2024-5-15 20:40:25 Author: securityboulevard.com(查看原文) 阅读量:2 收藏
Hold on, let’s guess.
You’ve moved a ton of your business to the cloud – storage, applications, the whole nine yards. Cloud computing offers flexibility, scalability, and a bunch of other benefits.
But here’s the not-so-rosy side:
80% of companies have reported a spike in cloud attacks.
That’s right, cybercriminals are flocking to the cloud just as fast as businesses are.
The cloud presents a vast attack surface, and for many companies, securing it can feel like a complex challenge.
But there’s a way to be proactive, not reactive.
This is where cloud penetration testing (pentesting) comes in.
What is Cloud Penetration Testing?
Cloud penetration testing, also known as cloud pentesting, is a simulated attack specifically designed to assess the security of an organization’s cloud-based systems and infrastructure. It acts like a controlled experiment where ethical hackers (penetration testers) attempt to exploit weaknesses in your cloud environment, just like a malicious actor might.
The primary focus of cloud pentesting is on uncovering misconfigurations and exploitable weaknesses within your cloud setup. These misconfigurations can be
- Incorrect security settings on cloud resources
- Unintended access permissions granted to users or applications
- Weak passwords or encryption keys
- Outdated software versions with known vulnerabilities
By simulating real-world attacks, pentesters can identify these vulnerabilities before they can be exploited by cybercriminals.
But before going deep in cloud penetration testing, it’s important to know why cloud security is such a hot topic.
Why Are Businesses Shifting to the Cloud?
Here’s the deal: companies are ditching traditional on-premise infrastructure for the flexibility and efficiency of cloud-based solutions. This move comes with a bunch of advantages that make cloud computing incredibly attractive:
- Accessibility on Demand: Cloud-based data and applications can be accessed from anywhere, anytime. This empowers employees to work remotely and collaborate seamlessly, regardless of location.
- Enhanced Security: Cloud providers invest heavily in top-notch security measures. They constantly update their systems to address vulnerabilities, so you benefit from these improvements without having to manage them yourself.
- Cost Optimization: Transitioning to the cloud eliminates the hefty upfront costs of buying and maintaining physical servers. Instead, you switch to a pay-as-you-go model, which translates to significant savings on CapEx (capital expenditure) and increased focus on OpEx (operational expenditure). Plus, serverless compute options based on usage (think “pay-per-pizza”) allow for incredible elasticity in your spending.
- Scalability Made Easy: The cloud caters to your business needs. Need to ramp up resources for a new project? No problem. Cloud platforms allow you to easily scale your infrastructure up or down to meet fluctuating demands.
- Unified Management: Managing your entire cloud environment becomes a breeze. Many cloud providers offer a single platform for centralized control and monitoring, simplifying IT operations.
- Built-in Security Features: Several cloud platforms offer robust security suites packed with advanced threat detection and prevention tools. This adds another layer of protection to your valuable data.
Major Cloud Service Providers
Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) are the top 3 cloud service providers, controlling 62% of the market as of 2024.

Source: Statista
The cloud offers a compelling value proposition for businesses. It’s no wonder companies are flocking to it. But with great opportunities come potential risks.
Why the Shift to Cloud Can Be Dangerous?
So, we’ve established that the cloud is fantastic for businesses—flexibility, efficiency, cost savings, the whole package.
But hold on; let’s not get too comfortable.
The very things that make the cloud so attractive can also introduce security risks.
Here are the snapshots of some recent cloud security breaches.
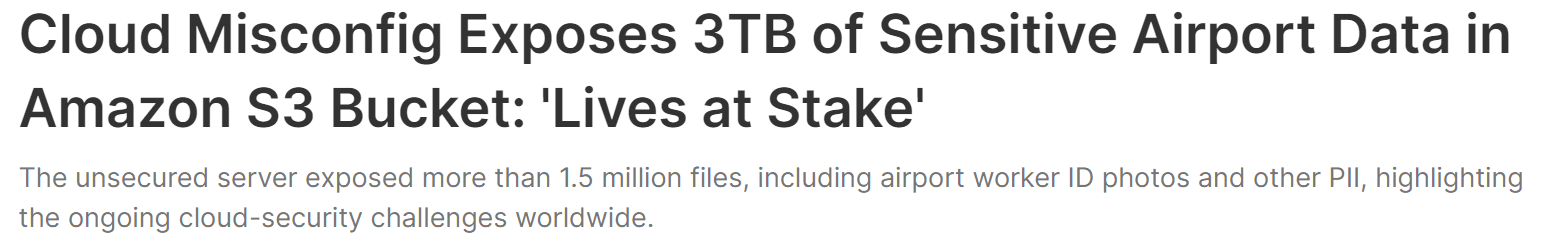


Source: Dark Reading SC Media CPO Magazine
Migrating to the cloud doesn’t magically solve your security woes. There are new threats to consider, and traditional security practices need to be adapted to this new environment.
Let’s take a look at 10 cloud security threats that you should be aware of:
- Misconfiguration: Cloud platforms offer a vast array of options, and it’s easy to miss a setting or two. A single misconfigured setting can leave your data wide open for attackers.
- Unauthorized Access: Shared responsibility is a key concept in cloud security. While providers offer strong security measures, you’re still responsible for access controls within your cloud environment. Weak passwords, insecure access policies, or compromised credentials can grant unauthorized users access to your sensitive data.
- Insecure Interfaces and APIs: APIs (Application Programming Interfaces) are the doorways to your cloud resources. If these interfaces are not properly secured, attackers can exploit vulnerabilities to gain access to your data or launch attacks on your systems.
- Data Loss: Data breaches can happen anywhere, and the cloud is no exception. Accidental deletion, insider threats, or even misconfigured cloud storage buckets can all lead to data loss.
- Denial-of-Service (DoS) Attacks: These attacks aim to overwhelm your cloud resources, making them unavailable to legitimate users. Cloud providers offer some protection against DoS attacks, but it’s crucial to have your own mitigation strategies in place.
- Malware: Malware can find its way into your cloud environment through various means, like infected files uploaded by employees or vulnerabilities in cloud applications. Cloud-based security solutions can help, but endpoint security measures are still important.
- Shared Technology Vulnerabilities: The beauty of the cloud is shared resources. The flip side? A vulnerability in a shared underlying system can impact all users on that platform. Staying informed about cloud provider security updates and patching your own systems promptly is crucial.
- Insider Threats: Unfortunately, malicious actors can exist within your own organization. Insider threats can leverage their authorized access to steal data, disrupt operations, or sabotage systems. Strong access controls and user activity monitoring are essential safeguards.
- Lack of Visibility: One of the biggest challenges in cloud security is maintaining visibility into your environment. Cloud providers offer monitoring tools, but you likely need additional solutions to get a complete picture of your cloud security posture.
- Data Residency and Compliance: Depending on your industry and location, there might be regulations regarding where your data can be stored. Understanding data residency requirements and implementing proper controls is crucial to avoid compliance issues.
This is where cloud penetration testing comes in—a crucial step to ensure your cloud environment is secure and can withstand any malicious attempts.
Benefits of Cloud Penetration Testing
| Feature | Company Benefit | CISO Benefit |
| Vulnerability Identification | Uncover security weaknesses before attackers exploit them, minimizing potential damage and downtime. | Gain a comprehensive understanding of your cloud environment’s risk profile, enabling informed security decisions. |
| Enhanced Security Posture | Proactively address vulnerabilities, strengthening your cloud security posture and reducing the likelihood of successful cyberattacks. | Demonstrate a commitment to proactive security measures, improving brand reputation and customer trust. |
| Compliance Validation | Verify adherence to industry regulations and data security standards through comprehensive testing. | Mitigate compliance risks and penalties, ensuring peace of mind and regulatory confidence. |
| Improved Data Protection | Identify and address security gaps that could expose sensitive data, safeguarding customer information and intellectual property. | Strengthen data security practices, minimizing the impact of potential breaches and protecting valuable assets. |
| Cost Savings | Prevent costly security incidents by proactively addressing vulnerabilities, reducing the need for reactive repairs and potential data recovery efforts. | Optimize security investments by focusing resources on identified risks, maximizing return on investment. |
| Strategic Advantage | Gain a competitive edge by demonstrating a commitment to robust cloud security, fostering trust with clients and partners. | Position yourself as a security-conscious leader within your industry, attracting and retaining valuable partnerships. |
Types of Cloud Penetration Testing
- White-Box Pentesting
Process: White-box testing involves a collaborative approach. Testers have full access to the cloud environment, including system configurations, source code, and user accounts. This allows for a deep examination of security controls and potential vulnerabilities within the architecture.
Benefits:
- Comprehensive Evaluation: White-box testing provides the most thorough assessment, identifying weaknesses in custom code, configuration errors, and access control issues.
- Improved Efficiency: Testers can leverage internal documentation and knowledge to streamline the process, leading to faster completion times.
- Targeted Recommendations: With a clear understanding of the system, testers can deliver highly specific remediation strategies.
Ideal For:
- Highly customized cloud environments with unique applications.
- Organizations seeking a comprehensive security posture evaluation.
- Businesses undergoing significant cloud infrastructure changes.
- Black-Box Pentesting
Process: Black-box testing simulates a real-world attack scenario. Testers have limited or no prior knowledge of the cloud environment, mimicking the approach an external malicious actor might take. They employ various tools and techniques to identify vulnerabilities in defenses and exploit potential entry points.
Benefits:
- Unbiased Assessment: Black-box testing reveals weaknesses an attacker might discover, providing a realistic picture of your security posture.
- Focus on External Threats: This approach prioritizes identifying vulnerabilities that could be exploited by external parties.
- Improved Prioritization: By identifying the easiest access points for attackers, it helps prioritize remediation efforts effectively.
Ideal For:
- Organizations with standardized cloud deployments or using off-the-shelf applications.
- Businesses seeking to test the effectiveness of perimeter security controls.
- Evaluating the security of newly deployed cloud environments.
- Gray-Box Pentesting
Process: Gray-box testing combines elements of both white-box and black-box approaches. Testers have some limited knowledge of the cloud environment, such as system types and functionalities, but not the specific details of configurations or code. This allows them to explore the system from a semi-informed attacker’s perspective.
Benefits:
- Balanced Approach: Gray-box testing offers a balance between comprehensiveness and efficiency, providing valuable insights without the need for full disclosure.
- Focus on Specific Areas: Testers can target specific areas of concern with some pre-existing knowledge, ensuring a more focused evaluation.
- Cost-Effective: This approach can be a good compromise between white-box and black-box testing, offering a good value for the investment.
Ideal For:
- Balancing comprehensive evaluation with time and resource constraints.
- Organizations with a hybrid cloud environment, combining custom and standardized solutions.
- Businesses seeking to test security controls for specific applications or services.
Choosing the Right Approach
The ideal cloud penetration testing approach depends on your specific needs and security posture. Consider factors like the complexity of your cloud environment, the level of access you’re comfortable providing, and the specific areas you want to focus on.
Cloud Pentesting Methodology
- Reconnaissance
This initial phase involves gathering information about the target cloud environment. It’s like a detective laying the groundwork for a case. Activities in this stage include:
- Understanding the cloud provider(s) and services used (e.g., AWS, Azure, GCP, and their specific offerings)
- Identifying the target assets within the cloud environment (storage buckets, databases, servers)
- Mapping the network topology to understand how resources are interconnected
- Discovering potential access points and entry vectors (e.g., APIs, user accounts)
- Reviewing cloud security documentation and configuration settings (if provided)
- Build Test Cases
Based on the information gathered in the reconnaissance phase, penetration testers create test cases. These test cases outline specific scenarios and vulnerabilities that will be targeted during the testing process. This might involve:
- Simulating common cloud attacks (e.g., misconfiguration vulnerabilities, insecure APIs).
- Testing for access control weaknesses and potential privilege escalation.
- Identifying potential data breaches or leaks within the cloud environment.
- Deploy Scanners
Automated vulnerability scanners are deployed to identify common security weaknesses within the cloud environment. These tools can scan for:
- Misconfigurations in cloud resources and services.
- Unpatched vulnerabilities in software components used within the cloud.
- Weak passwords or insecure access controls.
- Manual Penetration Test
Penetration testers manually exploit identified vulnerabilities and test the effectiveness of security controls. This can involve:
- Launching targeted attacks based on the test cases developed earlier.
- Gaining unauthorized access to systems or data within the cloud environment.
- Pivoting within the cloud infrastructure to escalate privileges and reach critical systems.
- Report Generation
Following the penetration testing activities, a comprehensive report is generated. This report includes:
- A detailed description of the methodology used and the scope of the testing.
- Identified vulnerabilities and their potential impact on the cloud environment.
- Proof-of-concept exploits demonstrating the exploitability of vulnerabilities.
- Recommendations for remediation and mitigation strategies to address the identified issues.

Cloud Security Shared Responsibility Model
The cloud environment operates on a shared responsibility model, where both the Cloud Service Provider (CSP) and the customer hold specific security accountabilities. This model ensures a comprehensive security posture by dividing tasks based on expertise and control.
Understanding the Division of Responsibility
| Cloud Layer | Cloud Service Provider (CSP) Responsibility | Customer Responsibility |
| Infrastructure (IaaS) | Physical security of data centers, underlying network infrastructure, hypervisor security | Operating system security, Data security, Application security, Access control configurations |
| Platform (PaaS) | Underlying platform security, operating system patching | Application security, Data security, Access control configurations within the platform |
| Software (SaaS) | Application security of the SaaS offering | Data security within the application, User access control configurations |
Why is the Shared Responsibility Model Important for Penetration Testing?
Understanding the shared model is critical for effective cloud penetration testing. Here’s why:
- Targeted Testing: By clearly defining responsibilities, you can tailor penetration tests to focus on areas under your control. This optimizes testing efforts and identifies vulnerabilities you are accountable for.
- Improved Security Posture: The shared model encourages collaboration between you and the CSP. Penetration testing can uncover weaknesses in both your security measures and the CSP’s infrastructure, leading to a more robust overall security posture.
- Regulatory Compliance: Many regulations mandate that organizations understand and address their cloud security responsibilities. Penetration testing aligned with the shared model demonstrates your commitment to compliance.
Aligning Penetration Testing with the Shared Model
- Map Your Responsibilities: Clearly define your security boundaries within the cloud environment based on the service model (IaaS, PaaS, SaaS) you utilize.
- Collaborate with your CSP: Establish clear communication channels with your CSP to understand their security practices and testing methodologies.
- Focus on Your Security Domain: Design penetration tests to target vulnerabilities within your control, leveraging the expertise of the CSP for any identified infrastructure weaknesses.
Cloud Pentesting vs Pentesting vs Traditional Pentesting
This table breaks down the key differences between cloud penetration testing, penetration testing in general, and traditional penetration testing methods.
| Feature | Cloud Penetration Testing | Penetration Testing | Traditional Penetration Testing |
| Target Environment | Cloud infrastructure (AWS, Azure, GCP, etc.) | IT systems, networks, applications (on-premise or cloud) | On-premise IT infrastructure (servers, networks, applications) |
| Focus | Cloud-specific configurations, security controls, APIs, storage access | Identifying vulnerabilities across IT systems, networks, and applications | Identifying vulnerabilities in hardware, software, network configurations |
| Methodology | Leverages cloud-based tools and techniques | Employs a combination of manual testing and automated tools | Primarily relies on manual testing with some automated tools |
| Shared Responsibility Model | Considers the division of security responsibility between the cloud provider and the organization | Applies to the organization’s entire IT infrastructure | Focuses solely on the organization’s on-premise assets |
| Expertise Required | Pentesters with knowledge of cloud security and specific cloud platforms | Pentesters with broad cybersecurity expertise | Pentesters with expertise in on-premise network security |
Major Cloud Penetration Testing Tools
This multi-cloud security auditing tool offers broad support for major cloud providers, allowing you to assess security posture across your entire cloud landscape.
Open-source and specifically focused on AWS security, Pacu identifies vulnerabilities and misconfigurations within your AWS environment.
A powerful framework for exploit development, Metasploit allows testers to simulate real-world attacks and assess the effectiveness of security controls.
This versatile web application security testing (WAST) platform is a valuable tool for identifying and exploiting vulnerabilities in web applications hosted in the cloud.
A powerful web application security testing tool that can be deployed on-premise or in the cloud, enabling in-depth scanning of cloud-hosted web applications.
Cloud Penetration Testing With WeSecureApp
Free, automated pentesting tools are okay for a quick scan, but when it comes to your cloud security, you need a deeper inspection. These tools can’t mimic the cunning of a real attacker, leaving you exposed to critical vulnerabilities. Enterprise risk management demands more.
WeSecureApp goes beyond the limitations of automated tools. Our pentesters wield industry-standard tools like Nmap and Burp Suite, but that’s just the beginning. We layer on manual expertise to exploit vulnerabilities exactly like real attackers would. This meticulous approach ensures we uncover even the deepest weaknesses that could be hiding in your cloud security.
We don’t just scan, we strategize, exploit, and expose vulnerabilities that could be hiding under the surface.
The result? Actionable intelligence that helps you prioritize remediation and ensure compliance with industry standards like HIPAA, GDPR, and SOC 2.
Don’t settle for a passing grade from a basic scanner. Get a pentest from WeSecureApp and gain the real-world security assurance you deserve.

The post Cloud Pentesting 101: What to Expect from a Cloud Penetration Test? appeared first on WeSecureApp :: Simplifying Enterprise Security.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security authored by Shubham Jha. Read the original post at: https://wesecureapp.com/blog/cloud-pentesting-101-what-to-expect-from-a-cloud-penetration-test/
如有侵权请联系:admin#unsafe.sh

