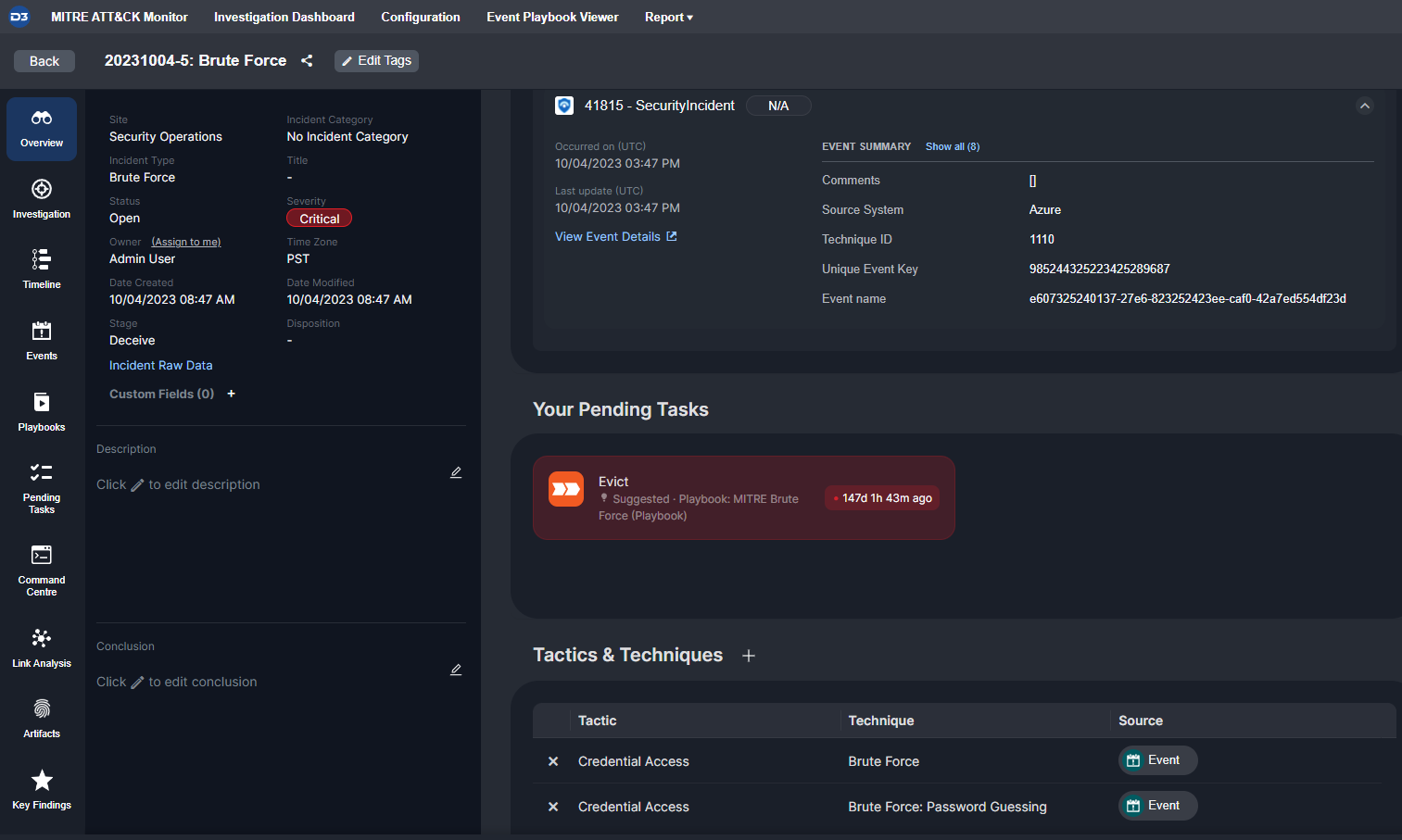
Tactic & Technique Tag
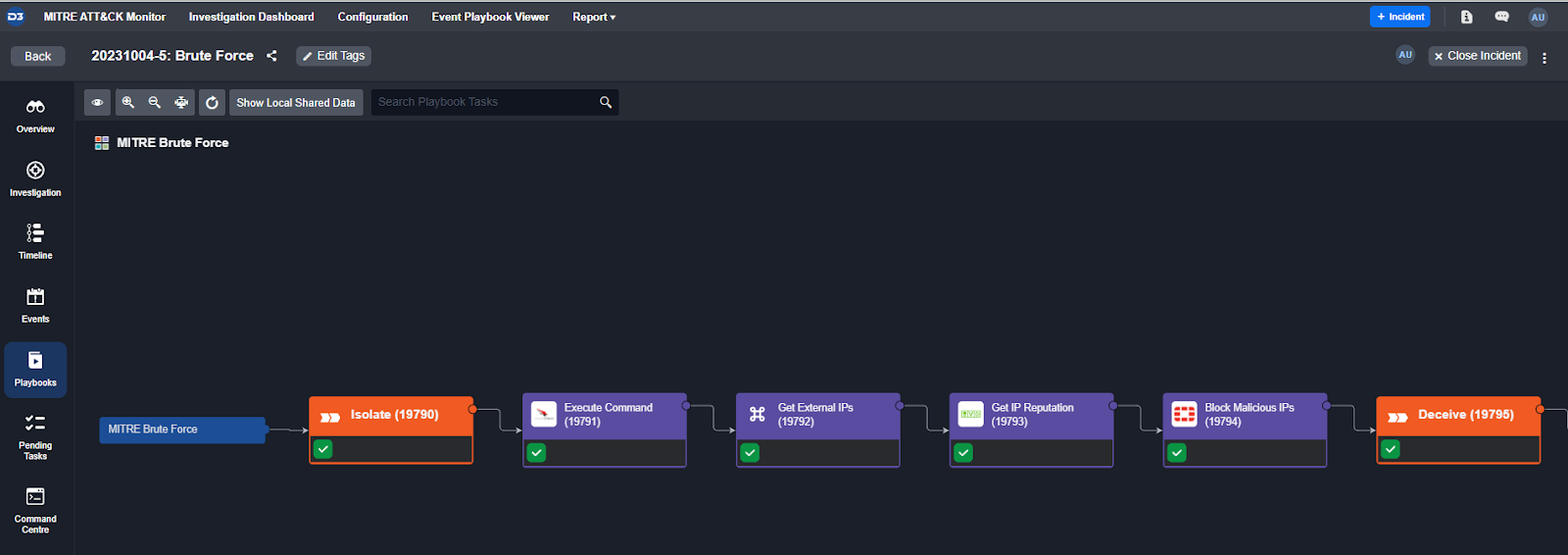
Incident Response Playbook
Analysis of Tactics and Techniques
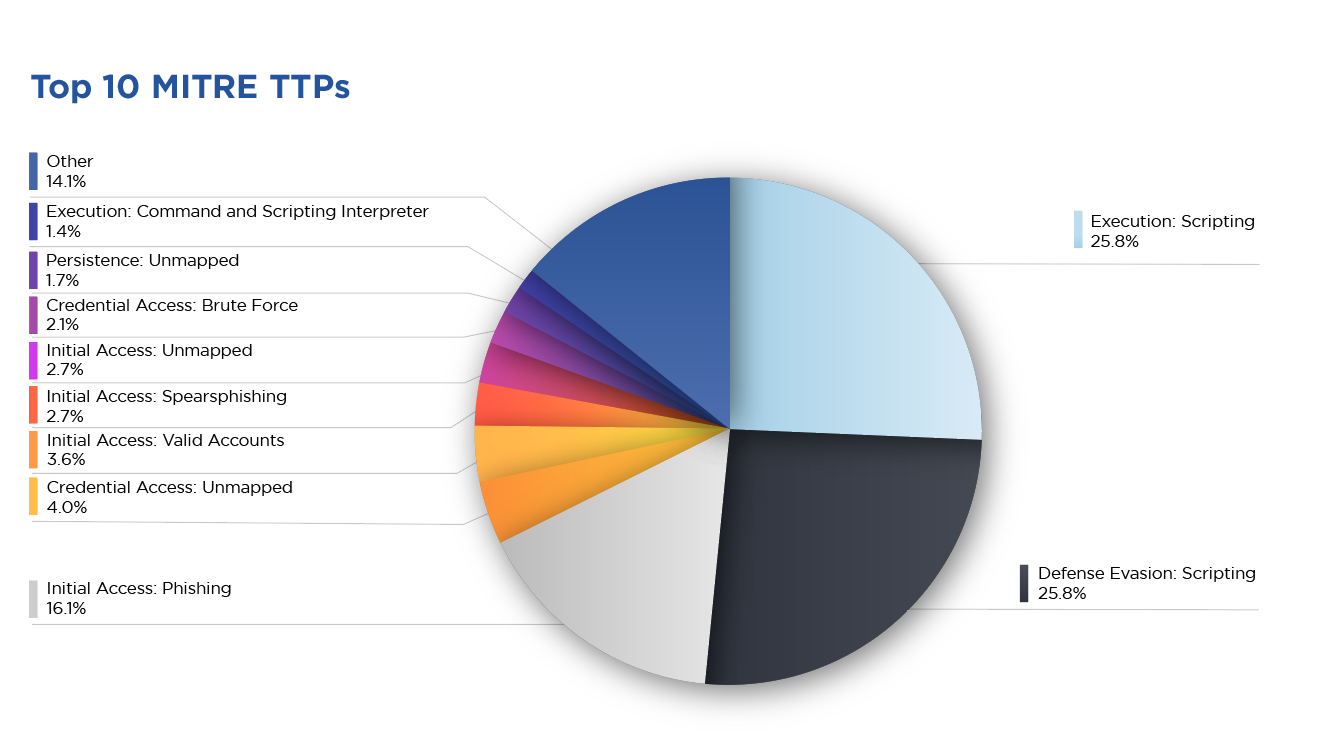
Execution: Scripting (TA0002)
The most frequently detected technique in our dataset was Execution: Scripting. Scripts are sets of commands saved in a file, intended for execution by a specific scripting language interpreter. Languages like PowerShell, Bash, Python, and JavaScript are commonly used for scripting. These scripts can automate tasks such as data collection, system configuration, and the deployment of software, including malware. Scripts can be used to download and execute malicious software without user interaction. For example, a PowerShell script can be crafted to download a ransomware payload from a remote server and execute it on the victim’s machine.
Defense Evasion: Scripting (TA0005)
The next most common technique was Defense Evasion: Scripting, a technique used by attackers to bypass security measures and remain undetected within a target network or system. This approach involves the use of scripts to modify or evade the functionalities of security software, such as antivirus programs, intrusion detection systems (IDS), and intrusion prevention systems (IPS).
Incident Response Workflow for Scripting Attacks

The workflow above uses SentinelOne to monitor active agent processes and terminate malicious ones from within the Smart SOAR platform itself. Then, it uses Microsoft Entra ID (formerly Azure Active Directory) to change the device’s script execution policies and resets the user’s password. Implementing an incident response workflow means organizations can reduce the time between detection and containment for scripting attacks.
Initial Access: Phishing & Spear Phishing (T1566)
Phishing and spear-phishing are common techniques used by attackers to gain initial access to a target’s systems or network. These methods involve the deceptive practice of sending emails that appear to be from a trusted source to induce individuals to reveal personal information, such as passwords and credit card numbers, or to convince them to download and install malware.
Incident Response Workflow for Phishing Attacks
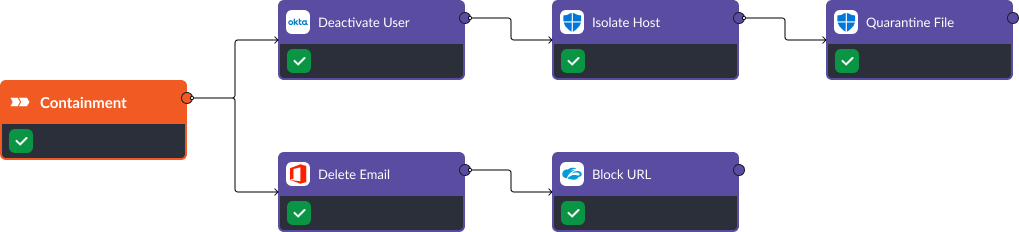
We’ve written a full blog on how to use SOAR to defend against phishing attacks. One of our many workflows for phishing is illustrated above. In this workflow, which activates during the containment stage, Okta is used to deactivate the compromised account, then Microsoft Defender for Endpoint is used to isolate the host and quarantine the file. At the same time Office 365 is used to delete the email and Zscaler is used to block access to a malicious URL or IP address with which the device may be communicating.
Phishing and spear-phishing attacks represent a significant threat as they often serve as the entry point for more sophisticated attacks. Defending against these attacks requires a combination of technical controls, user education, and robust security policies. By understanding the nature of these threats and implementing a layered defense strategy, organizations can significantly reduce their risk of falling victim to phishing and spear-phishing campaigns.
Initial Access: Valid Accounts (T1078)
The tactic of using valid accounts involves the exploitation of legitimate user credentials—such as usernames and passwords—to bypass security measures and gain unauthorized access to systems and data. This tactic is particularly dangerous because it can allow attackers to operate undetected for extended periods, blending in with normal user activities.
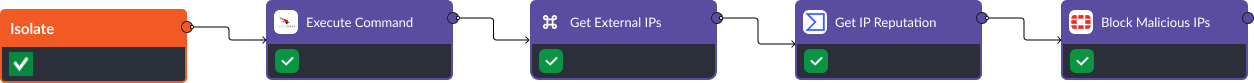
Incident Response Workflow for Valid Account Threats

The workflow above is an example of how SOAR users can automate incident response to valid account threats. It monitors user activity logs for location anomalies, comparing the detected IP locations against the users’ expected locations to identify potential unauthorized access attempts then verifies with the user before initiating a response. The verification is conducted through a secure method, ensuring the user’s legitimate confirmation of a potential breach.
Credential Access: Brute Force (T1110)
Credential access through brute force is a method employed by attackers to gain unauthorized access to a system or application by systematically trying every possible combination of usernames and passwords until the correct one is found. This approach exploits weak password policies, such as the use of common or default passwords, and relies on the absence of account lockout mechanisms or insufficient rate-limiting controls.
Incident Response Workflow for Brute Force Attacks
Similar to phishing, we’ve written a lengthy description of how to build a SOAR playbook to address brute force attacks. It’s also designed following MITRE D3FEND best practices.
Brute force attacks are rudimentary, yet, as our research shows, they are still a prevalent threat in the cybersecurity landscape, exploiting weak password practices and inadequate security policies. By implementing strong defensive measures, including robust password policies, MFA, and continuous monitoring, organizations can significantly mitigate the risk of unauthorized access through brute force methods. Educating users on secure password practices further reinforces an organization’s defense against these types of attacks.
Closing Thoughts
While incident response playbooks are critical tools in an organization’s cybersecurity arsenal, they are most effective when integrated into a comprehensive security strategy. This strategy should encompass reactive measures, like incident response, as well as proactive measures that prevent attacks from happening in the first place. By situating incident response playbooks within a broader security strategy that includes both preventive measures and a strong security culture, organizations can ensure a more robust defense against cyber threats. This holistic approach helps in effectively responding to incidents and preventing them from occurring, thereby enhancing the overall security posture and resilience of the organization.
The post The 10 Most Common MITRE Tactics & Techniques of 2023 appeared first on D3 Security.
*** This is a Security Bloggers Network syndicated blog from D3 Security authored by Pierre Noujeim. Read the original post at: https://d3security.com/blog/top-mitre-attack-tactics-and-techniques/
如有侵权请联系:admin#unsafe.sh