
The first step in defending your business against phishing is making sure that your employees know that these attacks exist and what they consist of. VMRay’s Abuse Mailbox enables Enterprise, MSSP and MDR SOC teams to create a dedicated mailbox hosted by VMRay solutions, allowing each client’s employees to forward any suspicious emails that may have bypassed the organizations primary phishing solution to VMRay for safe detonation and rapid analysis. SOAR solutions can then use that analysis to create an incident case file and initiate automated mitigation actions if required.
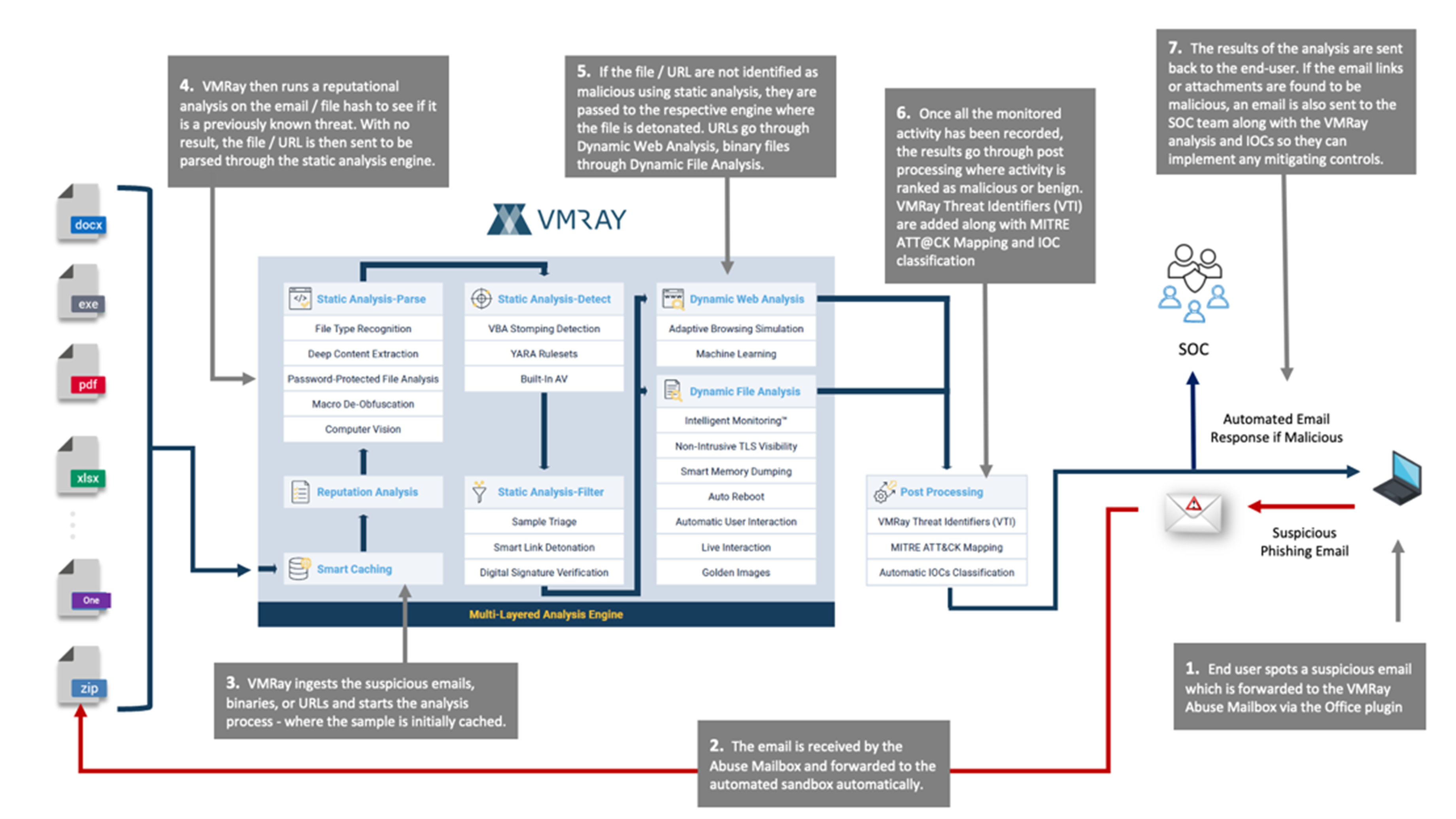
The ten steps below outline the workflow and simplicity of VMRay’s User Reported Phishing post end-user education and demonstrates how little the SOC is impacted in deploying and managing the solution.
- SOC Team enables Abuse Mailbox, then deploys the Outlook auto-submit plug-in to each client end-user desktop.
- End-user identifies a suspicious phishing email and one-click auto-forwards it to the company’s preassigned Abuse Mailbox; <[email protected]>.
- VMRay then strips the forwarding envelope and inspects the sender information along with the originating IP and mail server.
- Email attachments and embedded URLs are then submitted to the reputation engine which contains a database of known malicious file hashes, known benign file hashes, and referenced URLs prior to starting deeper analysis. If identified, previously known malicious files and web links are immediately flagged within seconds.
- The first stage after the reputation assessment is static analysis, which parses the suspicious phishing email or file attachment through a multi-stage process that includes:
Deep Content Extraction: Fully extracting all the embedded content from samples, no matter how deep they are hidden. After extraction these objects are sent for further analysis. This includes extracting embedded objects and links from documents, links and attachments from emails, archive unpacking with no depth limit, as well as decrypting password protected samples.
Computer Vision: An important part of detection & analysis is the ability to extract text from images using Optical Character Recognition (OCR) to detect social engineering techniques used in phishing campaigns.
Smart Link Detonation: Attribute-based rules that determine if links embedded in emails and documents should be detonated for example, domain age, reputation score, abnormal URL string.
Password-Protected File Analysis: Protection against malicious password-protected attachments by searching for passwords in the email body and subject.
- The additional technology used in Dynamic Web Analysis to identify phishing threats are:
Adaptive Browser Simulation: Certain phishing attacks delivered via web pages may only be triggered if the user clicks on a button for example, a download button on file sharing site. This technology detects and simulates the user interaction to automatically trigger payload delivery.
Machine Learning: Fed by high quality input data derived from the VMRay analysis, machine learning is used to identify hard to detect phishing and credential harvesting attacks.
Automatic User Interaction: Simulation of user behavior to spoof evasive malware into detonation so analysis can continue. This includes mouse movements and clicks, as well as clicking on dialog boxes and providing expected responses.
QR Code Detection: Extract and analyze URLs embedded in QR codes— detection techniques force the detonation of QR-encoded URLs originating from an email.
Live Interaction: Allows Threat Analysts to manually interact with the sample during Dynamic File Analysis and Dynamic Web Analysis.
- For links that reach out to external sites, VMRay follows all recursive links with multiple hops and determines whether the site / payload is malicious or not.
- Both the end-user and SOC team are alerted of the submission if malicious.
- The system generates an analysis report, which includes screenshots of any potentially harmful activity.
- SOAR solutions can be configured to monitor the Abuse Mailbox and collect the analysis once complete to create an incident case file, initiate an email Policy Rule update based on VMRay’s IOC’s, scan the endpoint to ensure no malware was deployed, or any other automated responses.
To see a quick video of the setup and demonstration of the Abuse Mailbox in action, click on the URL below.
There are many benefits to educating users on phishing attacks and how to identify them. When combined with VMRay’s User Reported Phishing, the burden is lifted from the SOC team by automating the analysis and the results in the form of IOCs can be used to create policy and quarantine rules to quickly mitigate the threat. Adding the human element to the organization’s detection fabric helps strengthens the weakest link in the cybersecurity chain – us.
User-reported phishing blog series:
Part 1: Making the case for user-reported phishing
Part 2: What organizations can do to mitigate phishing email bypass
如有侵权请联系:admin#unsafe.sh