
2024-3-15 21:0:0 Author: www.tenable.com(查看原文) 阅读量:6 收藏

Check out CISA’s latest best practices for protecting cloud environments, and for securely integrating on-prem and cloud IAM systems. Plus, catch up on the ongoing Midnight Blizzard attack against Microsoft. And don’t miss the latest CIS Benchmarks. And much more!
Dive into six things that are top of mind for the week ending March 15.
1 - Tips for integrating on-prem and cloud IAM systems
Ah, the joys of hybrid environments! So many benefits – and so many security challenges.
Here’s one critical and very common difficulty: Securely meshing the different identity and access management (IAM) systems in your on-premises and cloud environments.
Anyone struggling with this may want to peruse the guide “Hybrid Identity Solutions Guidance” that the U.S. Cybersecurity and Infrastructure Security Agency (CISA) published this week.
The 42-page document seeks to help organizations grasp identity management capabilities; understand the pros and cons of implementation options; and decide how to carry out implementations.
Here are a couple of high-level recommendations from CISA:
- Migrate to cloud-based, passwordless authentication
- Transition from on-prem federation approaches to a cloud-primary authentication approach
Topics addressed in the guide include:
- Hybrid identity architecture and model
- Federated authentication
- Pass-through authentication
- Cloud-primary authentication
- Multi-factor authentication
- Context-based access control
Hybrid Identity Architecture
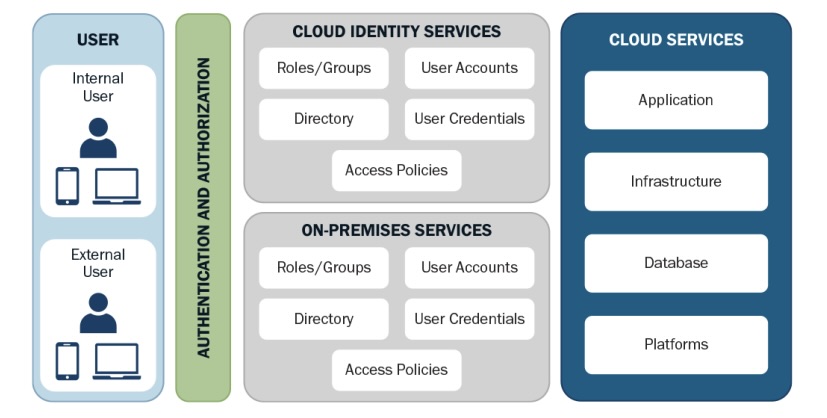
(Credit: CISA)
For more information about IAM security, check out these Tenable resources:
- “Why You Need Contextual Intelligence in the Age of Identity-First and Zero Trust Security, and How to Get It Now” (on-demand webinar)
- “Identities: The Connective Tissue for Security in the Cloud” (blog)
- “Strengthen the Effectiveness of Your Identity Security Program with Zero Trust Maturity” (on-demand webinar)
- “Identity has breached the ecosystem” (white paper)
- “Poor Identity Hygiene at Root of Nation-State Attack Against Microsoft” (blog)
2 - Midnight Blizzard swiped Microsoft’s source code, broke into its internal systems
And the news about Midnight Blizzard’s cyberattack against Microsoft keeps getting worse. Here’s the latest: The nation-state hacking group accessed Microsoft source code repositories and breached internal systems – and the attack is ongoing.
So said Microsoft last week in an update about the Midnight Blizzard debacle, which began in November 2023, after the hackers compromised a legacy, non-production test account that lacked multi-factor authentication protection.
Microsoft disclosed the attack in January, saying then that Midnight Blizzard had exfiltrated information from some employee email accounts, including from senior leaders and from cybersecurity and legal staffers.

In last week’s update, Microsoft said that Midnight Blizzard, which is backed by the Russian government’s Foreign Intelligence Service (SVR), is actively trying to exploit stolen “secrets” shared via email between Microsoft and some customers.
According to an Associated Press article, the stolen information includes “cryptographic secrets” such as passwords, certificates and authentication keys.
“A company spokesman would not characterize what source code was accessed and what capability the hackers gained to further compromise customer and Microsoft systems,” reads the AP article titled “Microsoft says it hasn’t been able to shake Russian state hackers.”
“We should all be furious that this keeps happening,” Tenable CEO and Chairman Amit Yoran told the AP. “These breaches aren’t isolated from each other and Microsoft’s shady security practices and misleading statements purposely obfuscate the whole truth.”
In a LinkedIn post, Yoran further added that “Microsoft continues to obfuscate and drip feed the truth from its executive email hack” and predicted that it’ll likely take “several months before the full story is known.”
For more information about Midnight Blizzard, which is also known as Nobelium, Cozy Bear and APT29, and about the Microsoft attack:
- “CISA, NCSC issue cloud security advisory on Russia-backed APT29” (Tenable)
- APT29 (MITRE)
- “Microsoft email breach: Attackers accessed internal systems, source code” (CSO)
- “Russian hackers breached Microsoft, HPE corporate mailboxes” (Help Net Security)
- “Hackers backed by Russian government reportedly breached US government agencies” (The Verge)
3 - CISA and NSA outline best practices for cloud security
Securing cloud environments can be a thorny endeavor, which is why cybersecurity teams can’t get enough insights and advice about this topic. If you want a fresh influx of cloud security tips, check out a handful of new guides from the U.S. National Security Agency (NSA) and CISA.
These five “cybersecurity information sheets,” as CISA calls them, not only include best practices but also recommended mitigations for areas including cloud IAM; keys management; network segmentation and encryption; and data protection.
“CISA and NSA encourage all organizations to review the practices and implement the mitigations provided in the joint CSIs to help strengthen their cloud security,” reads the joint statement “CISA and NSA Release Cybersecurity Information Sheets on Cloud Security Best Practices.”

Ready to dive in? Here are the links to the documents:
- Use Secure Cloud Identity and Access Management Practices
- Use Secure Cloud Key Management Practices
- Implement Network Segmentation and Encryption in Cloud Environments
- Secure Data in the Cloud
- Mitigate Risks from Managed Service Providers in Cloud Environments
For more information about cloud security trends and best practices, check out these Tenable resources:
- “Beyond the Horizon: Top 5 Cloud Security Trends to Watch in 2024” (blog)
- “When, Why and How Your Security Team Needs to Harness the Power of CNAPPs” (on-demand webinar)
- “Level Up Your Cloud Security Strategy” (blog)
- “Strategies, Solutions and Best Practices for Optimizing Your Cloud Environment -- A Cloud Security Master Class” (on-demand webinar)
- “Cloud Leaders Sound Off on Key Challenges” (blog)
4 - Poll: A quick check on configuration management practices
During our recent webinar about vulnerability management, we polled attendees about configuration management. Check out what they said about their configuration-management challenges and assessment methods.
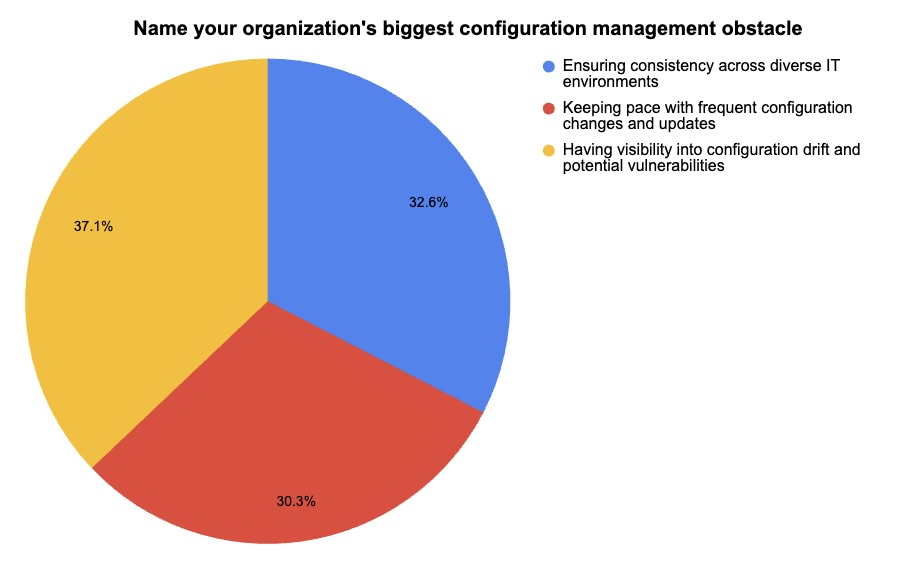
(178 respondents polled by Tenable, March 2024)
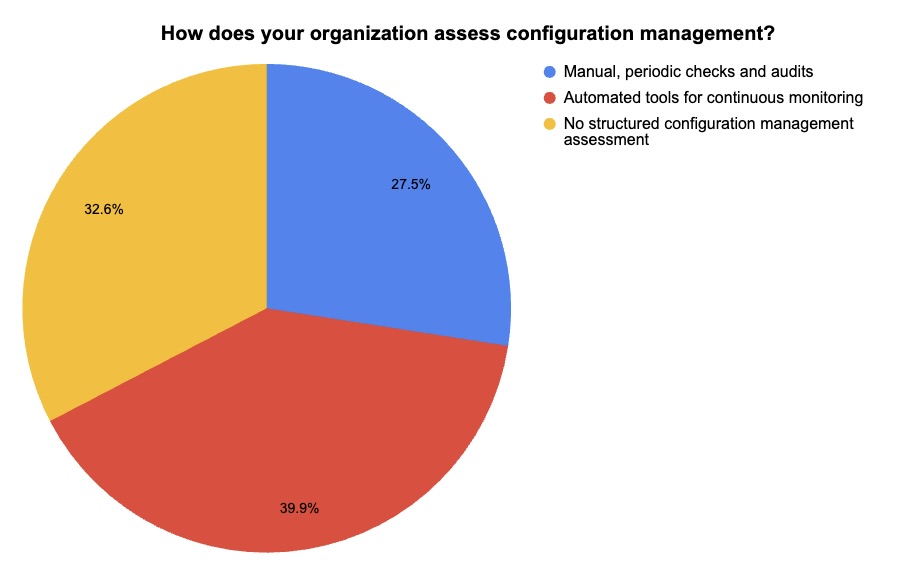
(193 respondents polled by Tenable, March 2024)
Want to take a deeper dive into configuration management within a vulnerability management context? Watch the webinar on-demand!
5 - CIS updates Benchmarks for Azure, Windows, Intune
The latest updates to the Center for Internet Security’s CIS Benchmarks are out, and they include new recommendations to securely configure Microsoft Azure, Microsoft Intune and Microsoft Windows.
Specifically, these CIS Benchmarks were updated in February:
- CIS Microsoft Azure Foundations Benchmark v2.1.0
- CIS Microsoft Intune for Windows 10 Benchmark v3.0.0
- CIS Microsoft Intune for Windows 11 Benchmark v3.0.0
- CIS Microsoft Windows 10 Enterprise Benchmark v3.0.0
- CIS Microsoft Windows 11 Enterprise Benchmark v3.0.0

CIS Benchmarks are secure configuration guidelines intended to harden products against cyberattacks. Currently, CIS offers more than 100 Benchmarks for 25-plus vendor product families.
There are CIS Benchmarks for cloud provider platforms; databases; desktop and server software; mobile devices; operating systems; and more.
To get more details, read the CIS blog “CIS Benchmarks March 2024 Update.” For more information about the CIS Benchmarks list, check out its home page, as well as:
- “How to use CIS benchmarks to improve public cloud security” (TechTarget)
- “How to Unlock the Security Benefits of the CIS Benchmarks” (Tenable)
- “CIS Benchmarks Communities: Where configurations meet consensus” (Help Net Security)
- “CIS Benchmarks: DevOps Guide to Hardening the Cloud” (DevOps)
CIS Benchmarks (CIS)
6 - CISA’s security attestation form for tech vendors is ready
Looking to sharpen and update the cybersecurity questionnaire your organization makes prospective software vendors fill out? If so, you might want to take a look at CISA’s “Secure Software Development Attestation Form,” which was finalized and released this week.
The form, which software vendors selling to the U.S. federal government will have to submit, covers four software development practices:
- Developing the software in a secure environment where, for example, multi-factor authentication is required and sensitive data is encrypted
- Protecting source code supply chains by using automated tools to assess the security of in-house and third-party code components, and to manage their vulnerabilities
- Tracking the origins of their products’ in-house code and third-party components
- Continuously checking for and addressing software vulnerabilities

“We envision a software ecosystem where our partners in state and local government, as well as in the private sector, also seek these assurances and leverage software that is built to be secure by design,” reads a blog by Federal CISO Chris DeRusha and CISA Executive Assistant Director Eric Goldstein.
To get more details:
- Check out the “Secure Software Development Attestation Form”
- Read the blog “Biden Administration Takes Step to Ensure Secure Development Practices”
For more information about assessing the security practices of prospective software vendors:
- “5 Key Questions When Evaluating Software Supply Chain Security” (Dark Reading)
- “Commercial Software Assessment Guideline” (University of California Berkeley)
- “SaaS and Third-Party Risk: Is Your Organization Asking the Hard Questions?” (Dark Reading)
- “Third-party risks: How to reduce them” (SC Magazine)
- “US government software suppliers must attest their solutions are secure” (Help Net Security)

Juan Perez
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
Related Articles
- Active Directory
- Center for Internet Security (CIS)
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Government
Cybersecurity News You Can Use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Try Tenable Web App Scanning
Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.
Your Tenable Web App Scanning trial also includes Tenable Vulnerability Management and Tenable Lumin.
Buy Tenable Web App Scanning
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Try Tenable Lumin
Visualize and explore your exposure management, track risk reduction over time and benchmark against your peers with Tenable Lumin.
Your Tenable Lumin trial also includes Tenable Vulnerability Management and Tenable Web App Scanning.
Buy Tenable Lumin
Contact a Sales Representative to see how Tenable Lumin can help you gain insight across your entire organization and manage cyber risk.
Thank You
Thank you for your interest in Tenable Lumin. A representative will be in touch soon.
Request a demo of Tenable Security Center
Please fill out this form with your contact information.
A sales representative will contact you shortly to schedule a demo.
* Field is required
Request a demo of Tenable OT Security
Get the Operational Technology Security You Need.
Reduce the Risk You Don’t.
Request a demo of Tenable Identity Exposure
Continuously detect and respond to Active Directory attacks. No agents. No privileges.
On-prem and in the cloud.
Request a Demo of Tenable Cloud Security
Exceptional unified cloud security awaits you!
We’ll show you exactly how Tenable Cloud Security helps you deliver multi-cloud asset discovery, prioritized risk assessments and automated compliance/audit reports.
See
Tenable One
In Action
Exposure management for the modern attack surface.
See Tenable Attack Surface Management In Action
Know the exposure of every asset on any platform.
Thank You
Thank you for your interest in Tenable Attack Surface Management. A representative will be in touch soon.
Try Tenable Nessus Professional Free
FREE FOR 7 DAYS
Tenable Nessus is the most comprehensive vulnerability scanner on the market today.
NEW - Tenable Nessus Expert
Now Available
Nessus Expert adds even more features, including external attack surface scanning, and the ability to add domains and scan cloud infrastructure. Click here to Try Nessus Expert.
Fill out the form below to continue with a Nessus Pro Trial.
Buy Tenable Nessus Professional
Tenable Nessus is the most comprehensive vulnerability scanner on the market today. Tenable Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Try Tenable Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Tenable Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Learn How Tenable Helps Achieve SLCGP Cybersecurity Plan Requirements
Tenable solutions help fulfill all SLCGP requirements. Connect with a Tenable representative to learn more.
如有侵权请联系:admin#unsafe.sh