
2024-5-21 22:36:2 Author: www.vmray.com(查看原文) 阅读量:4 收藏
Typically, large product suites sold as a bundle – in most industries – win over customers from a perceived value standpoint where best-in-class is less of a factor. However, as we are finding out from returning customers, there is a compelling argument for best-in-class when it comes to malware sandbox solutions.
“After a year of grappling with missed threats using an alternative solution, it became abundantly clear: VMRay’s dynamic analysis capabilities are unparalleled. We returned to VMRay for ultimate security and resilience, where others fell short.”
In this blog post we will try to explain why customers and prospects prefer the VMRay solution over another vendors product and why “Good enough is not enough” when dealing with advanced malware and phishing threats.
The Allure of Vendor Consolidation
There are many pros and cons to large Enterprise-class product suites and platforms. With multiple products offered as a one-stop shop, what could go wrong? Security Operations Center’s (SOC) on average work with 31 different vendors to provide their services and there are direct and indirect costs associated with maintaining those relationships. In fact, there are 75% more organizations looking into vendor consolidation than there were in 2020.
Many organizations struggle with the number of vendors they must deal with, from implementation, training, maintenance, legal contracts, procurement, and ongoing support. It is clear to see why many organizations jump at the chance to reduce the number of vendors by buying a product bundle with little or no thought of the consequences. If security automation is important for your organization where everything ties neatly together, a sole source solution makes sense.
However, the prospect/customer is mostly fixated on the flagship product and how all the other products within the portfolio work together, rather than delving into the underlying technology of the other bundled solutions. With Big Tech Security vendors, there are always some solutions in the product line that carry less weight, less focus, fewer dedicated resources, and inferior technology than their flagship products. They “tick a box.” I call them “Good Enough” products.
Deal Sweeteners Can Be a Bitter Pill to Swallow
“Good Enough” products typically find their way into an organization as deal sweeteners. When prospects/customer’s start complaining about price, or they are looking for some form of discount, vendors will often take their lowest value product and “throw it in for free.” This stops price erosion of the flagship product, the vendor gets to offload their inferior technology, while keeping other vendors from penetrating the account that may threaten their business.
It is at this point where many prospects/customers get caught out. “Well, the technology is free, it may not be best-in-class, but it’s free.” The prospect/customer will often forgo any due diligence on the technology, deploy it, and hope for the best. The vendor’s flagship product is solid, so every other product should be too. Right?
And with lots of other IT technologies, this is an OK approach. But NOT when it is related to your organization’s cyber security – and especially not when that inferior technology is the last line of your organization’s cyber defense. You need to do due diligence on your sandbox technology because not all sandboxes are the same and the impact of choosing the wrong technology could leave you dealing to a significant breach. The cause? Anti-Sandbox Evasion.
Choosing The Right Sandbox Technology
Why is sandbox technology so important? The reason is that the most evasive malware today is environmentally aware. Malware authors have written code that checks specific aspects of the system to ensure it is not in a malware sandbox or researcher environment. These checks look for evidence of debugging and monitoring tools, registry keys and file paths for Virtual Machine (VM) products, timing attacks, WMI checks, as well as checking browser history, document directories, mouse movement, and other variables that would indicate an illegitimate user environment.
Advanced malware has evolved into using multi-stage delivery systems where malware loader’s such as Smokeloader or Bumblebee ensure the legitimacy of the system before dropping the payload. Nearly all commercial sandboxes use legacy Hooking-based architectures, and this is the chink in their armor and your defenses. Hooking-based sandbox technology uses debugging and monitoring tools within a partially patched detonation environment which can therefore be detected by malware. Upon detecting any of these 200+ possible checks available to the malware author, the malware hibernates and goes to “sleep”. This is to protect the payload from further investigation, while also leading the Analyst to believe the malware is benign.
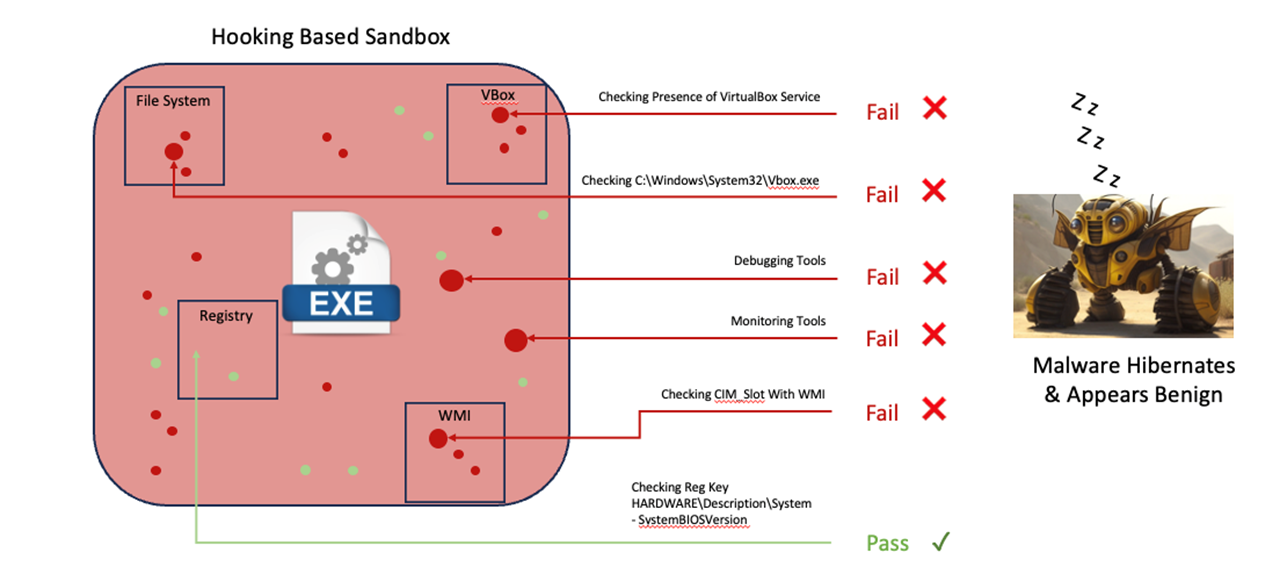
Figure 1. Hooking-based sandboxes have exposures that advanced malware can detect
Why is VMRay so different, you may ask? VMRay utilizes
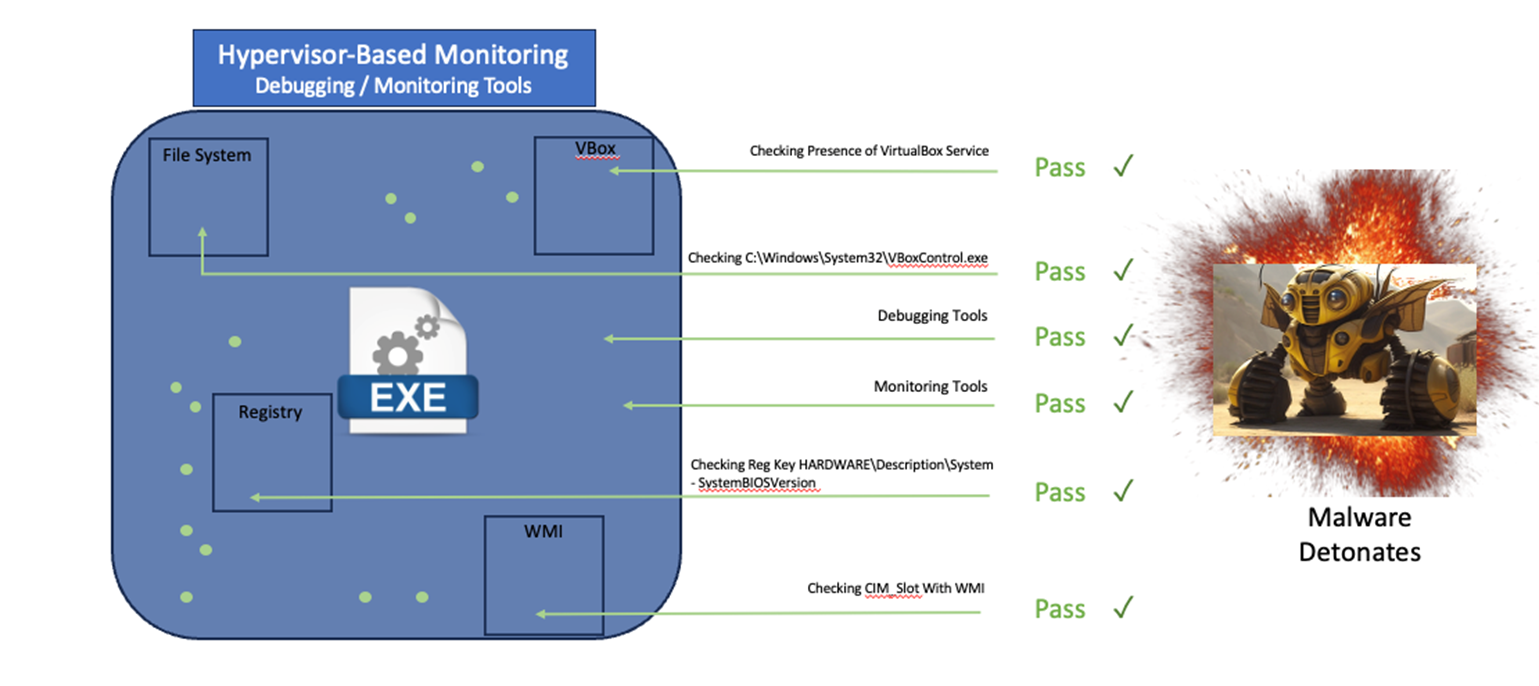
Figure 2. VMRay’s Hypervisor-based detonation environment is hardened against Anti-Sandbox Evasion checks.
In The Best Interests of the Customer?
Vendor lock-in is a strategy that many large product vendors practice all the time. They deprive the customer of choice and put the customer at risk. Yes, many security vendors have a broad focus to address most of the malware problems, but it is that .x% bypassing the vendor’s solution that will do the most damage. Sometimes with devastating results.
At the end of the day, “Good Enough” is not enough when it puts your entire organization at risk. The party that ultimately suffers most from product bundles and “deal sweeteners” of inferior technology is the customer. Identifying highly evasive malware and phishing emails with complex attack chains is a hard problem to solve.
That is why you need a solution from a company that has the experience, focus, and technology to identify advanced, evasive malware and generate actionable IOCs to fully mitigate these threats. Especially if SOC automation of malware triage and phishing analysis is one of your goals.
This is where VMRay comes in.
如有侵权请联系:admin#unsafe.sh