
2024-4-9 14:58:13 Author: www.vmray.com(查看原文) 阅读量:17 收藏
The Labs team at VMRay actively gathers publicly available data to identify any noteworthy malware developments that demand immediate attention. We complement this effort with our internal tracking and monitor events the security community reports to stay up-to-date with the latest changes in the cybersecurity landscape.
In March 2024, the VMRay Labs team has been specifically focused on the following areas:
- New VMRay Threat Identifiers, including:
- VTI to detect reverse shells on Linux and macOS systems
- VTI to detect process hollowing
- New YARA rules, including RisePro stealer malware family
- Reaction to phishing campaigns targeting Outlook
- Smart Link Detonation improvements
Now, let’s delve into each topic for a more comprehensive understanding.
In a few last blog posts, we introduced you to the concept of the VMRay Threat Identifiers (VTIs). In short, VTIs identify threatening or unusual behavior of the analyzed sample and rate the maliciousness on a scale of 1 to 5, with 5 being the most malicious. The VTI score, which greatly contributes to the ultimate Verdict of the sample, is presented to you in the VMRay Platform after a completed analysis.
1) VTI: Detect reverse shells on Linux and macOS systems
Category: Persistence
MITRE ATT&CK® Technique: T1059.004
A reverse shell is a type of shell session initiated from a target machine back to an attacker-controlled machine. This is in contrast to a traditional shell session, where a user interacts with a remote machine by connecting to it from their local machine.
The diagram below illustrates the basic flow of a reverse shell attack, showing how the attacker gains control over a compromised system through a reverse connection:

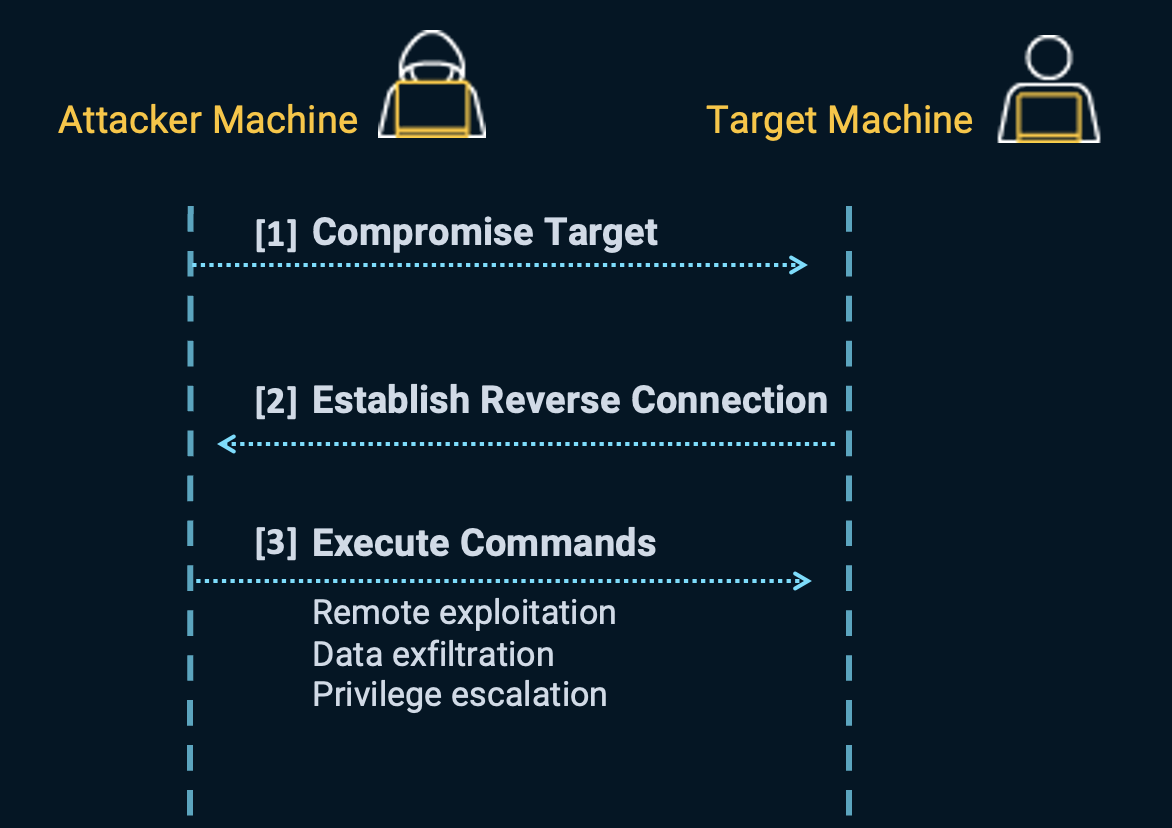
Attack steps:
[1]: Attacker compromises the target machine using various methods such as phishing emails, exploit kits, or social engineering techniques.
[2]: Target machine is compromised. Then, it establishes a reverse connection back to the attacker’s machine, creating a reverse shell session. It’s designed to bypass firewalls and network security measures since the connection is initiated from within the victim’s network.
[3]: Attacker gains control over the target machine and can execute commands, carry out further exploitation, exfiltrate data, escalate privileges, pivot to other systems within the network, etc.
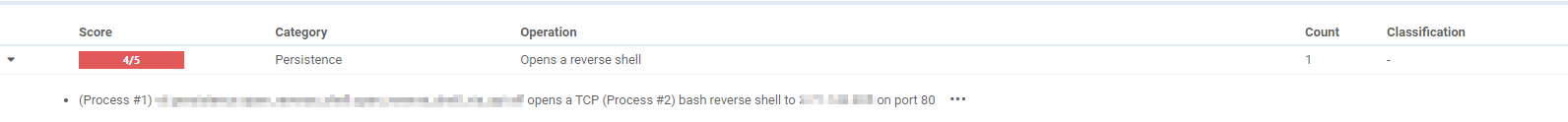
While it’s not a brand new trend, the use of reverse shells remains a commonplace strategy for achieving persistence on Unix systems, similarly to Remote Desktop Protocol (RDP) connections on Windows platforms. For instance, in a recent Linux malware campaign detailed in a report by Cadosecurity, the malware employs a reverse shell to maintain persistence across the hosts it infiltrates.
To address this threat effectively, we’ve implemented a new VTI designed to specifically detect reverse shells on Unix-like systems.

2) VTI: Detect process hollowing
Category: Process injection
MITRE ATT&CK® Technique: T1055.012
Process hollowing is a technique used by threat actors to inject malicious code into a legitimate process while maintaining the appearance of normal behavior. This technique is particularly effective for malware because it leverages trusted executables, making it harder for security solutions to detect and mitigate the malicious activity. Additionally, since the malicious code runs within a legitimate process, it can bypass certain security mechanisms that may be in place to monitor or restrict the behavior of standalone executables. Let’s have a look now at a simple diagram below illustrating the process hollowing attack:
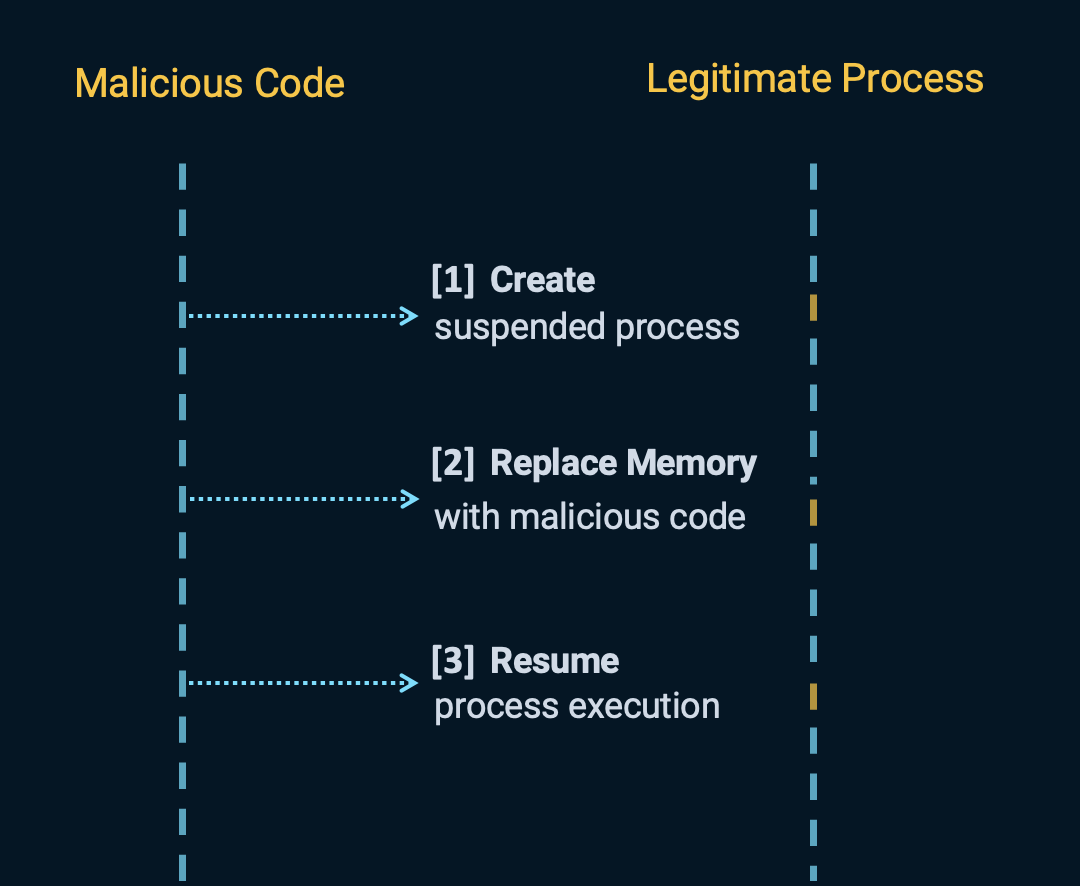

Attack steps:
[1]: Malicious code initiates the process hollowing technique by creating a new instance of a legitimate process in a suspended state.
[2]: Once the process is created, the malicious code replaces the memory contents of the legitimate process with its own malicious code.
[3]: After the memory replacement is completed, the execution of the legitimate process is resumed, but now it contains and executes the injected malicious code. The malicious code within the legitimate process can then carry out various malicious activities, such as data theft, further malware downloading, or other unauthorized actions on the system.
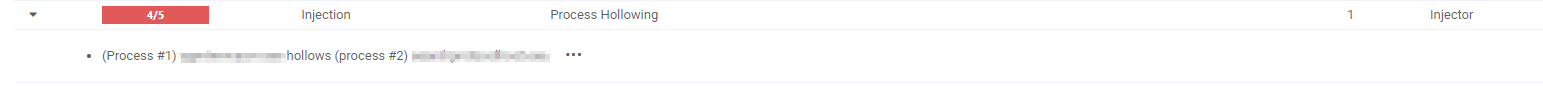
To counter this threat, we’ve introduced a new VTI that detects process hollowing, which, when identified accurately within malware samples, warrants a higher scoring for injection compared to other techniques.
In March 2024, we’ve made several improvements to the Smart Link Detonation (SLD) mechanism in our Platform products. If you haven’t read about it yet – SLD is a feature that enables the automatic evaluation and detonation of suspicious looking hyperlinks in document and email samples. Here’s a recap of the most important changes.
Google Redirect Abuse
We’ve witnessed a lot of campaigns where threat actors leverage seemingly benign platforms to distribute malware in the past. But this time Google is being used for the same purpose!. Malicious links disguised as clean google URLs are circulated through various channels, including emails, social media, and malicious websites. These links contain a redirect through Google’s servers, making them appear legitimate to unsuspecting users.
URL filtering technologies commonly used by organizations to block access to known malicious websites may not flag URLs that redirect through Google. This loophole enables threat actors to circumvent URL filtering systems, allowing their malicious links to reach intended targets undetected.
To address this threat, we’ve enhanced our Smart Link Detonation feature with a new mechanism that prompts our Platform to detonate redirection URLs, such as: hXXps://www.google.com/url?sa=t&url=http://example.org/. By using our SLD feature to detonate URLs employing Google redirects, security teams can effectively disrupt the malware distribution chain and protect users from falling victim to cyberattacks.
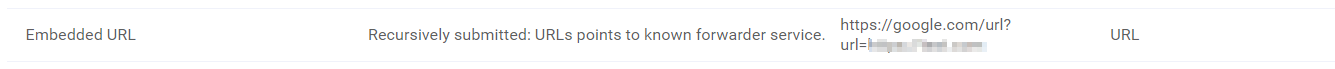
Expanding SLD domain trigger list
We’ve added new domains that were recently abused in phishing campaigns. This inclusion enables SLD to swiftly identify and neutralize threats originating from the following domains:
- “
tome[.]app” – stands out, noted for its role in hosting presentations containing links to phishing sites. - “
gamma[.]app” – this domain is associated with an online presentation service powered by machine learning (ML) and artificial intelligence (AI). - “
app.capacities” – that has been identified as a potential host for nefarious activities such as phishing.
In a recent phishing campaign, threat actors used a technique that has been in the usage for quite some time – mimicking the dialogue found on authentic Microsoft login pages. Upon accessing the site, users are directed to interact with a series of prompts, designed to simulate the experience of a legitimate login process. However, instead of gaining access to their accounts, users are led to a deceptive login form.
This specific campaign used a fake Microsoft login page, designed to imitate the authentic Microsoft interface. Upon loading the page, users were presented with what appeared to be a legitimate login prompt, offering options to log into either their work or personal email accounts. What made this phishing attempt insidious was its convincing appearance. The fake login page closely resembled the genuine Microsoft Outlook interface, complete with branding elements and design features that gave it even more authenticity.
This technique, while not new, poses quite a challenge to security tools. In this particular instance, unlike traditional phishing methods where the fake login form is immediately displayed, this campaign employs a different approach. Instead of instantly presenting the login form, users are initially prompted to choose between work or personal accounts. Failure to make a selection and reveal the login form may result in evasion of phishing detection mechanisms.
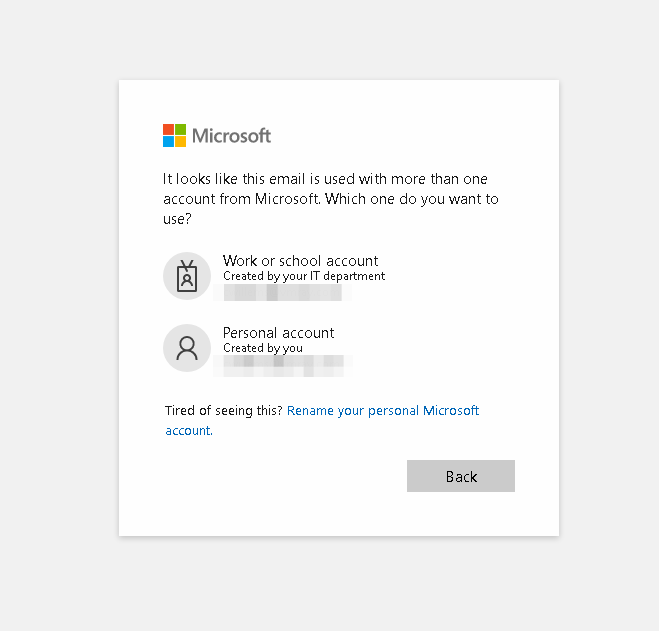
Taking measures against that campaign, we updated the Web engine AutoUI interaction with those pages to reveal the next stage of the phishing attempt without risking exposure to malicious intent. This automated interaction reveals the genuine login form, enabling a more precise detection of phishing attempts.
1) YARA rule for RisePro stealer
RisePro, is a malware-as-a-service info stealer coded in C++, discovered around mid-December 2022 by Flashpoint and Sekoia. Code similarities with Vidar, another popular stealer malware, have been noted. Additionally, Sekoia’s resources claim that RisePro’s code partially intersects with PrivateLoader, pointing to a substantial connection between these malware families.
RisePro sneaks credit card information, login credentials, passwords, and cryptocurrency wallets from infected devices. The perpetrators are already trading stolen data, termed RisePro logs, on Russian dark web marketplaces. Presently, RisePro can be purchased on Telegram, where potential users can connect directly with the malware developer. It’s worth mentioning that stolen accounts could serve as a means to distribute malware or to scam other users.
The latest iteration of the RisePro malware family, was seen in July 2023, and featured:
- The pages selling RisePro advertise it as a combination of the best capabilities of Redline and Vidar, elevating RisePro to new heights as a powerful info stealer.
- Unlike previous versions, where sellers maintained control over crucial logs and information, customers now host their own panels containing compromised data.
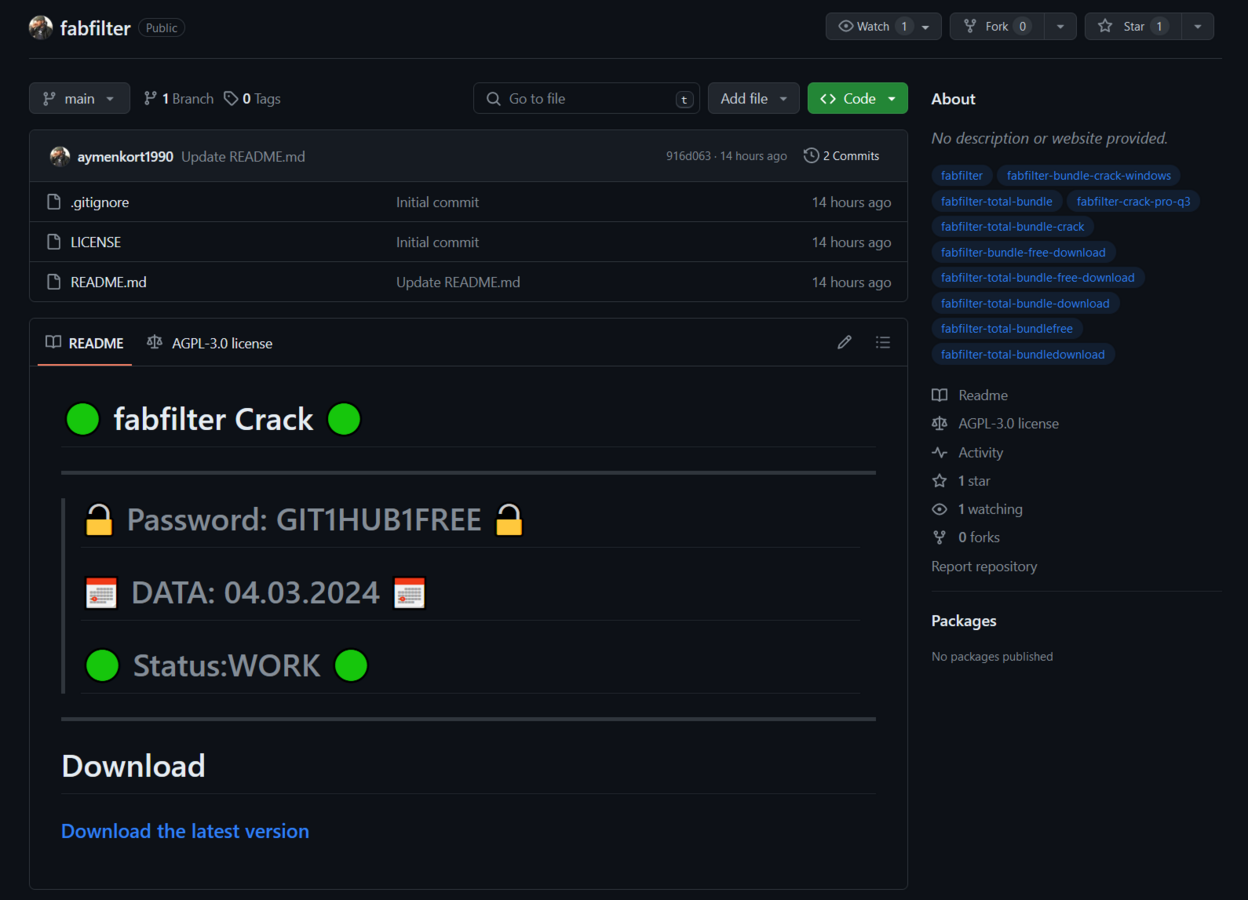
Moreover, in March 2024, G Data CyberDefense – a German cybersecurity company uncovered a significant RisePro campaign on GitHub, referred to as “gitgub” by its authors. This campaign involved 15 infected GitHub repositories offering cracked software. Users, enticed by the promise of free programs, downloaded RAR archive files containing the RisePro stealer. The installer, artificially inflated to a file of substantial size, concealed repeated blocks of code to evade analysis. Upon execution, the installer connected to an external Command and Control system, injecting RisePro into the victim’s system to collect sensitive information. This discovery highlights the ongoing evolution of info stealer threats and the importance of vigilance in protecting against such campaigns.
To stay ahead upon this malware family, as it is in a group of top 10 malware families observed in the wild, we’ve added this new YARA rule.
We do hope our constant research of new malware trends and the features we together bring to our products help you in the navigation of the complex landscape of cybersecurity. In the ongoing battle against evolving threats, it becomes evident that persistence is key. Techniques such as reverse shell attacks and process hollowing underscore the creativity of malicious actors in infiltrating systems and maintaining access. Stay tuned for the April updates, which we will share in the upcoming weeks. Wishing you a cyber-secure and happy beginning of the spring!
如有侵权请联系:admin#unsafe.sh