Encountering the HTTP Error 429 can be frustrating for both website owners and users. Error 429 is an HTTP status code indicating that a user has sent too many requests in a given amount of time. Websites and servers implement rate limiting to manage their resources efficiently and ensure access for all users.
In this post, we’ll dive into what 429 errors mean and how to fix them, elaborating on their causes, troubleshooting methods, and preventive measures.
Contents:
- What is HTTP Error 429
- HTTP Error 429 Header
- Common Causes of HTTP Error 429
- Steps to Fix HTTP 429 Error
- WordPress-Specific Fixes for HTTP 429 Error
What is HTTP Error 429?
The HTTP 429 Too Many Requests error occurs when a user has made more requests to the server than allowed within a certain time frame. This rate limiting is important for maintaining server health, preventing overloads, and ensuring all users have fair access.
For instance, an API might allow 100 requests per hour per user; exceeding this limit triggers a 429 error like this one:
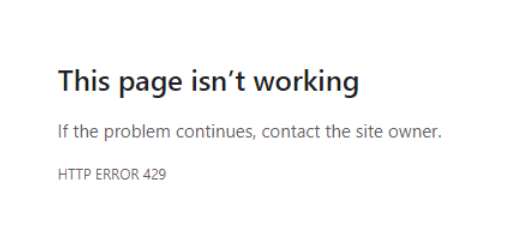
Here is an example of what an Error 429 HTTP header looks like:
HTTP/1.1 429 Too Many Requests Content-Type: text/html Retry-After: 4800
In this example, the 429 Too Many Requests response includes a Retry-After header to indicate how long to wait until making another request.
Common Causes of HTTP Error 429
Understanding the root causes of HTTP 429 errors is useful for troubleshooting. Here are some typical scenarios where you might encounter a 429:
High traffic volume
During peak traffic times, such as major sales or product launches, websites may receive an overwhelming number of requests. If the server’s rate limit isn’t configured to handle such spikes, it may result in 429 errors.

Automated Traffic & DDoS
Bots, crawlers, and automated scripts often make repeated requests to a site. These can be legitimate, like search engine bots, or malicious, like DDoS attack bots. Excessive automated requests can quickly exhaust rate limits, resulting in a 429 response.
Server Setting Misconfigurations
Incorrectly configured rate-limiting settings can unintentionally block users. It’s possible that limits set too low for the normal user traffic can lead to frequent 429 errors.
Resource-Heavy Requests
Some requests consume more server resources than others. For instance, requests that involve complex database queries can strain the server. If such requests are frequent, they may lead to rate limiting.
Shared Hosting Resources
On shared hosting platforms, resources are divided among multiple websites. If another site on the same server is experiencing high traffic or performing heavy operations, your site might suffer from reduced resource availability, leading to 429 errors.
Steps to Fix HTTP 429 Error
Troubleshooting and resolving HTTP 429 errors involve several strategies, from simple wait-and-retry approaches to more complex configuration checks.
1. Wait and retry
The simplest solution is often just to wait before sending more requests. This can be particularly effective if the rate limit is time-based (e.g., 100 requests per hour).
In some cases, your hosting provider may be receiving too many requests to load your site — this is much more common for shared hosting environments. If the issue keeps happening, you may want to consider upgrading your hosting plan or use a VPS.
2. Check response headers
When a 429 error is returned, the server might include `Retry-After` headers in the response. These headers indicate how long you should wait before making another request. Checking these headers can provide a clear pause duration for the issue.
3. Clear your browser cache
A full browser cache might repeat requests automatically, or save outdated settings that exacerbate the rate limit issue. Clearing your cache might reset your interaction with the server.
To clear your cache in Chrome:
- Click the settings icon at the top right of the Chrome window.
- From the drop-down menu, click More tools then click on Clear browsing data.
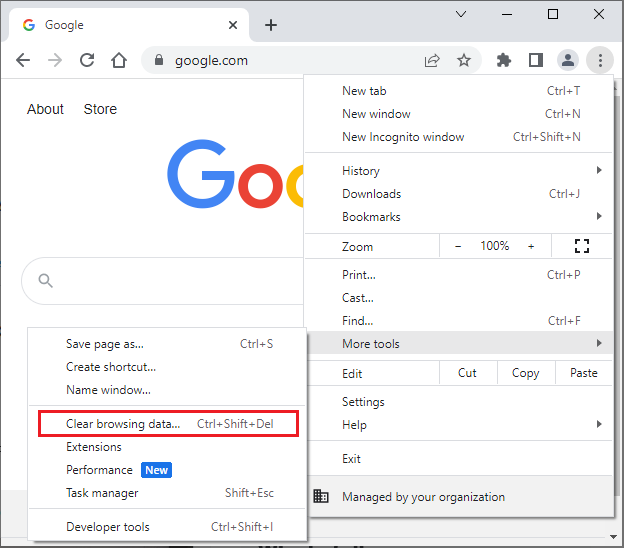
- Select a Time range. You’ll want to select All time to ensure all cache is deleted.
- Click the Clear data.
- Restart your browser.
Your browsing experience may be slower after clearing your cache. Wiping cache will also sign you out of most browsing sessions.
Shortcut:
If you’re on macOS, use Command+Shift+Delete to access your browser’s delete browsing data menu. This key combination works on most browsers, including Google Chrome, Firefox, Edge, and Opera.
For Windows users, press Ctrl+Shift+Delete.
4. Allowlist your IP’s with the Sucuri WAF
In order to filter out malicious requests, the Sucuri WAF acts as a middleman between visitors and the hosting server. Because of that, the connection is modified and the source IP at the network level will be shown as the Website Firewall IP address and not the visitor’s.
If you are a Sucuri firewall user and encountering 429 errors, you may need to allowlist our IP’s if the application needs the real visitor IP address. With the help of an XFF header, your application or web server can be configured to get the visitor IP address correctly.
One of the easiest ways to accomplish this is to install and activate the official Sucuri Plugin.
However, if you’re not a WordPress user there are some other options you can use as well. Learn more in our official documentation.
5. Increase server resources or rate limits
If you own the server or website, consider adjusting the rate limit settings or increasing server resources to handle more requests. Upgrading to a more robust hosting solution or configuring server settings to handle peaks efficiently can prevent the 429 errors.
6. Implement exponential backoff
Exponential backoff is a protocol for customizing the timing of requests to handle failure scenarios. When a request fails, instead of immediately resubmitting, wait for a progressively increased delay. This reduces the likelihood of hitting limits repeatedly and allows the server load to stabilize.
While this step is more for advanced users, setting exponential backoffs along with throttling limits can help reduce requests – and in turn reduce potential 429 errors.
7. Optimize your website code
You may want to look through your website code for potential culprits. If you are using a lot of external JavaScript or CSS resources, combining them can be useful to lessen the number of requests. For example, consider combining small jpegs into a single SVG file.
WordPress-Specific Fixes for HTTP 429 Error
Many WordPress users face the 429 error due to specific configurations or plugin issues. Here’s how to approach fixing them in a WordPress environment
Modify access to the default login URL
Frequent login attempts, particularly during brute force attacks, can trigger 429 errors. Changing the default login URL can mitigate unauthorized attempts significantly.
You can use a plugin like WPS Hide Login to easily change your login URL. Sucuri firewall users can go one step further and protect their login URL and admin pages with IP allowlisting, CAPTCHA, or password protection.
Deactivate problematic plugins
A faulty or resource-heavy plugin could be causing excessive requests. If none of the previous actions helped, try deactivating your plugins one by one to identify any potential offenders.
For example, some plugins overuse /wp-admin/admin-ajax.php which results in a DDoS-like behavior you should look out for.
To get started, log in to your WordPress Dashboard > Plugins. You can opt to deactivate them all at once.
Reactivate plugins one at a time to troubleshoot and confirm.
Switch your WordPress theme
Some WordPress themes can cause excessive requests due to poor coding or compatibility issues. Test with a default WordPress theme to see if it resolves the error before pinning down the problematic theme.
Contact your web host
If none of the above steps work, your hosting provider may have insights or solutions specific to their infrastructure. They can confirm if the issue is on their end and help resolve it.
How Sucuri protects sites from DDoS and rate limiting
Distributed Denial of Service (DDoS) attacks are more than a mere nuisance — they are effective tools employed by cybercriminals to disrupt operations, often resulting in dreaded HTTP errors. These errors occur when your server gets more traffic than it can handle, forcing it to deny legitimate user requests.
Protection via WAF and CDN
Sucuri uses two main tools to keep websites safe from these attacks: the Web Application Firewall (WAF) and the Content Delivery Network (CDN).
Web Application Firewall (WAF)
Imagine Sucuri’s WAF as a strong guard who keeps watch over your website. It does several important things:
- DDoS Protection: The WAF has special technology to stop DDoS attacks. It absorbs the unwanted traffic so that your website doesn’t get overwhelmed and shut down.
- Rate Limiting: It carefully controls how much traffic can come to your site at once. This way, real visitors can still use the website smoothly without facing any errors because of too much traffic.
- Real-time Monitoring: The WAF is always on the lookout. It inspects incoming packets and rejects anything malicious, preventing them from ever reaching your server.
Content Delivery Network (CDN)
Alongside the WAF, Sucuri’s CDN makes your website work even better around the world:
- Cached content: The CDN stores versions of your website in different places globally. This means the website doesn’t have to send data from the main server every time someone visits, which reduces pressure on your main server.
- Enhanced performance: By distributing your website’s data across the globe, it reduces the delay users might experience. This makes the website faster and easier for visitors to use.
- Scalability: The CDN can handle changes in traffic — like sudden or rapid increases — smoothly. This ensures that your website remains stable and responsive, no matter how many people visit.
By using these tools, Sucuri helps your site stay up and running efficiently, even when traffic surges during a DDoS attack (or your latest marketing campaign goes viral).
If you’re a website admin wrestling with recurrent rate limiting errors or simply concerned about potential DDoS attacks, installing Sucuri’s website firewall solution not only offers peace of mind but ensures your site remains operational, secure, and fast. This isn’t just about protecting from what’s out there today; it’s about being prepared for what comes tomorrow.
如有侵权请联系:admin#unsafe.sh