2024-3-15 13:46:13 Author: cyble.com(查看原文) 阅读量:27 收藏
Executive Summary
In the last week of January 2024, a patch was released to address a vulnerability found in aiohttp. This security issue impacts aiohttp versions prior to 3.9.2. The security flaw (CVE-2024-23334) is a directory traversal vulnerability in aiohttp that allows unauthenticated, remote attackers to access sensitive information from arbitrary files on the server if exploited.
Aiohttp is a versatile asynchronous HTTP client/server framework designed for asyncio and Python. Its flexibility and extensive capabilities make aiohttp a comprehensive solution for a wide range of asynchronous tasks. Cyble’s ODIN scanner, for instance, has identified over 43,000 Internet-exposed aiohttp instances worldwide, as shown in the figure below.

Figure 1 – Exposure of aiohttp instances
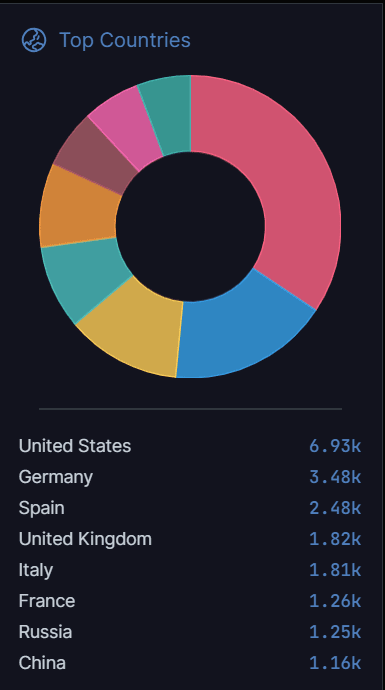
These instances are particularly prevalent in the United States, Germany, and Spain, and other regions, as shown below.

Figure 2 – Geographical Distribution of aiohttp exposures.
Given the prevalence of exposed instances, they are likely targets for Threat actors (TAs). Immediate patching to the latest versions is strongly recommended.
Vulnerability Details
Directory Traversal vulnerability in aiohttp
CVE-2024-23334
CVSS:3.1:
7.5
Severity:
High
Vulnerable Versions:
Prior to version 3.9.2
Description:
A directory traversal vulnerability has been identified in aiohttp, an asynchronous HTTP client/server framework for asyncio and Python. If exploited successfully, this vulnerability enables unauthenticated remote attackers to access sensitive information on the server.
Cyble Global Sensor Intelligence (CGSI) findings
On February 27, a Proof of Concept (PoC) for this exploit became available, accompanied by a comprehensive YouTube video illustrating its functionality.
On the subsequent day, February 29, 2024, CGSI began detecting multiple scanning attempts aimed at CVE-2024-23334, with such activity continuing thereafter. The below image shows the attack observed in the CGSI sensor.

Figure 3 – Scanning attempts on aiohttp servers captured by CGSI
It is evident that TAs swiftly attempted to exploit this vulnerability shortly after proof-of-concepts became publicly available.
Technical Details
aiohttp as an open-source Python library or framework that is specifically designed to offer asynchronous HTTP client and server capabilities. When setting up aiohttp as a web server and defining static routes for serving files, it’s essential to specify the root directory where the static files are located.
In addition, the option ‘follow_symlinks’ can be used to determine whether to follow symbolic links outside the static root directory. When ‘follow_symlinks’ is set to True, there is no validation to check if a given file path is within the root directory. This issue can lead to a directory traversal vulnerability, resulting in unauthorized access to arbitrary files on the server, even when symlinks are not present.
Threat Actor Attribution
After analyzing the scanning attempts detected by our Cyble Global Sensor Intelligence (CGSI) , we observed that one of the IP addresses 81[.]19[.]136[.]251 has been tagged in several instances of LockBit activity and also indicates an association with the ShadowSyndicate group.
ShadowSyndicate, an active cyber threat group since July 2022, operates as a Ransomware-as-a-Service (RaaS) affiliate, leveraging various ransomware strains to carry out their attacks.
Security researchers from Group-IB have been able to link this group to various ransomware incidents in the past, which include Quantum ransomware activity in September 2022, Nokoyawa ransomware campaigns occurred in October 2022, November 2022, and March 2023, as well as ALPHV ransomware activity in February 2023.”. These incidents illustrate ShadowSyndicate’s prolific involvement in ransomware operations over a relatively short period.
Conclusion
The prevalence of servers running on unpatched versions of the aiohttp framework poses a significant risk in cybersecurity. While attacks haven’t been observed utilizing this specific vulnerability at present, the scanning attempts by the Shadowsyndicate group underscore the looming threat.
Given their demonstrated interest, it’s imperative for organizations to act swiftly by updating to the recommended version 3.9.2 and implementing necessary mitigations. Failure to address these vulnerabilities promptly could expose systems to exploitation in the future.
Indicators Of Compromise
| Indicators | Indicator Type | Description |
| 81[.]19[.]136[.]251 | IP | IP observed attempting to exploit CVE-2024-23334 |
| 157[.]230[.]143[.]100 | IP | IP observed attempting to exploit CVE-2024-23334 |
| 170[.]64[.]174[.]95 | IP | IP observed attempting to exploit CVE-2024-23334 |
| 103[.]151[.]172[.]28 | IP | IP observed attempting to exploit CVE-2024-23334 |
| 143[.]244[.]188[.]172 | IP | IP observed attempting to exploit CVE-2024-23334 |
References
https://www.group-ib.com/blog/shadowsyndicate-raas
https://github.com/aio-libs/aiohttp/security/advisories/GHSA-5h86-8mv2-jq9f
Related
如有侵权请联系:admin#unsafe.sh