
2024-5-29 04:46:49 Author: flashpoint.io(查看原文) 阅读量:9 收藏
What is Black Basta?
Black Basta is a ransomware group that has rapidly risen to prominence in the cyber threat landscape since its first appearance in April 2022. Known for its highly targeted and sophisticated attacks, Black Basta operates as a Ransomware-as-a-Service (RaaS) enterprise. It most recently made news for breaching over 500 organizations worldwide. Its victims have included critical infrastructure sectors, according to a joint report by CISA and the FBI.
While some ransomware operators employ a scattergun approach, Black Basta meticulously selects its victims to maximize each attack’s impact.
The group is believed to be composed of former members of the infamous ransomware groups Conti and REvil. This connection is suggested by the similarities in their tactics, techniques, and procedures (TTPs), as well as their rapid establishment and effectiveness in the cybercriminal ecosystem. Like other infamous ransomware groups, Black Basta’s operations are characterized by their use of double extortion tactics, where they encrypt a victim’s data and threaten to release sensitive information on their public leak site if the ransom is not paid.
History and background
Black Basta made its public debut with a series of attacks in late April 2022, just a couple months after Conti ceased operations in February 2022. One of its earliest victims was the German wind energy company Deutsche Windtechnik. However, there are indications that the group may have been active as early as February 2022.
Since its inception, Black Basta has been highly active, amassing over 500 victims as of May 2024. The group utilizes top-tier hacking forums such as Exploit and XSS to seek insiders within target organizations to facilitate administrative access to networks.
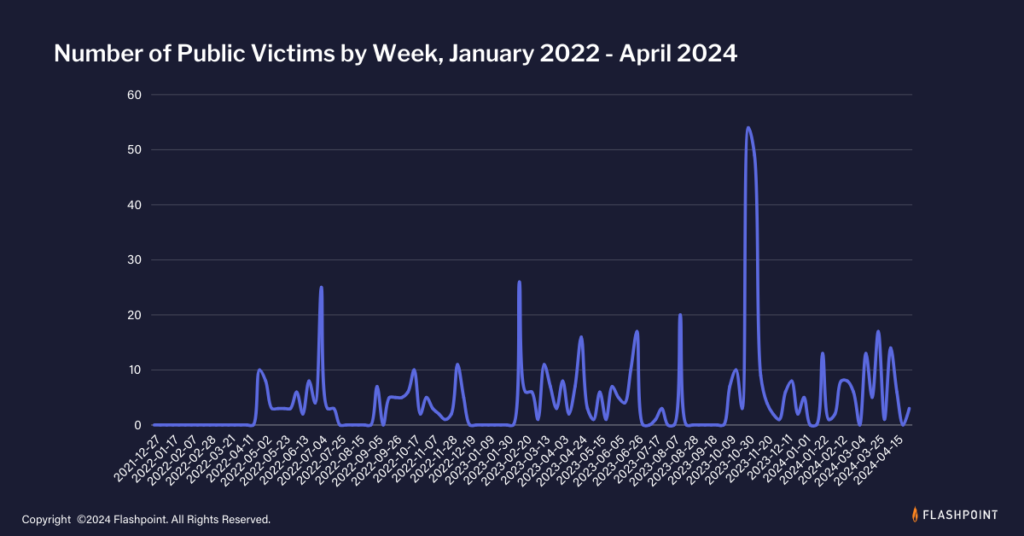
Global impact
Black Basta’s reach and impact are substantial, with the group targeting various sectors, including critical infrastructure. The group primarily targets organizations in the United States, Japan, Canada, the United Kingdom, Australia, and New Zealand.
According to a joint advisory from the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), the Department of Health and Human Services (HHS), and the Multi-State Information Sharing and Analysis Center (MS-ISAC), Black Basta has compromised over 500 organizations worldwide. Their victims span 12 out of 16 critical infrastructure sectors, including healthcare, public health, and energy.
How Black Basta attacks
Black Basta’s operations are characterized by their sophisticated and methodical approach to ransomware attacks. The group leverages a combination of advanced techniques and tools to infiltrate, compromise, and extort their targets.
Initial access
Black Basta employs several strategies to gain initial access to target networks:
- Spear-Phishing Campaigns: In its early campaigns, Black Basta used highly targeted spear-phishing emails to trick individuals into divulging their credentials or downloading malicious attachments.
- Insider Information: The group is known to use illicit forums like Exploit and XSS to recruit insiders within target organizations, offering significant financial incentives for network access.
- Buying Network Access: Black Basta has advertised on forums their intent to purchase corporate network access, collaborating with initial access brokers (IABs) to infiltrate target systems.

Lateral movement and credential harvesting
Once inside a network, Black Basta employs a range of tactics to move laterally and harvest credentials:
- QakBot (QBot): Black Basta uses QakBot to steal credentials and gather information. QakBot is a versatile malware that can perform actions like brute-forcing, web injects, and loading other malware.
- Mimikatz: This tool is used for credential dumping to extract passwords from memory.
- Exploiting Vulnerabilities: The group exploits known vulnerabilities such as ZeroLogon, NoPac, and PrintNightmare to escalate privileges within the network.
- Native Windows Tools: Black Basta utilizes tools like Windows Management Instrumentation (WMI), PowerShell, and PsExec to execute commands and move laterally across the network.
Command and control (C2)
For maintaining control over compromised systems, Black Basta uses various tools and methods:
- Cobalt Strike Beacons: This commercial penetration testing tool is frequently used for C2 operations, allowing the attackers to manage compromised systems remotely.
- SystemBC: Used as a C2 proxy to hide traffic and communicate with the infected systems.
- Rclone: A tool for data exfiltration, enabling the attackers to transfer stolen data to remote locations.
Data exfiltration and encryption
Before encrypting files, Black Basta takes steps to maximize their leverage:
- Disabling Security Tools: The group uses PowerShell scripts to disable antivirus products and endpoint detection and response (EDR) tools.
- Deleting Shadow Copies: To prevent recovery, they delete shadow copies using the command “vssadmin.exe delete shadows /all /quiet”.
- Data Exfiltration: Tools like Rclone and WinSCP are used to exfiltrate sensitive data before encryption.
Encryption
To ensure maximum disruption, they meticulously execute the encryption phase:
- Encryption Payload: Black Basta’s ransomware payload encrypts files using the XChaCha20 algorithm. They have transitioned from using the GNU Multiple Precision Arithmetic Library (GMP) to the Crypto++ encryption library.
- File Extensions and Ransom Note: Encrypted files are appended with a “.basta” extension. A ransom note, typically named “readme.txt”, is placed on the victim’s desktop, directing them to a .onion site for ransom negotiations.
- Advanced Obfuscation: The latest versions of their ransomware use heavy obfuscation and randomized filenames to evade detection by EDR products.
Increasing sophistication and activity
Black Basta continuously evolves its techniques to stay ahead of security measures. Recently, the group has adopted a combination of email DDoS and vishing (voice phishing) tactics. They flood targets with spam emails and then call them posing as IT support, convincing them to install remote access tools like AnyDesk or use Windows Quick Assist. Once access is gained, Black Basta executes batch scripts that appear as legitimate updates to establish persistence and exfiltrate credentials using Secure Copy Protocol (SCP).
Black Basta has expanded its operations to include Linux-based VMware ESXi virtual machines, using the ChaCha20 encryption algorithm. According to recent intelligence and advisories from agencies like CISA and the FBI, Black Basta is becoming increasingly sophisticated in its attacks. The group has been linked to other major ransomware players such as FIN7, indicating a possible collaboration or shared resources. Their use of advanced techniques and tools, combined with their ability to adapt quickly, makes them a formidable threat in the cybersecurity landscape.
Notable attacks
Hyundai Europe (April 2022)
One of Black Basta’s earliest and most significant attacks targeted Hyundai Europe, which led to significant operational disruptions and data breaches within Hyundai’s European operations.
Capita (March 2023)
UK-based outsourcing firm Capita fell victim to a Black Basta ransomware attack In March 2023, which they reported directly cost them approximately $32 million. The company also shared that indirect losses related to the attack, like goodwill impairment, led to additional losses of upwards of $100 million
Toronto Public Library (October 2023)
The Toronto Public Library faced significant outages due to a Black Basta ransomware attack that disrupted library services and affected access to public resources.
Chilean Government Customs Agency (October 2023)
The Chilean government issued a warning following a ransomware attack by Black Basta on its customs agency. They reported that thanks to the work of their IT teams, the incident would not affect the operational continuity of the Service.
The American Dental Association (April 2022)
The American Dental Association experienced an attack from Black Basta that forced them to take affected systems offline. The attack disrupted online services, telephones, email, and webchat.
Financial impact
Black Basta’s attacks have had profound effects on various sectors, including automotive, outsourcing, public services, government, healthcare, and telecommunications. Their attacks typically involve both encrypting data and exfiltrating sensitive information. They hold this information hostage and threaten to release it publicly unless they receive the ransom. This double extortion tactic significantly increases the pressure on victims to comply with ransom demands.
In late 2023, it was reported that Black Basta had accumulated at least $107 million in Bitcoin ransom payments.
The future of Black Basta
Black Basta is poised to remain a significant ransomware threat, driven by their ability to adapt and innovate. They are likely to continue refining their attack methods, increasing their use of sophisticated social engineering tactics such as email DDoS and vishing to gain access to networks. The incorporation of advanced malware and the targeting of diverse platforms, including cloud environments and IoT devices, are expected to enhance their capabilities.
Financial incentives remain a powerful motivator for Black Basta. With over $107 million in ransom payments, ransomware continues to be highly lucrative. Collaboration with other cybercriminal groups could become more structured, leading to the formation of ransomware cartels. These alliances might result in more coordinated attacks and the sharing of advanced tools and techniques. Black Basta’s connections with groups like FIN7 suggest further integration with advanced persistent threats (APTs), providing them with state-sponsored tools and expertise.
Law enforcement actions and improved defensive measures will also influence the future of Black Basta. Intensified efforts by agencies like CISA and the FBI could disrupt their operations, forcing the group to adapt or rebrand. As organizations enhance their cybersecurity defenses, Black Basta will need to innovate continuously to overcome these improved measures.
Take action against ransomware threats
Flashpoint helps organizations deeply understand malware capabilities, origins, and associated communication channels, along with tracking ransomware groups’ primary source communications, announcements about new victims, and trends across victims, industries and locations. Gain insights into criminal activities, dark web forums, and marketplaces, and expose the whereabouts of threat actors, information leaks, encrypted chats, ransomware data leak sites, vulnerabilities and victim auction marketplaces.
Discover how Flashpoint’s advanced threat intelligence and comprehensive security solutions can safeguard your critical assets. Don’t wait for an attack—be proactive and prepared. Sign up for a demo to see Flashpoint in action.
如有侵权请联系:admin#unsafe.sh