2024-5-1 22:56:8 Author: www.sentinelone.com(查看原文) 阅读量:3 收藏
It’s been little more than a week since Apple rolled out an unprecedented 74 new rules to its XProtect malware signature list in version 2192. A further 10 rules were appended in version 2193 on April 30th. Cupertino’s security team were clearly hoping that a concerted effort would serve to disrupt prolific adware distributor Adload’s assault on macOS devices. Those behind the adware, however, appear to have pivoted quickly as dozens of new Adload samples are already appearing that evade Apple’s new signatures.
In this post, we take a look at one variant of these new samples that is almost entirely undetected on VirusTotal at this time. We hope this exposure will both help inform security teams looking to keep adware nuisances out of their environment and serve to boost detection recognition across other vendor engines.

Apple’s Massive Adload Signature Update
With XProtect version 2192, Apple added 74 new rules to XProtect.yara. While a few of these were targeted at other malware and adware distributors, the vast majority targeted adware widely known as Adload.
Well, there are 74 new rules in XProtect v2192 🤩, so it's going to take me a bit to update https://t.co/Fgr7MGgRL2 with sample hashes, but interesting to see Apple trying to disrupt Adload's entire codebase. 🙌🦾 pic.twitter.com/n0eX6FfSEh
— Phil Stokes ⫍🐠⫎ (@philofishal) April 25, 2024
To put this update in context, prior to version 2192, XProtect had a total of 207 rules, with around two dozen targeting historical versions of Adload. With 2192, the rule count – taking into account both additions and removals – went up to 279, and then 289 with XProtect v2193.
While a few hundred malware rules pales in comparison to the efforts of external security vendors, who tend to have thousands if not tens of thousands of rules as well as behavioral and machine learning engines, an increase of 24% in one update represents a considerable amount of effort. Each rule has to be researched and thoroughly tested to ensure it will not cause false positives – catch innocent programs in its attempt to block malicious ones.
That undertaking would have been ongoing for quite some time and Apple would have hoped that the final result would cause the adware distributor to experience major disruption. No one would expect such actors to just give up and go home – not when there’s significant amounts of money to be made – but it must have been hoped that it would take some time for the malware authors to reconstruct their codebase.
Not so, as it turns out. We began observing new versions of Adload that evade XProtect’s new signatures during last week. Many of these were still widely detected by vendor engines, but by the weekend we were seeing Adload samples that were bypassing both XProtect and other vendors’ engines on VirusTotal.
The XProtect update on the last day of April, v2193, did not address these changes to Adload, instead targeting other prolific adware distributors Pirrit and Bundlore.
New Adload Go Variant (Rload/Lador)
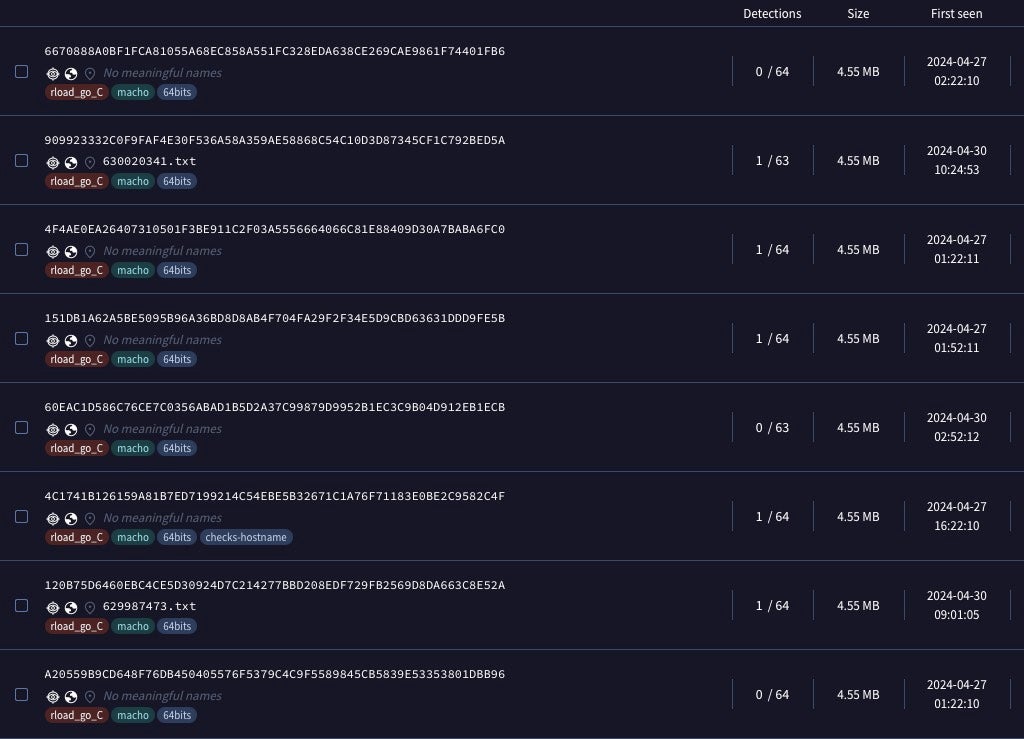
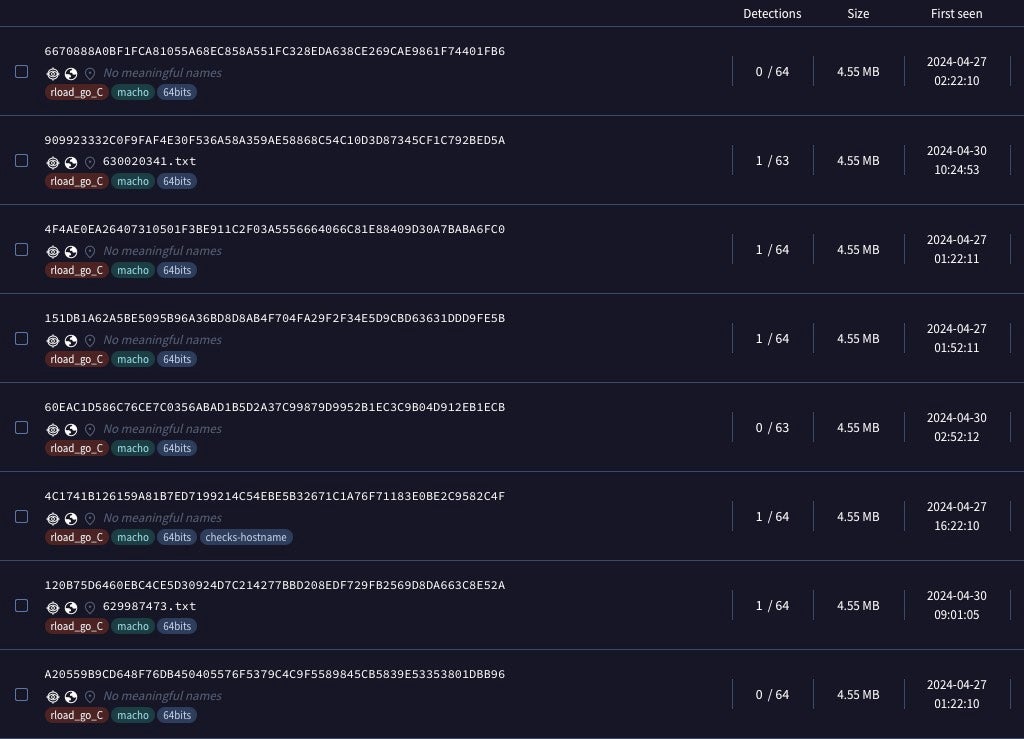
Of the new Adload variants that we have seen, one consistently showed up as having 0 or only 1 detection among VirusTotal engines. This variant has a file size of 4.55MB and is compiled solely for Intel x86_64 architecture. The binaries function as initial droppers for the next stage payload.
None of the early samples we saw this week showed relationships to a parent executable, application or disk image, and none were codesigned, leaving the specific distribution methods obscure, though typically these droppers are embedded in cracked or trojanized apps distributed by malicious websites, torrents and other means. However, all the new samples embedded a unique custom domain registered with NameCheap and following known Adload patterns.
| SHA1 | Domain |
| 13312b3dad9633fa185351e28397c21415d95125 | api[.]deployquest[.]com |
| 21c447cac1c13a6804e52f216a4c41a20c963c01 | api[.]searchwebmesh[.]com |
| 5b1d60c6f461cd8ba91cbca5c7190f4b2752979d | api[.]generalmodules[.]com |
| 67a56aa269b9301981c0538ace75bec2cd381656 | api[.]validexplorer[.]com |
| 7aaff54d2d6e3f38e51a4f084e17b9aad79a9de0 | api[.]operativeeng[.]com |
| 912a2ab06d3afe89e8e2ad19d3300055f0e0a968 | api[.]buffermanager[.]com |
| a99d03fc3b32742de6688274a3ee3cdaef0172bf | api[.]lookwebresults[.]com |
| f166eb63162ce4a5ac169e01c160be98b0e27e13 | api[.]navigationbuffer[.]com |
| feb2c674f135410c3ced05c301f19ab461e37b20 | api[.]inetprogress[.]com |
On execution, the droppers perform system information discovery (T1082) via the ioreg utility:
ioreg -rd1 -c IOPlatformExpertDevice
The malware then seeks to resolve a hardcoded domain name sym._main.dwnldUrl and send an http request to retrieve a remote gzip.
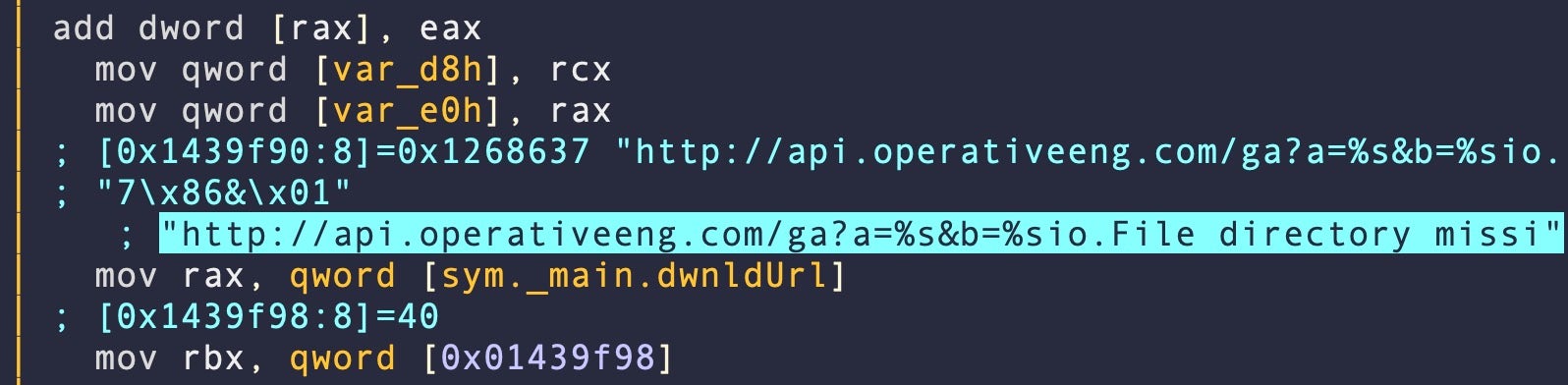
headers = Host: api[.]operativeeng[.]com, User-agent: Go-http-client/1.1, Accept-encoding: gzip, url = http[:]//api.operativeeng[.]com/ga?a=1104&b=E5282DF2-04D7-C854-BD9C-9B4A98F26EDC
The dropper writes the response to a subdirectory in /tmp/. The subdirectory name takes the form of /tmp/[0-9]{10}. If the remote server does not return a compressed archive, the subdirectory will contain an HTML 404 response.
Minor Tweak Evades XProtect Signature Rule
Looking at the binaries from a static point of view, there are a number of interesting artifacts. These binaries use an external (and legitimate) Go package to determine the machine’s unique ID.
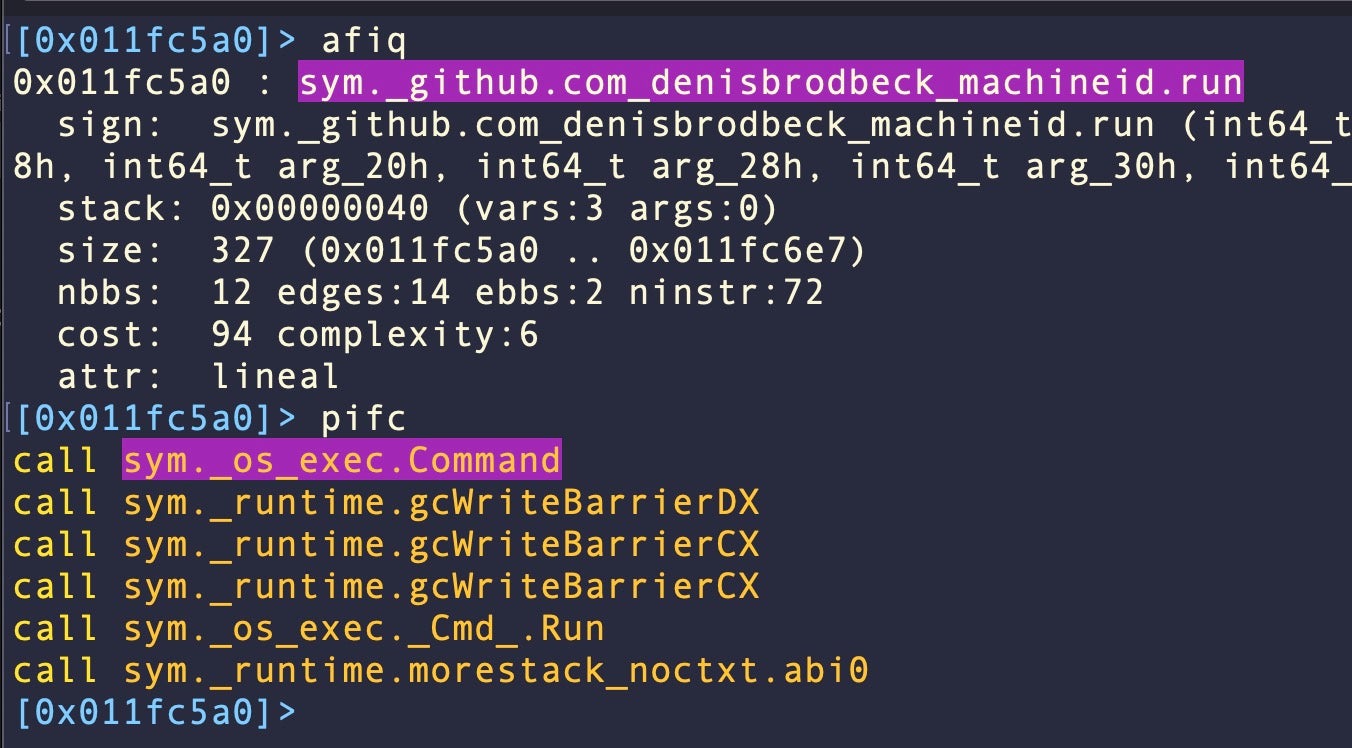
The function that utilizes this package also calls another function to shell out commands, namely sym._os_exec.Command. Although Apple has targeted both of these artifacts in its signatures, the malware still evades detection by XProtect. The rule in XProtect.yara responsible for protecting Mac devices against these adware droppers is as follows:
rule macos_smolgolf_adload_dropper
{
meta:
description = "MACOS.ADLOAD"
strings:
$varName = "main.DownloadURL"
$libraryName = "github.com/denisbrodbeck/machineid.ID"
$execCommand = "os/exec.Command"
condition:
Macho and all of them
}
However, the rule misses the latest samples as the authors have replaced the required string main.DownloadURL with main.dwnldUrl.
SentinelOne Detects Adload
These and many other Adload samples are, however, detected by SentinelOne Singularity. Our multi-engine, defense-in-depth platform uses a combination of static and dynamic engines to ensure the highest level of protection.
While we hope that Apple will quickly update its signatures to take into account this latest Adload pivot, it is inevitable that with XProtect’s YARA rules being transparent to malware developers it won’t take long for any such change to once again be circumvented.
Enterprises are advised to use a third party security solution such as SentinelOne Singularity to ensure that devices are protected against this and other threats targeting macOS devices in the fleet.
To learn more about how SentinelOne can help protect your organization, contact us or request a free demo.
Indicators of Compromise
File Hashes (SHA1)
13312b3dad9633fa185351e28397c21415d95125
21c447cac1c13a6804e52f216a4c41a20c963c01
5b1d60c6f461cd8ba91cbca5c7190f4b2752979d
67a56aa269b9301981c0538ace75bec2cd381656
7aaff54d2d6e3f38e51a4f084e17b9aad79a9de0
912a2ab06d3afe89e8e2ad19d3300055f0e0a968
a99d03fc3b32742de6688274a3ee3cdaef0172bf
f166eb63162ce4a5ac169e01c160be98b0e27e13
feb2c674f135410c3ced05c301f19ab461e37b20
Domains
api[.]buffermanager[.]com
api[.]deployquest[.]com.
api[.]generalmodules[.]com
api[.]inetprogress[.]com
api[.]lookwebresults[.]com
api[.]navigationbuffer[.]com
api[.]operativeeng[.]com
api[.]searchwebmesh[.]com
api[.]validexplorer[.]com
SentinelOne Singularity XDR
See how SentinelOne XDR provides end-to-end enterprise visibility, powerful analytics, and automated response across your complete technology stack.
如有侵权请联系:admin#unsafe.sh