
2024-3-26 17:31:50 Author: www.threatfabric.com(查看原文) 阅读量:6 收藏
These scams happen all over the world – although some regions (like the Nordics and the UK) are being targeted more often at the time of writing. Vishing Scams requires the criminals to have people, and internet and phone infrastructures at scale. They sometimes operate from call centers. They will go through a process that looks like this: Our research shows one in 5 scams are performed in this way. With the right tools, anti-fraud teams should be able to pick up the tell-tale signs of these attacks. The Fraud Kill-chain is a useful tool to identify detection opportunities and gaps. It allows anti-fraud teams to map capabilities to attacks, and helps controlling a wide variety of fraud and scams. Many scams are hard to detect due to the lack of “technical” TTPs. Vishing – RAT, however, has some touch points on the mobile (an incoming call), and on the device: a RAT installation, and an active RAT. We can see a plethora of TTPs identifying various stages of attacks before, during, and after. This means there is a lot of opportunity for detection, but it requires sensors and processes in digital channels. Incoming Phone Calls, and Active Phone Calls can be detected on the Mobile device. It is key that Device Risk uses Threat Intelligence, so anti-fraud teams understand what kinds of attacks are seen “in the wild”, and how Device Risk is integrated in your Anti-Fraud environment. When criminals are operating your account, their behavior will be different than yours. While Behavioral Biometrics is the best technology available, it’s key to have multiple models: By correlating Device Risk and Behavioral Risk, you can correlate “on-call” with “active RAT” with “behavioral risk”. Your capabilities should include visibility on both web and mobile – since often an scam operates on both, or moves from one channel to another during the attempt. Conclusion & Takeaways As scammers are raking in billions, anti-fraud teams are to perform the following checks: ThreatFabric helps banks and financials globally perform these analyses. If you’re interested in a detection readiness workshop, use the link below for a free consultation.This third episode covers what happens when scammers call you up on your phone. They pretend to be your bank, Microsoft, or the police. Their goal: to take over your device via a Remote Access Toolkit (RAT). Voice Phishing is often abbreviated to Vishing. The Scam is called an Impersonation Scam, or a Vishing – RAT scam.
This blog is part of a series, where we will offer the tools to check your fraud detection capabilities for readiness on the most prolific fraud and scam types. From Malware campaigns to scams, we’ll analyze TTPs, Kill-Chain mappings, and detection gaps.
The Problem

About the Fraud Kill Chain
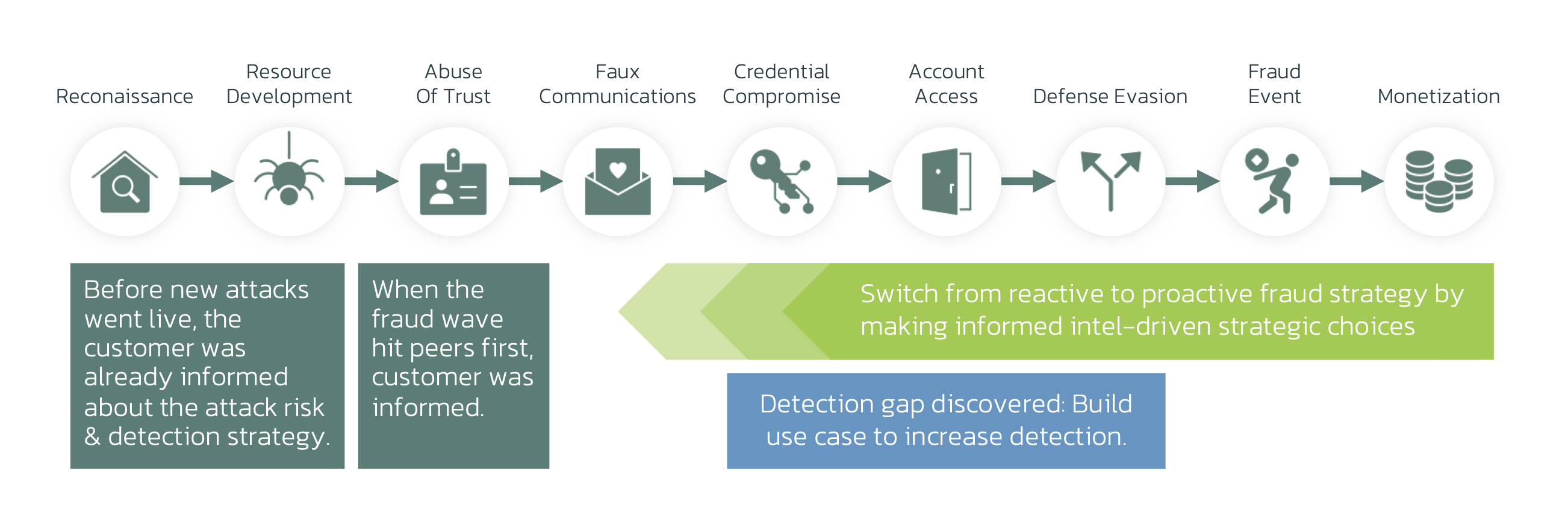
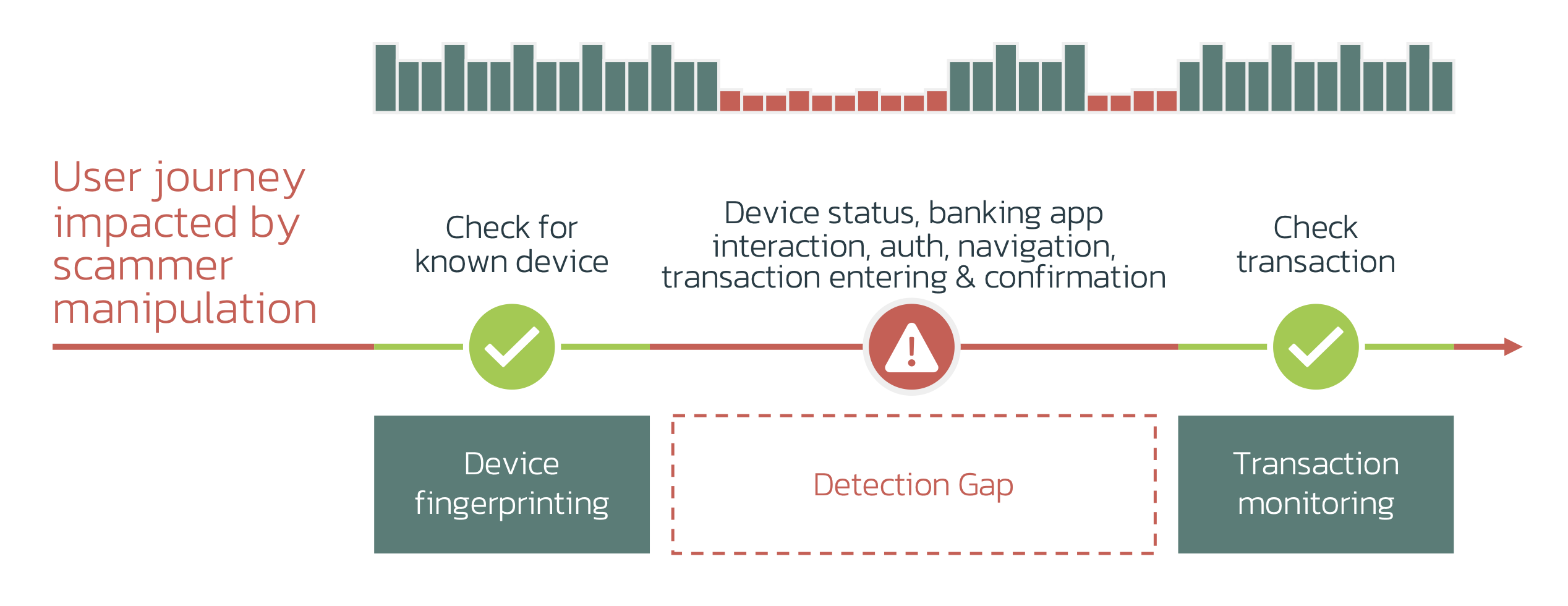
Vishing – RAT vs Fraud Kill Chain

Detection Gaps & Opportunities
Gap 1: Mobile Visibility / Device Risk
Gap 2: Behavioral Biometrics
Gap 3: Multi-Channel and Correlation
Detection Readiness Workshop
如有侵权请联系:admin#unsafe.sh