
The reason I extracted a PE file in my last diary entry, is that I discovered it was the dropper of a Cobalt Strike beacon @DebugPrivilege had pointed me to. My 1768.py tool crashed on the process memory dump. This is fixed now, but it still doesn't extract the configuration.
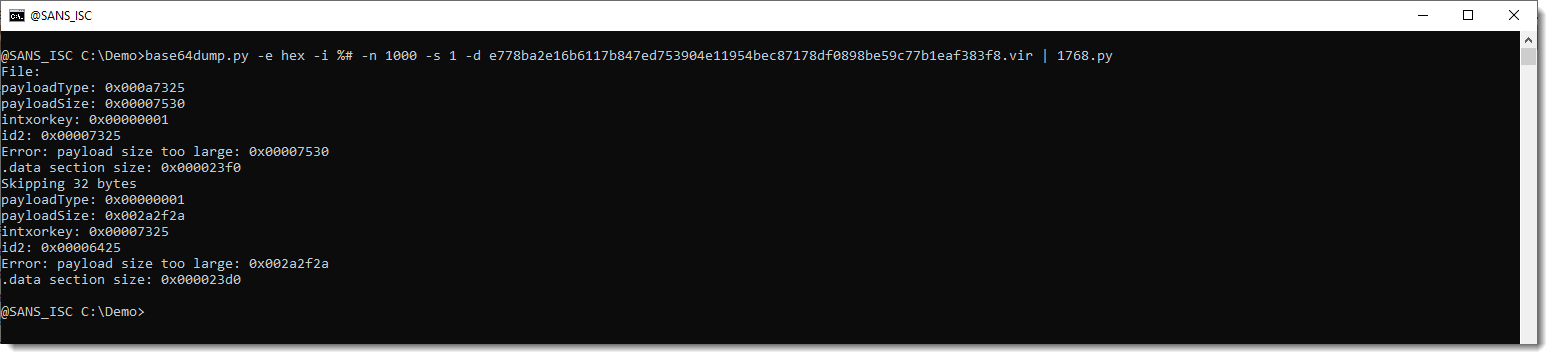
I did a manual analysis of the Cobalt Strike beacon, and found that it uses alternative datastructures for the stored and runtime config.
I'm not sure if this is a (new) feature of Cobalt Strike, or a hack someone pulled of. I'm seeing very few similar samples on VirusTotal, so for the moment, I'm adding the decoders I developed for this to 1768.py as experimental features. These decoders won't run (like in the screenshot above), unless you use option -e.
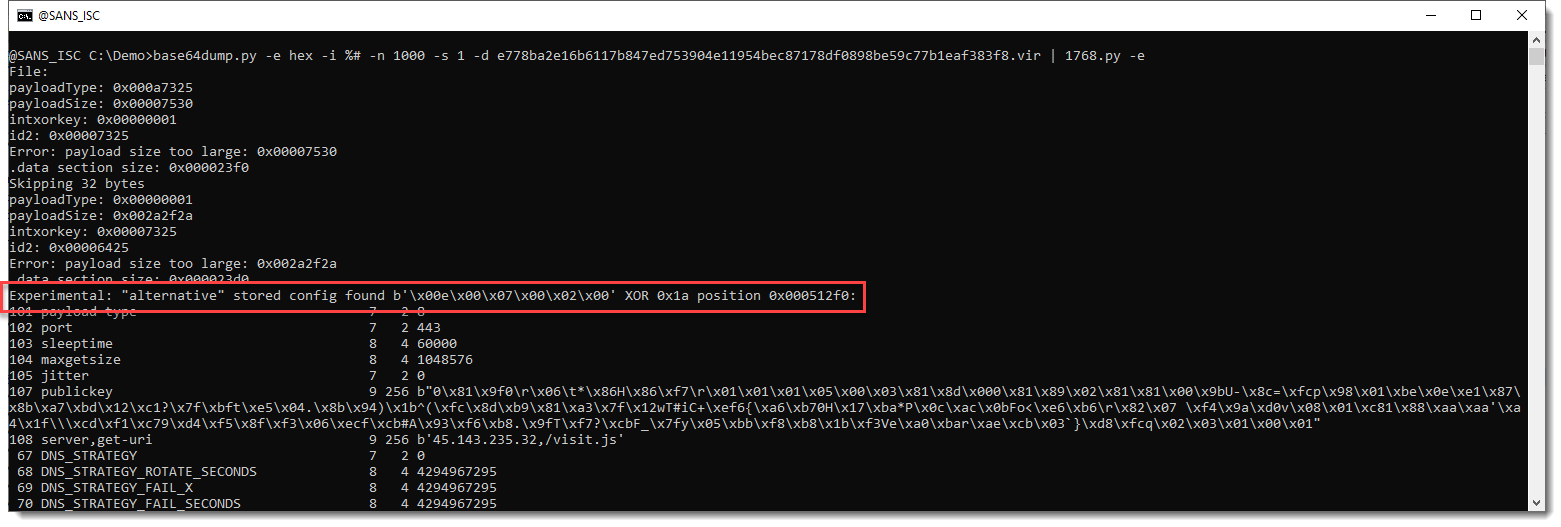
With option -e, the alternative stored config is found and decoded:
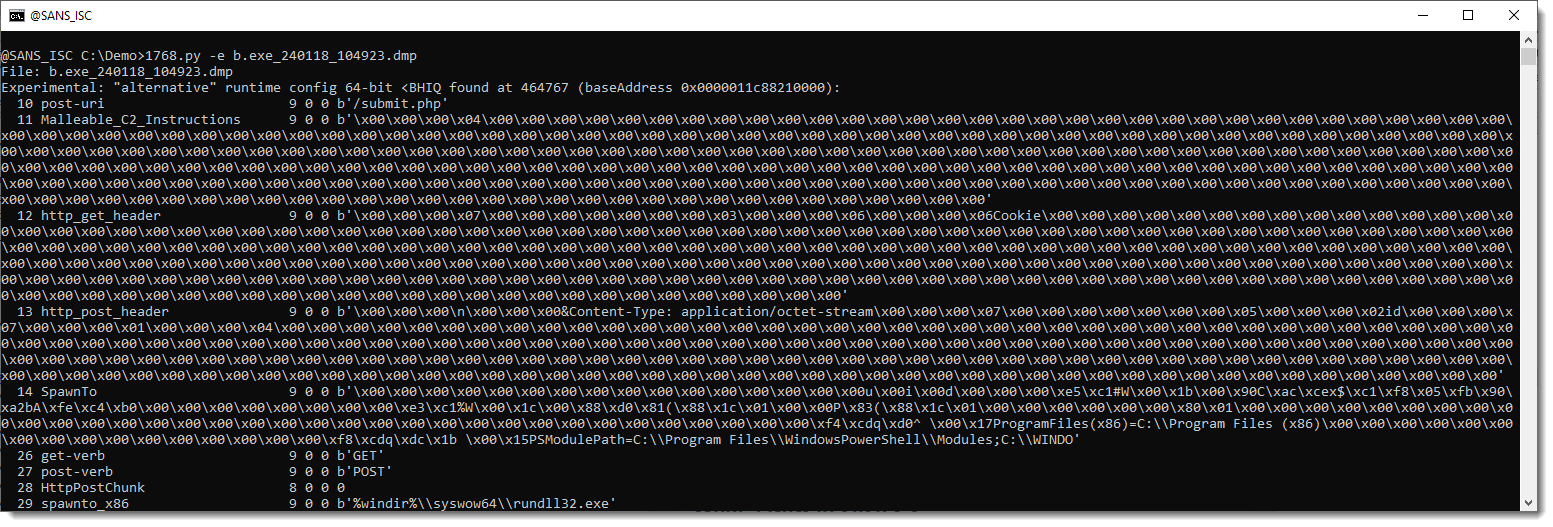
And it can also analyze the process memory dumps I was pointed to:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
如有侵权请联系:admin#unsafe.sh