
2024-4-26 00:0:0 Author: techcommunity.microsoft.com(查看原文) 阅读量:3 收藏
Industrial Control Systems (ICS) security has been a subject of research for many years, spurred, in part, by recent state-sponsored ICS-targeting malware and supply-chain attacks like the ZPMC cranes spying concerns that threaten critical infrastructure. Given the potential harm to thousands of people if water treatment facilities, power plants and nuclear reactors or other systems are breached, the stakes are high. Unfortunately, forensics for ICS devices is not as advanced as in IT environments like Windows and Linux. This can stall forensics investigation when incidents occur.
To overcome this challenge, Microsoft released ICSpector, an open-source framework that facilitates the examination of the information and configurations of industrial programmable logic controllers (PLCs). This framework simplifies the process of locating PLCs and detecting any anomalous indicators that are compromised or manipulated. This can assist you in safeguarding the PLCs from adversaries who intend to harm or disrupt their operations.
Many operational technology (OT) security tools based on network layer monitoring, such as Microsoft Defender for IoT, provide network protection for OT/IoT environments, allowing analysts to discover their devices and respond to alerts on vulnerabilities and anomalous behavior. However, one of the biggest challenges is retrieving the code running on the PLC and scanning it as part of an incident response to understand if it was tampered with. This act requires caution, because the PLCs are actively operating vital industrial process. This is where ICSpector can help individuals or facilities perform this task with best practices.
Industrial control systems in brief
Industrial Control Systems (ICS) and Operational Technology (OT) are critical to modern society, powering everything from power grids and water treatment plants to manufacturing facilities and transportation systems. These systems typically rely on a combination of hardware and software components to perform their functions. Programmable logic controllers (PLCs) are used to manage and control the various processes within an industrial environment. As these systems become increasingly digitized and interconnected, they are also becoming more vulnerable to cyberattacks.
Due to their critical role in ensuring the smooth operation of industrial processes, and the physical danger or extreme financial losses that could result if attacked, ICS devices are prime targets of cyberattacks, making ICS security an increasingly critical issue in today's digital landscape.
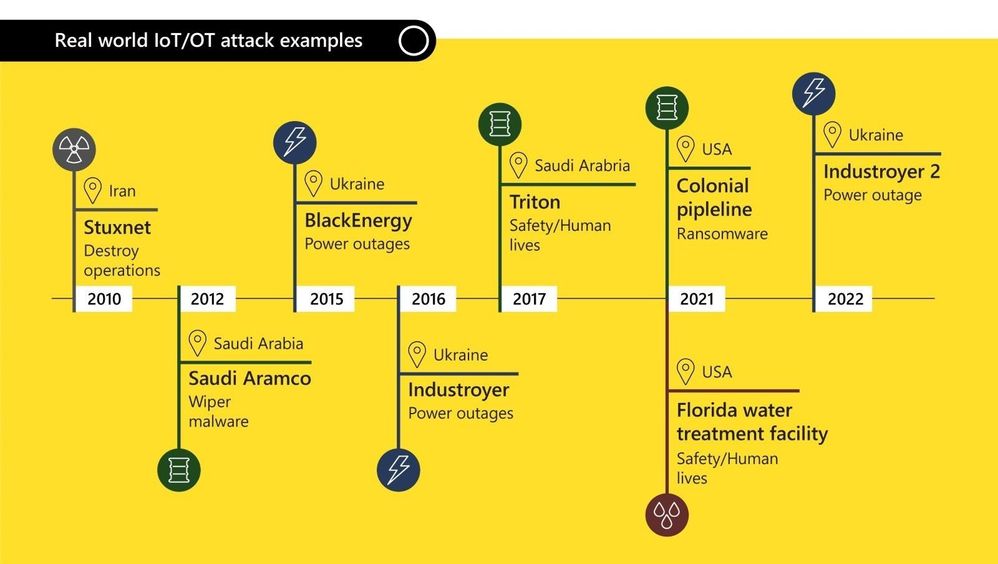
With ICS cyberattacks on the rise, facilities require a holistic solution to address the unique nature of critical infrastructure environments. A common threat involves ICS malware attempting to modify the controller program logic to disrupt operations and cause physical harm.
Extracting data from a controller can be challenging, as it requires specialized expertise in communicating with the device and understanding the specific, and at many times proprietary, protocols used to transmit and store data. This expertise is critical for conducting forensic operations because investigators must be able to extract specific data from a controller to identify security risks and determine the root cause of issues. The challenges around securing OT and the potentially large impact from even one controller being infected in a critical environment, highlight the need for effective security measures and forensic tools to investigate and remediate incidents.
Challenges in ICS forensics
ICS forensics differs from standard IT forensics, because ICS environments possess distinctive features that distinguish them.
Cybersecurity forensics in IT environments involves the collection, analysis, and preservation of digital evidence to identify the cause and extent of a security breach or cyberattack. This includes analyzing network traffic, logs, and system data to identify the source of the attack and to patch vulnerabilities. In contrast, forensics in OT environments involves analyzing ICS data, including data from sensors and controllers used in manufacturing and industrial settings.
While OT communication protocols and execution methods are based on general principles, each vendor can implement its own protocol for data exchange and management. As a result, there is no universal protocol that applies to all controllers, and researchers must investigate each device separately, from its communication patterns to its internal data structure.
Another challenge has to do with talent and tools. Because OT and IT environments were historically isolated and had distinct security operations center teams with different tools, most incident response specialists lack the expertise to analyze OT. And while the IT domain has a variety of forensics tools, such as Autopsy, The Sleuth Kit and FTK, the OT forensics domain is still emerging, lacks a common methodology, and requires OT experts to develop their own solutions.
Specialized tools and techniques have started to emerge to address the unique challenges of conducting investigations in ICS environments. These include the Top 20 Secure PLC Coding Practices, specific OT protocols implementations available on GitHub, and paid tools for an overview of controller programs for a specific set of protocols. Notably missing from these options has been an open-source solution that provides a comprehensive implementation of OT protocols and gives forensics investigators the ability to analyze extracted data and drill down into informative and suspicious areas within the controller loaded project.
ICSpector for industrial engineers and cybersecurity analysts
Microsoft aspired to fill the gap in the market by creating the ICSpector framework. Written in Python and available on GitHub, ICSpector is a framework with tools that enable investigators to:
- Scan their network for programmable logic controllers.
- Extract project configuration and code from controllers.
- Detect any anomalous components within ICS environments.
Security experts can use these forensic artifacts to identify compromised devices as part of manual verification, automated monitoring of tasks, or during incident response. The framework’s modular, flexible design makes it convenient for investigators to customize it to their specific needs.
The framework is composed of several components that can be developed and executed separately. The overall architecture is as follows:
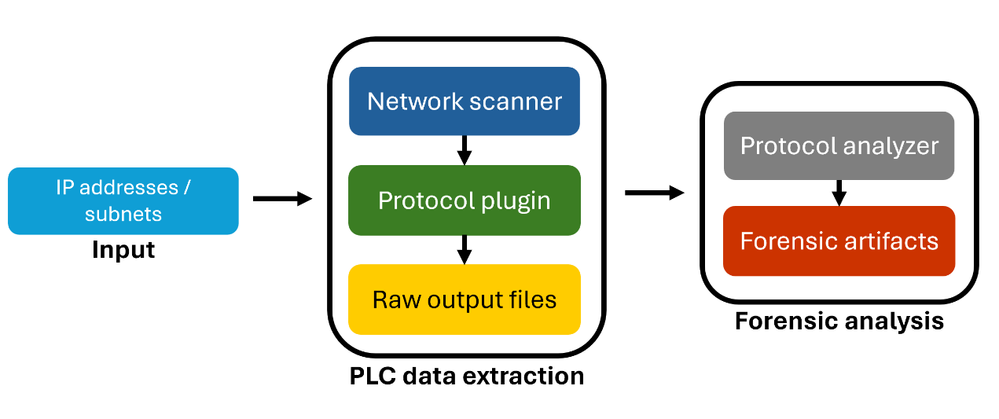
The network scanner identifies devices that communicate in the supported OT protocol and ensures they are responsive, based on a provided IP subnet. Alternatively, a user can provide a specific IP list that was exported from OT security products such as MDIoT, and the network scanner will only verify these devices are connected before beginning data extraction. After feeding the plugin the list of available devices, it extracts the PLC project metadata and logic. Then, the analyzer converts the raw data into a human-readable form and extracts different logic to highlight areas of the project artifacts that usually indicate malicious activity. The framework lets each component run independently with the required input. You can easily modify each component, adapting the operation to current needs, such as introducing protocol changes and analysis methods or altering the output. With the framework, users gain an inventory of assets based on the protocol scanning ability. In the data extraction phase, you can create snapshots of the controller projects and then compare changes over time.
Note: while the framework is not designed to disrupt the production process, due to the sensitive nature of ICS environments, we advise executing the data extracting component in a monitored environment.
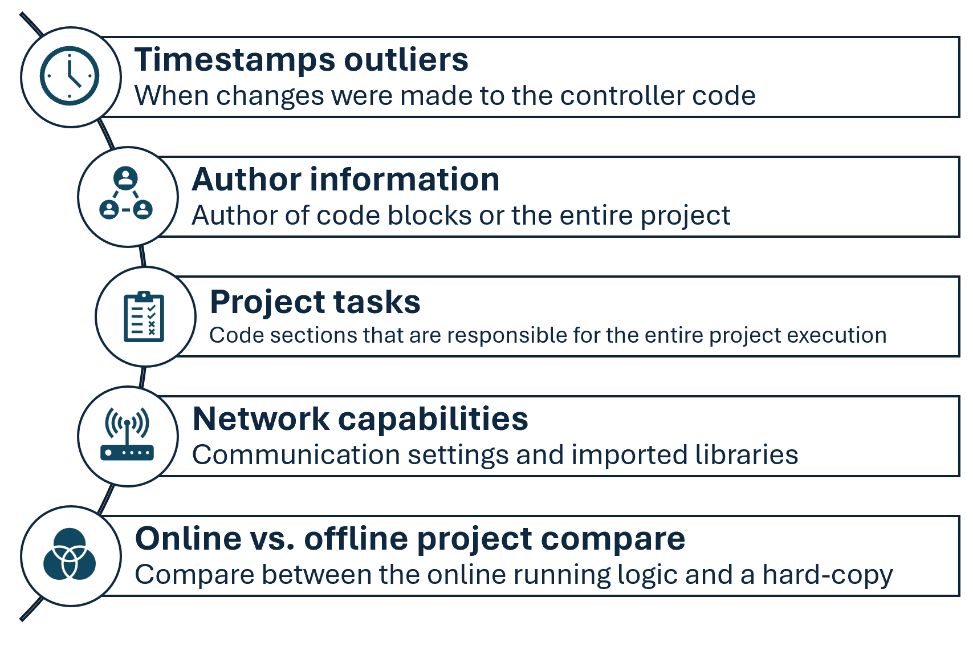
The forensic analysis component of ICSpector allows to dive deep into malicious modifications of controller code. With the ICSpector framework, you can extract timestamp outliers indicating that someone changed the controller code at an unexpected time. Author information is provided as well to help detect suspicious code writers. You can extract network capabilities to surface unexpected communication ports and network libraries. Tasks are the code components responsible for the entire code execution, and the framework gives you an overview of the execution flow Tasks are data structures that trigger the execution of the PLC project, and the framework gives you an overview of existing tasks and their configuration. Additionally, the entire call graph is exported to obtain a clear view of the execution flow. Stuxnet, a sophisticated computer worm that was responsible for causing significant damage to Iran’s nuclear program in 2010, altered a cyclic task to monitor its malicious activities and added malicious logic to the main block of the program. Since the code running on the controller may differ from an engineer’s hard copy, the framework lets you compare the differences between the online and the offline code to catch malicious changes. All of these analysis capabilities could have helped detect the presence of Stuxnet in the network.
Get started with ICSpector
ICSpector is a novel solution that enables OT experts and cybersecurity analysts to enhance their reactive and proactive incident response capabilities in ICS environments. The OT cybersecurity community can participate in and benefit from security efforts in OT forensics, advancing our vision of better security practices in the OT field.
ICSpector can be used in conjunction with Microsoft Defender for IoT, Microsoft Security’s solution for defending IoT and ICS/OT devices that maps out your OT network and alerts you of malicious activity. Defender for IoT, or any other OT security solution, can help with both proactive and reactive OT incident response. Try ICSpector to see how it could benefit your organization. Our how-to guide will walk you through the installation of the framework and explain the components and how to use them in your environment.
Currently, the system supports three OT protocols: Siemens S7Comm, which is compatible with the S7-300/400 series, Rockwell RSLogix, using the Common Industrial Protocol, and Codesys V3, which is a widely used SDK for industrial control devices and is implemented by different vendors.
We encourage you to contribute to the tool by adding new OT protocols and forensic logic.
Learning about ICS basics, PLC programming and investigation methodologies can be done through the webinar, hosted by Microsoft Defender for IoT Research team.
To get started with OT security, watch the “Introduction to ICS/OT Security” webinar series, hosted by Microsoft Security Community.
如有侵权请联系:admin#unsafe.sh