2024-3-21 18:0:0 Author: bishopfox.com(查看原文) 阅读量:26 收藏
In February, the cybersecurity community was provided with an unauthorized public information disclosure that gave an unprecedented look into some adversarial tools and tactics leveraged by the Chinese government, as well as specific campaigns and capabilities deployed against international companies and governments.
The data came from a private Chinese company called iSoon, also known as Auxun, which sold its tools and services to multiple Chinese government entities. Comprising documents and chat logs largely from 2022, while the leak was informative, it was incomplete in terms of in-depth technical details and evidence. However, a 44-page whitepaper included within provided a very interesting look at a tool used to manage and carry out cyber operations -- The integrated operations platform (一体化作战平台). The following provides selected highlights and our analysis of this platform’s claimed capabilities, design, and features based on the available information. (Screen shots below are taken directly from the dump. We wanted to provide them “as is” for context and have detailed interesting elements in text to compensate for the low resolution.)
Summary

Highlights
The following are some key takeaways of the integrated operations platform:
- It’s a standardized cyber campaign resource, collaboration, and mission management platform designed for iSoon and the Ministry of Public Security (MPS).
- The integrated operations platform encompasses both internal and external applications and networks. The internal application is mainly for mission and resource management. The external application is designed to carry out cyber operations.
- The platform provides data for various stakeholders (upper management and business entity, operations, etc.) on each mission and overall operator performance. It also had a reward management system to award points to operators for each completed mission. Management stakeholders can then review operators’ performance and comment on their work.
- The external application and systems used for cyber campaigns have specific, evasive capabilities to avoid detection and hinder response and attribution, such as self-destruct, evidence removal, and use of non-Chinese language and time zones to help obfuscate operators’ locations and nationality.
- Exploits/payloads are stored, and can be managed, from the platform.
- Sandbox environments are available on both internal and external applications for analysis of the hacking tools and exfiltrated data from targets of interest.
- The internal application is used to maintain a community knowledge base for operators to share their experiences and techniques about tools, vulnerabilities, and social engineering methodologies.
- The application can deploy, manage, and securely decommission the virtual private server (VPS) systems used for cyber campaigns.
Integrated Operations Platform (一体化作战平台)
The integrated operations platform is an offensive cyber campaign management platform developed by iSoon and used by the company in its own campaigns, as well as sold to the MPS. The single platform allows them to standardize and improve service integration, resources efficiencies, team collaboration, and platform security.

The platform consists of two applications (an internal and an external application) split between two private networks, with a firewall that segments the two networks. The internal application is referred to as the integrated operations intranet platform (一体化作战内网平台) and the external application is referred to as the integrated operations extranet platform (一体化作战外网平台). Both of these applications appear very similar but have distinct functionalities and roles. The internal network consists of the internal application and Command and Control (C2) terminals that send out encrypted commands to external C2 terminals over an encrypted out-of-band connection. The external application and private network are used to hide the identity of operators and direct attack campaigns through anonymously registered virtual private servers (VPS) that are purchased via potentially unwitting host providers allowing attack activity to hide in the noise. The external application manages the VPSs, payloads and exploits, as well as link generation used for the cyber campaign. Connection to the internet is anonymized through a proxy layer (likely Tor or a similar service) before reaching the target host to conceal their tracks.
Built for Ministry of Public Security
The primary user of this platform is the TZ cyber unit in the MPS. TZ is noted in the leaked documents as an abbreviation for “special detective/reconnaissance” (特侦 or 特别侦察) based off the following context:

The following is an old recruitment article available on Sohu.com for the 2018 Special Detective Unit of the Xinjiang Public Security Bureau that had a reference to this type of unit’s title:

The whitepaper also stated the external network of the platform cannot contain any personally identifiable information (PII). Below are a few prohibited types of PII including “public security officer number”:

This indicates that that platform is likely used by the MPS for offensive cyber operations and they want to prevent any potential vectors for identification and attribution.
Anti-Reconnaissance Design
The white paper indicates that the platform has various “best practice” security design principles to ensure the integrity of the platform, such as data-at-rest and data-in-transit encryption, periodic security testing, system and vulnerability monitoring, and patching. However, the most interesting security elements are the anti-reconnaissance design features in the external network elements, including:
- Use of long and randomized login host names for the external platform.
- Use of uncorrelated system hostnames
- The platform is disguised to prevent guessing of the login address.
- All information on the external platform must have nothing to do with the iSoon business/service, including text, logo, functionalities, and bookmarks.
- Development and developer related information cannot exist in the platform code. Code audits and security testing are required prior to release.
- The platform does not store any information related to operators or log any usage history.
- The platform development, network provider registration, and VPS hosting must be done anonymously to conceal identity. System, languages, time zone, system environment, input method must all be configured to use languages other than Chinese.
- The external platform disconnects from the internet and initiates a self-destruct process if the platform is detected, or the system had been compromised.
The self-destruct features appear to be a common feature found on previously identified Chinese spyware used to target dissidents:
- https://cyberscoop.com/researchers-uncover-latest-version-chinese-spyware-used-target-dissidents/
- https://thehackernews.com/2014/04/Spyware-german-aerospace-center-cyber-espionage.html

Integrated Operations Intranet Platform
The intranet platform appears to primarily focus on mission and resources management. It maintains a community knowledge base and its own security sandbox environment for analysis of retrieved files.
Mission Management
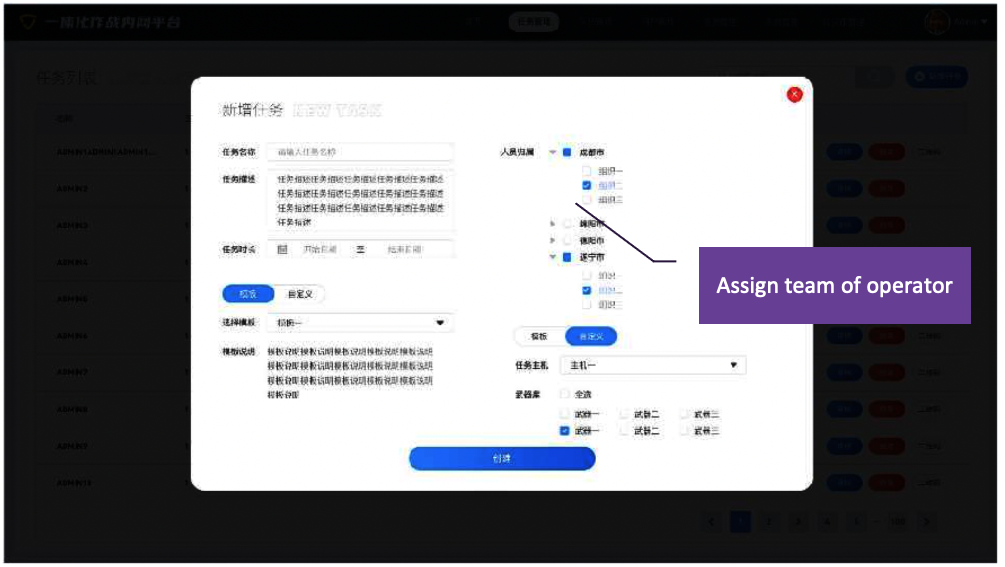
The internal application offers task management for leaders (superiors) to create, review, approve, (re)assign, comment, and distribute missions to operators. The following is a screenshot of the create mission page that contains the following input fields: mission name, description, mission duration, mission template, teams (each city can have multiple teams), assigned servers:

The next screenshot is a mission detail dashboard that contains the following tabs across the top: mission information tab, notes tab, file management tab, vulnerability tab, access permission tab, server tab. However, the data on this page are mock data to demonstrate the product:

The missions(tasks) can be approved or denied by superiors and can be assigned to, and carried out, by different teams across different cities:

The platform also contains scoring management functionality that can award points for each completed mission and display points earned by each operator for performance review purposes.

The dashboard can also provide statistical data and analysis to the superior on the operator’s area of expertise and resources assigned to each mission.
Knowledge Base Management
The techniques and tactics, skills, tools usage, and experiences of operators can be shared and catalogued in the internal knowledge base built into the internal platform. The following screenshot is the techniques and tactics knowledge base tab:

The list of categories shown in the techniques and tactics knowledge base tab of the screenshot above (starting from the top left) are: web application penetration, internal network penetration, terminal penetration, anti-reconnaissance/detection, web application control and bypass, vulnerability discovery and exploitation, data analytics, evasion, password cracking, intelligent analysis, network reconnaissance. The whitepaper did display an actual knowledge base page, but the text shown in the screenshots consists of mock data.
Integrated Operations Extranet Platform

The extranet platform is primarily a cyber operational management platform used by the operators to carry out attack operations. It provides operators the ability to deploy, manage, and securely decommission the VPS used in cyber campaigns, manage the tools and exploits used by operators, and keep track of mission notes, vulnerabilities, and servers.
Weapons Management

The weapon management feature is an arsenal warehouse that allows operators to import, search, display, and keep track of their tools. It also has versioning functionality to keep copies of the older tools and manage updates. As to what kind of tools are available or used by the iSoon and MPS team, this information was not discussed in the whitepaper.
Security Sandbox
Both the internal and external application have their own security sandbox environments for identifying any potential malware in the tools or files/data retrieved from the target. The weapon sandbox environment on the external application offers the same capability as the internal security sandbox environment. The latter is used to inspect the stolen data that was transmitted back to the internal application to prevent honeypot attacks or trojans. The sandbox environment capabilities include:
- File analysis: executables, DLL, PDF, office documents, URL, zip archive, etc.
- Win32 API inspection to detect malicious activities.
- Behavior analysis of the application for malicious intent.
- Process graph flow analysis (disassembler graph).
- PCAP* packet capture analysis.
- Detection for malicious screen capture and file modification.
* The white paper document had PCAP spelled incorrectly as “PACP”.
Conclusion
The integrated operations platform documentation provided a glimpse into how cyber operations are run by a foreign adversary and how they coordinate and manage their team, business, and infrastructure. This blog post only summarized the highlights and interesting facts from the whitepaper, it is not a comprehensive translation and analysis of the original document.
Subscribe to Bishop Fox's Security Blog
Be first to learn about latest tools, advisories, and findings.
如有侵权请联系:admin#unsafe.sh