2024-4-7 16:23:34 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Vulnerability Overview
Recently, NSFOCUS CERT detected that the security community disclosed a supply chain backdoor vulnerability in XZ-Utils (CVE-2024-3094), with a CVSS score of 10. Since the underlying layer of SSH relies on liblzma, when certain conditions are met, an attacker can use this vulnerability to bypass SSH authentication and gain unauthorized access on the affected system, thus executing any system command. After investigation, it is found that the tarball upstream software package of xz infects a backdoor program. The backdoor extracts the .o file from the disguised test file during the building process, and then uses the extracted file to modify specific functions in liblzma, resulting in the generation of a modified liblzma library. Any software linked to this library may use it to intercept and modify data interaction with this library. At present, the vulnerability PoC has been made public. Relevant users are requested to take measures as soon as possible for troubleshooting and protection.
XZ-Utils is a tool library suite widely used for processing .xz files in Linux, Unix and other POSIX compatible systems, including components such as liblzma and xz, which are integrated in the vast majority of Linux distribution repositories. NSFOCUS CERT has been successfully reproduced this vulnerability:

Reference link:
https://tukaani.org/xz-backdoor/
https://www.openwall.com/lists/oss-security/2024/03/29/4
Background
n October 2021, JiaT75, the developer who implanted backdoor vulnerabilities, began to participate in the development of XZ-Utils project and gradually gained trust. It took over the maintenance authority of the project in 2023. In February 2024, it submitted malicious files to liblzma/xz, introduced a hidden backdoor that allowed attackers to access SSH without authorization, and contacted the maintainer of Linux distribution. Libraries with backdoors were required to be packaged and distributed to end users, and developer Andres Freund discovered this supply chain attack activity on March 29 when analyzing SSH performance failures. GitHub has now shut down the entire XZ-Utils project.

Backdoor analysis
When the sshd process linked to the malicious dynamic database is started, the malicious code in liblzma.so will modify the pointing address of the RSA_public_decrypt function symbol through Hook technology. When the sshd process receives a new SSH login request, it triggers the RSA_public_decrypt function to verify the signature of related payload fields. After the verification, the attack payload hidden in the certificate field is extracted and passed to the system function for arbitrary code execution.
Trigger conditions:
- The process path name is /usr/sbin/sshd.
- LANG environment variable exists
- LD_DEBUG, LD_PROFILE environment variables do not exist
The attacker then constructs an attack payload according to a specific message format, wrapping the command to be executed (passed into the system function) in the certificate field:

The sshd process uses RSA_public_decrypt to decrypt (verify) the payload of this segment. Then, it accesses a function that is hijacked by an attacker and verifies the workload of this segment. It sends the cmd command filled in earlier to the system function for execution. Since this step involves the verification of public and private key pairs, load that cannot pass correct decryption/verification will not trigger subsequent system execution. Therefore, for liblzma.5.6.0 and liblzma5.6.1 files pre-introduced by the original attacker, only the attacker itself can realize backdoor exploitation.
Scope of Impact
- XZ Utils = 5.6.0 – 5.6.1
Note: No malicious code is found in the Git distribution version of XZ, and it only exists in the complete download package.
Affected Linux distribution:
- Fedora Rawhide (development version)
- Fedora 41
- MACOS HomeBrew x64openSUSE Tumbleweed and MicroOS (released March 7-28)
- Kali Linux (xz-utils 5.6.0-0.2 released March 26-28)
- Debian (XZ beta version 5.5.1alpha-0.1 to 5.6.1-1)
XZ Supply Chain Impact System Query: https://repology.org/project/xz/version
Unaffected version
- XZ Utils < 5.6.0
- XZ Utils >= 5.8.0
Note: As the developer of the implanted backdoor has been involved in maintenance since 2021, it is recommended that users downgrade XZ-Utils to 5.4 or earlier for safety reasons. CentOS/Redhat/Ubuntu/Debian/Fedora and other stable warehouses are not affected.
Detection
You can run the following command to determine whether the xz in use is the affected version:
xz –version

Script troubleshooting
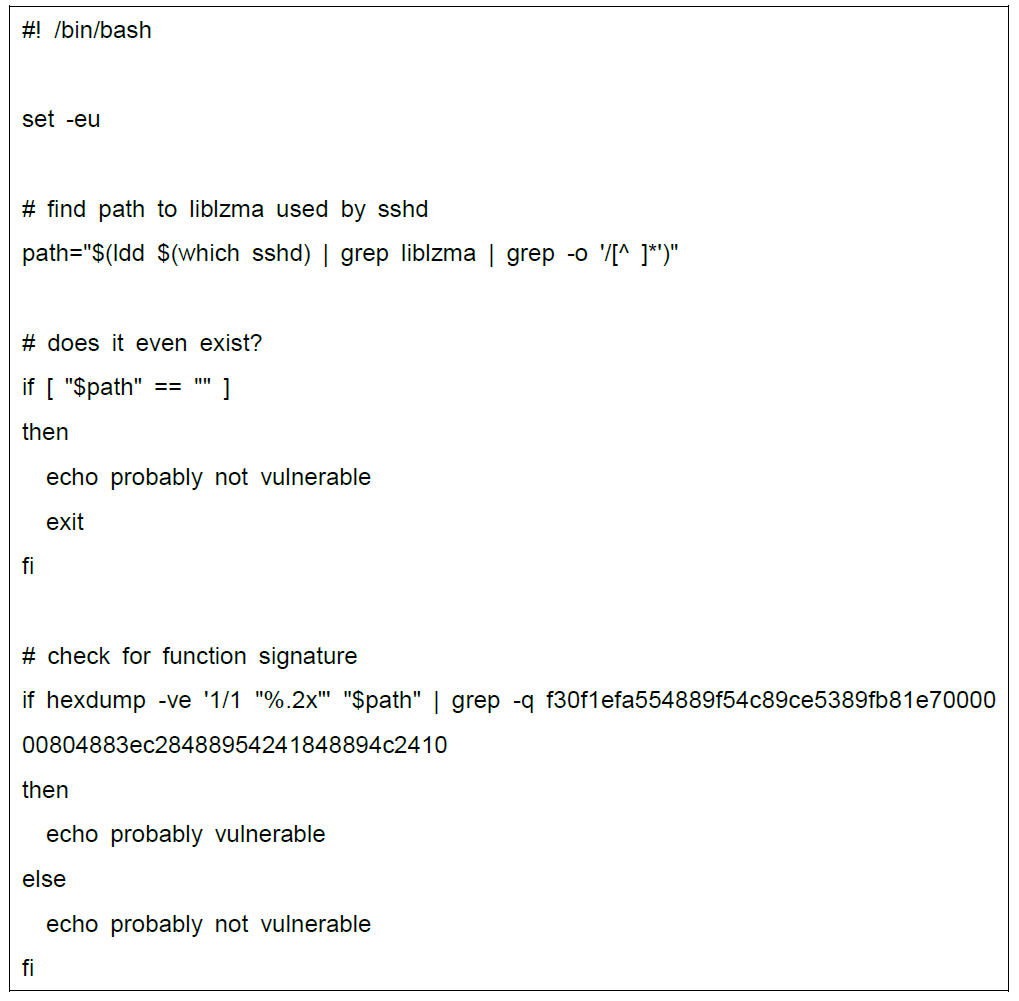
Relevant users can also use the scripts published on Openwall to check whether the system is infected with backdoor:

It needs to be determined whether the binary data of the liblzma library file that the SSHD program depends on contains backdoor signatures.
Mitigation
At present, the officially released pure version 5.8.0 for this backdoor vulnerability. The download link is https://git.tukaani.org/. Relevant users can also downgrade xz-utils to a version earlier than 5.6 or replace it with 7zip and other components in applications. Note: The brew update has been rolled back from 5.6.1 to 5.4.6; Debian released an updated version of xz utils, with the version number of 5.6.1 + really 5.4.5.
Other Recommendations
Establish a supply chain management system for product procurement and open source software, improve the safety management of application development life cycle, strengthen the monitoring of upstream and downstream threat intelligence of software, and timely grasp the security risks of applications and products.
Statement
This advisory is only used to describe a potential risk. NSFOCUS does not provide any commitment or promise on this advisory. NSFOCUS and the author will not bear any liability for any direct and/or indirect consequences and losses caused by transmitting and/or using this advisory. NSFOCUS reserves all the rights to modify and interpret this advisory. Please include this statement paragraph when reproducing or transferring this advisory. Do not modify this advisory, add/delete any information to/from it, or use this advisory for commercial purposes without permission from NSFOCUS.
About NSFOCUS
NSFOCUS, a pioneering leader in cybersecurity, is dedicated to safeguarding telecommunications, Internet service providers, hosting providers, and enterprises from sophisticated cyberattacks.
Founded in 2000, NSFOCUS operates globally with over 4000 employees at two headquarters in Beijing, China, and Santa Clara, CA, USA, and over 50 offices worldwide. It has a proven track record of protecting over 25% of the Fortune Global 500 companies, including four of the five largest banks and six of the world’s top ten telecommunications companies.
Leveraging technical prowess and innovation, NSFOCUS delivers a comprehensive suite of security solutions, including the Intelligent Security Operations Platform (ISOP) for modern SOC, DDoS Protection, Continuous Threat Exposure Management (CTEM) Service and Web Application and API Protection (WAAP). All the solutions and services are augmented by the Security Large Language Model (SecLLM), ML, patented algorithms and other cutting-edge research achievements developed by NSFOCUS.
The post XZ-Utils Supply Chain Backdoor Vulnerability Updated Advisory (CVE-2024-3094) appeared first on NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks..
*** This is a Security Bloggers Network syndicated blog from NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks. authored by NSFOCUS. Read the original post at: https://nsfocusglobal.com/xz-utils-supply-chain-backdoor-vulnerability-updated-advisory-cve-2024-3094/
如有侵权请联系:admin#unsafe.sh