Burp Suite Target, a pivotal component in the arsenal of every hacker and security professional!
Burp Suite Target is a module within the Burp Suite toolset specifically designed for web application security testing and analysis. It serves as the focal point for targeting and assessing the security posture of web applications.
Key features of Burp Suite Target include:
- Target Definition: Burp Suite Target allows users to define and configure the target web application they wish to assess. This includes specifying the URL, scope, and any authentication parameters required to access the application.
- Site Mapping: The tool enables users to comprehensively map out the structure and functionality of the target web application. This includes identifying all accessible pages, directories, parameters, and endpoints.
- Vulnerability Detection: Burp Suite Target includes built-in vulnerability detection capabilities, allowing users to automatically scan the target application for common security flaws such as SQL injection, cross-site scripting (XSS), and more.
- Customized Testing: Users can customize their testing approach within Burp Suite Target, tailoring scans and assessments to focus on specific areas of interest or to meet compliance requirements.
- Reporting: The module provides robust reporting features, allowing users to generate detailed reports of their findings, including identified vulnerabilities, recommended remediation steps, and overall risk assessment.
How to use Burp Suite Target
The Burp Target component mainly consists of three parts: site map, target domain, and Target tool. They help penetration testers better understand the overall status of the target application, which target domains are involved in the current work, and analyze possible attack surfaces and other information. Below Let’s take a look at the three components of Burp Target respectively.
The main contents of this chapter are:
- Target domain settings Target Scope
- Site MapSite Map
- Using Target Tools
Burp Suite Target domain settings Target Scope
The definition of scope in Target Scope is relatively broad. Generally speaking, when we perform a penetration test on a product, we can restrict intercepted content by domain name or host name.
The domain name or host name here is what we call the scope; if we If you want to make the restriction more fine-grained, for example, if you only want to intercept all requests under the login directory, we can also set it here. In this case, the scope is the directory. Generally speaking, Target Scope is mainly used in the following scenarios:
- Limit results displayed in sitemap and proxy history
- Tell Burp Proxy which requests to intercept
- What content does Burp Spider crawl?
- Burp Scanner automatically scans which scopes for security vulnerabilities
- Specifying URLs in Burp Intruder and Burp Repeater
Through Target Scope, we can easily control Burp’s interception range and operation objects, and reduce invalid noise. Target Scope’s settings mainly include two parts: allow rules and remove rules.
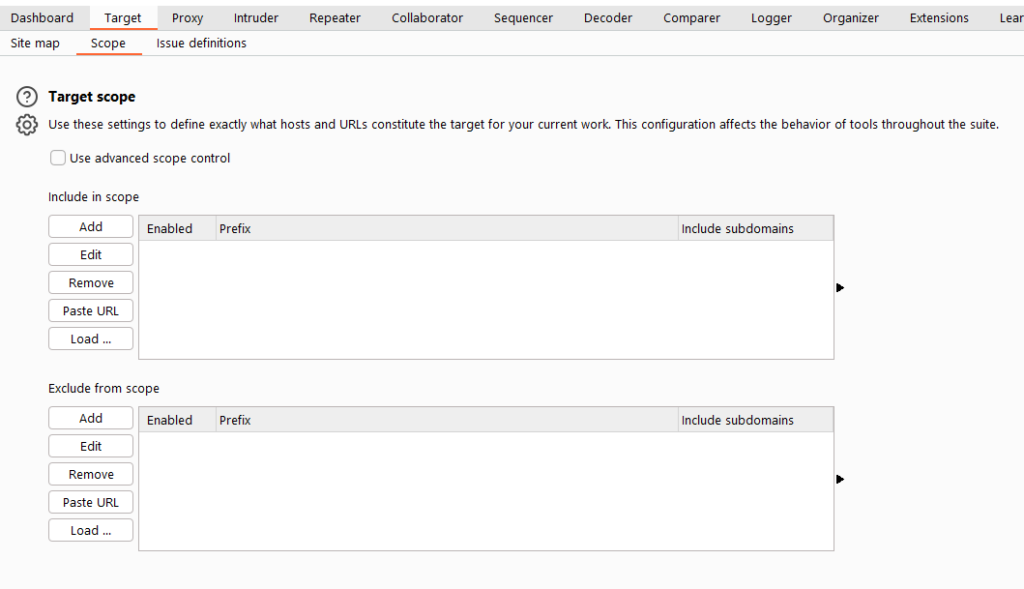
The allow rules are as the name implies, that is, the operations included in this rule list are deemed to be allowed and valid. If this rule is used for interception, the request message matching the inclusion rule list will be intercepted; otherwise, the request message matching the removal list will not be intercepted.
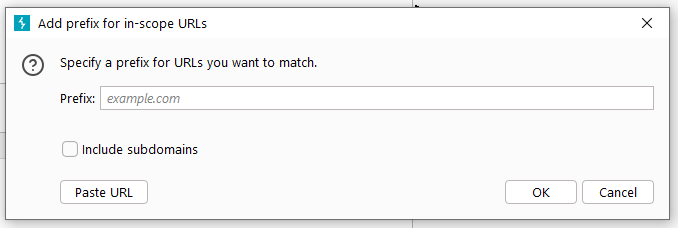
As we can see from the Add Rule dialog box in the above figure, the rules mainly consist of four parts: protocol, domain name or IP address, port, and file name. This means that we can add the following parameters from the protocol, domain name or IP address, port, and file name. There are 4 dimensions to control which messages appear in the rule list or are allowed or excluded.
When we set up the Target Scope (all are allowed by default), use Burp Proxy for proxy interception, and when browsing the application through the browser proxy in the penetration test, Burp will automatically record the browsing information, including detailed information about each request and response. , saved in the Target sitemap.
Burp Suite Target Site Map
The site map shown in the figure below is the result of the browser browsing history displayed in the site map during a penetration test.
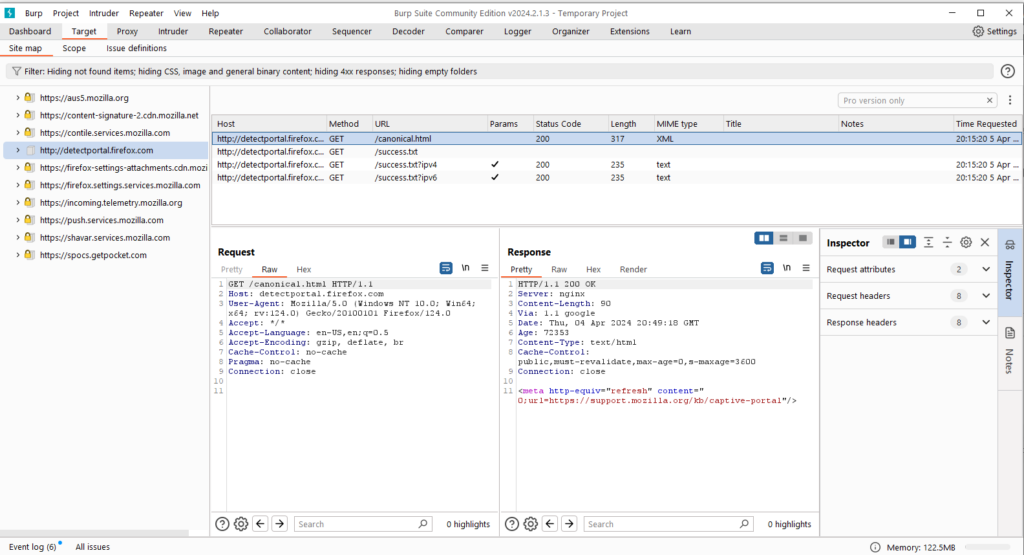
From the figure, we can see that the left side of the Site Map is the accessed URL. According to the level and depth of the website, the tree shape shows the structure of the entire application system and the URLs associated with other domains,
The right side shows the accessed URL of a certain URL. Detailed list, which URLs were visited, and what the request and response content were, are all recorded in detail. Based on the tree structure on the left, we can select a branch to add to scope.
In addition to adding the Target Scope, from the above figure, we can also see that for the layering of the site map, you can fold and expand it for better analysis. Site structure.
Using Target Tools site comparison
The use of Target tools mainly includes the following parts:
- Obtain sitemap manually
- site comparison
When we obtain the sitemap manually, we need to follow the following steps:
- 1. Set up the browser proxy and Burp Proxy proxy and make them work properly.
- 2. Turn off the interception function of Burp Proxy.
- 3. Browse the web page manually.
At this time, Target will automatically record the site map information. One advantage of manually obtaining the site map is that we can independently control the access content according to our own needs and analysis, and the recorded information is more accurate. Compared with automatic crawling, it takes longer.
If the product system that needs penetration testing is a large system, the power and time required to operate the function points of the system in sequence will be very costly to the penetration tester. very big.
Site comparison is a tool that Burp provides to penetration testers for dynamic analysis of sites. We often use it when comparing account permissions. When we log in to the application system and use different accounts, the accounts themselves are given different permissions in the application system, so the functional modules, content, parameters, etc. that the accounts can access are not the same.
At this time, use site comparison, It can help penetration testers distinguish them very well. Generally speaking, there are three main scenarios:
- The same account has different permissions and compares the difference in the results of two requests.
- Two different accounts with different permissions, compare the differences in the results of the two requests.
- Two different accounts have the same permissions and compare the differences in the results of the two requests.
Let’s take a look at how to compare sites.
First, we right-click on the function link that needs to be compared, find the menu of site comparison, and click the menu to enter the next step.
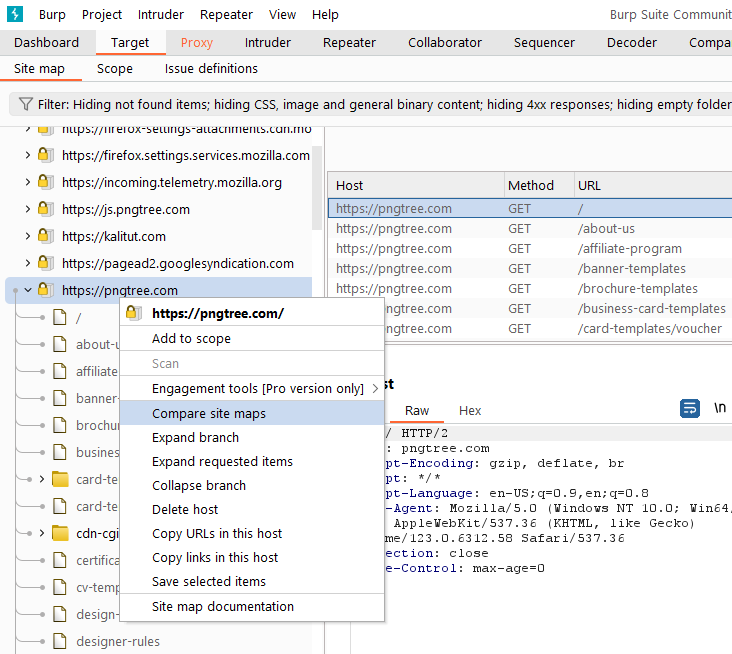
Since site comparison is performed between two site maps, we need to specify Site Map 1 and Site Map 2 respectively during the configuration process. Normally, Site Map 1 we default to the current session. As shown in the picture, click [Next].
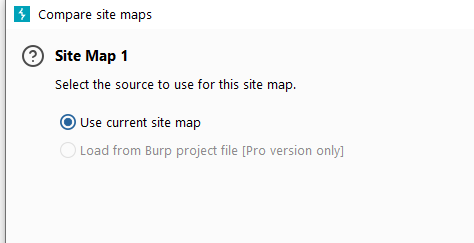
At this time we will enter the Site Map 1 settings page. If we want to compare the entire site, we will choose the first item. If we only compare the functions we selected, we will choose the second item. As shown below, click [Next]. If we are comparing the entire site and do not want to load other domains, we can check to select only the current domain.
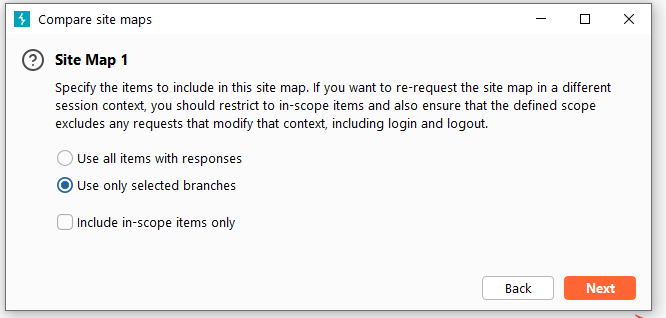
Next is the configuration of Site Map 2. We also have two methods for Site Map 2. The first is the Burp Suite site record we have saved before, and the second is to re-generate a request as Site Map 2. Here , we choose the second method.
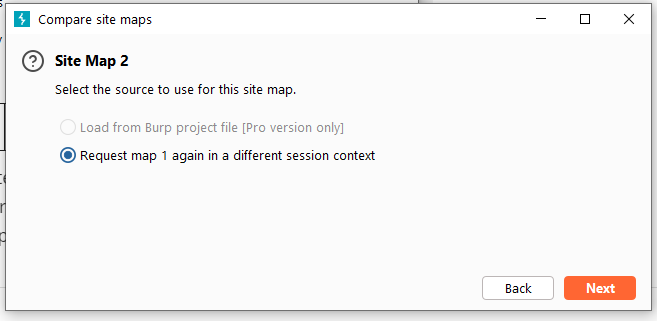
If you selected the second method in the previous step, enter the request message setting interface. In this interface, we need to specify the number of concurrent threads for communication, the number of failed retries, and the pause time.
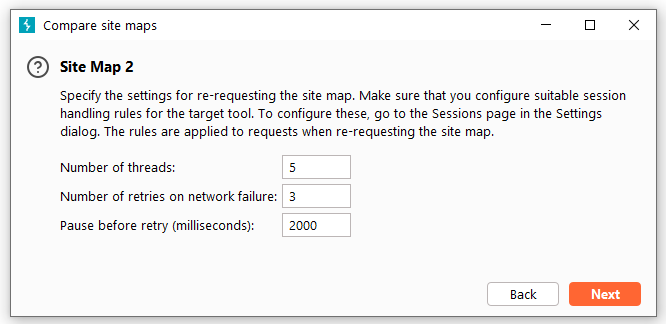
After setting up Site Map 1 and Site Map 2, you will enter the request message matching settings. In this interface, we can filter matching conditions by URL file path, HTTP request method, request parameters, request headers, and request body.
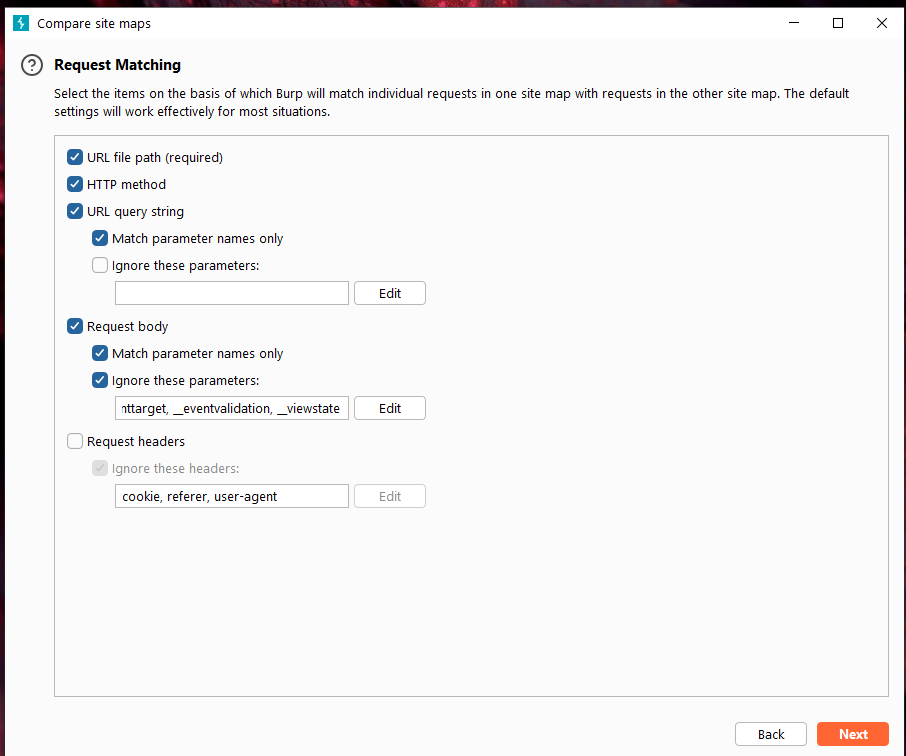
Set the request matching conditions, and then enter the response comparison setting interface. On this interface, we can set what content we specify that needs to be compared. From the figure below, we can see that there are mainly response headers, form fields, spaces, and MIME types. Click [Next].
If we were comparing the entire site before and chose to re-produce it as Site Map 2, you will be constantly prompted with the progress of data loading during the interface loading process. If there are few links involved in function requests, it will be very difficult. Quickly enter the comparison interface. As shown below.
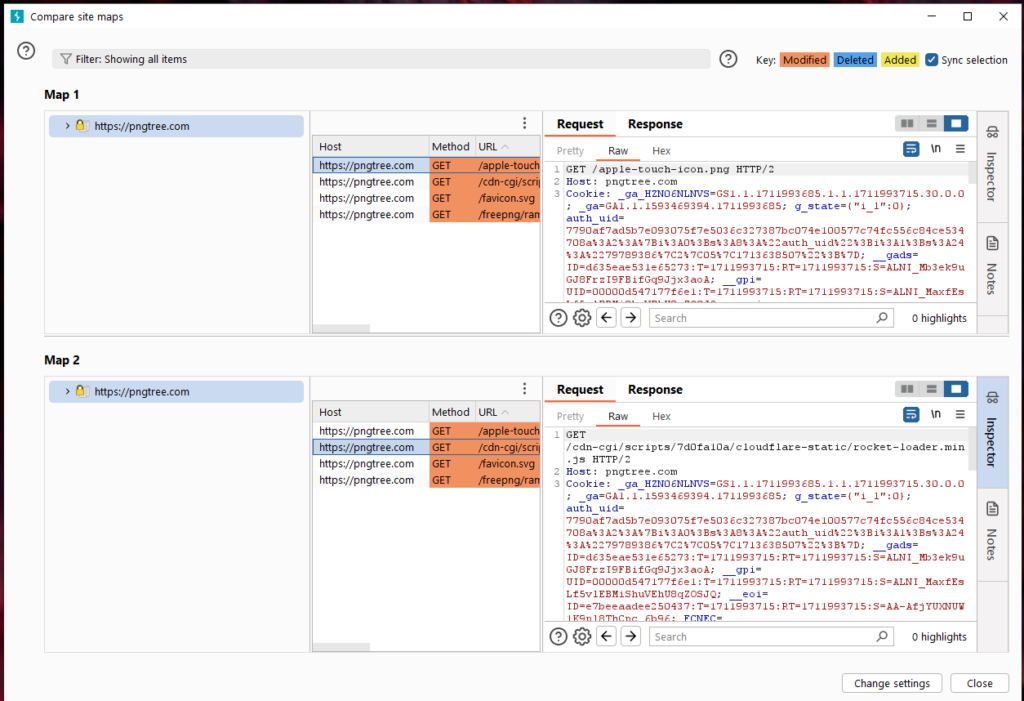
From the picture above, we can see that the upper part of the site comparison interface is the filter (this filter is used the same as other filters, so I won’t go into details here), and the lower part is composed of left, middle and right blocks. The left is the requested link list, the middle is the message records of Site Map 1 and Site Map 2, and the right is the message details.
When we select a message record in Site Map 1, the corresponding record in Site Map 2 will be automatically selected by default. This is controlled by the [Synchronization Selection] checkbox in the upper right corner.
At the same time, in the message details area on the right, The difference in communication messages between Site Map 1 and Site Map 2 will be automatically displayed, including request messages and response messages. Differences will be marked with a background color.
Burp Suite target scan
we will delve into the basics and usage of Burp Suite target analysis and target scanning.
Target scanning basics
Target scanning is a feature in Burp Suite for automated testing of web applications. It automatically discovers vulnerabilities and security issues in web applications and generates reports for analysis.
In Burp Suite, target scanning includes the following main components:
- Target: The web application that the user wants to test.
- Target Scope: Defines the scope of the web application to be tested.
- Scan policy: Define the scan policy to use.
- Scan options: Includes advanced settings such as setting scan speed and excluding specific vulnerability types.
Define scan targets
Before using the target scanning function, we need to define the target to be scanned. In Burp Suite, we can define scan targets through the following steps:
- In the “Target” tab of the main interface of Burp Suite, click the “Site map” button.
- Right-click on the target you want to scan and select the “Add to scope” option. This will add the target to the target scope.
- In the “Target” tab, click the “Engagement tools” button.
- In the Engagement tools tab, select the Scan tab.
- Click the “Add” button, select the target to scan, and select the scanning policy to use.
- Click the “Start scan” button to start scanning the target.
Through the above steps, we can add targets to the target scope and use scanning policies to automatically discover vulnerabilities and security issues in web applications.
Define scan range
After defining the scan target, we need to define the scan scope. The scan scope defines the scope and depth of the web application to be tested. In Burp Suite, we can define the scan scope in the following ways:
- Manually add: Manually add the URL or IP address to be tested.
- Automatic addition: Automatically add URLs or IP addresses to test by using Burp Suite’s “Spider” tool.
- Import from file: Import the URL or IP address to be tested from a file.
After defining the scanning scope, we can use scanning strategies to automatically discover vulnerabilities and security issues in web applications.
Define scan strategy
Scan policies define the testing techniques and vulnerability types to be used. In Burp Suite, we can choose from the following scanning strategies:
- Active Scanning: Use Burp Suite’s active scanning feature to discover vulnerabilities and security issues in web applications.
- Driven Scanning: Use Burp Suite’s driven scanning feature to discover vulnerabilities and security issues in web applications.
- Manual Testing: Manually test web applications for vulnerabilities and security issues.
After selecting a scan strategy, we can use scan options to further define our testing needs.
Define scan options
Scan options include advanced settings such as setting scan speed and excluding specific vulnerability types. In Burp Suite, we can define scan options by following these steps:
- In the “Target” tab of the main interface of Burp Suite, click the “Engagement tools” button.
- In the Engagement tools tab, select the Scan tab.
- In the Scan tab, select the scan policy to use.
- Click the “Settings” button to enter the scanning options interface.
In the scan options interface, we can set the scan speed, exclude specific vulnerability types and other advanced settings.
In this article, we discuss the basics and usage of target scanning for Burp Suite target analysis. We learned how to define scan targets, scan scope, scan strategy, and scan options.
By using Burp Suite target analysis and target scanning, we can automatically discover vulnerabilities and security issues in web applications and generate reports for analysis.