Organizational red teams are tasked with the critical responsibility of ensuring preparedness against real-world threats. But the ability to accurately replicate complex threat behavior can often be resource-intensive, expensive, and difficult to operationalize. As sophisticated threat actors continue to evolve their attack patterns, replicating this rapidly changing behavior can become nearly impossible. Security teams implementing red team programs also need the ability to scale and consistently repeat these attack patterns across different parts of the network to identify the true impact of the threat on the organization.
The Need to Replicate Realistic Attack Scenarios
As threat actors become more sophisticated and targeted with their methods (especially nation-state groups with specific agendas), traditional red teaming exercises can have several limitations when replicating real adversary behavior, including the inability to pivot to a different tactic if the first one is blocked.
Without accurately replicating the tactics, techniques, and procedures (TTPs) of advanced threat actors, red teams cannot assess the true resilience of an organization’s security program. Simply assuming threat actor behavior can have dire consequences on the organizational security posture and can potentially lead to data breaches, disruption of critical operations, fines, and more. By truly replicating advanced threat actor patterns and behavior, red team exercises can accurately validate security controls, ensure staff readiness, and stress-test the threat response mechanisms.
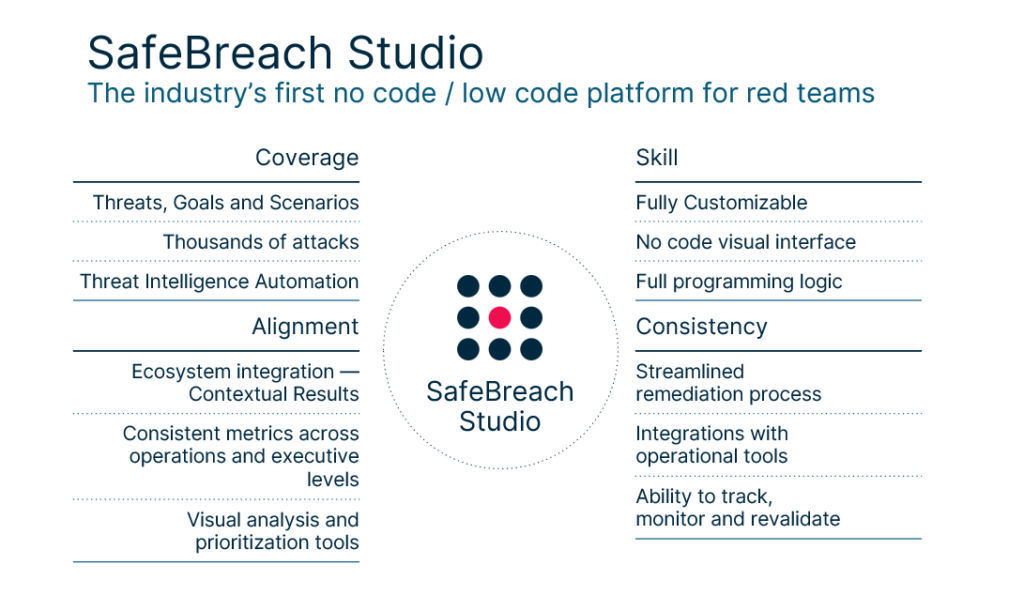
Simplifying Red Teaming with SafeBreach Studio
SafeBreach Studio was created to solve this very challenge. SafeBreach Studio is the industry’s first no-code red team platform created to meet the unique needs of red teams. It unifies every aspect of attack planning—from scenario development through execution—in a single environment. Red teamers of all skill levels can create, customize, and run sophisticated attacks using a simple drag-and-drop interface that enhances efficiency and provides the data you need to drive results—with no coding experience necessary. With SafeBreach Studio, security teams can now consistently design attack workflows that replicate real-world behavior and have the freedom to easily scale attacks and change the exercise scope, leveraging the guidance provided by the SafeBreach Platform. SafeBreach Studio provides red teams with key benefits, including:
- Ease of Use – Simple drag-and-drop interface to design attack workflows and modify attacks.
- Attack Customization – Leverage visual programming to customize every aspect of the attack kill-chain. This includes the ability to fully customize the built-in scenarios as well as create fully-custom attacks using Breach Studio.
- Scalability – Create and execute custom attacks in a consistent, repeatable way without the need for constant manual intervention.
- Minimal Cost of Execution – Leverage the SafeBreach platform’s vast attack playbook and execution capabilities to eliminate the need to hire experts and ensure maximum coverage of the available content.
- Improved Collaboration – Perform complex red-teaming and remedial blue-teaming activities within the same platform to ensure enhanced collaboration between typically siloed security teams.
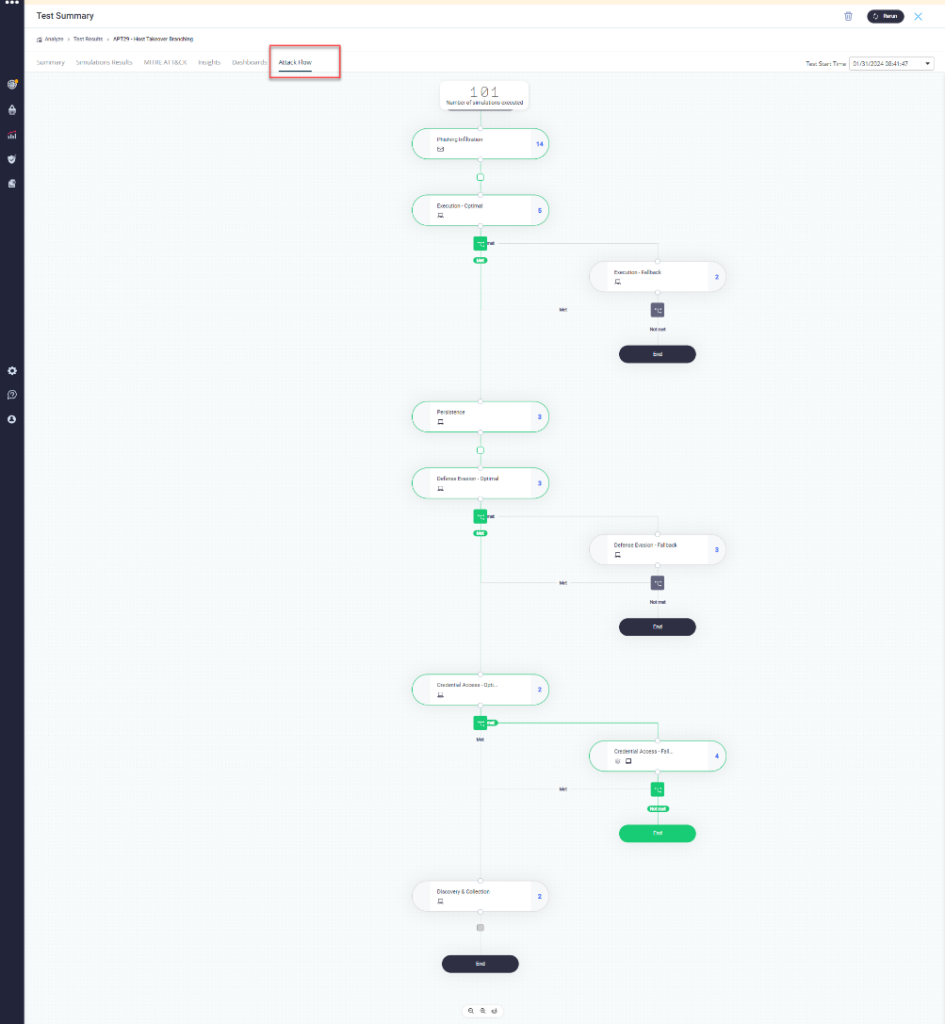
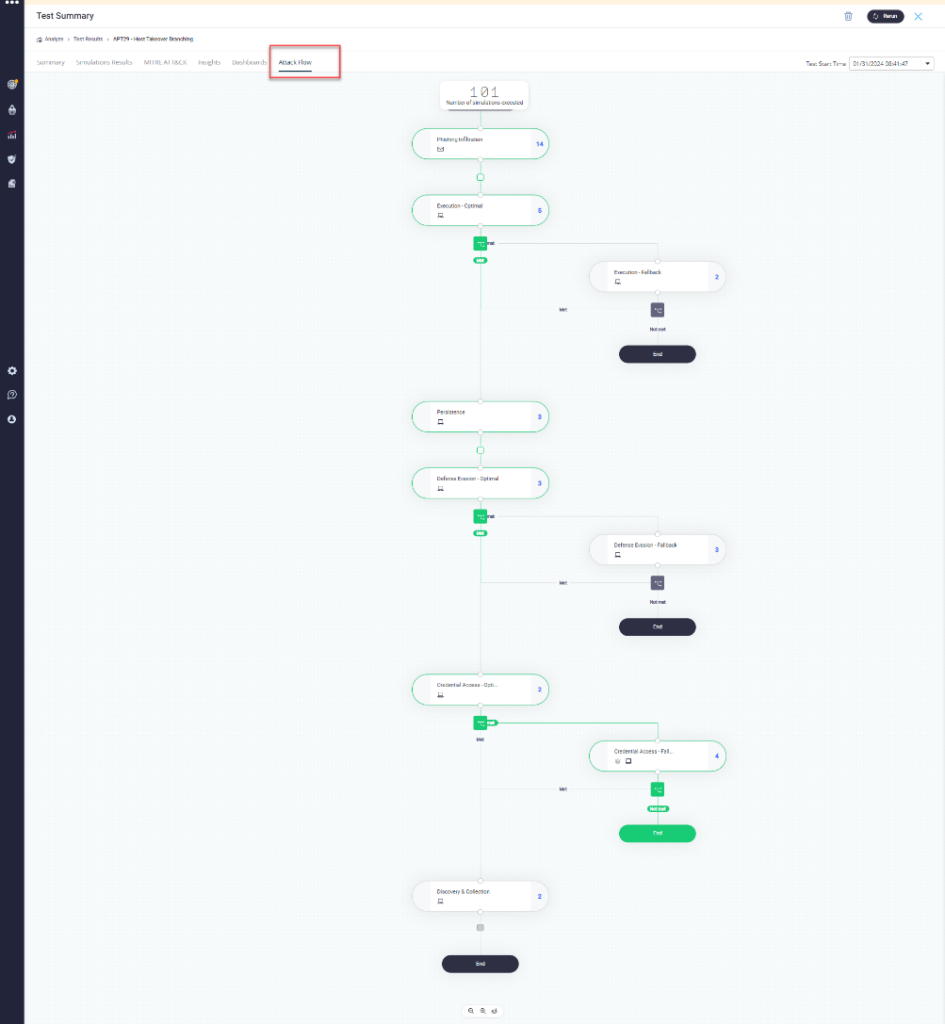
Introducing SafeBreach Studio Branching and Success Criteria
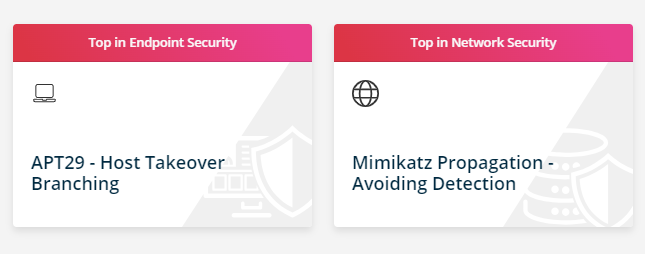
The SafeBreach platform is powered by the largest attack playbook offered by any BAS vendor with more than 28k real-world attacks. To further enable security teams to replicate realistic attack behavior, SafeBreach recently introduced branching capabilities and success criteria for progression along an attack sequence that allows attack designers to make red teaming more realistic by having the ability to create complex, conditional branches representing dynamic attacker behavior once inside the network. The platform now includes two out-of-the-box branching scenarios that showcase these new capabilities, APT29 – Host Takeover Branching and Mimikatz Propagation – Avoiding Detection:
- APT29 – Host Takeover Branching Scenario: This scenario emulates a host takeover attack inspired by APT29’s tactics. APT29, linked to Russia’s SVR, is known for being one of the most threatening advanced persistent threats (APTs) in the world. The scenario comprises consecutive actions where each step’s success determines the next. From initial intrusion to admin control, the scenario mimics a dynamic cyber threat landscape. By running this scenario, you can enhance your defenses and incident response to confront APT-style attacks effectively.
- Mimikatz Propagation – Avoiding Detection Scenario: This scenario revolves around Mimikatz, a notorious credential-harvesting tool, while evading detection. This scenario consists of conditional actions, with the success of each step dictating the next move. The execution methods vary between stealthy intrusion and evasion tactics to just executing the original Mimikatz, reflecting the adaptability of modern cyber threats. By running this scenario, you may see how an attacker would try to leverage Mimikatz in your environment with the goal of propagating within your network.
We are continuously updating our scenario library with additional branched scenarios to arm defenders against the latest threats.
These scenarios allow security teams to not only understand how threat actors could first attempt their attacks, but also highlight the backup techniques that they can leverage if the primary techniques are not successful. These branching scenarios can be further customized by utilizing the newly introduced Success Criteria as well as the Wait Period capabilities. Setting up these new branching attacks is extremely easy and can be summarized below:
- To begin, click on the connector between any of the two steps in the above scenarios. Note – there must be a step following the step you want to branch from.
- Define the success criteria, which allows you to determine the conditions for which to take action/ next steps. The platform allows teams to define what makes a step partially or completely successful based on the outcome of one or multiple attacks. Analysts have full flexibility to determine how best to proceed if an attack is blocked. They can choose to completely abandon the original attack flow and pivot to alternative, backup attacks.
- Define a parallel set of steps for the scenario to proceed based on the previously defined success criteria. If the condition is met, the scenario will continue with the basic flow. If not, it will go to a new step on an alternate branch that is automatically created.
- Defining a wait period adds another layer of realism to the scenario. No attacker in a real environment will keep attempting different techniques back-to-back without understanding why the previous attack was successful or failed. By adding a wait period, users can easily define a time period after which the next step would be executed.
While it is important to run realistic attacks in your network, it is equally important to analyze the executed attack flow to understand which steps were successful and which were not. This is one of the best ways to understand how an attacker might execute these attacks in real-world scenarios, allowing you to be better prepared against them.
SafeBreach’s product experts recently demonstrated the new enhanced conditional branching capabilities of SafeBreach Studio. This discussion was focused around:
- How adversaries leverage complex attacks to bypass organizational security
- How SafeBreach can help you replicate dynamic and realistic attacker behavior without complex coding or programming
- How visually understanding an attacker’s behavior can help you prepare better against it
View the discussion to gain valuable insight on leveraging SafeBreach Studio’s red teaming capabilities to prepare your organization against today’s evolving threats. Schedule a consultation with a SafeBreach team member to learn more about this capability. If you are an existing SafeBreach customer and would like to leverage these capabilities in your organization, please reach out to your customer success representative.
You Might Also Be Interested In
Get the latest
research and news
The post Replicating Realistic Threat Behavior is Critical to Red Teaming, But It Doesn’t Have to Be Complicated appeared first on SafeBreach.
*** This is a Security Bloggers Network syndicated blog from SafeBreach authored by SafeBreach. Read the original post at: https://www.safebreach.com/blog/replicating-realistic-threat-behavior-red-teaming/