2024-3-21 21:46:39 Author: www.threatfabric.com(查看原文) 阅读量:6 收藏
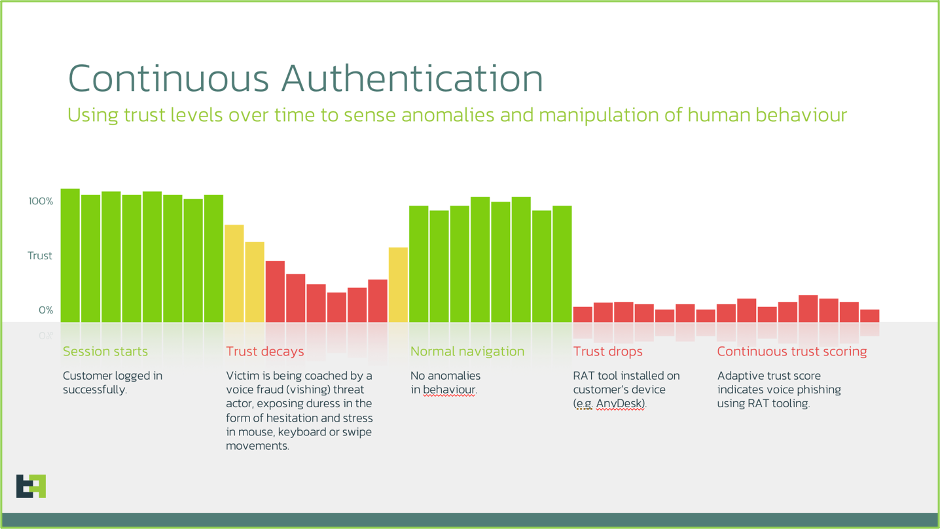
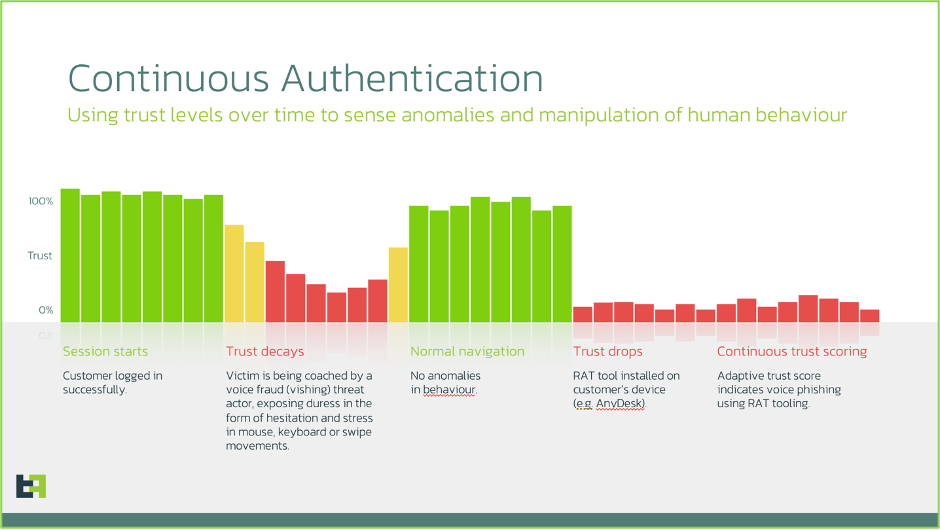
Today, we store almost everything that we value in digital vaults. We store our money in digital banking accounts. We store our health records in digital healthcare databases. We store our intellectual property in corporate networks. We store our communications with loved ones on our devices or in the cloud. Authentication methods exist to guard these digital vaults and ensure that users are who they claim to be. In a utopian world, where no criminals or fraudsters exist, we wouldn’t need authentication. Unfortunately, this is not the world we live in. There are three common factors that can be used for authentication: Possession factor: Something you have (such as a smartphone or token device) Through high-tech cyberattacks and low-tech social engineering, almost all these authentication factors can be overcome, with varying ease and cost. Passwords are easily found on the criminal underground through data leaks (I found my old email password in 13 different data leaks) or can be harvested through phishing links. One-time passcodes can be socially engineered from users or acquired through sim-swapping. Voice samples can be cloned through commercially available generative AI tools such as ElevenLabs. Fingerprints and face IDs are still resilient, and we are heavily reliant on these authentication methods for our closest guarded digital possessions. However, ThreatFabric’s malware researchers found that recent Android banking trojans perform fingerprint and Face-ID downgrade attacks, whereby malware bypasses biometric authentication and falls back to PIN-based authentication, which is easier to compromise. Furthermore, with the quality of deepfakes improving at pace, authentication providers have an imperative to prepare for the post-biometric world, where biometrics are no longer a reliable source of authentication. There is a growing field of research to bolster liveness checks using: Another field of research has been looking at whether alternative inherence factors can be used. At ThreatFabric, we have teamed up with Patrick Bours, a professor at the Norwegian University of Science and Technology (NTNU), who has two decades of experience looking at alternative forms of authentication through behavioural biometrics. He has published papers on Gait Recognition (recognising a person by his/her walking style), Keystroke Dynamics (recognising a person by his/her typing style), and Continuous Authentication (detecting a user change) through analysis of smartphone data. There are three main advantages of using behavioural biometrics for authentication: Patrick Bours, of NTNU, emphasises this point: “Human behaviour is so complex and ingrained in our subconscious, that we cannot mimic the full behaviour of another person. When we adjust our behaviour to fit one aspect of the other person’s behaviour, then other parts of our behaviour will automatically “fall back” on our own ingrained way of doing so.” In Gartner’s recent review on Account Takeover risks, they find that: “During the journey time, there is an overreliance on active authentication measures — typically a password and sometimes an additional authentication factor — to secure login processes. Except device profiling and bot mitigation, there is relatively limited adoption of passive authentication that can provide risk and recognition signals without impacting the user experience (UX).” This point of view has also been reinforced by regulators, such as the European Banking Authority (EBA), who have approved and endorsed the use of behavioural biometrics as an inherence factor in Strong Customer Authentication (SCA). The main disadvantage when using behaviour alone for authentication is that there are higher false positive rates. This is due to the “intra-class variability” that stems from our behaviour change when we are in a different emotional state (e.g. sad, angry or nervous) to our baseline state. Although this is a disadvantage for authentication purposes, this intra-class variability is the cornerstone for detecting social engineering and scams through digital behaviour. There are various methods to reduce false positives, including correlating behavioural biometrics with additional device-related data points. At ThreatFabric, we are strong proponents of using continuous adaptive trust and risk assessments that leverage a variety of risk signals. This contrasts with point-in-time security gates that are overly reliant on a few risk signals. The diagram below shows an example of how continuous authentication can help surface risks at different stages of the digital journey: Wherever there is a vault, there will be someone looking to get inside. Today, most vaults are being cracked by us giving away the code rather than the lock being picked. Bolstering authentication approaches with factors that are difficult to spoof or socially engineer from us, such as behavioural biometrics, may hold the key to security in a post-biometric world. With that being said, we have been humbled time and time again by the ingenuity and immorality of fraudsters. The cat-and-mouse game continues.Digital vaults
Broken factors
Alternative inherence factors
Continuous Authentication
Where do we go from here?
如有侵权请联系:admin#unsafe.sh