.msg email files are ole files and can be analyzed with my tool oledump.py.
They have a lot of streams, so finding the information you need (body, headers, attachments, ...) can take some time searching.
That's why I have a plugin that summarizes important information from .msg files: plugin_msg.summary.py.
This is how its output looks like when I run it on a .msg file with malicious attachment:
While showing a friend my plugin features, I got the idea to make some updates to this plugin.
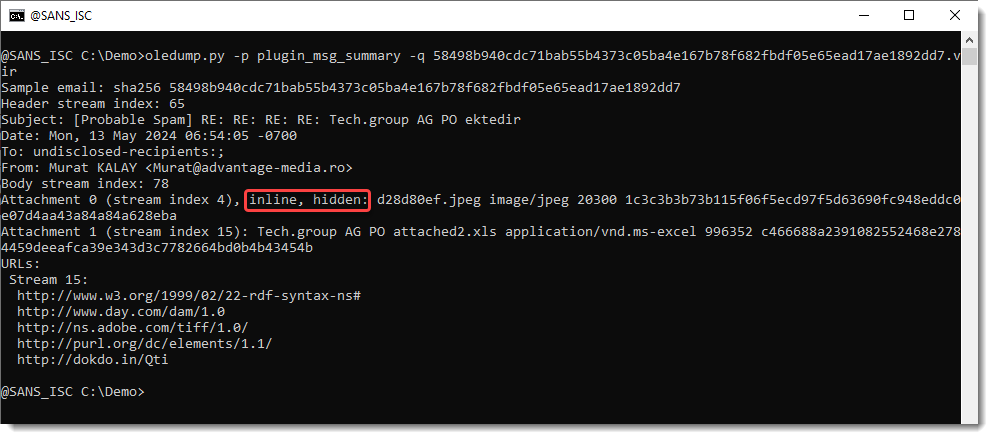
First, when attachments are inline and/or hidden, that information is added to the attachment overview, as can be seen in the screenshot above for attachment 0.
Inline attachments are typically pictures that have been pasted into the email's body, and do not appear as seperate attachments when opened in Outlook, for example.
If you are analyzing an email for malicious attachments, you can first focus on attachments that are not inline.
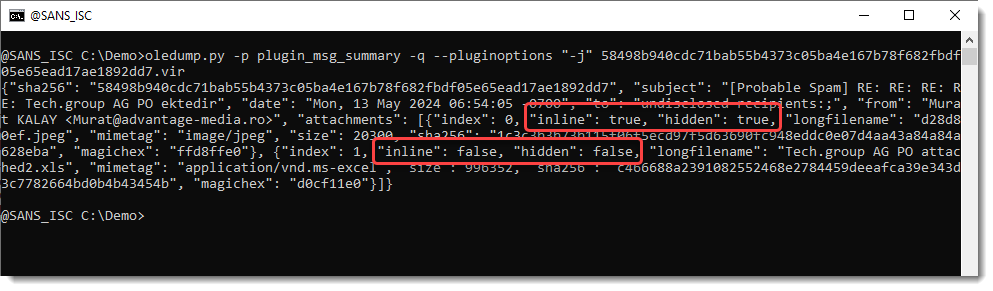
This information also appears when outputing JSON information for the analyzed .msg file:
Second, I added a new option to output JSON information for the attachments with their contents, so that these attachments can be analyzed as I explained in recent diary entries "Analyzing PDF Streams" and "Another PDF Streams Example: Extracting JPEGs".
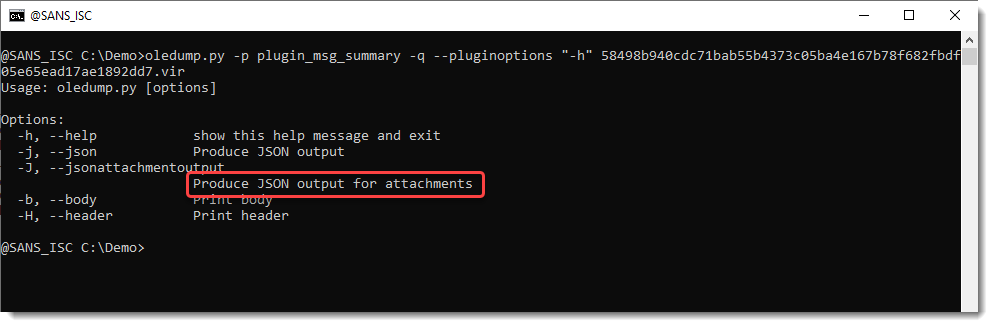
This JSON output can be piped into my other tools that support this JSON format, like file-magic.py (to identify the file type based on its content):
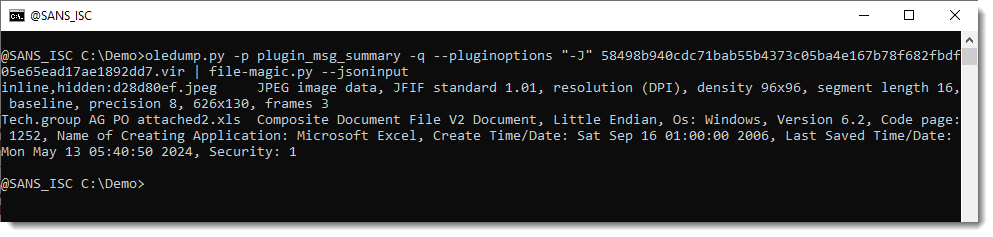
If an attachment is inline and/or hidden, this -J output option prefixes the attachment name in the JSON output:
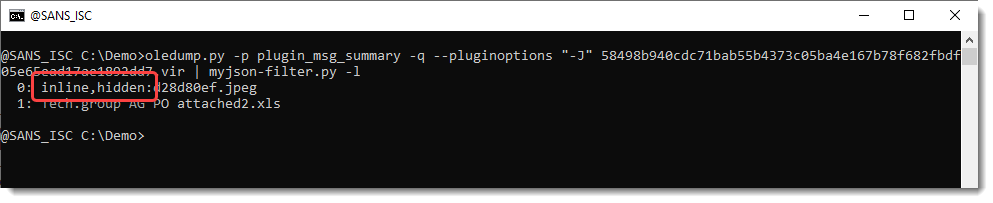
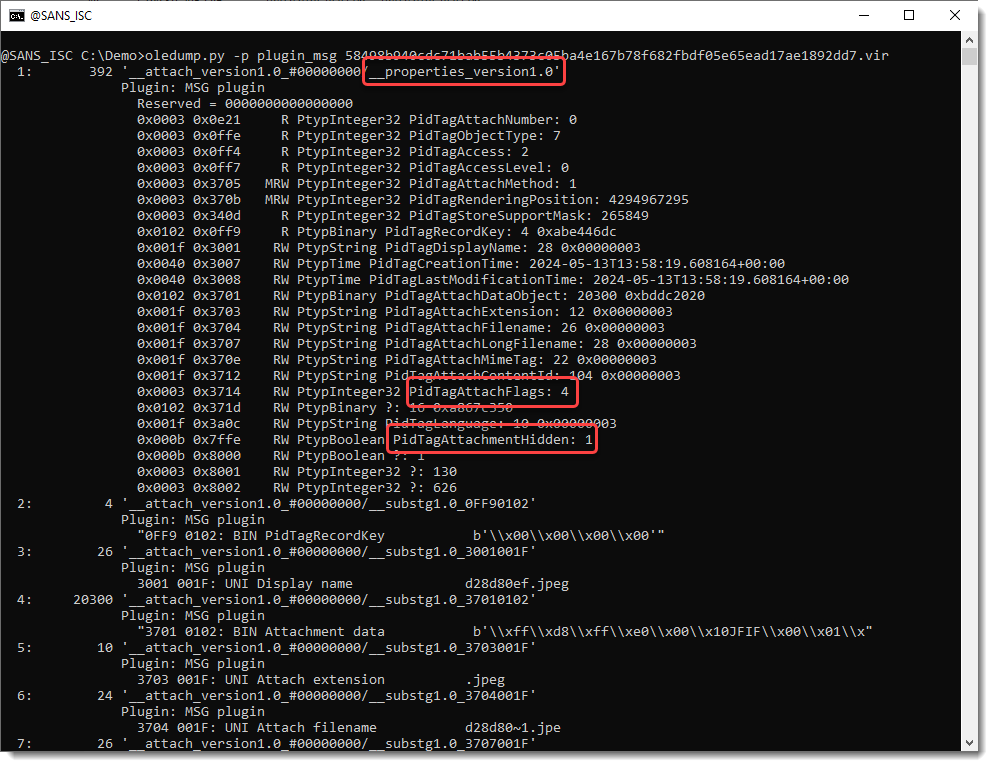
And I also updated my plugin plugin_msg.py to parse property streams. This is where information like inline and hidden are stored:
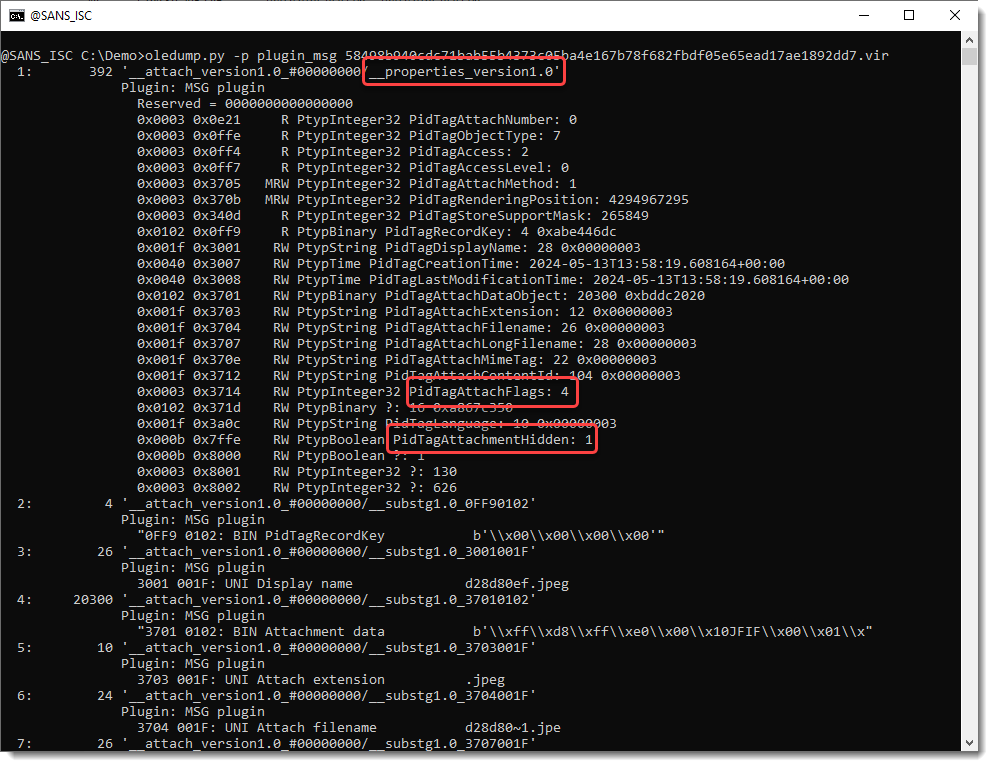
As can be seen in the screenshots, there are also properties for timestamps like creatiion time and last modification time.
Didier Stevens
Senior handler
blog.DidierStevens.com
如有侵权请联系:admin#unsafe.sh