
What is Key Management?
Key management refers to the administrative control over cryptographic keys. It encompasses their creation, distribution, storage, and deletion. This process ensures that the keys used to encrypt and decrypt data are securely handled and accessible only to authorized entities. Effective key management is fundamental to maintaining the integrity and confidentiality of sensitive information.
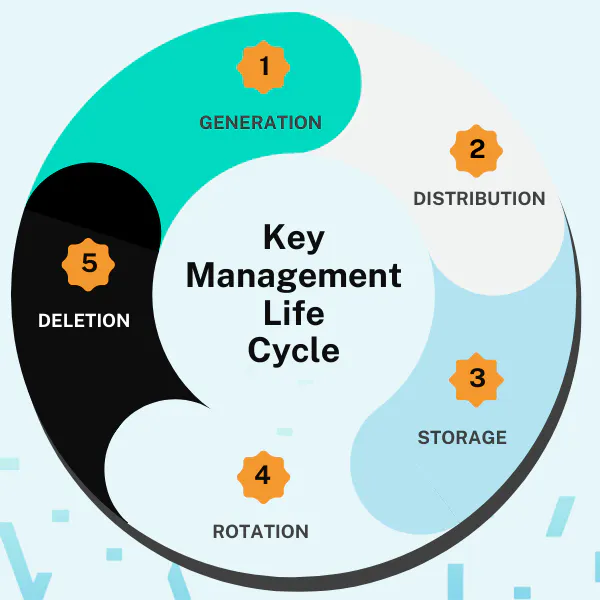
Key Lifecycle Stages
To navigate the intricate landscape of digital security, it’s crucial to understand and efficiently manage cryptographic keys. Key management, a cornerstone in safeguarding sensitive data, involves a meticulous process that spans across various stages, from creation to deletion, ensuring these keys are in the right hands and used appropriately. This meticulous oversight is vital for upholding data integrity and confidentiality.
- Generation: Creating strong, unique keys using secure methods.
- Distribution: Safely transferring keys to required systems or users while tracking their distribution and use.
- Storage: Keeping keys securely, ensuring they are protected against unauthorized access.
- Rotation: Regularly changing keys to mitigate risks of key compromise.
- Deletion: Securely removing keys that are no longer needed, ensuring they cannot be recovered.
Modern Challenges in Key Management
- Key Sprawl: As businesses grow, so does the number of keys, making them harder to manage.
- Complexity: The diversity of IT environments, including cloud and on-premises systems, complicates key management.
- Compliance: Meeting regulatory requirements demands rigorous control and audit trails for key usage.
Navigating these challenges requires a comprehensive approach, highlighting the importance of an effective key management strategy to secure digital assets and ensure operational resilience.
Key Management’s Role in Secrets Management
Secrets management, a broader concept, involves handling not just cryptographic keys but also passwords, certificates, and API tokens. Key management is a critical subset of secrets management, focusing on the lifecycle of cryptographic keys. Together, they form a comprehensive approach to protect digital assets and communication channels against unauthorized access and potential breaches.
What is a key management service?
A key management service (KMS) is a platform or software that provides a secure environment for managing cryptographic keys. It automates many aspects of the key management process, such as key creation, distribution, rotation, and deletion. A KMS often includes features like secure key storage, access control, and auditing capabilities to help organizations comply with security standards and regulations.
Akeyless’s Approach to Key Management
Akeyless revolutionizes key management by integrating advanced security and operational simplicity, leveraging its unique Distributed Fragments Cryptography (DFC
(DFC ) and SaaS delivery for unparalleled protection and ease of use.
) and SaaS delivery for unparalleled protection and ease of use.
Key Features of Akeyless Key Management
- Secure Key Storage: Akeyless uses DFC
 to ensure cryptographic keys are never fully assembled and that each fragment is continually refreshed, enhancing security.
to ensure cryptographic keys are never fully assembled and that each fragment is continually refreshed, enhancing security. - Automated Key Rotation: Simplifies the process, reducing the risk of key exposure.
- Seamless Integration: Works effortlessly with existing DevOps tools and cloud platforms.
- Comprehensive Audit Trails: Offers detailed logging for compliance and security monitoring.
Benefits of Using Akeyless for Your Key Management
- Enhanced Security: Advanced encryption methods protect against unauthorized access.
- Zero Knowledge
- Operational Efficiency: Automation and integrations streamline key management processes.
- Regulatory Compliance: Helps meet stringent compliance requirements with detailed auditing.
Start Exploring Akeyless Today
Get started on a comprehensive and secure approach to key and secrets management with Akeyless today. See what it can do for your enterprise with a live demo today!
Frequently Asked Questions (FAQ) About Key Management
What do you mean by key management?
Key management refers to the process of handling cryptographic keys throughout their lifecycle. This includes their creation, distribution, storage, rotation, and deletion. It’s a fundamental practice to ensure that keys, which encrypt and decrypt data, are managed securely and only accessible to authorized individuals. Effective key management is crucial for maintaining the integrity and confidentiality of sensitive information.
What is key management for businesses?
For businesses, key management is an essential aspect of their security framework, crucial for protecting digital assets and sensitive data. It involves implementing policies and procedures to manage cryptographic keys securely. This practice helps businesses mitigate risks associated with data breaches, ensure compliance with regulations, and safeguard their reputation by maintaining the trust of customers and stakeholders.
What is the goal of key management?
The primary goal of key management is to protect sensitive data by ensuring that cryptographic keys are handled securely throughout their lifecycle. This involves making sure that keys are strong, securely distributed, stored safely, rotated regularly, and securely deleted when no longer needed. Effective key management aims to prevent unauthorized access to encrypted data, thus maintaining its confidentiality and integrity.
The post What is Key Management? appeared first on Akeyless.
*** This is a Security Bloggers Network syndicated blog from Blog | Akeyless authored by AnneMarie Avalon. Read the original post at: https://www.akeyless.io/blog/what-is-key-management/
如有侵权请联系:admin#unsafe.sh
