Burp Suite Repeater is a tool within the Burp Suite software package, which is widely used by security professionals for web application security testing. Burp Suite Repeater is a testing tool for manual verification of HTTP messages.
It is usually used for message analysis of server-side responses after replaying request responses multiple times and manually modifying request messages.

Usage of Burp Repeater
During the penetration testing process, we often use Repeater to perform message verification and analysis of requests and responses, such as modifying request parameters to verify input vulnerabilities; modifying request parameters to verify logic override; and capturing characteristic request messages from interception history records. Make a request for replay.
The operation interface of Burp Suite Repeater is as shown below:
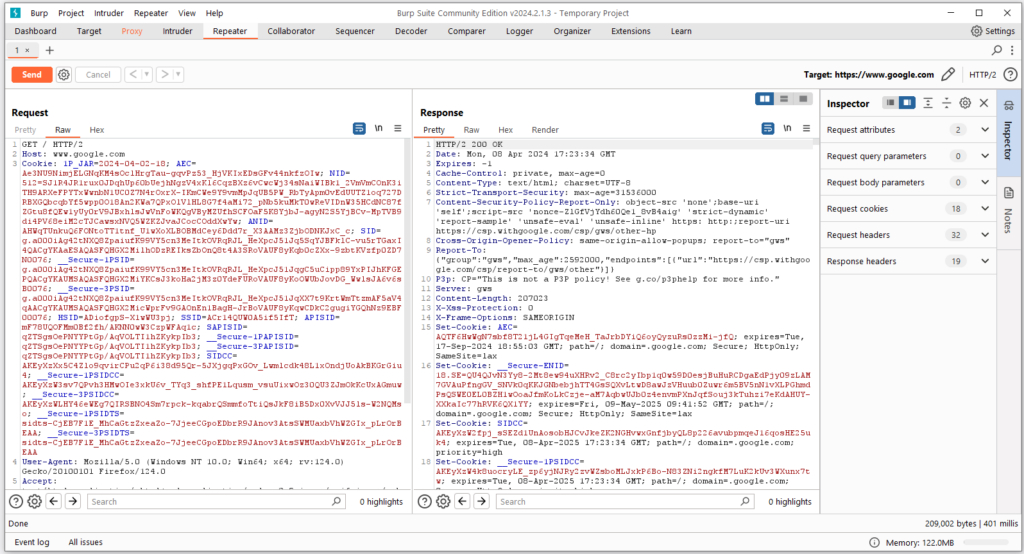
The request message area is the detailed information of the request message sent by the client.
Burp Repeater has a request number for each request. When we double-click on the number of the request encoding, we can modify the name of the request.
This is to facilitate multiple requests. Used for making notes or distinctions when sending messages. Under the number, there is a [send] button. After we edit the requested message, click this button to send the request to the server.
The response message area is the feedback message from the server after clicking the [send] button for the corresponding request message. By modifying the parameters of the request message to compare and analyze the differences between each response message, it can better help us analyze possible vulnerabilities in the system.
When we use Burp Suite Repeater, we usually use it in conjunction with other Burp tools, such as Proxy’s history records, Target’s site map, etc., through the right-click menu on other tools, execute [Send to Repeater], Jump to the Repeater tab, then modify the request message, request replay, data analysis and vulnerability verification.
Burp Repeater settings
Different from the settings of other Burp tools, Repeater’s optional settings menu is located in the menu bar at the top of the entire interface, as shown in the figure:
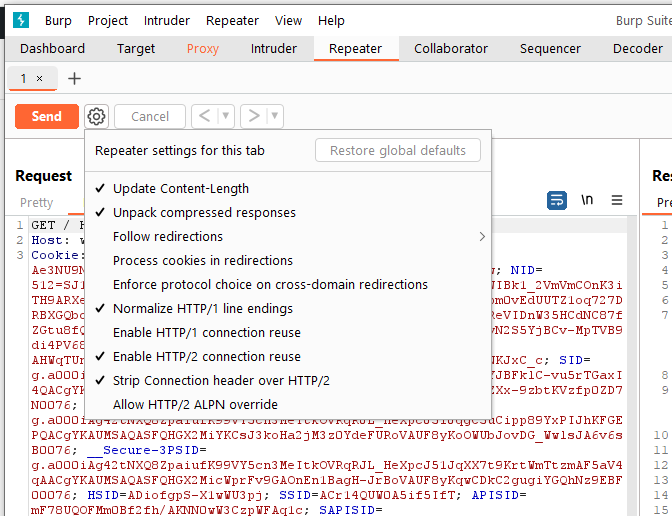
Its settings mainly include the following:
- Update Content-Length
This option is used to control whether Burp automatically updates the Content-Length in the request header. - Unpack and compress (Unpack gzip / deflate) This option is mainly used to control whether Burp automatically decompresses or compresses the content of the server-side response.
- Jump control (Follow redirections) This option is mainly used to control whether Burp automatically follows the server to make request jumps. For example, if the server returns a status code of 302, whether it will follow the response and jump to the URL pointed to by 302. It has 4 options, namely Never, On-site only, In-scope only, and Always, among which Never, Always jump is easy to understand. Intra-site jump refers to the current jump within the same site; target domain jump means that the domain configured in the target scope can jump;
- Process cookies in redirections If this option is selected, the cookie information set during the jump will be brought to the URL page pointed to by the jump and can be submitted.
- Other operations (Action) point to other tool components of Burp through submenus.
Here’s how Burp Suite Repeater works:
- Capture Request: Initially, you capture HTTP requests using another tool within Burp Suite called the Proxy. This captures all HTTP traffic between your browser and the web server.
- Send to Repeater: Once you’ve captured a request you want to inspect or manipulate further, you can send it to Burp Suite Repeater.
- Manual Manipulation: In the Repeater interface, you can manually adjust various parts of the HTTP request, such as headers, parameters, or the request body. This allows for fine-tuning and customization of the request.
- Reissue Request: After making any necessary modifications, you can reissue the request to the server directly from within Repeater.
- View Response: Once the server responds to the modified request, you can view the response in Repeater. This allows you to observe how the server reacts to different inputs and configurations.
Example of Burp Repeater attack
The most dangerous usage of Burp Suite Repeater would involve its exploitation by malicious actors to perform various types of attacks against web applications. Burp Suite Repeater, while primarily a tool for security professionals to manually manipulate and reissue individual HTTP requests, can be misused in several ways:
- Injection Attacks: Malicious actors could use Burp Suite Repeater to perform injection attacks such as SQL injection, command injection, or XSS (Cross-Site Scripting). By manipulating parameters or request payloads and observing the responses, attackers can attempt to exploit vulnerabilities in the application’s input validation and security mechanisms.
- Session Hijacking: If Burp Suite Repeater identifies weaknesses in session management or authentication mechanisms, attackers could exploit these vulnerabilities to hijack user sessions. By capturing and replaying session tokens or cookies, attackers could gain unauthorized access to sensitive user accounts or perform actions on behalf of authenticated users.
- Parameter Tampering: Attackers could use Burp Suite Repeater to tamper with parameters, headers, or other parts of HTTP requests to modify application behavior or access unauthorized functionality. This could lead to data manipulation, privilege escalation, or unauthorized access to sensitive information.
- Brute-Force Attacks: Burp Suite Repeater can be used to automate and iterate over different values or combinations of parameters, headers, or payloads in order to perform brute-force attacks. This could be used, for example, to guess passwords, authentication tokens, or other sensitive information.
- API Abuse: Malicious actors could abuse APIs (Application Programming Interfaces) by using Burp Suite Repeater to manipulate API requests and responses. This could lead to unauthorized access to sensitive data, API rate limiting evasion, or denial-of-service attacks against API endpoints.
It’s important to emphasize that Burp Suite Repeater itself is a legitimate security tool used by ethical hackers and security professionals to identify and mitigate vulnerabilities in web applications. However, in the wrong hands, it could be misused to exploit weaknesses for malicious purposes, potentially causing significant harm to individuals, organizations, and their data. Therefore, it’s crucial for organizations to implement strong security measures, including proper access controls, monitoring, and auditing, to prevent misuse of tools like Burp Suite Repeater and protect against potential attacks.
Burp Suite Repeater is particularly useful for testing and debugging web applications, as it provides a controlled environment for experimenting with individual requests and observing their effects in real-time. It helps security professionals identify vulnerabilities, assess the impact of potential attacks, and verify the effectiveness of security measures.