What is Device Binding?
Device binding is a security feature commonly used in mobile banking apps to strengthen account protection. Device binding is the process of registering your device as a trusted device for banking. It registers your device and validates it with the registered mobile number. This allows access to the mobile banking application from a trusted device only and makes your app usage safe and secure.
Why is it necessary to implement device binding in banking and UPI applications?
Device binding is a security feature that improves transaction security and safeguards user data across a variety of applications, including financial and payment services companies like banks and payment service providers (PSPs). It involves connecting a particular device, like a computer, tablet, or smartphone, to an individual’s account or an action, like making a financial transaction. Applications use device binding for several reasons, particularly in the financial sector:
- Enhanced Security: Device binding makes it possible for only approved devices to access accounts and carry out particular tasks. This lowers the possibility of fraud and illegal access.
- Compliance: To secure sensitive financial data, a number of laws and industry standards, such as the Payment Card Industry and Data Security Standard (PCI DSS), mandate or advise using device binding or robust authentication methods.
- User Convenience: Device binding can improve user convenience, even if it is primarily a security measure. On reliable devices, users can access their accounts or finish transactions faster and don’t require repeated authentication.
- Data protection: By making sure that an attacker would still need access to the specific device linked to the account in the event that the credentials for the account were compromised, it can help protect sensitive user data.
- Authentication on Untrusted Devices: To increase security even more, users may be required to utilize better authentication techniques when logging into their accounts from unfamiliar or untrusted devices.
How does Device Binding work?
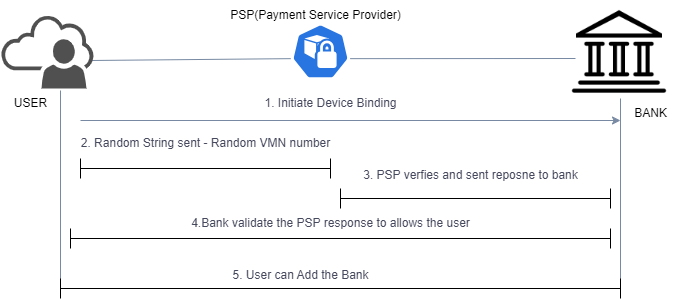
- User Initiates Device Binding: The process begins with the user initiating the device binding. This step involves the user’s device, like a mobile phone, requesting to establish a connection with a specific service.
- Operating System Validation: The system checks for the compatibility and validation of the user’s operating system. This ensures that the user’s device meets the necessary requirements for the intended action.
- Random String Sent to a Virtual Mobile Number (VMN): A unique and randomly generated string is sent to a Virtual Mobile Number (VMN). This string serves as a kind of security code or token.
- PSP Verification: The Payment Service Provider (PSP) verifies whether the user has received the correct string. It ensures that the transmitted string matches what was sent.
- PSP Response to Bank: Following successful verification, the PSP sends a response to the user’s bank. This response confirms that the device binding process has been accurately completed.
- Bank Validation: The user’s bank validates the response received from the PSP. This step is crucial for ensuring that the user’s action is legitimate and secure.
- User Account Addition: Once the bank validates the response, the user is granted permission to add their bank account. This final step allows the user to link their account to the service, establishing the necessary connection.
This section explores how attackers might exploit weaknesses in device binding for mobile banking apps:
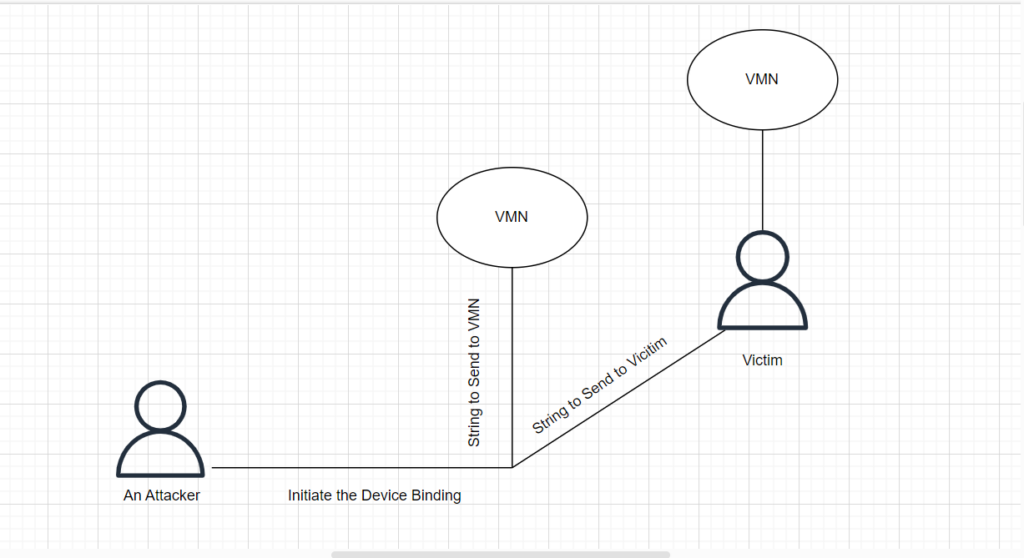
Case Study 1: Social Engineering and VMN Interception
Attacker’s Goal: Register a UPI on the victim’s devic
Method:
- Gaining Access: The attacker tricks the victim into installing malware through social engineering. This malware grants them control over the victim’s device.
- Exploiting VMN Verification: During device binding, the app sends a unique code to a VMN (virtual phone number).
- Message Forwarding: The attacker uses a message forwarding app to redirect this code to both the VMN and the victim’s phone number.
- Intercepting Response: By intercepting the victim’s response containing the code, the attacker could potentially register another user’s UPI on the victim’s device.
Prevention:
- NPCI Check: Implement a system to reject device binding requests if the same code originates from multiple phone numbers within a short timeframe. This effectively thwarts the attacker’s attempt to use the intercepted code.
Remember: Social engineering is a common tactic. Be cautious when installing apps and avoid clicking on suspicious links.
Case Study 2: Exploiting Weak Server-Side Validation
Attacker’s Goal: Bypass the daily limit on device binding attempts.
Method:
- Limited Validation: The attacker discovers a flaw in the app’s server-side validation for the device binding limit. This weakness allows them to manipulate the app’s response to the server.
- Manipulating Response: By exploiting this vulnerability, the attacker can trick the server into believing they are making fewer attempts than they actually are. This could involve techniques like:
- Modifying data packets: Intercepting and altering the data packets sent between the app and the server to hide the true number of attempts.
- Replaying requests: Resending a successful binding request multiple times to bypass the limit.
Prevention:
- Robust Server-Side Validation: Banks should prioritize robust server-side validation that enforces the device binding limit strictly. This validation should be secure and resistant to manipulation by attackers. Here are some ways to achieve this:
- Independent counters: Maintain separate counters on the server for each device to track binding attempts accurately.
- Cryptographic verification: Implement cryptographic techniques to ensure the authenticity and integrity of data exchanged between the app and server.
- Risk-Based Monitoring: In addition to enforcing limits, employ risk-based monitoring to identify suspicious activity. This might involve:
- Tracking IP addresses: Monitor the IP addresses used for binding attempts and flag those originating from suspicious locations or showing unusual activity patterns.
- Device fingerprinting: Use device fingerprinting techniques to identify and potentially block known malicious devices.
By combining strong server-side validation with risk-based monitoring, banks can significantly reduce the risk of attackers bypassing device binding limits.
Key Takeaways
Device binding has emerged as a critical security measure in the realm of mobile banking and UPI applications. By linking a user’s account to a specific device, it adds an extra layer of protection against unauthorized access and fraudulent transactions.
This blog has explored the various benefits of device binding, including enhanced security, regulatory compliance, user convenience, and data protection. We’ve also discussed potential vulnerabilities and how robust server-side validation and risk-based monitoring can mitigate these threats.
While no security system is foolproof, device binding serves as a powerful deterrent against unauthorized access. By implementing robust device binding practices, banks and UPI service providers can significantly enhance the security of their platforms and instill trust among their users.
For an even more secure banking experience, remember to:
- Remain vigilant against social engineering tactics.
- Avoid clicking on suspicious links or downloading apps from untrusted sources.
- Regularly update your mobile device’s operating system and security patches.
By adopting a multi-layered approach that combines device binding with user awareness and best practices, we can create a safer and more secure digital banking environment for everyone.
Recommended Reading
AWS Penetration Testing | Amazon Cloud Security
Azure Penetration Testing – Cloud Security Audits | Microsoft
GCP Penetration Testing | Google Cloud Platform Security
The post Device Binding to Protect Your Banking and UPI Apps appeared first on WeSecureApp :: Simplifying Enterprise Security.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security authored by Sai Nithin. Read the original post at: https://wesecureapp.com/blog/device-binding-to-protect-your-banking-and-upi-apps/
