2024-3-11 16:31:54 Author: www.mobile-hacker.com(查看原文) 阅读量:17 收藏
![]()
APKDeepLens is a Python-based tool that is used for scanning Android applications (APK files) to identify potential security vulnerabilities, with a particular focus on the OWASP Top 10 mobile vulnerabilities. It was developed by Deepanshu Gajbhiye and presented at Blackhat MEA 2023 and will be at Blackhat ASIA 2024. This tool is designed for a Windows and Linux desktop machines. In this blog I will show you how to install and run it on non-rooted Android device using Termux. This brings convenience of analyzing Android apps directly on device either for vulnerability scan, or to understand them before installation. This tool can automate the scanning while on the go. Besides downloaded apps, you can analyze even app already installed on you smartphone.
APKDeepLens functionality
APKDeepLens uses jadx to decompile input APK file. Using the decompiled source code, it will search for specific strings by parsing the output. The output lists app’s:
- Package name
- Build version code
- Compiled SDK version
- Permissions
- Dangerous permissions
- Activities
- Exported Activities
- Services
- Exported services
- Receivers
- Exported receivers
- Providers
- File paths
- Hard-coded secrets (IP addresses, tokens, API keys, private keys, etc.)
- Insecure connections (
http,ftp,smtp,JavaScript)
The scan output might lead to identify potential entry points that might lead to identify app vulnerabilities. However, without further manual analysis, it would be very difficult. By default, the output is displayed in console, however the report can be exported in json, pdf or html file.
Installation in Termux
Setup process for desktop is straightforward, as explained on the GitHub page. However, the installation process on Android in Termux is slightly different. Before installation, it is important to have installed Termux from GitHub or F-Droid store. The important thing is not to download it from Google Play, because Termux builds on Google Play store are deprecated and no longer supported. Additionally, user needs to install java development kit, set JAVA_HOME environment variable and resolve the issue with xhtml2pdf library that is responsible for generating pdf output.
Before installation process, make sure to update and upgrade, install java and set the environment variable using commands:
apt update
apt upgrade
pkg install openjdk-17
export JAVA_HOME=/data/data/com.termux/files/usr/opt/openjdkRestart the Termux to apply changes. Continue by installing the APKDeepLens using commands:
git clone https://github.com/d78ui98/APKDeepLens.git
cd /APKDeepLens
python3 -m venv venv
source venv/bin/activate
pip3 install -r requirements.txtThe installation of requirements results in an error where xhtml2pdf module can’t be installed. This module is responsible for generating reports in pdf format. I wasn’t able to solve this error, but I was able to bypass it by editing and commenting the import of the module in report_gen.py file, see Figure 1. As a result, APKDeepLens now cant generate pdf reports.
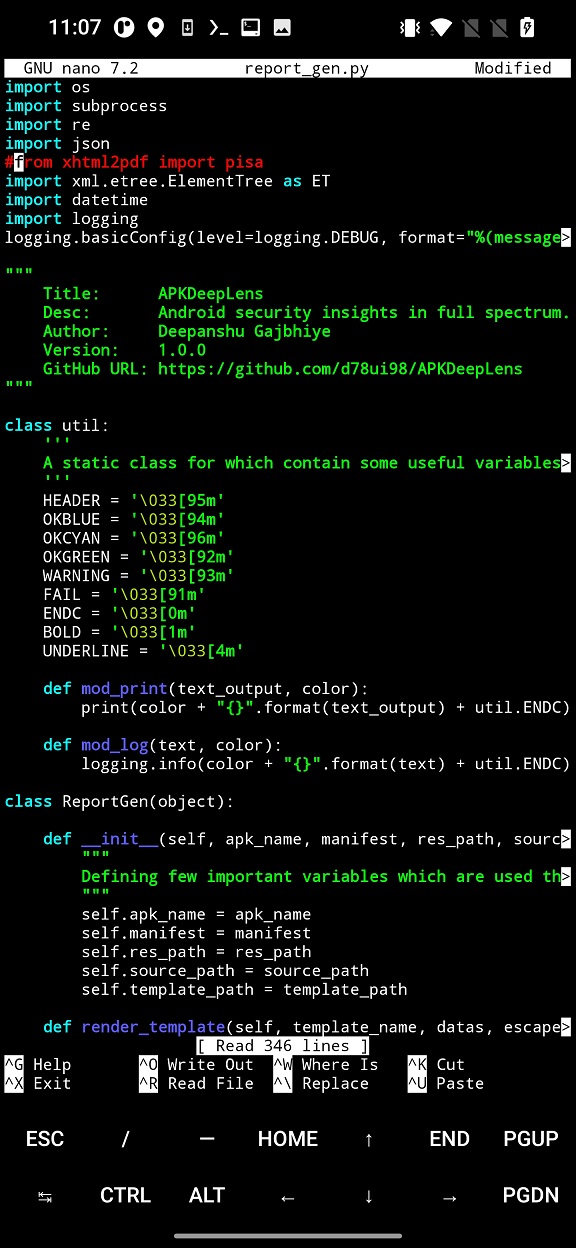
xhtml2pdf module in report_get.pyUsage
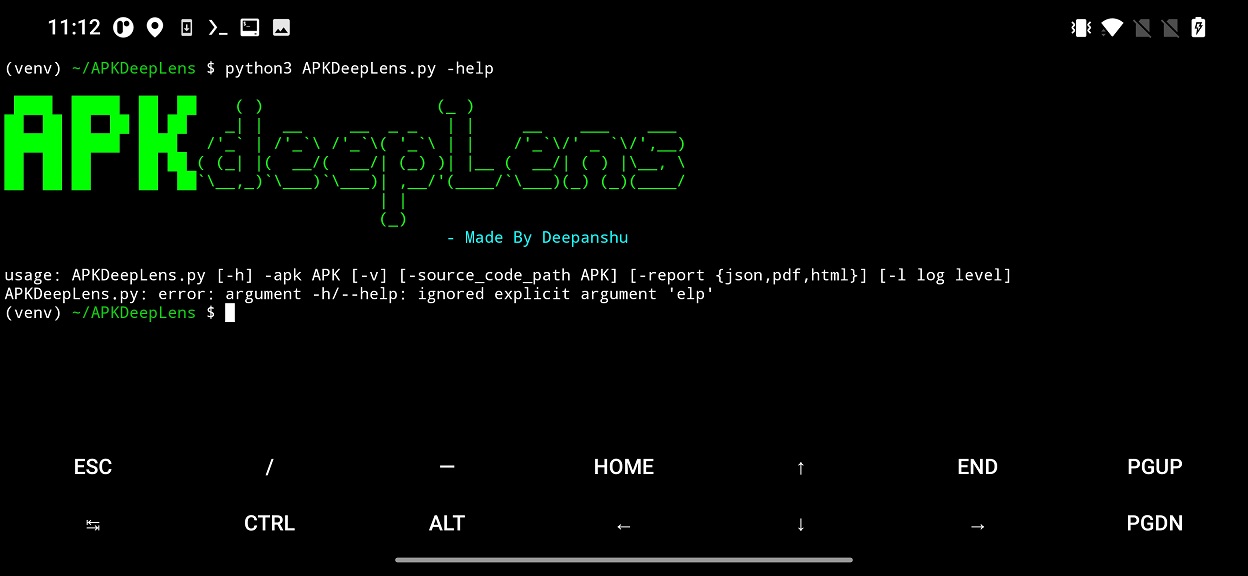
Now you can run the APKDeepLens in Termux. List its options using python3 APKDeepLens.py -help command.
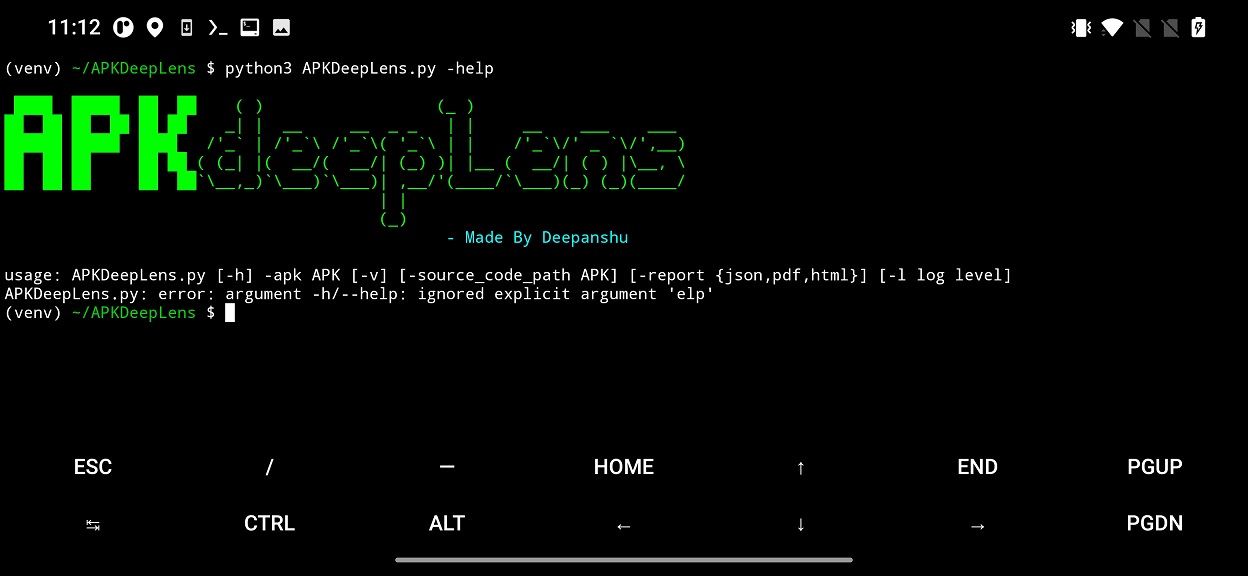
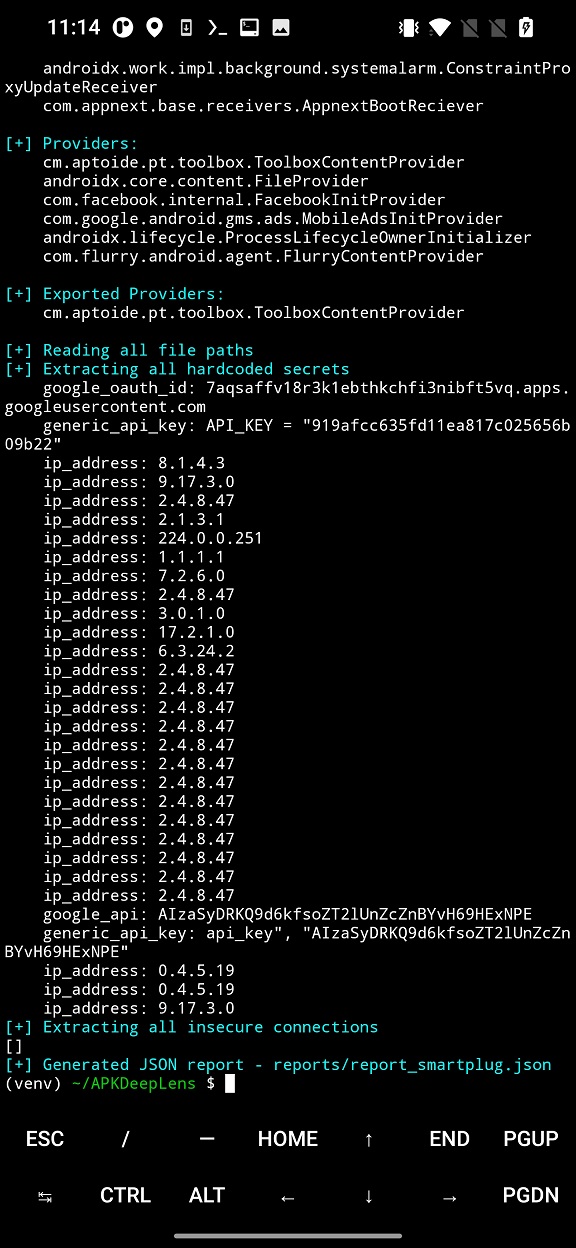
To scan app, input file path to Android app as -apk parameter. The analysis result is displayed in terminal, as visible in Figure 3.
Analyze installed apps
Using the APKdeepLens, you can analyze not just downloaded apk files (from alternative sources), but also already installed applications. All you need is to find the file path to the analyzed app. Apk files are stored under random file path. To get the file path for all third party installed apps, you can use command pm list packages -f -3. The output contains path to apk files and their package name that identify the application. You can manually list the output or use grep to filter specific apps using a keyword. In example below I will search for Facebook app (pm list packages -f -3 | grep facebook).
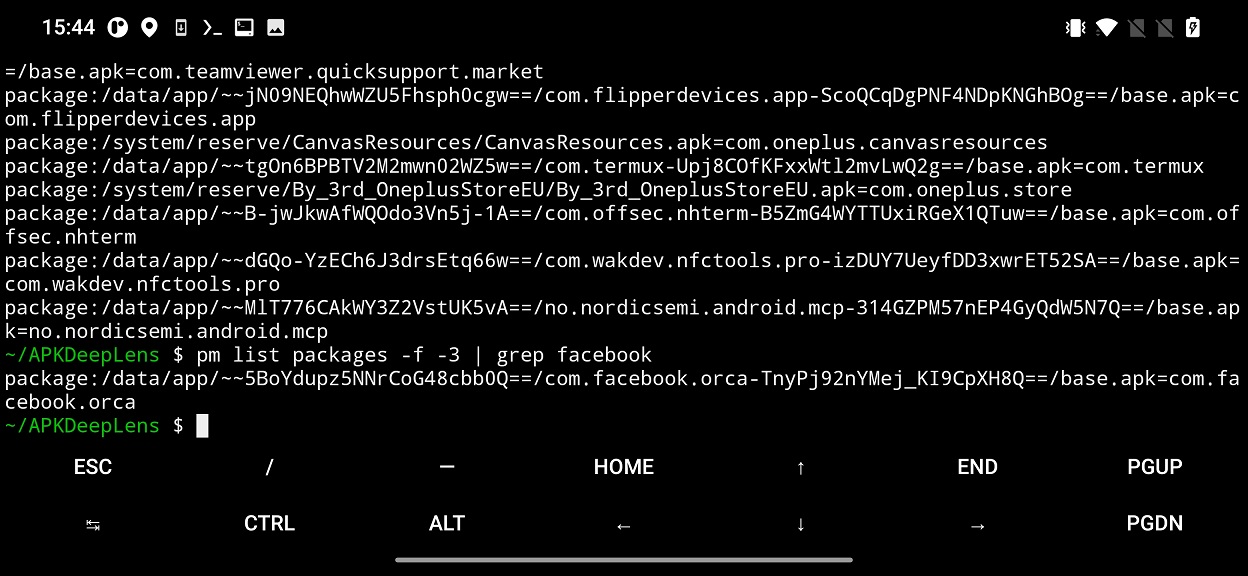
From the result, copy path to the app and insert it to APKDeepLens as -apk argument.
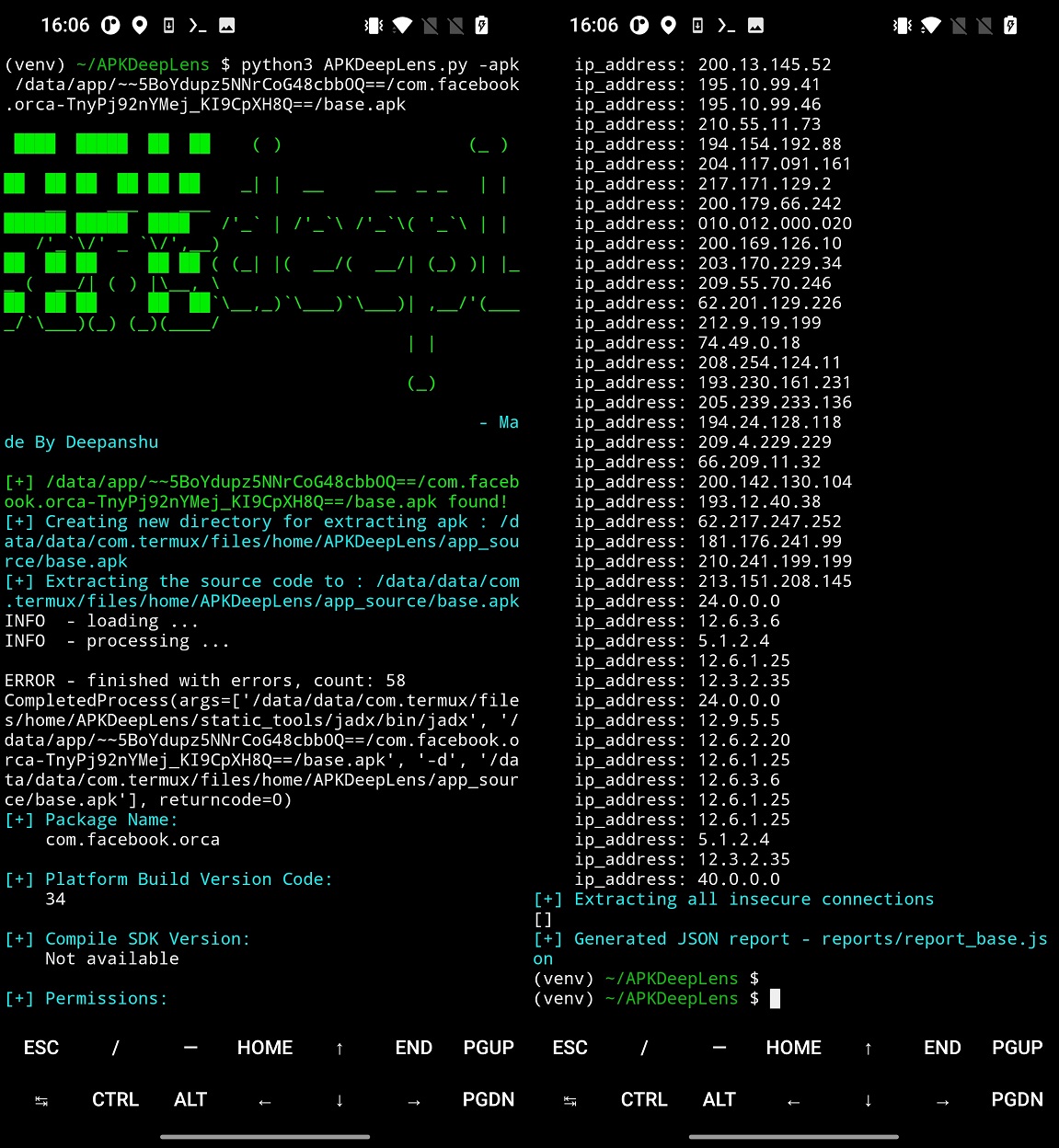
There is one downside. This tool stores the scans under apk file name directory in app_sources. This means that if you are going to scan installed apps, you always need to remove or rename the decompiled sources e.g /app_sources/base.apk/ directory. In Figure 6 I removed the decompiled data, otherwise they will not be overwritten by APKdeepLens.
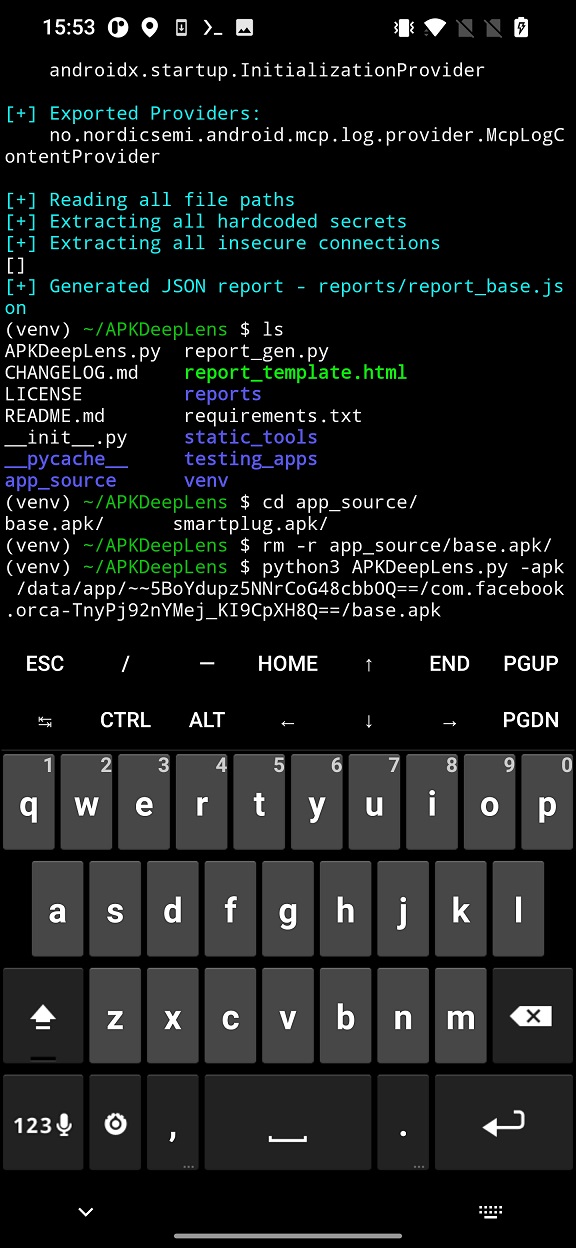
base.apk outputConclusion
This tool may offer capabilities for permissions analysis and searching for potential app secrets such as hard-coded tokens, API keys, IP addresses, etc. It aims to help users understand app’s behavior and identify entry points for potential security risks. As a possible benefit, you can customize the script to expand its functionality or to save time scan only for information you are interested in.
如有侵权请联系:admin#unsafe.sh